You’ve probably heard the line that Apple makes all the decisions for you and there’s nothing you can really customize in macOS. The first part is true; the second, in my view, is utter nonsense. macOS has…
CONTINUE READING 🡒 Meltdown and Spectre: Explaining Speculative Execution Side-Channel Vulnerabilities in CPUs
Over the New Year holidays, security researchers gave hackers the biggest gift imaginable: they uncovered fundamental flaws in modern CPU architecture. By exploiting these vulnerabilities, it’s easy to break address space isolation and read passwords, encryption keys,…
CONTINUE READING 🡒 11 Windows Privilege Escalation Techniques: How Attackers Gain Admin Access
One of the most common security best practices is to run applications and services under a least-privileged account. It doesn’t eliminate security issues, but it does make an attacker’s job harder. Consequently, whatever you’re breaking or pentesting—an…
CONTINUE READING 🡒 The BlackBerry We Lost: A Retrospective on One of the…
By 2017, the mobile OS market had effectively become a duopoly: Google versus Apple, with Android firmly outpacing iOS across most markets. But just a few years earlier, things looked different. Microsoft’s Windows Phone was doing reasonably…
CONTINUE READING 🡒 Android: Island app to isolate and freeze apps — no…
On Android, it’s all too easy to pick up malware. But what if you still have to install a sketchy app? Don’t sweat it—Island lets you not only keep that app away from your data, but also…
CONTINUE READING 🡒 Down the rabbit hole. Storming Yandex Station debug console
This article describes my experience in reverse engineering of firmware used in Yandex Stations. I reversed the U-Boot debug console of the smart station processor and created a utility that extracts it from the decrypted bootloader. The method is applicable to all similar devices and, potentially, to other gadgets…
CONTINUE READING 🡒 How to Discover Neighboring Cisco Devices Using Cisco Discovery Protocol…
Cisco Discovery Protocol (CDP) is a Cisco‑proprietary protocol that allows network devices to advertise information about themselves and their capabilities, and to receive information about neighboring devices.
CONTINUE READING 🡒 The Problems with Xiaomi’s MIUI
MIUI is a great OS and a prime example of how far you can push Android if you want to turn it into something more. And, paradoxically, for that very reason it’s also a bad OS—one that…
CONTINUE READING 🡒 What Is IPAM? How It Streamlines IP Address, DNS, and…
As a corporate network scales from a small LAN with a dozen machines into a sprawling infrastructure, an admin can run into all kinds of issues. Misconfigurations—especially when IP address management isn’t automated—and service disruptions become a…
CONTINUE READING 🡒 Malware Reverse Engineering for Beginners: Unpacking Packers and Defeating Protectors
One of malware authors’ favorite tricks is to use executable packers and protectors. Originally, these tools were fairly mundane: they were meant to shrink compiled binaries or produce demo builds without adding protection to the main code.…
CONTINUE READING 🡒 Optimizing Linux Power Management for Maximum Laptop Battery Life
Be honest: how many times have you felt like spitting in the face of the marketer who dreams up those ridiculous “10–12 hours of battery life” claims? Six or seven is closer to reality—and even then only…
CONTINUE READING 🡒 Samsung Stock Firmware Modding Guide: Root Access, System Tweaks, and…
Samsung smartphone firmware comes packed with features and settings. However, some of them are hidden, and many handy capabilities you’d find in custom ROMs are simply unavailable. On top of that, the firmware includes plenty of preloaded…
CONTINUE READING 🡒 What Hackers Can Do with Your iPhone Passcode: Data Theft,…
Over the past few months, we’ve written a lot about what’s new in iOS 11. “Now we’re really set!” we thought. We were wrong. With iOS 11, Apple not only introduced new security mechanisms but also weakened…
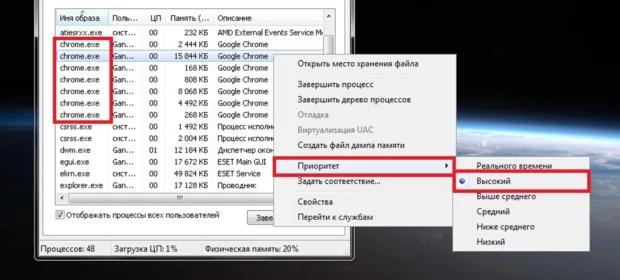
CONTINUE READING 🡒 Launching Processes with a Preset Priority in Windows
This isn’t a new topic, but it might still be useful to someone. How can you automatically launch processes with high or low priority without using third-party tools—just doing it yourself? I’ll demonstrate on Windows 7, but…
CONTINUE READING 🡒 Active Directory Audit: How to Find Inactive User Accounts by…
Once a domain has more than a few hundred users, keeping track of everyone gets tough. If the domain structure is complex and managed by multiple admins, it’s even harder. Throw in departures, promotions, lateral moves, and…
CONTINUE READING 🡒 Root Access on Recent Android Versions: What You Need to…
We cataloged the most common ways to get superuser access on current Android builds; unpacked the differences between SuperSU, phh SuperUser, Magisk, KingRoot, and KingoRoot; tested various methods of hiding root; examined Android 7’s security model and…
CONTINUE READING 🡒 Wi‑Fi USB Flash Drive Teardown: Capabilities and What’s Inside
We examined the internals of a Wi‑Fi–enabled USB drive and took a close look at how it operates. Appearances were deceiving, and our test results overturned our initial assumptions about the device. Below is our unedited, unsanctioned…
CONTINUE READING 🡒 What Data Google Has on You—and How to Export It…
As everyone knows, Google stores a vast amount of data about its users, a point it’s constantly criticized for. In response, Google built a tool that lets you export and download all your data. The service is…
CONTINUE READING 🡒 Monitor and Control: How to Audit and Track Everything on…
Are you sure you’re on top of everything happening on your system? Maybe you’re already using a monitoring stack like Prometheus or Zabbix, but do you know how to generate your own detailed reports on system and…
CONTINUE READING 🡒 Hunting Raccoon Stealer: How a Malware Developer’s OPSEC Failure Exposed…
In most cases, actors get unmasked because the malware author makes a basic OPSEC mistake. That’s what happened this time: the Trojan’s developer not only exposed himself but also gave away all his customers—much to the delight…
CONTINUE READING 🡒