Modern computers and browsers have reached impressive performance levels. Ten years ago, an interactive web app felt like a marvel; now JavaScript powers not just games, but even full-fledged emulators of vintage computers. We’ve picked a few…
CONTINUE READING 🡒 The Crimson Collective hacking group claims to have stolen 570…
The ransomware group Crimson Collective has claimed to have stolen 570 GB of data from 28,000 internal Red Hat repositories. Company representatives confirmed that one of its GitLab instances was breached.
CONTINUE READING 🡒 Hackers Are Sending SMS via Vulnerable Milesight Industrial Routers
Fraudsters are exploiting unsecured Milesight industrial routers to send out phishing SMS messages. Sekoia specialists discovered that such campaigns have been ongoing since 2023.
CONTINUE READING 🡒 Internet access in Afghanistan is starting to be restored
Analysts from the international organization NetBlocks reported that after two days of a complete shutdown, internet connections in Afghanistan have begun to be restored. Meanwhile, the country’s authorities stated that the outages were caused by aging fiber-optic…
CONTINUE READING 🡒 Automating x64dbg. How to transform a debugger into a hacker…
Why automate x64dbg? Because an automated debugger enables you to create custom tools for standard debugging tasks: unpack files, search for signatures, intercept or substitute function outputs on the fly, and even perform fuzzing in RAM! Let’s see how this can be done.
CONTINUE READING 🡒 3 Reasons to Skip the Latest Android Updates
For power users and app developers, Android has long been a very comfortable platform. Open-source code, rich capabilities, and the absence of heavy-handed control from Google made an Android smartphone a true pocket computer. But times change,…
CONTINUE READING 🡒 New Android banking trojan Klopatra uses VNC to control infected…
An Android banking trojan and RAT called Klopatra masquerades as an IPTV and VPN app and has already infected more than 3,000 devices. The malware is a trojan capable of monitoring the device’s screen in real time,…
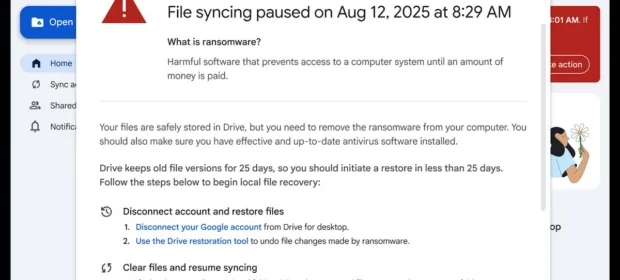
CONTINUE READING 🡒 AI to detect ransomware in Google Drive
Google has introduced a new AI tool designed for Drive for desktop. The model is said to be trained on millions of real ransomware samples and can pause syncing to reduce the damage from a ransomware attack.
CONTINUE READING 🡒 Hiding Sensitive Data in Android Apps: Techniques for Storing and…
At some point, almost every developer has had to hide data inside an app. This could be encryption keys used to decrypt parts of the program, API endpoint URLs, or strings you’d rather conceal to make a…
CONTINUE READING 🡒 Tile Trackers Transmit Data in Plaintext
A group of researchers from the Georgia Institute of Technology claims that Tile Bluetooth trackers transmit identifying data in plaintext. This makes it easy to identify and track their owners.
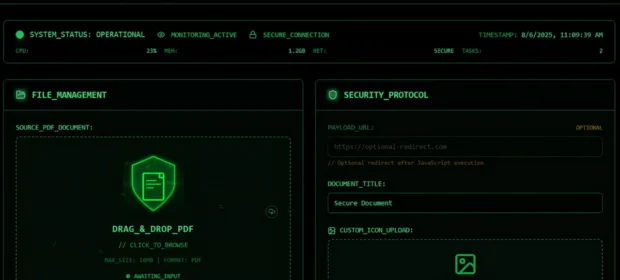
CONTINUE READING 🡒 MatrixPDF Turns PDF Files into Phishing Lures
A new phishing toolkit, MatrixPDF, has been discovered that allows attackers to turn ordinary PDF files into interactive lures that bypass email security and redirect victims to sites for credential theft or malware downloads.
CONTINUE READING 🡒 How to Reduce Mobile Data Usage on Android: Practical Tips…
Cellular networks are delivering ever-faster Internet access, and mobile devices keep consuming more data. But mobile Internet is still far from cheap: plenty of users are still on plans capped at 4 GB, and when you travel,…
CONTINUE READING 🡒 Critical sudo vulnerability is under active exploitation
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned that hackers are actively exploiting a critical vulnerability (CVE-2025-32463) in the sudo utility, which allows commands to be executed on Linux with root-level privileges.
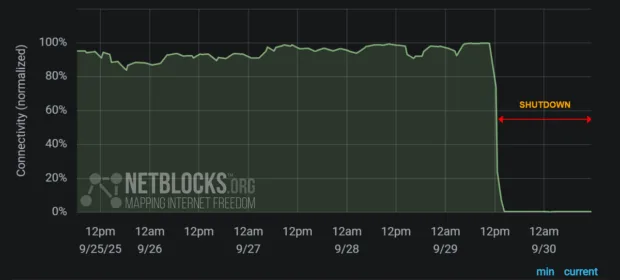
CONTINUE READING 🡒 Internet Completely Shut Down Across Afghanistan
According to specialists from NetBlocks and Cloudflare, on September 29, 2025, a complete internet shutdown was imposed in Afghanistan. Analysts reported that internet service providers in the country were disconnected in stages, and telephone service is also…
CONTINUE READING 🡒 Is Google Building an Android Successor?
In April of last year, without any fanfare, Google quietly published the source code for a new OS called Fuchsia, written in Dart. Because Fuchsia was built on a tiny microkernel, the knee‑jerk reaction from journalists and…
CONTINUE READING 🡒 Japan’s largest brewer halted operations after a hacker attack
Asahi Group Holdings (hereinafter, Asahi), the producer of Japan’s best-selling beer, suffered a cyberattack that disrupted operations at multiple production sites. The incident affected order intake and delivery processes, which had to be suspended. The call center…
CONTINUE READING 🡒 Brave to add Ask Brave AI search feature
The developers at Brave Software, the company behind the privacy-focused browser and search engine, have introduced the Ask Brave feature, which combines search and an AI chat into a single interface.
CONTINUE READING 🡒 F-Droid developers criticize Android’s restrictions on sideloading third-party apps
Recently, Google announced that starting in 2026, only apps from verified developers will be installable on certified Android devices. Representatives of F-Droid say that if developers operating outside the Google Play store are required to undergo verification,…
CONTINUE READING 🡒 Why End-to-End Encryption in Signal, WhatsApp, Telegram, and Viber Won’t…
Encryption in messaging apps became popular because it happens entirely behind the scenes. Users don’t have to generate key pairs, sign them, or revoke old and compromised keys on their own—everything is handled automatically, and the conversation…
CONTINUE READING 🡒 UK government to allocate £1.5 billion to Jaguar Land Rover…
The UK government will provide Jaguar Land Rover with a government-backed loan of £1.5 billion ($2 billion) to restore its supply chain after a large-scale cyberattack that forced the automaker to halt production.
CONTINUE READING 🡒