Useful Stuff
- Cloak-And-Dagger — source code for a Cloak & Dagger–style overlay attack; a keylogger implemented via SYSTEM_ALERT_WINDOW.
- personal_script — a collection of custom scripts for IDA Pro, Frida, Burp Suite, and 010 Editor.
- krackattacks-scripts — scripts for testing devices and access points for the KRACK vulnerability.
- Evil-Droid — a tool for injecting malicious code into Android applications.
- Droidefense — a malware analysis tool that leverages multiple utilities to dissect APKs.
Recommended reading
Project Treble and the Evolution of the Linux Kernel
Project Treble Brings Extended Linux Kernel Security Support to Combat Fragmentation — an interesting look at how Google is using Android to reshape the broader Linux ecosystem and Linux-based devices.
The gist is that the Linux kernel has special LTS releases with a two-year support window. They don’t get new features, but bug fixes continue to land. These LTS releases are used by server distro maintainers (since a major kernel upgrade can break things) and by Android device makers—more precisely, SoC vendors—because porting a new kernel to a given SoC is anything but trivial.
So, Google has reached an agreement with the Linux Foundation to extend LTS kernel support from two years to a full six. This means we can expect better device support from manufacturers (they won’t have to fix bugs in already end-of-life LTS kernels themselves), as well as improved support for other Linux-based hardware—routers, smart bulbs, and other IoT gear. And of course, it’s a very positive sign for developers of server editions of Linux distributions.
Universal Android 8 ROMs
A Revolution in Custom ROMs: How Project Treble makes Porting Android Oreo a 1 Day Job — an interesting article about how Project Treble simplifies porting custom ROMs to devices.
Recall that Project Treble is a Google initiative to modularize Android’s internals by cleanly separating the OS into two independent parts: one that includes the kernel, drivers, and other hardware support components (the vendor layer), and the other being the Android OS/framework itself.
The idea is that the interface between these two components should be strictly defined and remain stable over time. This would make it much faster to bring new Android releases to older devices: in theory, there’s nothing to port at all—you just take the image of the new Android version and flash it onto the device.
We haven’t really seen it in practice yet—the groundwork for Treble first appeared in Android 8, the latest OS version at the moment. Still, several different smartphones are already running Android 8 with markedly different builds. What if you just took the Android image from one phone and ran it on another? Would Treble help with that?
Turns out, yes. XDA user phhusson built an Android image in just twenty hours that boots on multiple devices without any modifications: Huawei Mate 9, Honor 8 Pro, Honor 9, Sony Xperia XZ1 Compact, and the Essential Phone—spanning three manufacturers and two different chipsets (HiSilicon Kirin 960 and Qualcomm Snapdragon 835).
This means that in the future, instead of a huge number of device-specific builds of a custom Android ROM (each taking dozens of hours to port), we’ll have a single universal build you can install on any smartphone. Think Linux or Windows: download it from a website and install it on any phone.
Multi-headed Trojan on Google Play
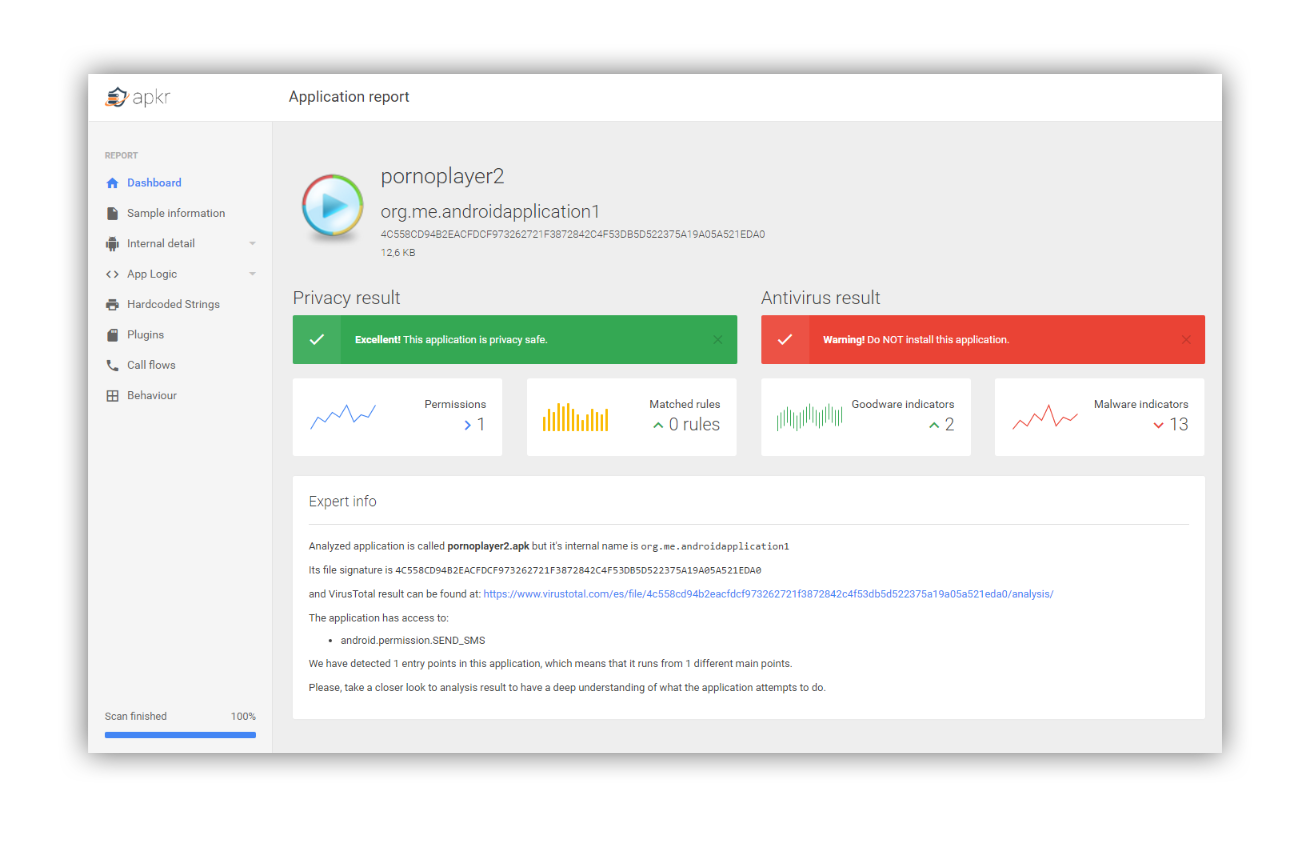
Multi-stage malware sneaks into Google Play — an analysis of the Android/TrojanDropper.Agent.BKY Trojan, which hides from antivirus tools and Google Play’s security checks by splitting its operation into multiple stages.
Right after launch, the trojan silently decrypts, extracts, and runs its first stage, which then decrypts and runs the second. That stage, in turn, downloads a new app from a specified URL and triggers its installation. If the user agrees to install and run the APK (which masquerades as Adobe Flash Player), the fourth stage is decrypted and executed.
The fourth stage is a classic banking Trojan that displays on‑screen overlays to steal users’ credentials.
Interestingly, because the fourth stage was delivered via a bit.ly short link, the researchers were able to see how many times it was accessed—about 3,000.
Android Clickbots
Clicking Bot Applications is an in-depth article about click fraud in the Android ecosystem—specifically, malicious apps that compromise phones to covertly click on ads. It examines two types of such apps: those that abuse Accessibility services to gain the ability to tap any UI element, and those that use the ViewGroup. API, which lets an app “click” its own UI elements—that is, the ads it displays itself.
The second type is the simplest and most primitive. An ad network can easily detect it by analyzing click frequency, which parts of the ad are tapped, and how those taps “look”: pressure, touch area, press duration, and so on.
The app, in turn, can try to fool the ad network: it can save the parameters of the user’s most recent tap and reuse them for an ad click, while also randomizing the click timing. It can additionally choose which ad network to engage with and which ones to leave alone.
Example of capturing user click data in the com.life.read.physical.trian Trojan:
public class MainActivity extends SlidingFragmentActivity implements View.OnClickListener, View.OnTouchListener {
public boolean onTouch(View view, MotionEvent motionEvent) {
if(motionEvent.getAction() == 0) {
ClickSimulator.getMotionEventInfo(((Context)this), motionEvent);
}
return 0;
}
public class MotionEventInfo {
public static MotionEventInfo setInfo(String name) {
MotionEventInfo options;
try {
options = new MotionEventInfo();
JSONObject JSON_Obj = new JSONObject(name);
options.deviceId = JSON_Obj.optInt("de");
options.pressure = JSON_Obj.optDouble("pr");
options.size = JSON_Obj.optDouble("si");
options.xprecision = JSON_Obj.optDouble("xp");
options.yprecision = JSON_Obj.optDouble("yp");
options.metaState = JSON_Obj.optInt("me");
options.edgeFlags = JSON_Obj.optInt("ed");
}
catch(Exception ex) {
options = null;
}
return options;
}
}
}
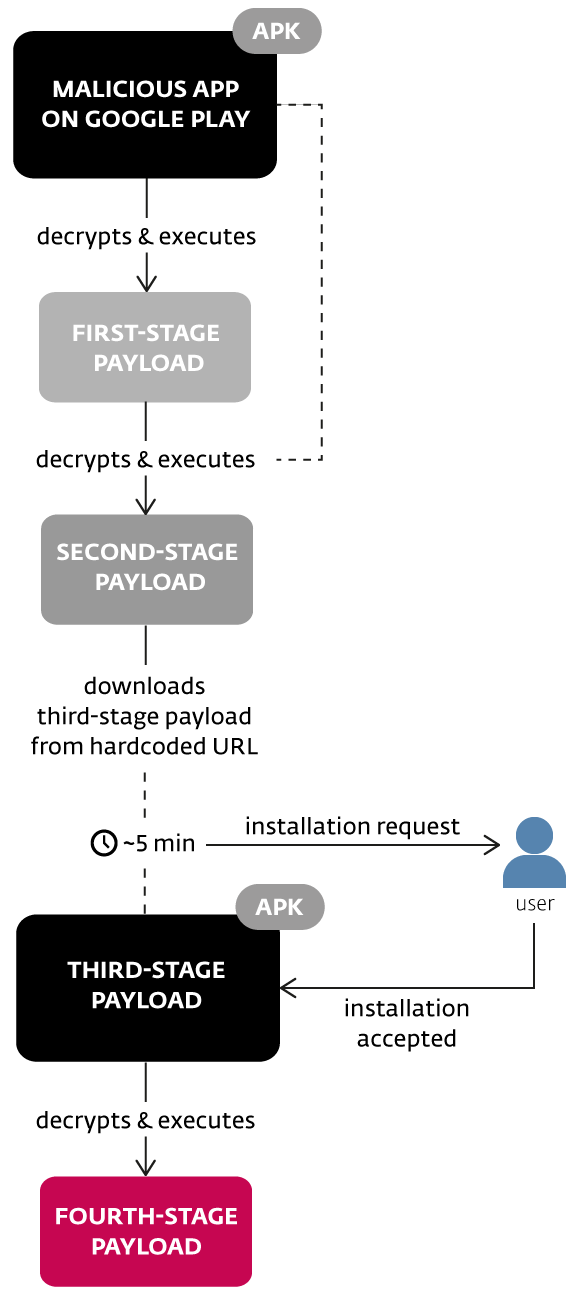
The first type of click-fraud apps abuses the Android Accessibility Service, which lets them inspect the UI and simulate taps on almost any part of any app—or even the system itself. These apps can also earn money for their operators by installing promoted apps (installation fraud).
However, these clickbots have a drawback: they either need to somehow trick the user into enabling their Accessibility service, or use the Cloak & Dagger attack to turn it on stealthily. Fortunately, few malware developers know how to pull off that attack.
Malware Using Toast Overlays
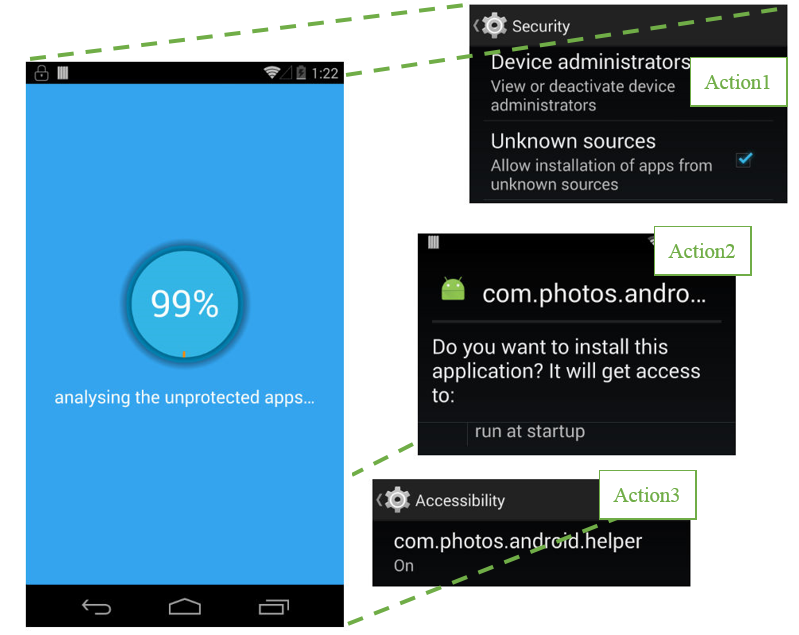
Toast Overlay Weaponized to Install Several Android Malware — an article about the ANDROIDOS_TOASTAMIGO malware, the first Trojan to use a Toast overlay attack to silently install apps on a smartphone without the user noticing.
Toast overlay is an attack that exploits a quirky Android vulnerability allowing a full-screen window to be embedded inside the small toast notification window meant for brief messages. A trojan uses this overlay to cover the screen while it opens Settings in the background and tricks the user into tapping specific spots—taps that pass through the overlay—thereby enabling the Accessibility service.
Then, using a similar trick, the trojan enables the “install from unknown sources” setting, downloads and installs another piece of malware on the device, and kills antivirus apps. The downloaded payload is a clickbot. Notably, it can establish a connection through a proxy server to bypass regional restrictions on the availability of the AdMob and Facebook ad networks.
Note that the Toast overlay vulnerability was fixed in the September Android update.
Hacking Android Apps via Exported Components
Hack Android Application Through Exposed Components — a solid introductory article on hacking Android apps via exposed (exported) components: activities, services, broadcast receivers, and content providers.
The article explains the purpose of each component and then, using a vulnerable app, demonstrates how to disassemble the app with apktool and then use Drozer to identify exported components.
One example is to launch a hidden Activity directly to view the list of saved apps.
adb shell am start -n <package_name>/<activity_name>
Inside the iOS Backup Format
Reverse Engineering the iOS Backup — an exploration of the iOS backup format. No revelations—just a catalog of files, their contents, and their purpose. Worth bookmarking for when you need it.
Spoiler: practically the entire backup is just .plist files you can open in a regular text editor and SQLite databases you can browse with any database manager.
How to Make Apps Trust Rogue Certificates
Bypassing Android’s Network Security Configuration — how to bypass an app’s default Network Security Configuration to conduct a penetration test.
Android 7 introduced a mechanism called Network Security Configuration. It lets developers adjust network security settings via a dedicated XML file inside the APK. The same mechanism makes all apps targeting Android 7 or higher trust only the system certificate store, which means you can’t simply install your own CA certificate to intercept and analyze their traffic.
The author suggests two ways to solve this: rebuild the app with a custom security config, or use Frida to modify how Android treats the app on the fly. The former is much simpler, but it won’t work if you need to preserve the app’s original signing certificate (for example, when two apps share the same private directory).
Configuration that makes the app trust user-installed certificates:
<?xml version="1.0" encoding="utf-8"?>
<network-security-config>
<base-config>
<trust-anchors>
<certificates src="https://hackmag.com/wp-content/uploads/2025/09/13344_system"/>
<certificates src="https://hackmag.com/wp-content/uploads/2025/09/13344_user"/>
</trust-anchors>
</base-config>
</network-security-config>
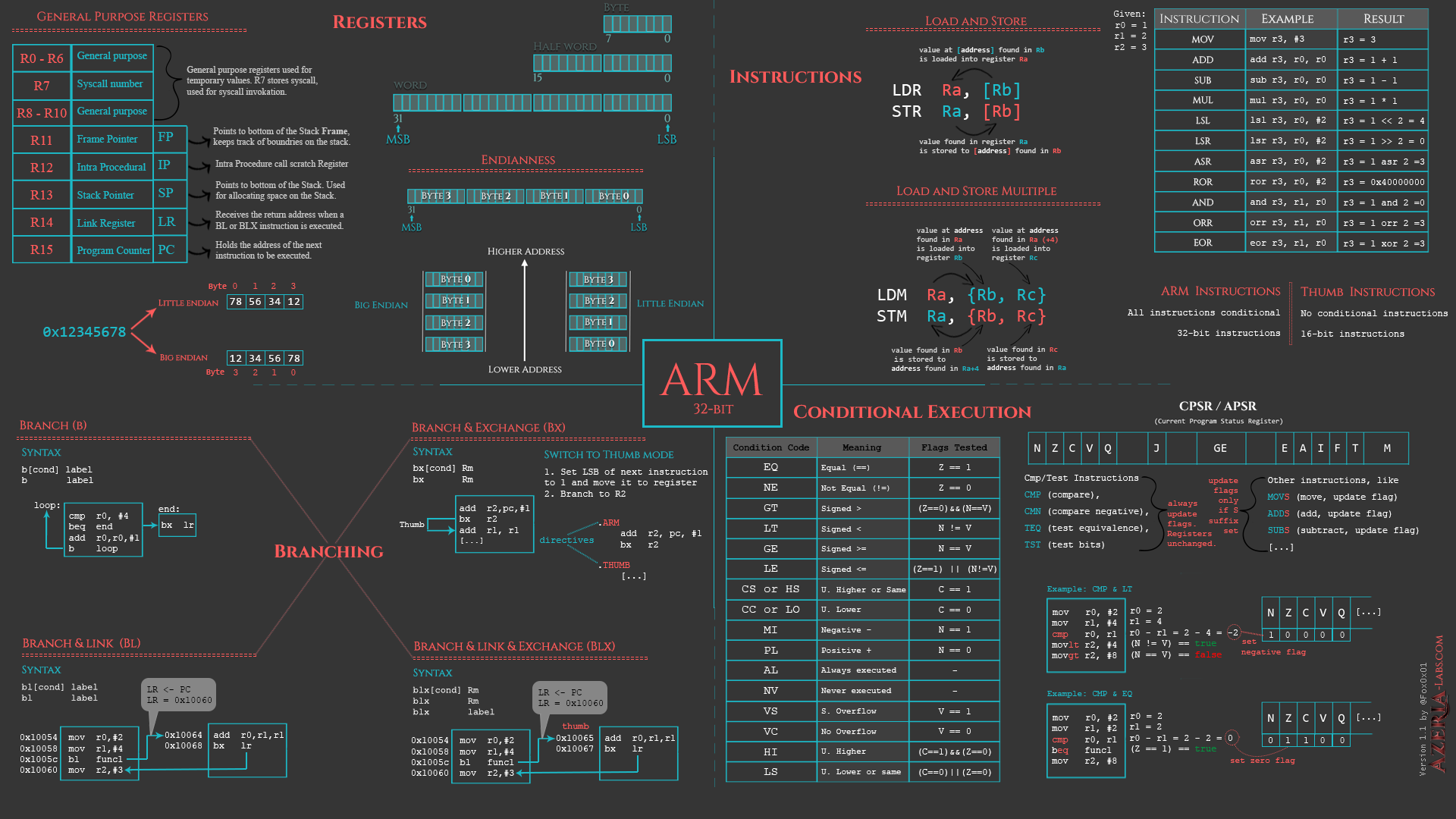
ARM Cheatsheet
Download
LineageOS for microG is a LineageOS build (a custom Android ROM) with microG services and the F-Droid app store built in. Its appeal is that it lets you access Google services without installing Google’s own services on your phone.
Why is this necessary? Simple: if you flash a stock LineageOS build on your smartphone, you won’t have access to the Play Store or Google Maps, and apps won’t be able to receive push notifications. To make all of that work, you need to install the GApps package, which includes Google services.
The problem is that even the minimal GApps package is over 120 MB, and the full package exceeds 700 MB. The Google services bundled with GApps are also notorious for their appetite for RAM and battery life. On top of that, they’re closed-source, so only Google knows exactly what they do.
microG, on the other hand, is open source, only about 4 MB in size, doesn’t drain the battery, and uses hardly any RAM. People say you can even run the Play Store on microG, but I haven’t verified that myself.
Programming
Google and Kotlin
Update on Kotlin for Android — Google announced three important Kotlin-related updates.
- They published a Kotlin coding style guide: https://android.github.io/kotlin-guides/style.html. Nothing particularly novel—mostly the same advice as for Java: always use braces with if, put a space after if/for/catch, don’t insert a space between an object and its method call, etc.
- They’ve ported some of their sample apps to Kotlin: https://developer.android.com/samples/index.html?language=kotlin
- They added nullability annotations in Support Library version 27, so Kotlin developers can now tell whether values returned by Google’s standard libraries are nullable or not.
Lesser‑Known Kotlin Features
Advanced Kotlin tips — another roundup of interesting but non-obvious Kotlin features. We covered some of them in the previous installment: local, infix, and inline functions, and labeled returns. New this time:”
- The keyword
tilereclets you tell the compiler that the following function calls itself and only itself (in other words, it’s recursive). This enables optimizations that replace the method call with a loop: - Operator overloading. No comment.
Simple tips for writing better code
Simple but painful steps for writing a better code — four extremely simple yet effective tips.
Tip #1: Stop instantiating objects inside helper classes. For example, the class below is impossible to test:
class VehiclesManager(val context: Context) {
fun getVehiclesNextToMe(): List<Vehicle> {
val api = VehiclesRetrofitApi(context)
val currentLocation = LocationProvider.currentLocation()
return api.getVehicles()
.filter { it.coordinates.distanceTo(currentLocation) < 100 }
}
}
It doesn’t need a Context (it needs a VehiclesRetrofitApi instance). It’s tightly coupled to the Retrofit library. The correct version:
class VehiclesManager(val vehiclesApi: VehiclesRetrofitApi) {
fun getVehiclesNextToMe(): List<Vehicle> {
val currentLocation = LocationProvider.currentLocation()
return vehiclesApi.getVehicles()
.filter { it.coordinates.distanceTo(currentLocation) < 100 }
}
}
Tip #2: Don’t call singletons directly. Pass them into class constructors as parameters.
Tip #3: Stop naming your classes Manager, Handler, Controller, or Processor. Those words add no real meaning; without them, the class name will be clearer.
Tip #4: Stop overusing subclasses. In many cases, this makes the code less readable and harder to understand.
10 Android Libraries You Should Definitely Try
10 Awesome Android libraries you definitely want to try. Honestly, this is one you need to experience firsthand—those animated screenshots are worth it—but here’s a quick rundown:
- Lottie — renders Adobe After Effects animations natively on Android.
- StyleableToast — a library for customizable Toast messages.
- CoordinatorTabLayout — a TabLayout/CoordinatorLayout hybrid.
- Material About — a polished “About” screen.
- SlidingRootNav — a side drawer with a slick reveal effect.
- InfiniteCycleViewPager — a ViewPager with an infinite cyclic scroll effect.
- JazzyViewPager — another ViewPager with various page transition effects.
- Side-Menu.Android — a side menu for category selection.
- AwesomeBar — an ActionBar/Drawer combo with smooth animations.
- ShimmerRecyclerView — a RecyclerView that shows a shimmer placeholder while loading items.
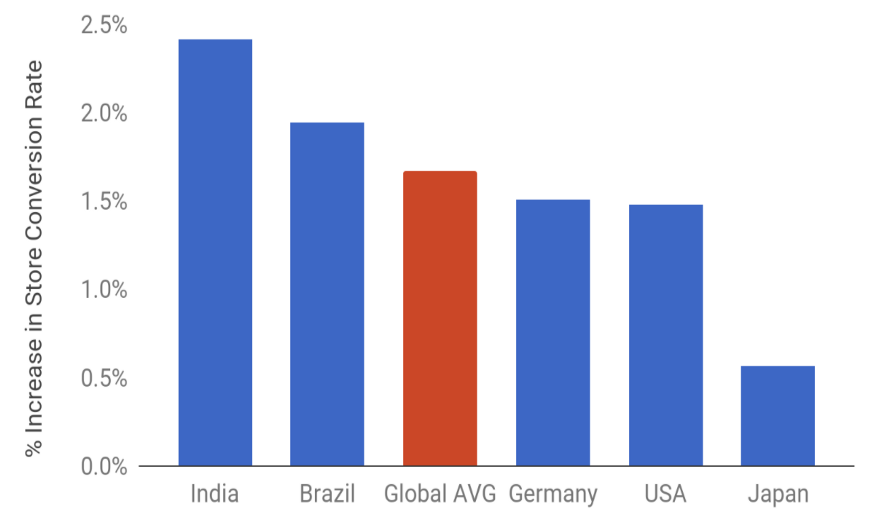
How App Size Affects Installs
Shrinking APKs, growing installs is an interesting study on how app size affects users’ willingness to install. The authors found that every additional 6 MB leads to a 1% drop in installs. And for a 100 MB app, about 30% of the losses come not from people deciding not to install in the first place, but from users canceling after the installation has already started.
First and foremost, these results stem from the lack of reliable, high‑quality internet access in many parts of the world. For example, in India and Indonesia only 50% of smartphone users have access to Wi‑Fi. In African countries, the share is even lower.
Android 4.0–8.1 Changelog
AndroidSDKPoster — a giant wall poster charting changes in the Android SDK from versions 14–27. Viewing it online is pointless—you’ll want to print the PDF and hang it on the wall. Available sizes: A0 and A1.
Libraries
- Time — a simple Kotlin library that lets you write 10.seconds instead of 10 * 1000, as well as 10.hours, 5.minutes, and so on.
- DownZ — an HTTP library with JSON and image caching, plus cancellation for image downloads and uploads.
- RippleLayout — a layout that creates a water ripple effect when you touch any part of it.
- FastTextView — a faster, more flexible alternative to TextView.
- android-extensions — a set of extension functions for more efficient Kotlin development.
- circle-menu-android — a beautifully animated circular menu.
- CircularDialogs — animated circular dialogs.
- Serial — a fast, efficient object serialization library (by Twitter).
- PRDownloader — a file downloader with pause, resume, and concurrent downloads.
