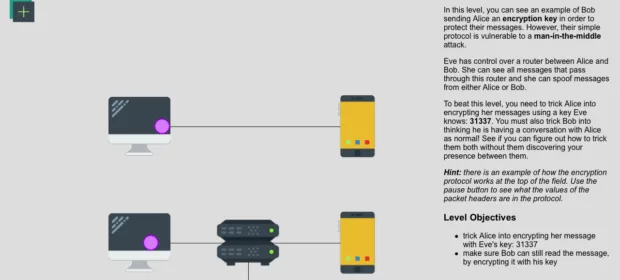
If you’re just getting into hacking, it helps to learn how networks work and what the basic attack types look like. If you feel shaky on the topic and want to walk through common scenarios in detail…
CONTINUE READING 🡒 Category: DevOps
How to Discover Neighboring Cisco Devices Using Cisco Discovery Protocol…
Cisco Discovery Protocol (CDP) is a Cisco‑proprietary protocol that allows network devices to advertise information about themselves and their capabilities, and to receive information about neighboring devices.
CONTINUE READING 🡒 What Is IPAM? How It Streamlines IP Address, DNS, and…
As a corporate network scales from a small LAN with a dozen machines into a sprawling infrastructure, an admin can run into all kinds of issues. Misconfigurations—especially when IP address management isn’t automated—and service disruptions become a…
CONTINUE READING 🡒 Active Directory Audit: How to Find Inactive User Accounts by…
Once a domain has more than a few hundred users, keeping track of everyone gets tough. If the domain structure is complex and managed by multiple admins, it’s even harder. Throw in departures, promotions, lateral moves, and…
CONTINUE READING 🡒 Building an Open-Source SIEM for Log Analysis: Tools, Architecture, and…
Even a small organization can have a variety of security tools, and their log formats can differ significantly, complicating operations. In this article, I’ll show how to use free and open-source software to structure and normalize logs…
CONTINUE READING 🡒 Deploying Snort IDS and Writing Intrusion Detection Rules
Attackers can compromise even the most hardened systems, and administrators may go months without noticing an intruder who has gained a foothold and is exfiltrating data. To prevent this and detect attacks, there are intrusion detection systems…
CONTINUE READING 🡒 Firewall Level 2: Configuring a MikroTik Router to Block Common…
In this article, we’ll cover how to harden a MikroTik router against attacks and port scans, and how to keep your network off blocklists. The techniques you learn here will also help you configure other types of…
CONTINUE READING 🡒 How to Set Up Zentyal 5.0: Free All‑in‑One Linux Server…
I was once asked to provision and configure a server remotely for a small company with about 30 workstations. I went with Zentyal—an Ubuntu-based distribution purpose-built for servers in small and medium-sized corporate networks. I’ll use this…
CONTINUE READING 🡒 MikroTik Router Firewall Configuration: Step-by-Step Guide
The firewall is the first—and, unfortunately, in many cases the last—line of defense for a network. The internet is full of advice on how to configure it, but blindly copying someone else’s rules can do more harm…
CONTINUE READING 🡒 Understanding Active Directory Terminology: Navigating the Forest and Trees
Upon first encountering terms like "forest," "trees," and related "trust relationships," it's natural to feel a bit intimidated. The same goes for Active Directory itself, which has a reputation for being one of Microsoft's most complex technologies.…
CONTINUE READING 🡒 Wazuh Guide: Perimeter Security and Protection Strategies
Today, I'm going to talk about my experience working with Wazuh—an open-source platform that combines the features of SIEM and XDR. This is a flexible system that easily adapts to various tasks, from safeguarding Active Directory and…
CONTINUE READING 🡒 Checklist: Essential Steps After Purchasing a Virtual Linux Server
A virtual server is suitable for handling a wide range of tasks, especially since renting one is quite affordable. If you're using a VDS, make sure to review this quick checklist after purchasing a virtual server. Ignoring…
CONTINUE READING 🡒 Setting Up a Free and Simple Monitoring System with Netdata
You might have a server, router, or some other device that needs monitoring. How can you set up a monitoring system that doesn't demand attention or resources on its own? In these cases, I recommend using a…
CONTINUE READING 🡒 Enhancing Event Auditing in Windows with Sysmon for Security Experts
Technical specialists who have tried to find crucial information in the log files of Microsoft Windows operating systems, either when investigating cybersecurity incidents or troubleshooting issues, know that event audit logs do not always capture all the…
CONTINUE READING 🡒 Setting Up the ELK Stack: Configuring Elasticsearch, Logstash, and Kibana…
Service and application logs are often the only way to identify the source of issues, but they are usually neglected after installation and debugging. Modern approaches to development, deployment, and maintenance of applications demand a completely different…
CONTINUE READING 🡒 What Challenges To Overcome with the Help of Automated e2e…
This is an external third-party advertising publication.
CONTINUE READING 🡒 Dangerous developments: An overview of vulnerabilities in coding services
Development and workflow management tools represent an entire class of programs whose vulnerabilities and misconfigs can turn into a real trouble for a company using such software. For a pentester, knowledge of these bugs is a way to successful exploitation; while for an admin, it’s a great opportunity to enhance…
CONTINUE READING 🡒 The beginning of Nginx. Igor Sysoev tells the story of…
On December 12, 2019, a surprise search was conducted in the Moscow office of Nginx, Inc. Igor Ippolitov, an engineer at Nginx, was the first to inform the public of it in his Twitter. The original tweet…
CONTINUE READING 🡒 Boost your Nmap! Empowering iconic network scanner with NSE scripts
Nmap is an iconic scanner broadly used by hackers, and many of them are wondering how to expand its capacity. In most cases, Nmap is used in combination with other software tools. In this article, I'll explain…
CONTINUE READING 🡒 Tempesta FW, a handfull firewall against DDoS attacks
DDoS attacks have become a real scourge of the modern Internet. They are countered by both organizational methods (we wrote about them in our magazine more than once) and technical means. The latter are usually either ineffective…
CONTINUE READING 🡒