Encryption in messaging apps became popular because it happens entirely behind the scenes. Users don’t have to generate key pairs, sign them, or revoke old and compromised keys on their own—everything is handled automatically, and the conversation…
CONTINUE READING 🡒 Author: 84ckf1r3
The Great Password Collider: Recovering Passwords from Hashes Without Heavy…
It’s often necessary to recover a password when all you have is its hash. You could brute-force it on your own machine, but it’s much faster to leverage existing databases. Even public datasets contain tens of millions…
CONTINUE READING 🡒 Two Alfa USB Wi‑Fi adapters are better than one: preparing…
In earlier articles on pentesting Wi‑Fi access points, we covered the basics; now it’s time for more advanced techniques. We’ll look at adapter specifics and turn up the power on our dongle. This is necessary to use…
CONTINUE READING 🡒 Why Messaging Apps Don’t Truly Protect Your Chat Privacy—and How…
End-to-end encryption (E2EE) is often touted as a cure-all against persistent attempts by hackers and law enforcement to read online conversations. It’s commonly summarized as “the keys live only on the participants’ devices and never touch the…
CONTINUE READING 🡒 Hacking with Google: Up-to-Date Google Dork Queries for OSINT and…
Penetration tests usually rely on a toolkit of specialized utilities, but one of them is available to everyone and always at your fingertips—Google. You just need to know how to use it. Google dork queries are clever…
CONTINUE READING 🡒 Best Privacy-Focused Linux Distros for Bypassing Censorship and Protecting Against…
Maybe you’ve already used the Tails distribution—or even run it daily. But it’s not the only OS that can mask your presence online and help you bypass regional restrictions. In this article, we’ll look at five Tails…
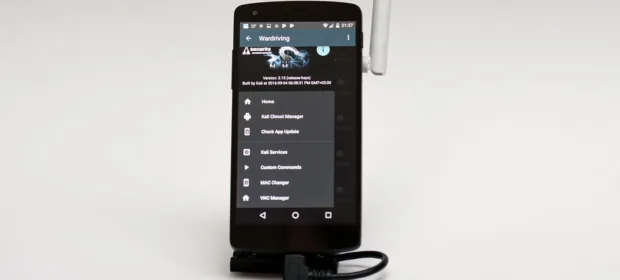
CONTINUE READING 🡒 Conducting a Wi-Fi Security Audit Using a Smartphone with Kali…
Wardriving can be effectively conducted using a smartphone, but the built-in radio module and Android apps are often insufficient for advanced attacks. Instead, external Wi-Fi adapters and console programs for Linux are typically used. All the necessary…
CONTINUE READING 🡒 Earn Cryptocurrency by Renting Out Your Hard Drive Space
If you have unlimited internet and plenty of free disk space, you might be able to make some money from it. We'll explain how blockchain is used for data storage and conduct an experiment with the Storj…
CONTINUE READING 🡒 Understanding and Hacking BitLocker: Exploring Windows Disk Encryption and Its…
The BitLocker encryption technology was first introduced ten years ago and has evolved with each new version of Windows. However, not all changes have been aimed at increasing cryptographic strength. In this article, we will take an…
CONTINUE READING 🡒 Hacking Wi-Fi Networks Using a Smartphone: Reconnaissance and Initial Attack…
You've probably tried hacking wireless networks using a laptop and noticed that it's not very convenient to carry around, plus it attracts attention. But why use a laptop when you have a real pocket-sized computer that lets…
CONTINUE READING 🡒 Victory over “bads”: using Victoria to recover data and reset…
Recovering deleted files is not a problem; there are dozens of utilities for this. But what if the drive is damaged, has an erroneous geometry description, or is password protected at the controller level? Then the Victoria utility comes to the rescue. It is written in assembler, takes up…
CONTINUE READING 🡒 The deplorable four. Testing free antiviruses: Huorong, Preventon, Zoner, and…
Today, I am going to battle-test four antivirus programs: a British one, a Chinese one (featuring an original engine), a Finnish one, and an exciting Czech project at the beta-version stage. All of them are free and…
CONTINUE READING 🡒 Wi-Fi total PWN. Mastering actual Wi-Fi pentesting techniques from scratch
The best way to check the network's security is by trying to hack it. In the past, HackMag had published materials about auditing Wi-Fi networks. Unfortunately, such guides quickly become obsolete. Today, I will share some practical…
CONTINUE READING 🡒 Keep your eyes open! Hacking others IP and Web cameras…
Remote access to Web cameras and security cameras is a common hacking technique. It does not require any special software or even special skills. All you need is a Web browser and a few simple manipulations. In…
CONTINUE READING 🡒 Chromium Alloy. How to forge a hacking tool from a…
The phrase "hacking utilities" has gradually come to acquire a negative meaning. Antivirus software teams curse them out, and users look down on them, placing them on a par with potential threats. But one can perform an…
CONTINUE READING 🡒 How to find vulnerabilities in routers and what to do…
Often, the manufacturers of routers do not particularly care about the quality of their code. As a result, the vulnerabilities are not uncommon. Today, the routers are a priority target of network attacks that allows to steal…
CONTINUE READING 🡒