The Anonymous User’s Handbook
The articles in this series are published for free and are available to everyone. We believe everyone has the right to basic knowledge about protecting their data.
Other articles in the series:
- Authentication tokens: how they work and how they differ from passwords — https://xakep.ru/2019/10/17/jwt-howto/
- Email encryption: theory and practice — https://xakep.ru/2019/06/25/emails-encryption/
- How to encrypt your Jabber chats: a step-by-step guide — https://xakep.ru/2017/07/21/jabber-otr-howto/
- Make a “spy” USB drive with the Tails secure OS — https://xakep.ru/2016/11/01/tails-live-flash/
If you find these materials trivial — great! You’ll do a good deed by sharing the link with your friends, acquaintances, and family members who are less tech‑savvy.
Proxy servers
Proxy servers are the most accessible way to anonymize your traffic: they’re affordable and widely available. The idea is simple: a proxy acts like a mail carrier that sends envelopes on your behalf, carefully removing the sender’s name, and then delivers the reply straight back to you.
Originally, this technology was designed to shield internal corporate networks from the wider internet (employees accessed the internet from inside the network through a gateway), but it ended up becoming the first widely used method of anonymizing traffic.
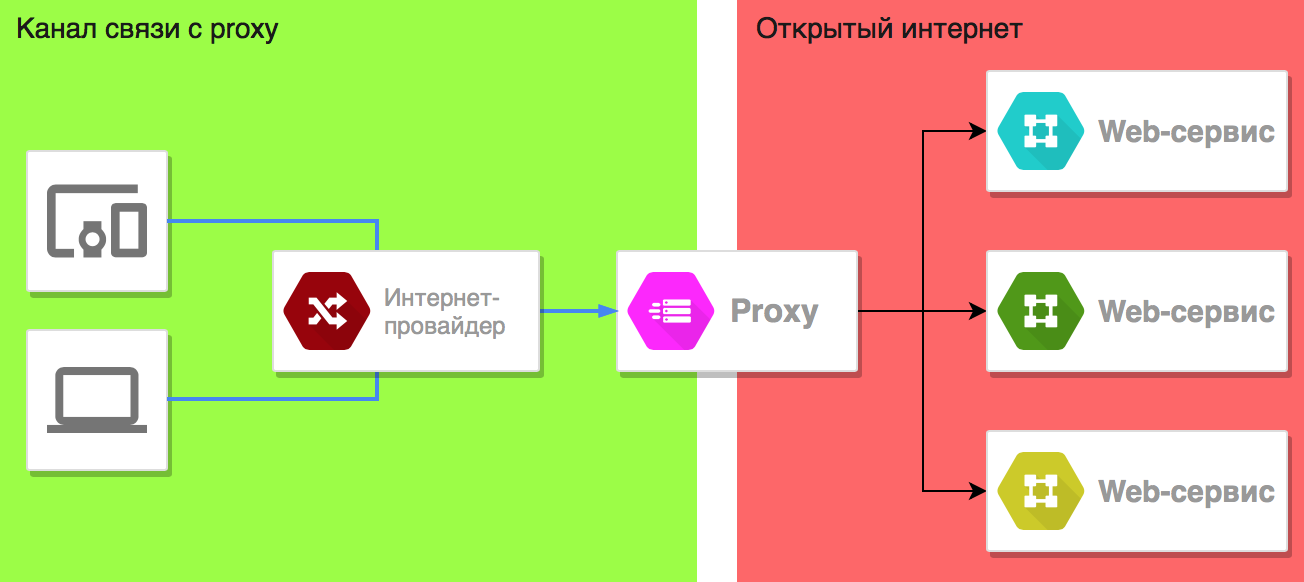
When you route your traffic through a proxy, your computer sends its requests to an intermediary (a proxy server), which then fetches data from websites on your behalf, presenting itself as your machine. Proxy servers are specialized, so different network protocols typically use different kinds of proxies. For example, FTP (File Transfer Protocol) uses an FTP proxy. We’ll take a closer look at three types of proxy servers.
HTTP and HTTPS only handle HTTP requests; the key difference is that HTTPS encrypts data in transit, while HTTP does not. For this reason, HTTP proxies aren’t recommended: they can change your IP address, but they can’t protect your data. Also be careful when choosing a proxy server—some won’t just fail to protect your data, they can also reveal your identity.
info
Pay attention to the proxy type—transparent or anonymous. Transparent proxies won’t conceal your identity.
Using this kind of proxy is straightforward: find one online or set up a server you trust, then open your browser’s network settings and enter the details.
The SOCKS type is used by applications that either don’t use HTTP/HTTPS or don’t have built-in proxy support. Unlike the previous type, this one won’t expose your IP by default, so anonymity isn’t an issue. However, SOCKS itself doesn’t provide any encryption—it’s just a transport protocol. To use it, you can turn to tools like Shadowsocks.
SOCKS4 and SOCKS5 are different versions of the proxy protocol. I strongly recommend using version 5, as it offers more features and better security. For example, it supports username/password authentication and DNS requests. Better yet, use Shadowsocks — it’s SOCKS5 on steroids. It provides strong encryption, traffic obfuscation, and the ability to bypass various blocks. There are clients for both desktop and mobile, so you can stay protected continuously.
To start using SOCKS in your everyday apps, you don’t need anything special. Firefox and µTorrent have built-in support you can enable in their settings. For Google Chrome, there’s the Proxy Helper extension. You can also use general-purpose tools like SocksCap or ProxyCap.
You can find large lists of free HTTP, HTTPS, and SOCKS proxy servers either via a web search or on Wikipedia.
VPN
A VPN (Virtual Private Network) wasn’t originally designed to secure or anonymize traffic. Its purpose was to link computers into a single network even when they were far apart. A key feature was that VPN connections were always protected with encryption, since they were used in corporate environments to connect multiple branch offices to headquarters.
A VPN supports two modes: linking two local networks over the internet (site-to-site) and connecting an individual computer to a remote local network (remote access). The latter is the basis for the noncommercial, personal use case. Data protection in a VPN connection is provided by two techniques that are often used together:
- PPP (Point-to-Point Protocol) is used for protection at the data link layer—the lowest practical layer. Its role is to ensure a stable connection between two endpoints on the internet and to support encryption and authentication.
- PPTP (Point-to-Point Tunneling Protocol) is an extension of PPP. It establishes two connections for operation: a control channel and a data tunnel.
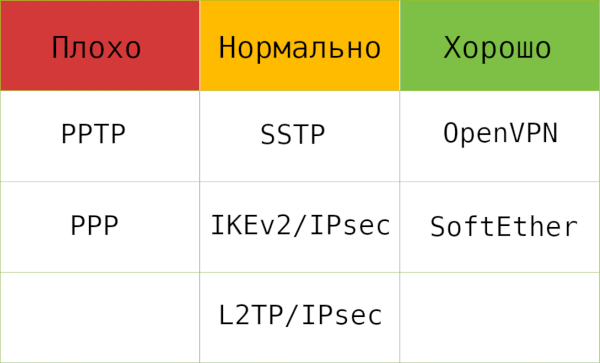
Because this protocol was designed back in 1999, its security is weak. None of the encryption methods used with PPTP are considered robust, and some can be cracked automatically. I therefore do not recommend using PPTP. It has serious vulnerabilities in both authentication and encryption, allowing an attacker to break the tunnel quickly and access the data.
A newer way to establish a connection is another protocol built on top of PPP — L2TP (Layer 2 Tunneling Protocol). The aim of this protocol is less about securing the link and more about standardizing how hosts communicate on the network. Besides setting up VPN connections, it’s also used, for example, to connect ATMs to bank branches, which provides a degree of assurance. However, note that L2TP has no native encryption of its own.
L2TP doesn’t protect the traffic it carries. That role is typically handled by IPsec (IP security). IPsec is designed to protect the contents of IP packets and can encrypt virtually any type of connection. For VPNs, only the tunnel mode is used: it protects not just the packet payload but also the original IP headers by encapsulating the entire packet. As a result, observers see only the tunnel endpoints, not the original sender and recipient.
IKE and IKEv2 (Internet Key Exchange) are key exchange protocols that negotiate cryptographic parameters and establish the keys that secure data in transit. They’re used exclusively with IPsec, serving as its security/control layer—thanks to IKE, the traffic in the connection stays encrypted. These protocols underpin most modern VPN tools and implementations, and it’s time to discuss the options and how to choose among them.
With the rise of SSL and TLS, the PPP protocol was extended into SSTP (Secure Socket Tunneling Protocol), which runs not over a plain connection but over SSL. This provides strong encryption and reliable transport. Keep in mind, however, that SSTP was developed by Microsoft, and Microsoft cooperates with governments, so assess your trust in SSTP accordingly.
OpenVPN is the most popular solution for establishing a secure connection. It’s an open-source protocol that offers strong protection, so it’s widely trusted. Setting it up shouldn’t take more than a couple of minutes.
SoftEther is a multi‑protocol VPN client that supports the protocols mentioned above, including OpenVPN, as well as its own protocol, which is at least as secure as OpenVPN.
The table below offers a brief summary of these solutions.
Tor
Tor (The Onion Router) is one of the most effective ways to stay anonymous online. It uses a three-hop design with layered encryption to protect your data and anonymize your traffic.
As the name implies, Tor uses onion routing: your data is the onion’s core, and the protective layers surround it. Each intermediate Tor relay peels off its own layer of encryption, and only the third hop—the exit node—exposes the core and forwards the request to the Internet.
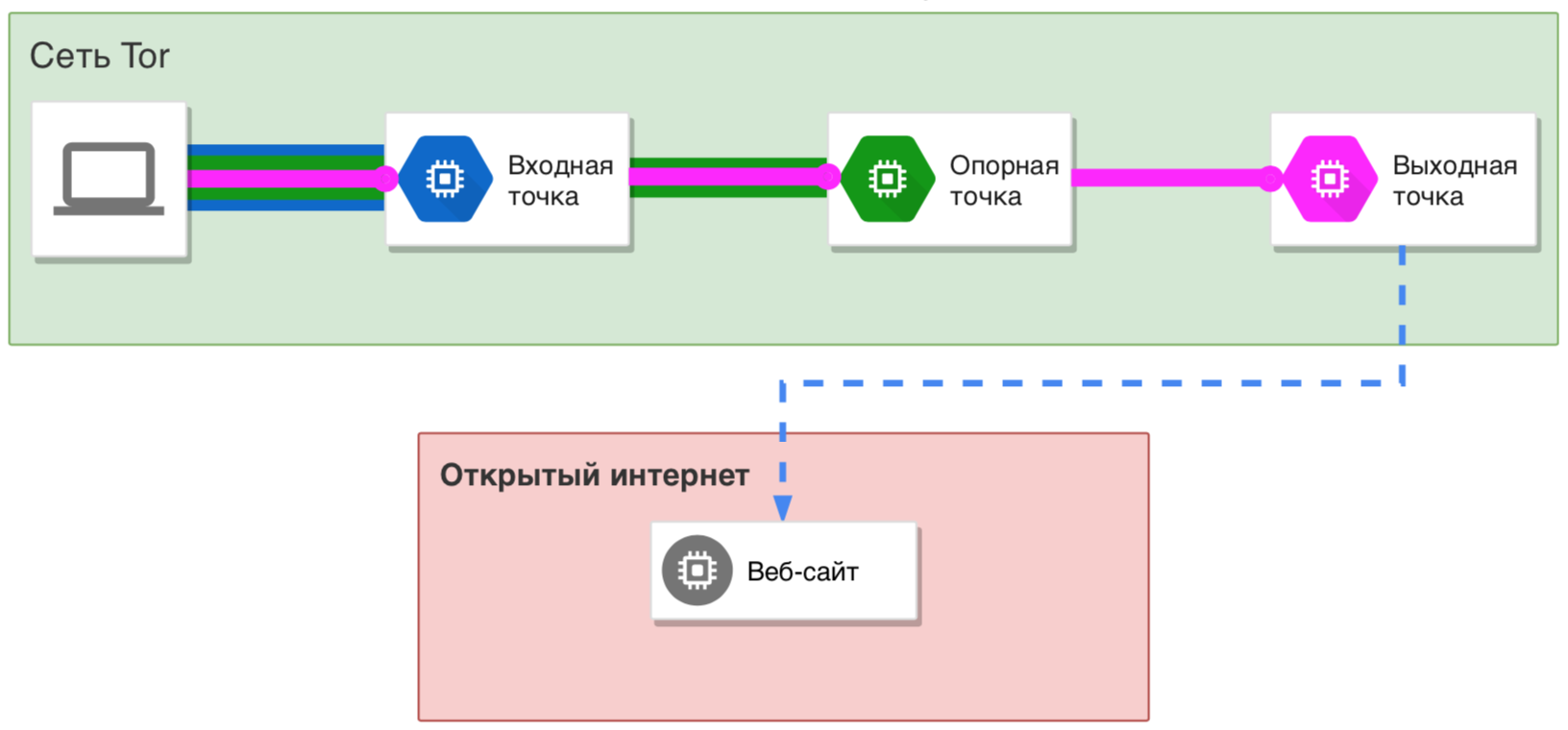
The entire network is kept running by thousands of volunteers around the world who champion human rights and privacy. As a result, Tor builds a separate circuit of relays for each site you visit, giving you strong protection: every site sees a new identity.
One of Tor’s biggest strengths is its stability and strong focus on anonymity: thanks to the efforts of many experts, it works even in China—a country notorious for stringent censorship and harsh penalties for bypassing it.
To make things easier for users, the developers created Tor Browser, based on Firefox, and enhanced it with extensions that prevent sites from tracking you. For example, HTTPS Everywhere forces websites to use encryption, and NoScript disables script execution on pages, effectively blocking the collection of any user data.
You can download Tor, along with the bundled browser, from the project’s official website, Tor Project.
DPI
Unfortunately, all these tools can be rendered useless if your ISP starts blocking traffic using DPI (Deep Packet Inspection)—a system for deep analysis of network traffic. The purpose of DPI is to drop anything that doesn’t look like a normal person using a normal computer—in other words, to block any activity that appears suspicious. And because traffic anonymization methods are suspicious by default, these programs often malfunction or simply refuse to work altogether.
There are ways to counter that, too. For nearly every method of securing a communication channel, there are pluggable transports that help slip past the watchful eye of DPI. For example, Shadowsocks includes built‑in DPI evasion and masquerades as a standard connection to a remote server.
OpenVPN traffic is easy to fingerprint on its own, but stunnel can also help you evade packet inspection. Stunnel wraps the VPN inside an SSL/TLS connection that looks innocuous—like a regular browser visiting a site over HTTPS. That makes this kind of tunnel hard to block. If you overdo it, you risk blocking virtually everything.
tls-crypt—a mode introduced in OpenVPN 2.4—also helps bypass DPI by encrypting the VPN’s TLS control channel.
The Tor Browser team actively works on evading DPI-based blocking. When connecting to the Tor network, you can use a pluggable transport that ensures an unobstructed connection to your first Tor entry point. You can either choose one from the built-in list (public bridges) or request a personal bridge on the official Tor Bridges site.
The best results come from obfs4—an obfuscation transport that scrambles traffic so it’s indistinguishable on the wire. DPI generally lets such packets through because it can’t tell what they are.
There are also a few tools that try to evade packet inspection in various ways—for example, by fragmenting traffic or altering headers. These include GoodbyeDPI and Green Tunnel (the latter has a simple GUI). They don’t hide your IP or your data, but they can bypass blocking.
A comprehensive, all-in-one option is the Streisand project; a Russian-language overview is available on GitHub. It’s a real Swiss Army knife for data security. In just a few minutes, this tool deploys and configures multiple data-protection services on a remote server and provides detailed, step-by-step instructions for each.
Conclusion
To protect our online security and anonymity, a wide range of technologies has been developed at different levels. Some are time-tested, while others defend against the latest censorship techniques. Thanks to these, we can still stay under the radar—you just have to remember to use them.
