The world has seen plenty of attempts to build a secure smartphone: from Blackphone, which promised end-to-end encrypted communications, to the rather dubious BlackBerry Priv, and even the GATCA Elite, whose creators didn’t bother to innovate and…
CONTINUE READING 🡒 Category: Mobile
What Data Android Phones Secretly Send to Google and How…
It’s no secret that our phones know way too much about us. And as long as your device is with you, it’s hard to find a moment when some piece of data about what you’re doing isn’t…
CONTINUE READING 🡒 Google’s Fuchsia OS: Inside the Next‑Gen Android Successor
The source code for Google’s mysterious new OS first surfaced online in August 2016. By May 2017, it had gained some documentation and an alpha-stage user interface. Today, Fuchsia is well-documented and under active development—not just an…
CONTINUE READING 🡒 iOS 12 Jailbreak Tutorial: Step-by-Step Guide
No doubt about it: the iPhone is a very convenient device, especially for anyone who’s fully moved into the Apple ecosystem. But iOS has one quirk that can really get on iPhone owners’ nerves—and make Android fans…
CONTINUE READING 🡒 The BlackBerry We Lost: A Retrospective on One of the…
By 2017, the mobile OS market had effectively become a duopoly: Google versus Apple, with Android firmly outpacing iOS across most markets. But just a few years earlier, things looked different. Microsoft’s Windows Phone was doing reasonably…
CONTINUE READING 🡒 Android: Island app to isolate and freeze apps — no…
On Android, it’s all too easy to pick up malware. But what if you still have to install a sketchy app? Don’t sweat it—Island lets you not only keep that app away from your data, but also…
CONTINUE READING 🡒 The Problems with Xiaomi’s MIUI
MIUI is a great OS and a prime example of how far you can push Android if you want to turn it into something more. And, paradoxically, for that very reason it’s also a bad OS—one that…
CONTINUE READING 🡒 Samsung Stock Firmware Modding Guide: Root Access, System Tweaks, and…
Samsung smartphone firmware comes packed with features and settings. However, some of them are hidden, and many handy capabilities you’d find in custom ROMs are simply unavailable. On top of that, the firmware includes plenty of preloaded…
CONTINUE READING 🡒 What Hackers Can Do with Your iPhone Passcode: Data Theft,…
Over the past few months, we’ve written a lot about what’s new in iOS 11. “Now we’re really set!” we thought. We were wrong. With iOS 11, Apple not only introduced new security mechanisms but also weakened…
CONTINUE READING 🡒 Root Access on Recent Android Versions: What You Need to…
We cataloged the most common ways to get superuser access on current Android builds; unpacked the differences between SuperSU, phh SuperUser, Magisk, KingRoot, and KingoRoot; tested various methods of hiding root; examined Android 7’s security model and…
CONTINUE READING 🡒 Android: 8 Universal ROMs, Modern Click Bots, App Hacking, and…
In this issue: universal Android 8 ROMs, multi-headed trojans and chatbots, clickbots, abusing Android notifications, breaking into apps via trusted components, and of course a quick network pentest—how to make apps trust us. We didn’t forget coding…
CONTINUE READING 🡒 Android for Linux Users: Integrating Your Smartphone with Linux
Android and Linux distributions aren’t just related OSes—they share the same kernel and are very similar under the hood. Most Linux commands work on Android; you can install bash, write scripts, and even run servers. Set up…
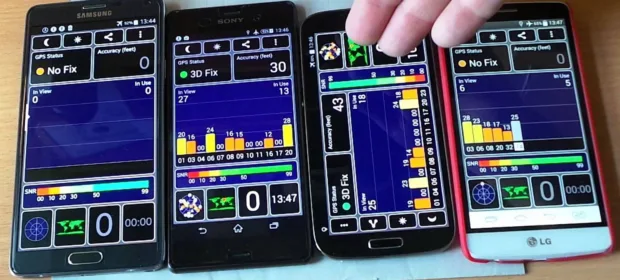
CONTINUE READING 🡒 How to Test and Improve GPS Signal Quality on Android
If you often find your phone struggles to get an accurate GPS fix, don’t rush to blame the navigation app. The problem is usually with GPS signal reception and satellite acquisition. You can test the receiver’s performance…
CONTINUE READING 🡒 Android SQLite Database: Quick Integration Guide
Android apps can store large amounts of data in a private, app-specific database—hidden from prying eyes. You’ll be surprised how useful this is and, more importantly, how easy it can be.
CONTINUE READING 🡒 3 Reasons to Skip the Latest Android Updates
For power users and app developers, Android has long been a very comfortable platform. Open-source code, rich capabilities, and the absence of heavy-handed control from Google made an Android smartphone a true pocket computer. But times change,…
CONTINUE READING 🡒 Hiding Sensitive Data in Android Apps: Techniques for Storing and…
At some point, almost every developer has had to hide data inside an app. This could be encryption keys used to decrypt parts of the program, API endpoint URLs, or strings you’d rather conceal to make a…
CONTINUE READING 🡒 How to Reduce Mobile Data Usage on Android: Practical Tips…
Cellular networks are delivering ever-faster Internet access, and mobile devices keep consuming more data. But mobile Internet is still far from cheap: plenty of users are still on plans capped at 4 GB, and when you travel,…
CONTINUE READING 🡒 Is Google Building an Android Successor?
In April of last year, without any fanfare, Google quietly published the source code for a new OS called Fuchsia, written in Dart. Because Fuchsia was built on a tiny microkernel, the knee‑jerk reaction from journalists and…
CONTINUE READING 🡒 Why End-to-End Encryption in Signal, WhatsApp, Telegram, and Viber Won’t…
Encryption in messaging apps became popular because it happens entirely behind the scenes. Users don’t have to generate key pairs, sign them, or revoke old and compromised keys on their own—everything is handled automatically, and the conversation…
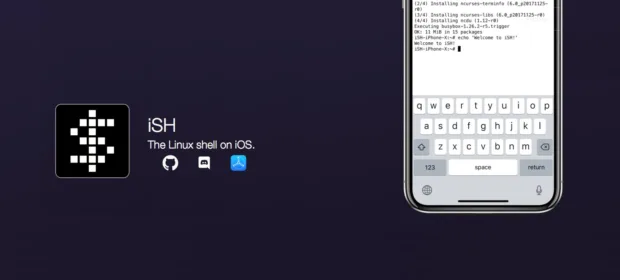
CONTINUE READING 🡒 iSH: A Pocket Linux Environment for iOS
Apple’s restrictions on iOS and its apps haven’t stopped people from trying all sorts of things with the system. iSH is one of the latest attempts to shoehorn a Linux shell onto the platform, and it runs…
CONTINUE READING 🡒