warning
Sustained, total anonymity is practically unattainable in practice. Moreover, persistent attempts to achieve it will inevitably draw attention to you. For more background, see the XKeyscore program. You can read about it and its legacy within the NSA and GCHQ on onion sites.
The Building Blocks of Privacy
A seasoned Linux hacker can roll their own OS, load it up with their favorite tools, and encrypt every last bit. But that takes a lot of time, so it’s really only for the most hard‑core tinkerers. For everyone else, there are ready‑made options where thousands of details have already been considered and proven privacy protections are bundled and preconfigured.
Despite their surface-level differences, these distributions have a lot in common, since safeguarding personal privacy relies on the same core approaches. Privacy protection involves the following stages, addressed at both the local and network levels:
- Secure wiping of activity traces and any unique (and thus potentially identifying) data used during the session;
- Encryption of data that needs to be retained (e.g., wallets, documents, audio/video recordings, other personal files and configuration files);
- Plausible deniability for encrypted data (using steganography and camouflaging it among more conspicuous decoy crypto‑containers that don’t contain valuable information);
- Application isolation and assigning certain services to separate virtual machines (sandboxes, Xen, VirtualBox, and other virtualization tools) to reduce the risk of deanonymization if compromised by malware/Trojans;
- Kernel hardening patches to tighten interprocess controls and minimize the risk of deanonymization via exploits;
- Panic shutdown mechanisms that quickly purge the most compromising data if the boot drive is at risk of physical seizure;
- Early MAC address spoofing for network interfaces (typically during boot);
- Preventing IP address disclosure (VPN health checks, DNS leak protection, script filtering, chaining high‑anonymity proxies, routing all application traffic through Tor, etc.);
- Anonymous communication channels (chat, email, file sharing);
- Circumventing regional blocks (auto‑configuring public DNS resolvers, free VPNs, fast proxies, Tor, I2P, Freenet).
Naturally, every distribution has its own limitations and won’t bundle all of the tools listed above into a single image—and in practice, it doesn’t need to. Many entries in this list overlap in functionality or are even mutually exclusive.
info
We won’t be discussing the human factor, which can undermine the reliability of any system. We’ll stick to the technical side and simply note that nothing can completely prevent people from making mistakes.
Kodachi
In the previous installment, we looked at distributions for digital forensics, while Kodachi positions itself as an anti-forensics project that makes it harder to analyze your storage and RAM. Technically, it’s another Debian fork with a privacy focus. In some respects, it’s even more thoughtfully designed than the popular Tails.
The latest stable release, Kodachi 3.7, was published in January of last year. The OS hails from Oman—a country with firsthand experience of internet censorship—which gives it a distinctive character.
Xfce was chosen as Kodachi’s desktop environment, and the overall OS interface is styled to resemble macOS. The status of Tor and VPN connections, along with most current system startup parameters, are displayed in real time right on the desktop.
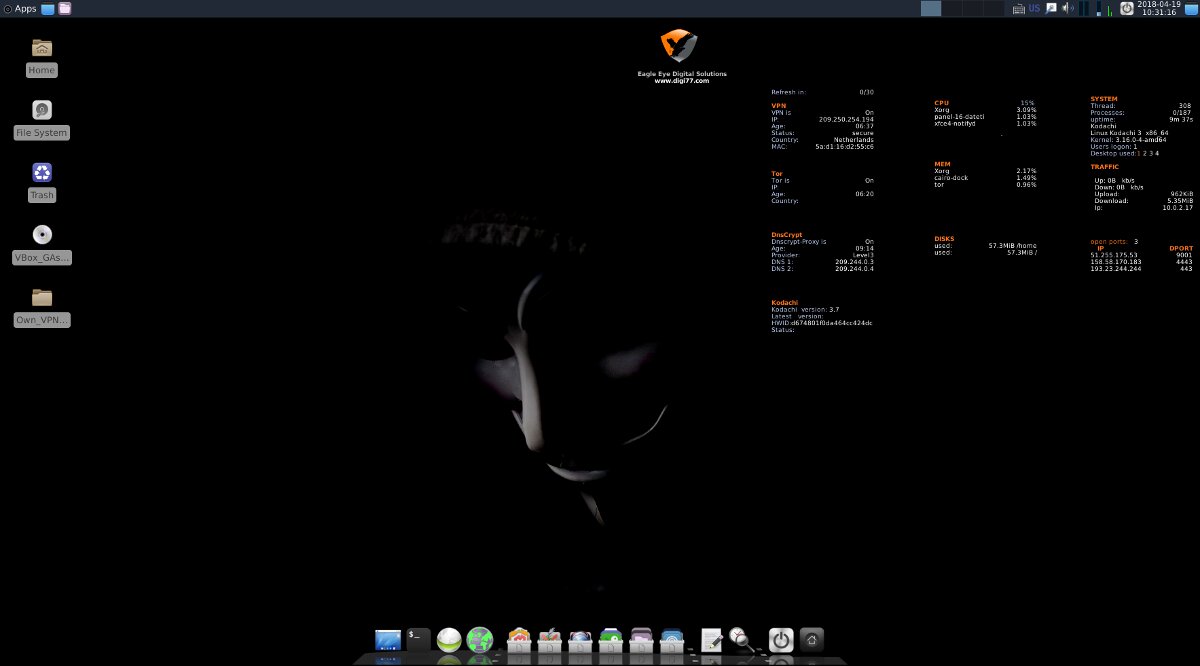
Among Kodachi’s key features are forcing all traffic through Tor and a VPN, with a free VPN preconfigured out of the box.
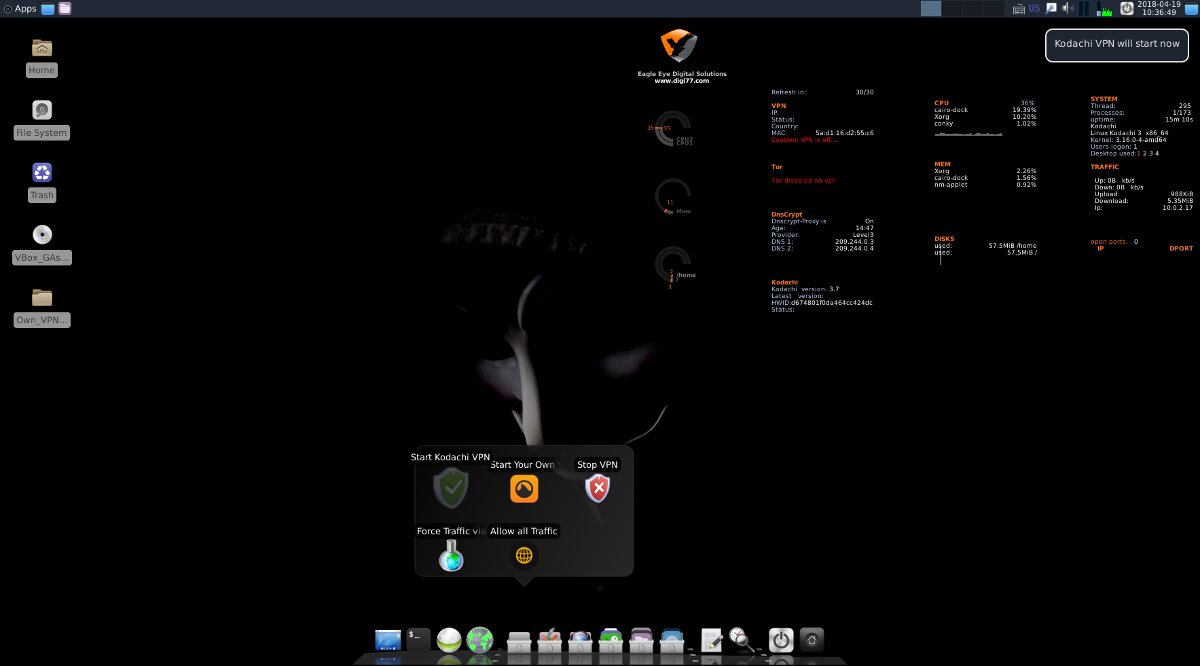
Kodachi also includes built-in DNSCrypt support—a protocol and tool that encrypts DNS queries (e.g., to OpenDNS) using elliptic-curve cryptography. This mitigates common issues like DNS leaks and leaving traces of your online activity in your ISP’s DNS logs.
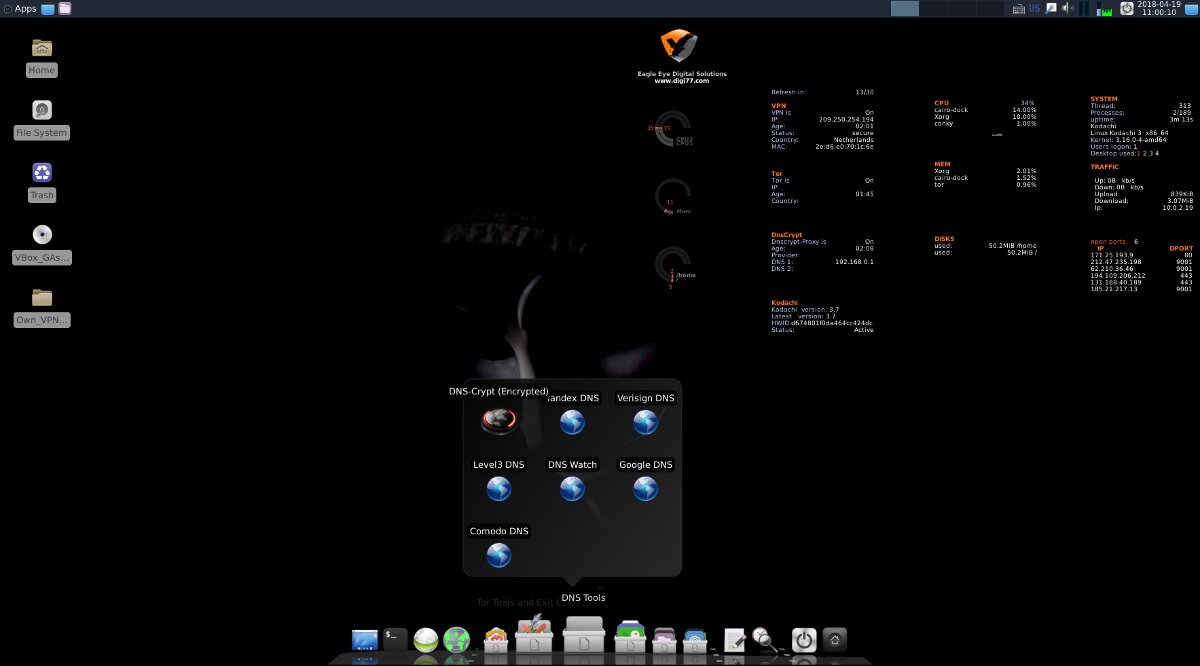
Another thing that sets Kodachi apart is the built-in Multi Tor, which lets you quickly rotate Tor exit nodes and even choose a specific country, and PeerGuardian to help shield your IP on P2P networks (and block peers from a large blacklist).
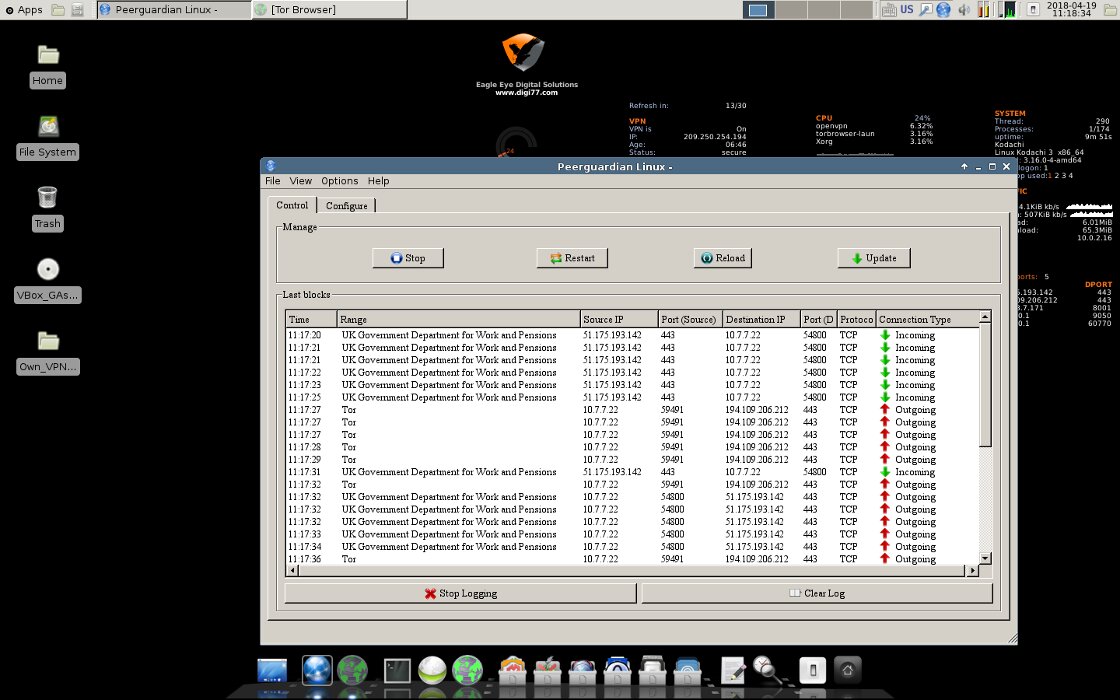
In addition to PeerGuardian, the Uncomplicated Firewall (UFW) is used as the firewall, with the gufw graphical front end.
In Kodachi, you can easily isolate applications using the built-in Firejail sandbox. It’s especially recommended for the browser, email client, and messenger.

The OS comes loaded with cryptography tools (TrueCrypt, VeraCrypt, KeePass, GnuPG, Enigmail, Seahorse, GNU Privacy Guard Assistant) and track‑erasing utilities (BleachBit, Nepomuk Cleaner, Nautilus‑wipe).
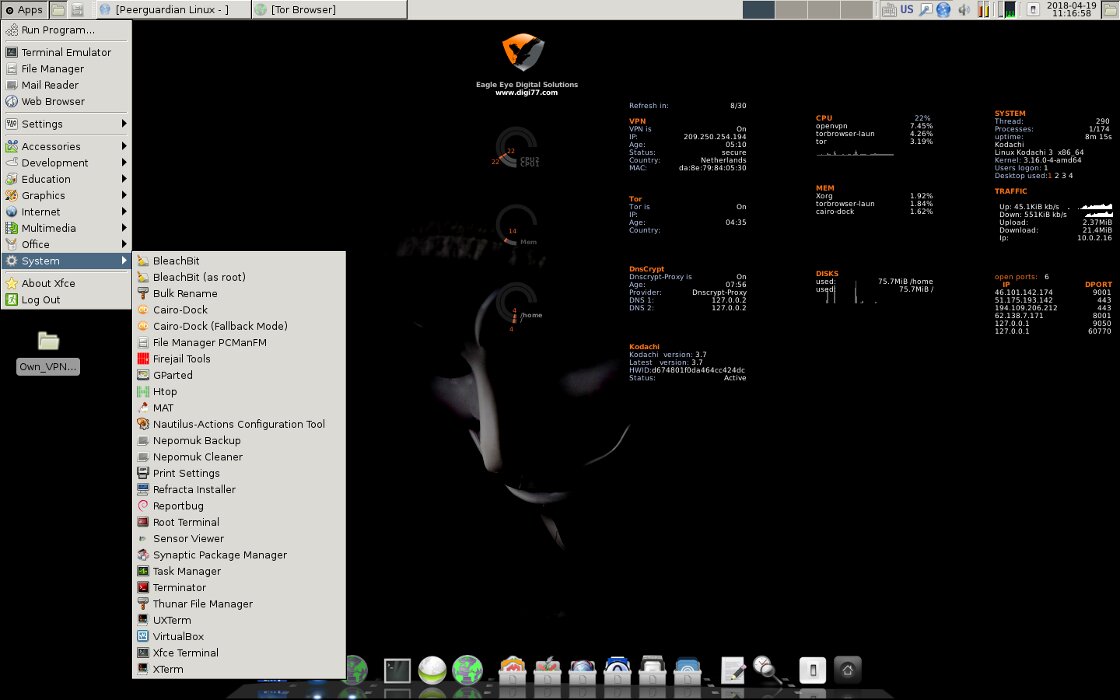
Kodachi includes protection against cold boot attacks. During a cold boot attack, an attacker can partially recover data that was in RAM just seconds earlier. To prevent this, Kodachi overwrites system memory with random data when the computer shuts down.
Rapid-response tools are grouped under the Panic section. It includes utilities for securely wiping data on disk and in RAM, resetting network connections, locking the screen (xtrlock), and even a command to completely wipe the OS.
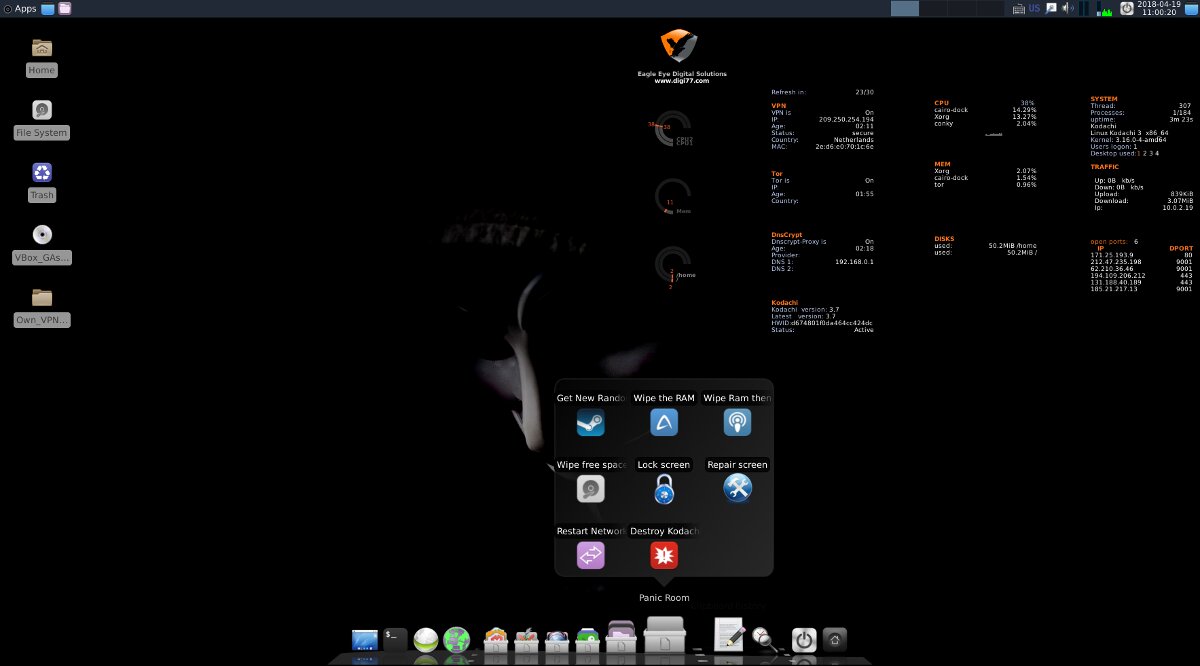
Kodachi runs from a USB flash drive like a typical live distribution (so it doesn’t leave traces on the local computer), but if you prefer, you can launch it in a virtual machine (assuming you trust the host OS). Either way, by default you log in as the user kodachi with the password r@@t00. To use sudo, enter the username root and the same password r@@t00.
MOFO Linux
This is a rapidly evolving, well-equipped Ubuntu-based OS. Out of the box, it includes SoftEther VPN and OpenVPN, along with an automatic scan that selects the fifteen fastest free servers (not necessarily the closest to you). It displays each server’s latency to you, latency to google.com, and available bandwidth.
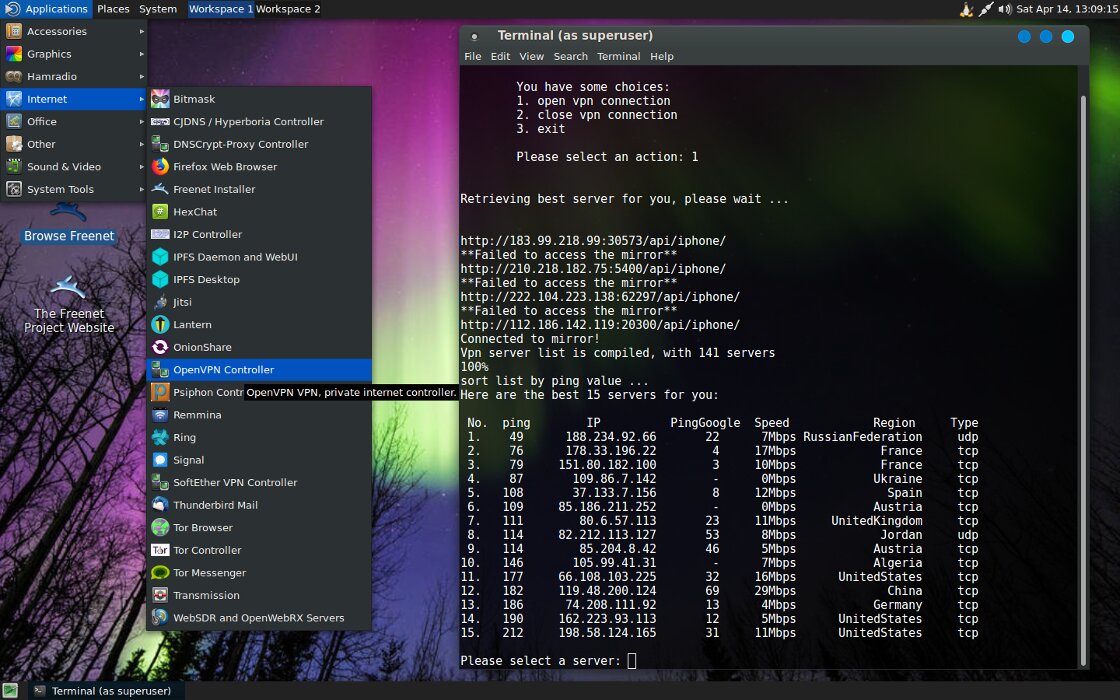
Beyond Tor and VPNs, MOFO also supports I2P, plus Lantern and Psiphon as fast proxy options. That said, Psiphon is a bit flaky right now, and Lantern’s free tier only includes 500 MB of unthrottled data per month—but you can always upgrade to a paid plan.
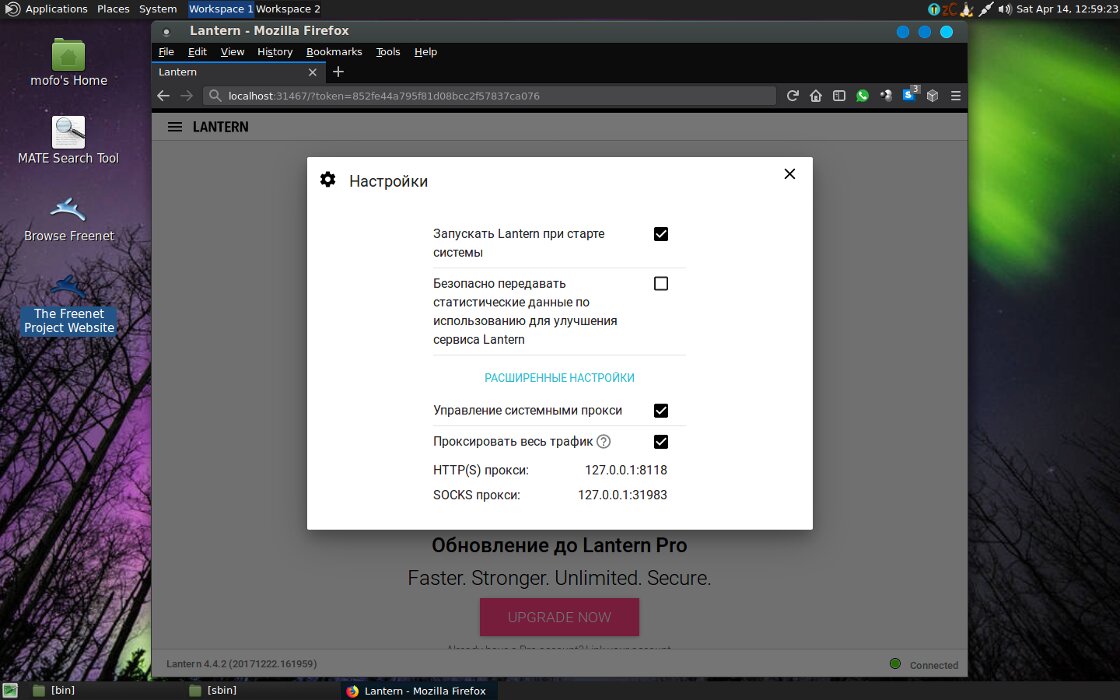
You can install the Freenet client—a peer-to-peer anonymous network with distributed storage of encrypted data—directly from the graphical menu in just a couple of clicks. It hosts its own sites and forums that are virtually impossible to censor.
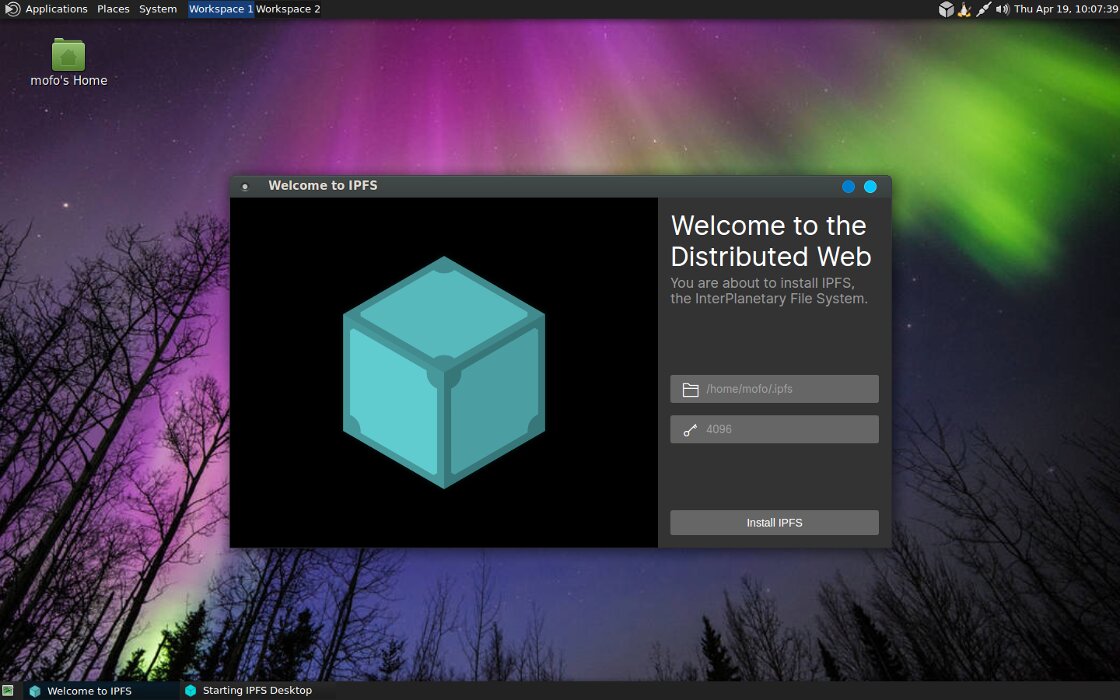
MOFO now includes a link to install support for the IPFS (InterPlanetary File System) distributed file system, built on P2P technologies. IPFS lets you share local files and host sites that won’t disappear due to censorship or blocking. MOFO also supports the Cjdns network protocol, which allows you to create a virtual IPv6 network with encrypted traffic.
MOFO secures personal data with eCryptfs, a stacked filesystem with on-the-fly encryption. It operates on top of an existing filesystem (ext3, ext4, or XFS) and doesn’t require a dedicated partition.
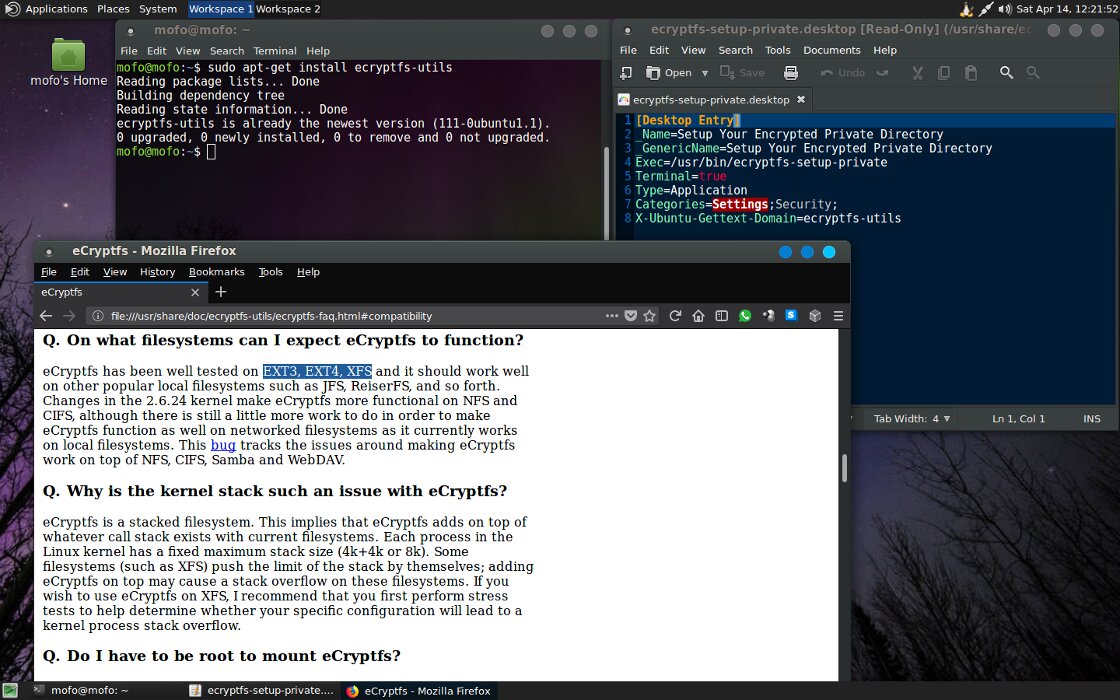
MOFO also comes with ZuluCrypt preinstalled, with support for TrueCrypt and VeraCrypt container formats.
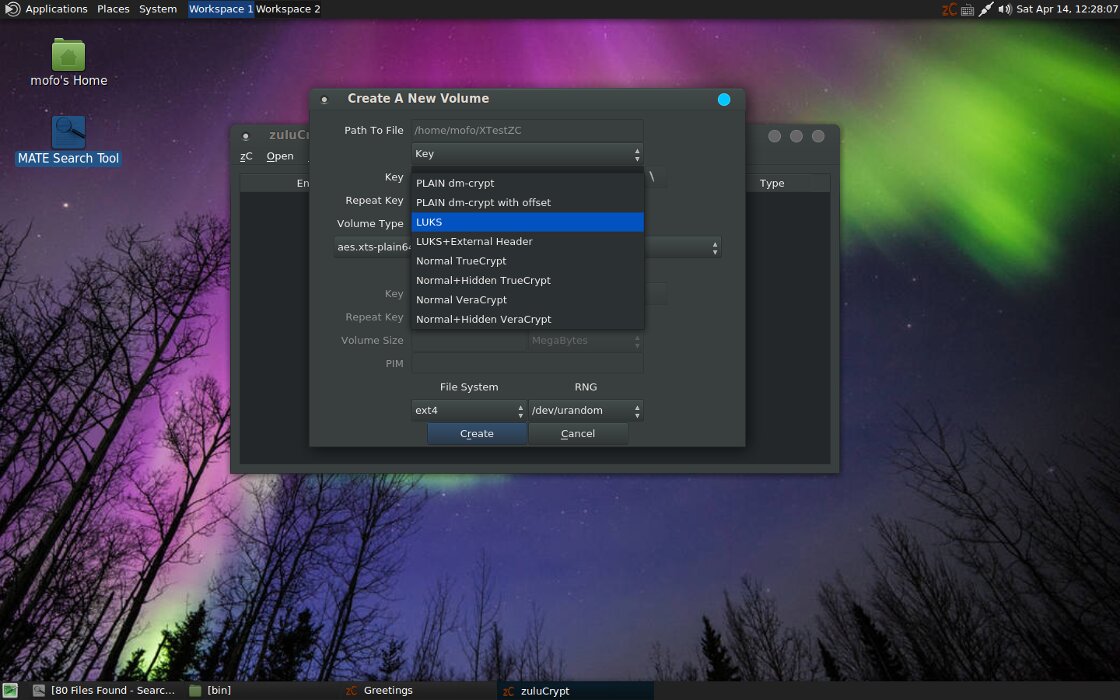
As of the testing date, the available release was mofolinux-6.0 from February 18, 2018. By default, the admin account has no password set.
Subgraph OS
We wrote about this OS in 2016, and not much has changed since. It’s still a very rough Debian fork that Snowden once praised for the idea but not the execution. The only thing that has noticeably changed in Subgraph is the list of preinstalled software.
The most recent release is the September 2017 alpha: сентябрьская альфа. It can run in live mode, but for full functionality you’re expected to install it to a hard drive.
A key feature of Subgraph OS is its Oz sandboxing framework Oz. It isolates selected applications from each other and from the base system using namespaces, and enforces restrictions with seccomp-bpf—much like the previously mentioned Firejail.
The Subgraph OS kernel is built with PaX/Grsecurity patches. These restrict access to files under /proc, enforce stricter chroot() isolation, provide a more advanced form of address space layout randomization (ASLR), mark the stack as non-executable, and regulate the allocation of network sockets.
Subgraph OS installs on an encrypted partition, includes controls to allow or block applications’ network access, and supports YubiKey hardware keys with one-time passwords (OTP).
Email is secured with PGP, and the built-in firewall routes all outbound connections through the Tor anonymity network.
The built-in Subgraph OS Instant Messenger is a fork of CoyIM that supports XMPP and routes traffic over Tor by default.
You can create anonymous file shares with OnionShare, and the tool works the same way on other Linux distributions as well.
At first glance, Subgraph OS seems solid—a genuinely respectable OS—but the reality is more complicated. Only certain apps run inside the built-in sandbox. There’s a predefined list of applications that are automatically sandboxed; the rest—including the GNOME desktop environment—run like regular applications, just as they would on any other Linux distribution.
This architecture opens up many ways to compromise the OS. For example, Tor Browser runs in a sandbox but has full access to the ~/ directory (so it can save downloaded files). If a vulnerability is found in the browser and an attacker figures out how to exploit it to run code, they could write anything to ~/, including a . file. A . file can embed arbitrary commands, which will execute when the user navigates to ~/ and clicks it. And because Subgraph OS uses Nautilus, a file manager that runs outside the sandbox, for filesystem navigation, that script would have access to the entire system.
In April 2017, Micah Lee and Joanna Rutkowska (creator of Qubes OS) took advantage of this oversight, carrying out a proof-of-concept hack of Subgraph OS. See their write-up: demonstration hack.
heads
The relatively new OS is called exactly that—heads, in lowercase. The FAQ offers a terse explanation from the developer: “Because I said so.” The rest of the answers aren’t much more informative. It’s a young project, fueled by pure enthusiasm, so the documentation is sparse.
As of this writing, the official site offered version 0.4, released on March 26, 2018. Technically, it’s a Devuan-based fork; Devuan itself is a fork of Debian that uses the sysvinit init system instead of systemd.
Heads supports only the i386 and x86_64 CPU architectures, so it isn’t suitable for mobile devices with ARM processors. For the graphical environment, Heads ships with the Awesome tiling window manager, which enables fast, keyboard-driven window management. As a more traditional option, Openbox is also available.
The toolset in heads is very minimal. There’s a browser, email, chat, a cryptocurrency wallet, and a handful of programs for working with different file types.
On the other hand, thanks to its lightweight design, Tor starts up very quickly, and the browser is ready to use almost immediately.
Heads’ key features are its deep Tor integration and its use of exclusively free software. All traffic—not just browser traffic—in Heads is routed through Tor. The Heads website is also accessible over Tor.
Additionally, Heads can spoof the MAC address at boot, and the Permakey kernel module will automatically shut down the OS if the boot USB drive is removed (useful if you need to leave quickly). You can disable this behavior by unchecking the corresponding options during startup. The administrator password is also set at boot.
By default, external drives aren’t auto-mounted. In Openbox, you can mount them by clicking the udiskie tray icon in the bottom-right panel. The OS is still in an early stage, so expect plenty of rough edges. Even finding drivers for GPUs, network adapters, and other hardware can be troublesome. If you’re lucky with your setup, heads will boot quickly into Live mode and route all application traffic through Tor.
Still, it’s not always necessary. For example, with HexChat you won’t be able to join many popular channels. They detect login attempts coming from Tor exit nodes and automatically kick you out.
Heads includes a very short list of Tor resources, but they’re easy enough to find on your own.
Tails
Tails (The Amnesiac Incognito Live System) is probably the most well-known operating system for anonymous web browsing and bypassing internet censorship. We’ve written about it many times, so we won’t dwell on it here. In particular, we’ve covered how to install Tails on a USB stick and how to use VirtualBox in Tails. For this roundup, we’re looking at the latest release 3.6.2 dated April 11, 2018.
Technically, Tails is an Irish fork of Debian (based on the stable branch) with GNOME as the desktop environment. Tails supports the Russian language, can configure various ways to connect to Tor, and randomizes the MAC address right at startup.
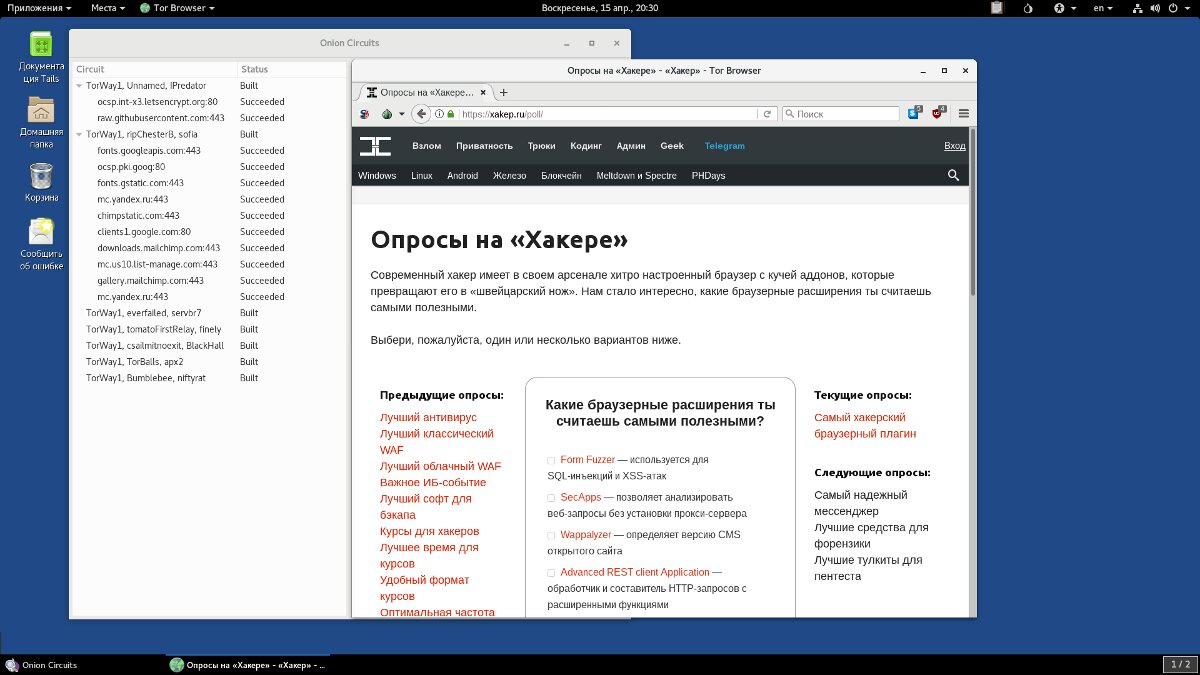
Automatic Tor configuration takes a few minutes, but it’s easy to monitor with Onion Circuits.
Tails updates come out regularly, and they’re mostly security patches. Each release turns up a slew of vulnerabilities, and a new version is pushed out quickly — all in keeping with a rapid release cycle.
Notably, Tails can detect when it’s running in a virtual machine and warns that in this case it can’t guarantee anonymity, since it can’t vouch for the security of the host OS.
Tails comes with a mid-sized set of preinstalled apps (it used to be very minimal), and you can always install anything from the Debian repositories. The catch is that downloading packages over Tor takes time, and all changes vanish when you end the session—unless you create an encrypted persistent storage on the USB using the built-in tool.
All data is kept in RAM and never written to disk to avoid leaving traces (unless you use encrypted persistent storage). On shutdown, Tails overwrites RAM with random data to mitigate cold boot attacks. It also includes a failsafe for sudden USB removal and MAC address randomization for the network interface (works with external adapters too). All network traffic, including DNS queries, is routed exclusively through Tor.
Tails comes with the Gobby tool for anonymous, real-time collaborative editing. It supports Unicode, syntax highlighting for popular programming languages, and color-coding for text added by different users. Versions are also available for Windows and macOS.
Despite its age—the project is nearly nine years old—Tails is still prone to odd glitches. For example, when reading news in Liferea, its search results sometimes vanish from the screen, or all running applications abruptly terminate. It’s intermittent, and we haven’t been able to correlate it with any specific actions yet.
Whonix
Arguably the most nontrivial OS in today’s roundup. It ships as prebuilt virtual machines (.ova) and is split into two interlinked components.
The server component is called Whonix-Gateway, and the client is Whonix Workstation. The latest stable release was published on May 31, 2016. By default, Whonix uses the username user and the password changeme.
To use Whonix, download both virtual machines, import their configs into VirtualBox, and start them in order, beginning with the Gateway. They don’t require many resources; the optimal defaults are already set.
The rest of the configuration is handled by a wizard in just a few clicks. You won’t need to touch the command line.
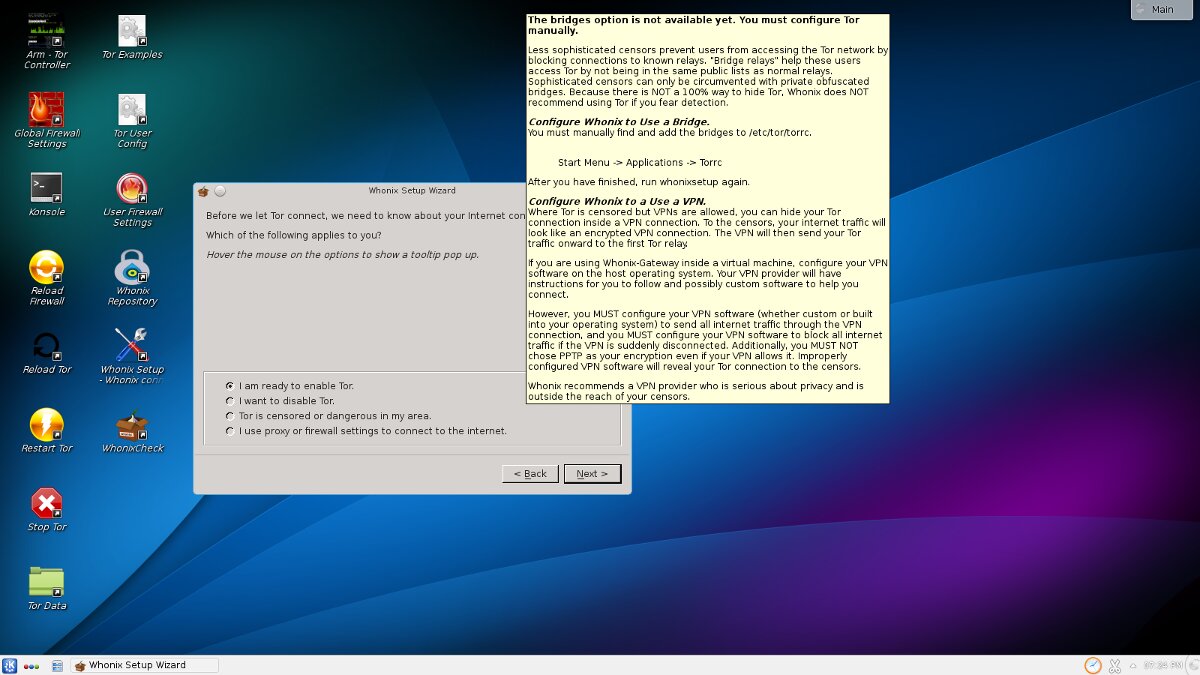
The server-side component will handle routing through Tor and VPN, process DNS queries, and filter network packets.
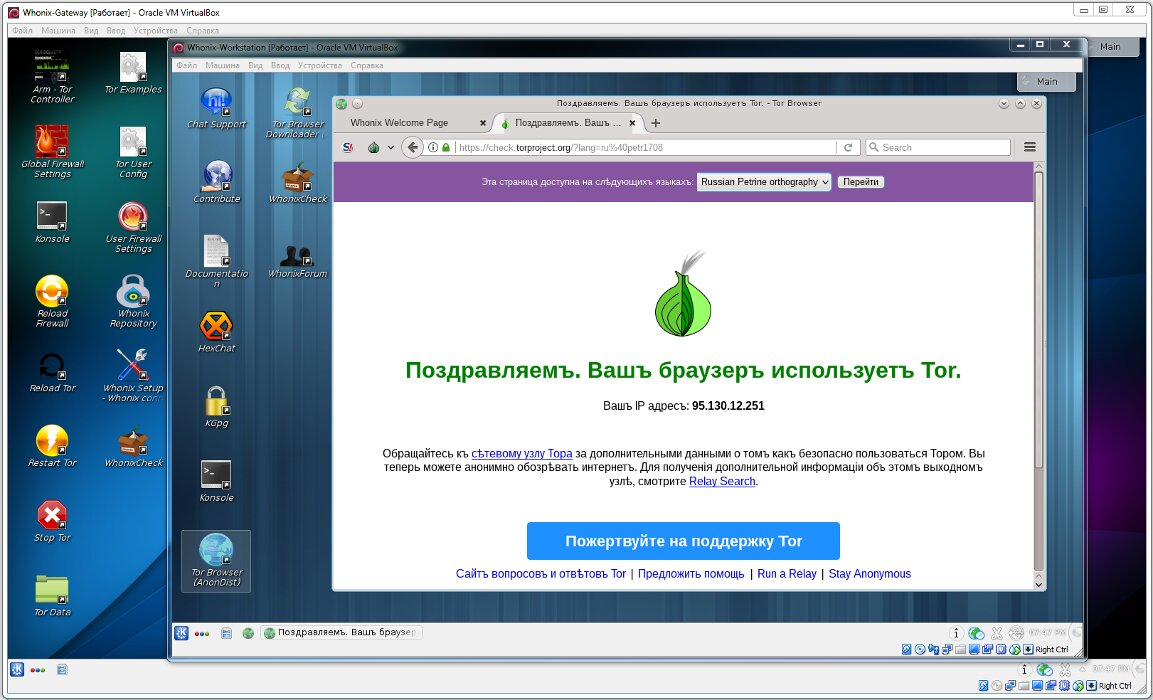
This setup keeps all user data confined to one virtual machine, while the machine exposed to attacks is the Gateway. It also addresses the well-known deanonymization issue: there’s no risk of your real IP leaking due to DNS leaks or routing glitches.
Even if the Whonix gateway gets compromised, the attacker won’t learn your IP address or reach your documents and Bitcoin, since they’re kept in the separate workstation (client) VM.
Whonix’s preinstalled software is fairly standard: Tor Browser; messaging apps Tor Messenger, Tox, and Ricochet; Mozilla Thunderbird with the TorBirdy add-on and PGP support; secure file transfer via SCP (RCP over SSH); and various system utilities. See the full, categorized list here: https://www.whonix.org/wiki/Software
As with any virtual machine, Whonix’s security ultimately depends on how well-protected the host operating system is. You can run it on computers with Windows, macOS, or Linux.
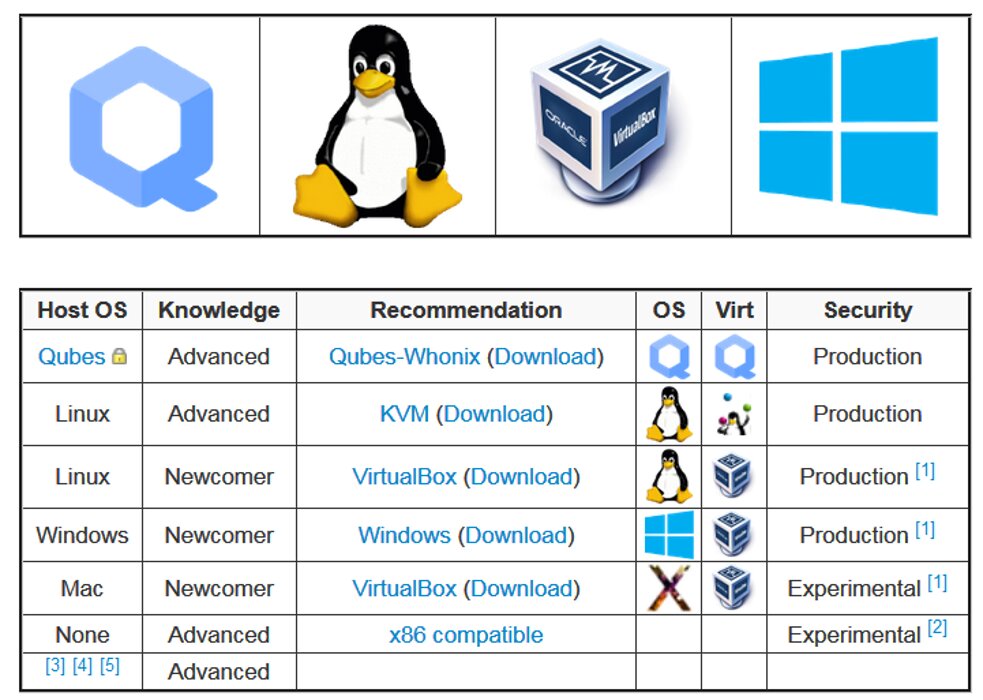
One of the most reliable options is running Whonix inside Qubes OS on trusted hardware with known-good (reference) firmware. Qubes is a security-focused OS developed by Joanna Rutkowska that uses the Xen hypervisor. It isn’t a live distribution and therefore isn’t covered in this review. However, its fundamental design has been discussed previously in the pages of Hacker magazine.
Conclusion
Among the operating systems for anonymous web browsing and bypassing internet censorship, some are heavily promoted (Tails, Subgraph OS) but not very user-friendly, while others are less well-known yet more capable (MOFO, Kodachi). I recommend focusing on the latter when choosing a live OS.
This review excludes distributions whose development has been dormant for two years or more. That includes JonDo, Sabayon Linux, the NSA‑blessed TENS, Discreete Linux, IprediaOS, and many others. That doesn’t mean they’re bad—just that more current options are available now, and at this point it feels like everyone has spun up their own “anonymous Linux” fork.