The highest level in the logical hierarchy of Active Directory (AD) is the forest. A forest refers to a completely independent Active Directory organization, possessing a specific set of attributes and serving as the organization’s security perimeter.
A forest can include one or multiple domains. All objects created within a forest share a common set of attributes. For example, a “user” object contains a first name, last name, address, phone number, group membership information, and other parameters. By modifying this set, we change it for all objects in the forest. This set is called the AD schema. It describes all the objects we can create and their structure.
By default, the first domain created in a forest is considered its root domain. A domain refers to a logical grouping of users and computers that supports centralized administration and security settings. It also serves as a replication unit—all domain controllers within a domain must participate in replication with one another.
Domains are typically named using the DNS namespace. Trust, in turn, is the relationship between two domains that enables permissions for accessing certain objects in another domain. A tree is simply a collection of domains that use connected namespaces. For example, if a domain is named example.com, then a child domain might be test.example.com. In summary, you can visualize this hierarchy as “Forest — Tree — Domain.”
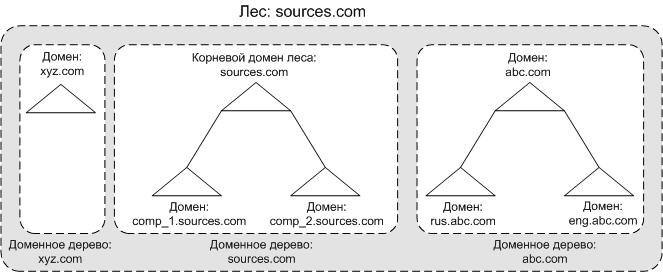
Most organizations typically use a very basic structure: a single forest with a root domain that contains various objects like users and computers. A more complex structure is mainly found in large companies that have a substantial IT workforce and different levels of responsibility. Often, only architects have full access rights, while regular administrators have rights limited to their own domains.
That covers the initial terminology. In one of the upcoming issues, I’ll discuss the types of trust relationships.
