We often write about abstract ways to break into and secure mobile devices, with the built-in assumption that defenses exist and the adversary is a hypothetical attacker. But what if the threat isn’t an idealized thief in…
CONTINUE READING 🡒 Category: Security
Weapons of Mass Deception: 10 Simple Social Engineering Tactics Explained
Social engineering is usually seen as part of a targeted attack, but what happens if you run these tactics at scale? The author devised and tested ten such scenarios to see how people would respond and what…
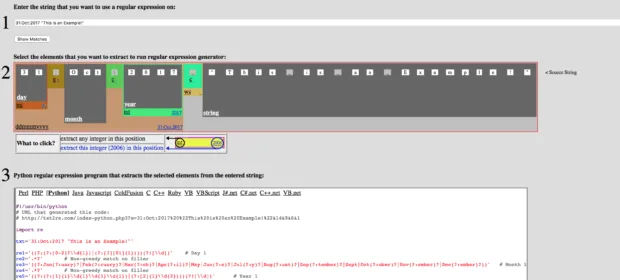
CONTINUE READING 🡒 txt2re: Regex Generator for People Who Hate Writing Regular Expressions
Regular expressions let you parse strings and text files quickly and elegantly—but only if you know the syntax well and have some experience. Otherwise, they turn into an eldritch horror, and prolonged exposure may cost you your…
CONTINUE READING 🡒 SMS Bomber in Python: A Reader’s Trick Shows Mobile Operator’s…
In this article, we examine flaws in how CAPTCHA and CSRF tokens are implemented, ultimately enabling the mass sending of SMS messages via the Vodafone gateway.
CONTINUE READING 🡒 macOS Setup Guide: Hidden Settings, Essential Apps, and Under-the-Hood Tweaks…
You’ve probably heard the line that Apple makes all the decisions for you and there’s nothing you can really customize in macOS. The first part is true; the second, in my view, is utter nonsense. macOS has…
CONTINUE READING 🡒 Meltdown and Spectre: Explaining Speculative Execution Side-Channel Vulnerabilities in CPUs
Over the New Year holidays, security researchers gave hackers the biggest gift imaginable: they uncovered fundamental flaws in modern CPU architecture. By exploiting these vulnerabilities, it’s easy to break address space isolation and read passwords, encryption keys,…
CONTINUE READING 🡒 11 Windows Privilege Escalation Techniques: How Attackers Gain Admin Access
One of the most common security best practices is to run applications and services under a least-privileged account. It doesn’t eliminate security issues, but it does make an attacker’s job harder. Consequently, whatever you’re breaking or pentesting—an…
CONTINUE READING 🡒 Down the rabbit hole. Storming Yandex Station debug console
This article describes my experience in reverse engineering of firmware used in Yandex Stations. I reversed the U-Boot debug console of the smart station processor and created a utility that extracts it from the decrypted bootloader. The method is applicable to all similar devices and, potentially, to other gadgets…
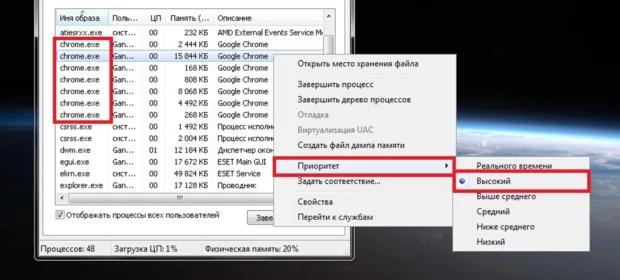
CONTINUE READING 🡒 Launching Processes with a Preset Priority in Windows
This isn’t a new topic, but it might still be useful to someone. How can you automatically launch processes with high or low priority without using third-party tools—just doing it yourself? I’ll demonstrate on Windows 7, but…
CONTINUE READING 🡒 Wi‑Fi USB Flash Drive Teardown: Capabilities and What’s Inside
We examined the internals of a Wi‑Fi–enabled USB drive and took a close look at how it operates. Appearances were deceiving, and our test results overturned our initial assumptions about the device. Below is our unedited, unsanctioned…
CONTINUE READING 🡒 What Data Google Has on You—and How to Export It…
As everyone knows, Google stores a vast amount of data about its users, a point it’s constantly criticized for. In response, Google built a tool that lets you export and download all your data. The service is…
CONTINUE READING 🡒 ReactOS: Why Trojans Run on the Windows Alternative but Microsoft…
On display in our cabinet of curiosities today is an unusual specimen—a twenty‑year‑gestating OS embryo learning to take its first steps. For now it can only stand and move gingerly, but it’s already trying to communicate with…
CONTINUE READING 🡒 Passive Reconnaissance: OSINT Tools and Techniques for Stealthy Information Gathering
The success of a penetration test largely depends on how well you profile the target. What services and software does it use? Which ports and protocols are exposed? Who does it communicate with, and through what channels?…
CONTINUE READING 🡒 Open Redirect Vulnerability: How Attackers Exploit It for Phishing and…
Open Redirect vulnerabilities let attackers send users to a phishing site or trick them into downloading a rootkit disguised as legitimate software. Despite how serious these flaws are, even Google is in no rush to patch them.…
CONTINUE READING 🡒 Building an ESP32 Packet Sniffer: Wi‑Fi Packet Capture and Bluetooth/BLE…
It all started when we kicked off a bug and vulnerability hunting project at GS-Labs. The target hardware was quirky—no way to get root, and no trusty Ethernet either. And hackers, as you know, hate flying blind.…
CONTINUE READING 🡒 An ‘Easter Egg’ in Telegram. How to log in without…
Telegram developers are continuously improving their product: the messenger gets more and more functions every year. But some of its cool features can turn, as of a sudden, into nasty bugs. This article discusses a curious vulnerability discovered when I was investigating…
CONTINUE READING 🡒 The Great Password Collider: Recovering Passwords from Hashes Without Heavy…
It’s often necessary to recover a password when all you have is its hash. You could brute-force it on your own machine, but it’s much faster to leverage existing databases. Even public datasets contain tens of millions…
CONTINUE READING 🡒 Speech-to-Speech: Building an AI Voice Cloning Neural Network
There are more and more ways to identify someone by their voice. At the same time, researchers are finding ways to bypass these mechanisms—both to protect personal data and to break into systems that rely on them.…
CONTINUE READING 🡒 5 Simple Python Examples to Inspire You to Learn Python
Over the past decade, Python has exploded in popularity and shows no signs of slowing down—its use in both teaching programming and building applications keeps growing. Few languages can claim such broad appeal across fields as varied…
CONTINUE READING 🡒 Hamster Kombat Automation: Building an Auto-Clicker Bot to Farm Coins
In this article, I’ll walk through how I explored the feasibility of automating the fast-rising game Hamster Kombat. Not every tactic I tried worked out, but you might still find the methods useful in other contexts.
CONTINUE READING 🡒