QR codes are everywhere these days—major services like WhatsApp, Yandex, and AliExpress use them as an authentication method. But how secure is this approach? Is it possible to craft a QR code that, when scanned, delivers and…
CONTINUE READING 🡒 Category: Security
Choosing the Best PE Editor for Windows Executables: A Reverse…
The primary—and hardest—task for a hacker during a software break-in is to identify the protection mechanism and bypass it. For reconnaissance I typically use the WinDbg debugger, and for “patching” the application I rely on the Hiew…
CONTINUE READING 🡒 A Practical Guide to Stable Diffusion XL: Choosing Models, Refiners,…
If you decide to run generative image models on your own machine, you’ll quickly hit a tough choice: there are many of them, and while their outputs are similar, they’re all a bit different. In this article,…
CONTINUE READING 🡒 SI473X SDR Hacks: Building a DIY Receiver and Uncovering Hidden…
Today I’ll walk through how modern broadcast receivers are put together, using the SI473x family—single‑chip SDR receivers—as an example. Along the way, we’ll write our own library to drive these chips. You might ask, why build yet…
CONTINUE READING 🡒 MITRE ATT&CK Matrix: How the Threat Description Language Works and…
MITRE ATT&CK is one of the most widely used frameworks among cybersecurity professionals. In this article, we’ll cover how the knowledge base was created and how it’s structured—how it’s used to describe malware capabilities, profile APT groups,…
CONTINUE READING 🡒 Silent call. Concealing NTAPI calls from security tools
Since recently, EDR systems have been increasingly frequently using call stack tracing to detect malicious applications and envenom red teamer’s lives. Let’s analyze this powerful technique and find a way to fool EDR and call NTAPI covertly — so that even stack unwinding won’t…
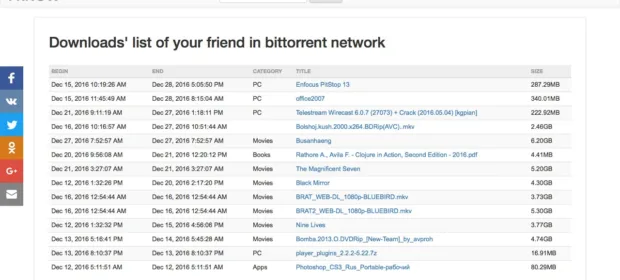
CONTINUE READING 🡒 I Know What You Downloaded: A Website That Tracks Who…
The site’s name translates to “I Know What You Downloaded.” Its creators built a system that monitors public torrents to log lists of files downloaded via BitTorrent and the IP addresses of peers. If you download torrents…
CONTINUE READING 🡒 IMSI-Catchers Explained: Mobile Network Interception FAQ, Detection, and Protection
By now, everyone knows public Wi‑Fi hotspots aren’t safe. That doesn’t stop everyday users from relying on them—often without any VPN—even though VPN features are built into many security suites these days. A long‑standing “safer” alternative has…
CONTINUE READING 🡒 Reverse Engineering Fundamentals: Hands-On Executable Analysis in IDA Pro
In this article, we’ll dive into an in-depth static analysis using IDA Pro—the go-to disassembler for hackers and security professionals. We’ll start with the basics and steadily work our way forward, cutting through the thicket of code…
CONTINUE READING 🡒 TrueNAS CORE vs TrueNAS SCALE vs OpenMediaVault: Choosing the Right…
Despite the abundance of off‑the‑shelf NAS devices from major vendors, the urge to build and tune your own NAS shows no sign of fading. The options are dizzying: TrueNAS Core, TrueNAS Scale, openmediavault, specialized setups with Unraid…
CONTINUE READING 🡒 WebSDR: A Browser-Based Gateway to Software-Defined Radio (SDR)
They say that once you dip your toes into SDR (software-defined radio), you fall down the rabbit hole—buying all sorts of gear and tinkering with it. If that warning doesn’t scare you off, the WebSDR site is…
CONTINUE READING 🡒 10 Facts You Didn’t Know About the Python Programming Language
Python is a programming language with a relatively low barrier to entry, which is why many beginners choose it. Still on the fence about learning Python? Here are ten facts that can help you put your doubts…
CONTINUE READING 🡒 Using Open vSwitch to Segment and Isolate VMs with VLANs
Virtualization has long been a staple of nearly every enterprise infrastructure. Any admin has either used a hypervisor or at least experimented with one. We’ve already covered how to deploy a virtualization host, so today we’ll focus…
CONTINUE READING 🡒 5 Essential OSINT Tools: Building a Network Reconnaissance Toolkit
OSINT (open-source intelligence) can be incredibly useful, especially during incident investigations. Most people know the theory—what to look for and where—but in practice the data sets are so large that going through them by hand is impossible,…
CONTINUE READING 🡒 Total Commander Reverse Engineering: Bypassing Protection in All Versions
Total Commander (formerly Windows Commander) is a popular graphical file manager for Windows. You can find plenty of methods to crack it on warez sites. Their perennial downside is how kludgy they are: every time a new…
CONTINUE READING 🡒 Ghidra vs IDA Pro: What the NSA’s Free Reverse Engineering…
In March 2019, the U.S. National Security Agency (NSA) released a reverse‑engineering toolkit called Ghidra. I’d first come across the name a couple of years earlier in WikiLeaks leaks and was very curious about what the NSA…
CONTINUE READING 🡒 Gridcoin: Earn Cryptocurrency Rewards for Scientific Computing
While some people mine crypto, others crunch scientific data. Until recently, you had to choose between profit and altruism, since most distributed computing projects don’t offer payouts. Now there’s a third‑party rewards program, and it’s already showing…
CONTINUE READING 🡒 How to Install VirtualBox on Tails OS and Route VM…
Tails is the best operating system if your goal is to maximize your anonymity online. But it has a few quirks, and one of them is that you can’t properly install VirtualBox using the standard tools. We’ll…
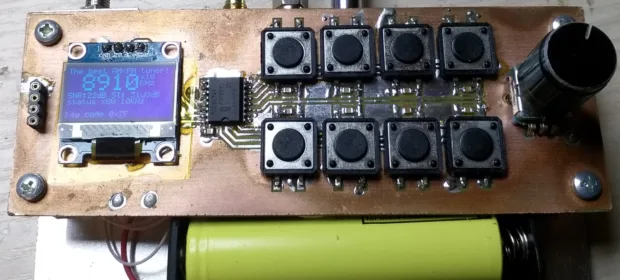
CONTINUE READING 🡒 DIY USB HID Attack Device: Building and Programming a BadUSB…
USB’s versatility creates a broad attack surface: researchers at Ben-Gurion University have identified nearly three dozen ways to weaponize USB. In this article, we’ll examine one of the most effective approaches—automating keystroke injection using a DIY HID-class…
CONTINUE READING 🡒 OAuth successors. Attacks targeting OpenID Connect
OpenID Connect is a reenvisioning of the OAuth protocol; it was designed to solve the authentication problem and patch security holes in the original specification by making the standard more stringent and demanding. But people continue making mistakes, and misconfigs resulting in vulnerabilities still occur. This article…
CONTINUE READING 🡒