So, what is MITRE and what are these “attacks”? MITRE is a U.S.-based nonprofit that operates research and development centers for the federal government and for state and local agencies. Its focus areas include artificial intelligence, quantum information science, health informatics, space security, sharing cyber threat intelligence and defensive techniques, and more.
In cybersecurity, MITRE is best known for the CVE list (Common Vulnerabilities and Exposures) cve.mitre.org. Launched in 1999, it’s a catalog of publicly disclosed vulnerabilities and has since become one of the primary resources for organizing and storing information on software flaws. Attackers often consult such databases right after scanning a network, during their initial attempts to breach a target’s environment.
CVE isn’t the only MITRE project focused on cybersecurity. Other actively developed initiatives include:
- ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge), attack.mitre.org — a structured knowledge base of real-world adversary tactics and techniques, organized as matrices.
- Structured Threat Information Expression (STIX) — a language and serialization format for exchanging cyber threat intelligence (CTI) between security tools and platforms.
- CAR (Cyber Analytics Repository) — a knowledge base built on the ATT&CK model; its analytics are often expressed as pseudocode that defenders can use to implement detection logic.
- SHIELD Active Defense — a knowledge base of active defense and adversary engagement techniques that complements the risk-mitigation guidance in ATT&CK.
- AEP (ATT&CK Emulation Plans) — playbooks for emulating adversary behavior using a defined set of ATT&CK-mapped TTPs (tactics, techniques, and procedures).
Russian regulators are also doing similar work—on February 5, 2021, FSTEC of Russia published a methodological guide on information security threat assessment. An example attack scenario is shown on page 30.
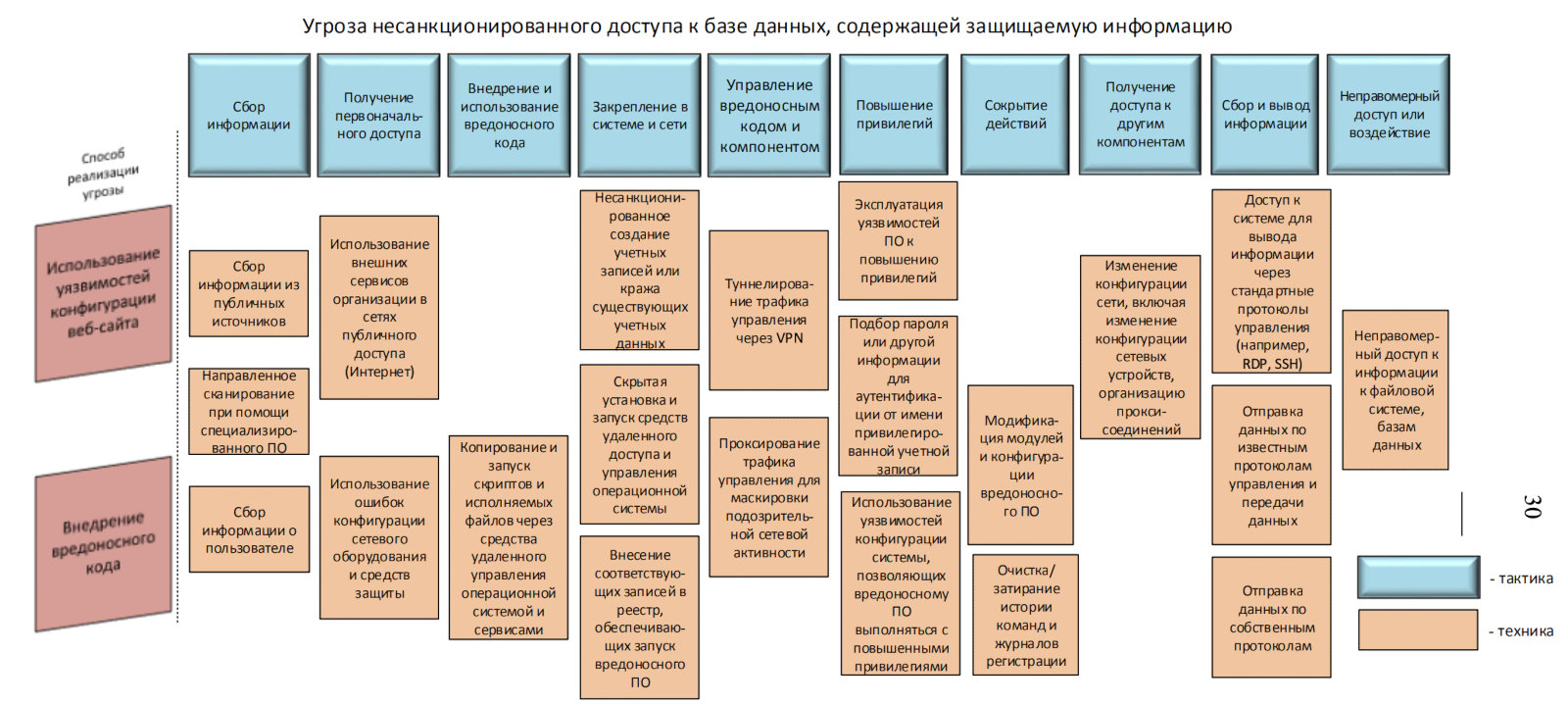
People are already calling this table “FST&CK,” but that’s a story for another day…
Why ATT&CK Matters
MITRE introduced the ATT&CK matrix in 2013 as a way to describe and categorize adversary behavior (i.e., behavioral patterns) based on real-world observations. Before we dive into how to use the matrix, let’s walk through the key concepts—don’t worry, there are only three.
APT (Advanced Persistent Threat) is a group of attackers—or even a nation-state—that conducts prolonged cyberattacks against organizations or countries. The literal translation is “advanced persistent threat.” As you’ll see after reading the whole article, there’s nothing particularly “advanced” about it.
www
A comprehensive list of known APT groups, maintained by cybersecurity enthusiasts.
TTP sets (Tactics, Techniques, and Procedures) are broken down as follows:
- tactic — how an adversary operates at different phases of an intrusion; the attacker’s goal or objective at a given step. Example: TA0002 Execution — when the adversary tries to run their malicious code. Yes, it sounds basic, but wait till you see what comes next;
- technique — how the adversary achieves that goal: the tools, technologies, code, exploits, utilities, and so on. Example: T1059.001 PowerShell — using PowerShell during an attack;
- procedure — how that technique is carried out and for what purpose. For example: malware uses PowerShell to download a payload, which then loads Cobalt Strike in an attempt to execute on remote hosts (feel how the technique and the tactic come together here?).
How does an attacker actually operate? They open their handbook for wannabe hackers, where on the second page they’re introduced to the concept of the Kill Chain. The Kill Chain is a model that describes the sequence of actions that lead an intruder to their objective. It consists of a series of typically sequential stages:
- reconnaissance — intelligence gathering on the target
- weaponization — preparing the attack: selecting/building the tooling and payload
- delivery — delivering the payload to the target
- exploitation — triggering the exploit to execute code on the target
- installation — installing malware or backdoors on the target system
- command and control (C2) — establishing remote control via C2 infrastructure
- lateral movement — moving laterally and spreading within the network
- actions on objectives — achieving the intended impact on the target
The MITRE ATT&CK matrix began as an internal project known as FMX (the Fort Meade eXperiment). In it, security specialists were tasked with simulating adversary TTPs against a network, and the resulting attack data was collected and analyzed. That dataset became the foundation of ATT&CK. Because ATT&CK provides a fairly comprehensive description of the behaviors adversaries use to compromise networks, the matrix is useful for a variety of offensive and defensive use cases—metrics, visualizations, and other mechanisms (e.g., threat modeling aligned with FSTEC requirements).
MITRE has divided ATT&CK into several consolidated matrices:
- Enterprise — TTP used in attacks against organizations
- Mobile — TTP focused on mobile devices
- ICS — Industrial Control Systems: TTP for industrial control environments
Each of them covers tactics and techniques relevant to that matrix’s scope. The most popular matrix is Enterprise. It, in turn, is divided into branches, each covering its own area:
- PRE Matrix — the preliminaries, a.k.a. “foreplay”;
- Windows — attacks against Windows‑based infrastructure;
- macOS — same for Macs;
- Linux — you can guess;
- Cloud — attacks on cloud environments;
- Network — attacks on the network.
Next, we’ll focus on this specific matrix. The split into submatrices isn’t arbitrary. For example, the PRE Matrix and the other components can be mapped to the stages of the kill chain as follows.

As you can see, the PRE Matrix covers the preparatory stages of an attack—things like scanning and network inventory, phishing, or social engineering. The other sub-matrices of the Enterprise matrix are where the most interesting parts are. Along the top of the matrix there are 14 tactics, and each tactic contains techniques an adversary can use.

Let’s take the Execution tactic as an example. How many ways are there to run something on an endpoint? There’s no need to reinvent the wheel or convene a task force—smart folks have already mapped this out. Open up tactic TA0002 (Execution) and you’ll see how many execution techniques there are. There are ten in total, not counting sub-techniques:
- T1059 — Command and Scripting Interpreter: using command and script interpreters
- T1203 — Exploitation for Client Execution: exploiting client-side software vulnerabilities
- T1559 — Inter-Process Communication: leveraging inter-process communication (IPC)
- T1106 — Native API: calling the operating system’s native API
- T1053 — Scheduled Task/Job: abusing scheduled tasks/jobs for execution or persistence
- T1129 — Shared Modules: loading shared modules (e.g., DLLs)
- T1072 — Software Deployment Tools: abusing software deployment systems/tools
- T1569 — System Services: leveraging system services for execution
- T1204 — User Execution: inducing users to perform actions that aid the attacker (e.g., run payloads)
- T1047 — Windows Management Instrumentation: using WMI
Techniques can have sub-techniques. Click the right-hand area (the nondescript gray trapezoid) to expand them.
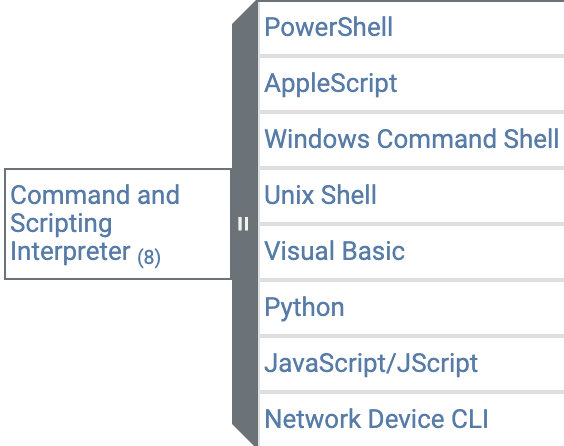
Scripts and commands are provided for various popular operating systems that adversaries might use during a malicious campaign. Clicking a label takes you to a page describing a specific technique; for example, clicking Command and Scripting Interpreter opens all related information about that method, including a brief technique overview, example procedures used by different groups, and recommended mitigations.
Under FSTEC’s new threat modeling methodology, you’re expected to use a set of TTPs like LEGO bricks. When you identify an attack, assemble all possible implementation paths (scenarios) from TTP building blocks. MITRE ATT&CK is listed as one of the possible sources for the input data.
To capture the techniques, tactics, and procedures (TTPs) used after analyzing the malware, you can use the MITRE ATT&CK Navigator instead of Excel. For an example, see the TTP breakdown of the Carbanak targeted attack.
In short, the MITRE ATT&CK matrix can and should be used—both for malware analysis and for mapping the tactics and techniques of different threat groups. As an example, check out this Group-IB research on the ProLock ransomware. It includes a MITRE ATT&CK Mapping section that outlines the tactics and techniques used.
To automate the mapping process, you can use the official (currently beta) Threat Report ATT&CK Mapper (TRAM). It leverages NLP (natural language processing) to suggest the appropriate tactic or technique based on keywords, and the analyst only needs to accept or reject the suggestion. We’ll cover this tool in a future article.
capa Rules
The permissions almost any Android app requests at install time have long drawn scrutiny from infosec professionals. They typically want access to the camera, the microphone, and the network—obviously so they can beam it all straight to your handler!
Researchers at FireEye liked the idea—why not check what capabilities a given executable has? No sooner said than done: enter the CAPA rules.
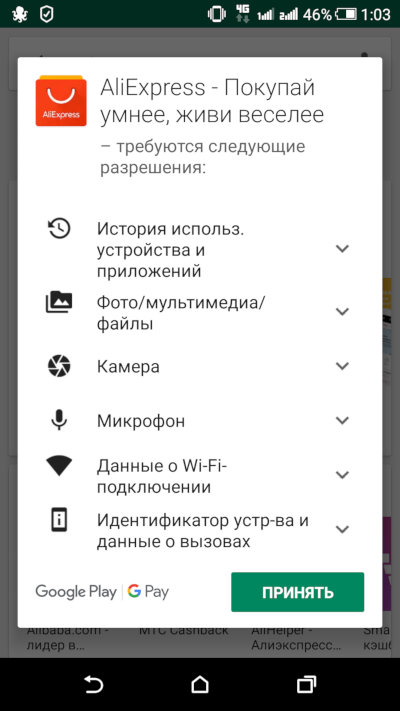
During dynamic analysis, the sample is executed in an isolated environment and all activity is monitored at the hypervisor level or with specialized tools. By leveraging capa rules (which are open source), an analyst can save time, perform a preliminary static review of the sample, and focus on the program’s potential behaviors and capabilities as mapped to the MITRE ATT&CK matrix.
Here’s what CAPA output looks like when analyzing an .exe. The sample program was written in Python and packaged into an executable using auto_py_to_exe.
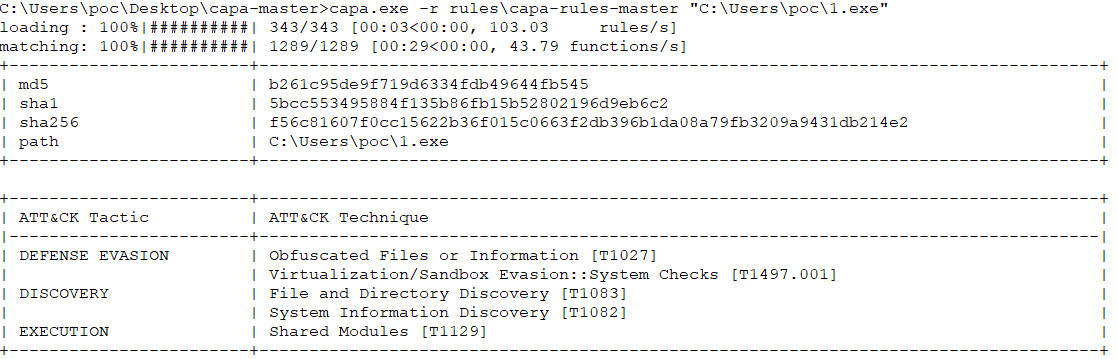
We see that the file under analysis maps to three tactics and five techniques in the MITRE ATT&CK matrix. In addition, CAPA reports the executable’s capabilities inferred from the functions it uses.
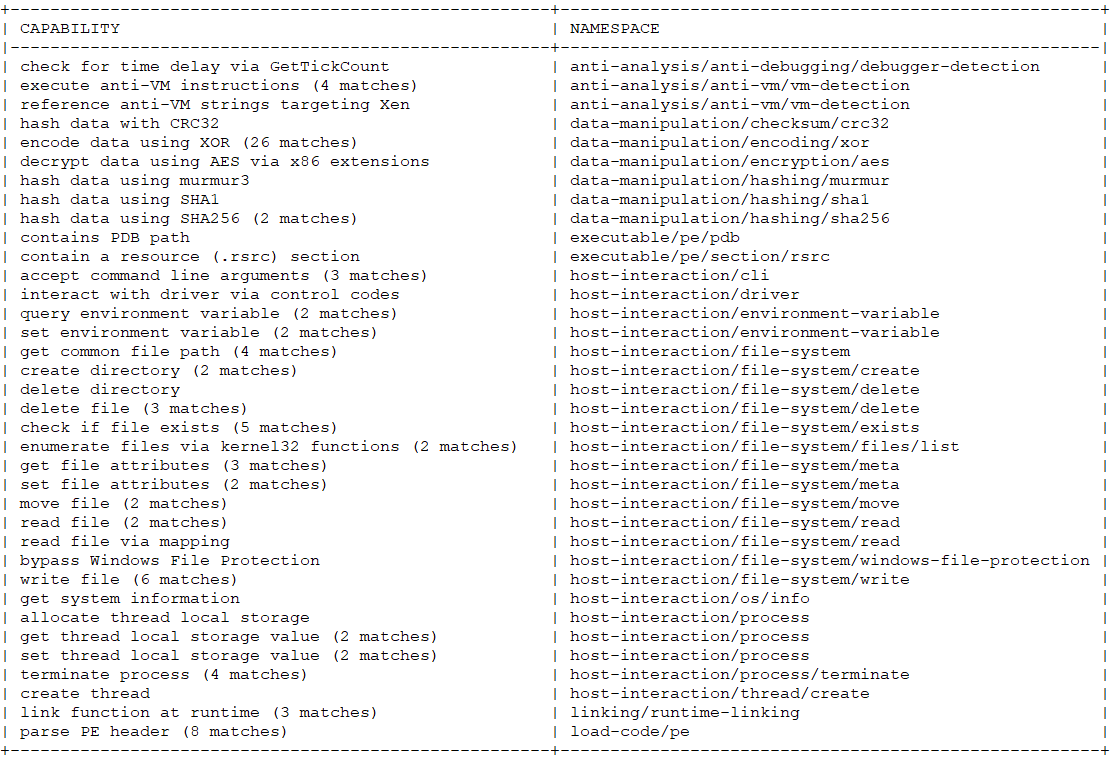
In CAPA, capability detection is automated by scanning for characteristic artifacts: API calls, strings, constants, creation of mutexes and sockets, and dynamically loaded libraries. These artifacts are described with rules (similar to YARA) that help reveal the behaviors implemented by the malware.
Let’s look at an example of a SARA rule.
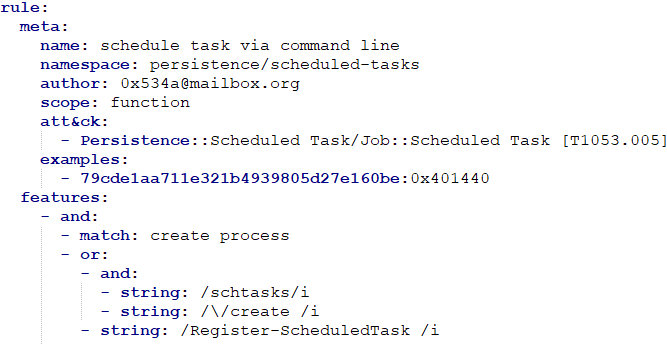
First, CAPA extracts strings and constants that might be function names or otherwise meaningful to an analyst. The findings are split into file properties and disassembly artifacts (strings, constants, calls). File properties include headers and imported APIs (including the names of the functions used). In the example above, a logical condition is used:
create_process AND [(string /schtasks/i AND string /\/create /i) OR string /Register-ScheduledTask /i]In other words, the rule detects console commands used to create tasks in the Windows Task Scheduler.
Note that CAPA rules only work with PE (Portable Executable) files. To get more details about the sample, use the -v and -vv flags.
Key takeaways
The community of practitioners who embrace the MITRE ATT&CK philosophy grows every year, and the matrix’s adoption is becoming mainstream. For example, vendors use ATT&CK to build alerts into their products. This approach streamlines incident investigation and response. In short, ATT&CK isn’t just hype; it’s a critical knowledge base for the entire cybersecurity industry.
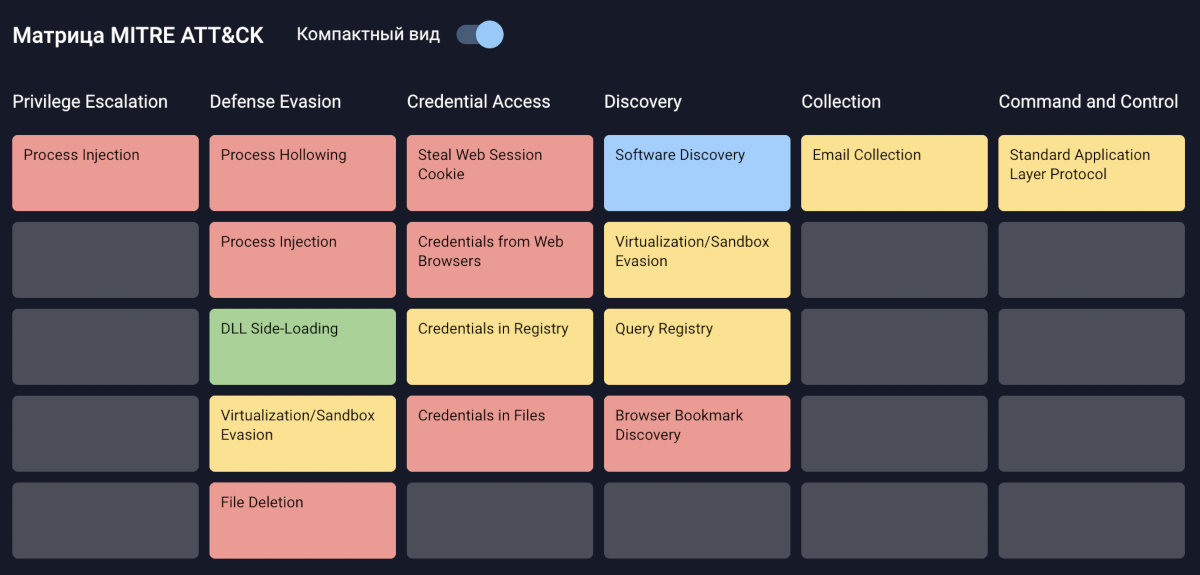
The matrix lets you build threat models for different types of organizations and show which known threats can be mitigated by specific solutions. In theory, it works like this: a company selecting defenses for its infrastructure maps an adversary’s capabilities onto the ATT&CK matrix and then checks which relevant threats remain unmitigated.
Mapping threat groups and their campaigns to MITRE ATT&CK helps you understand which tools adversaries use and get familiar with their techniques and tactics. These insights let you anticipate the most likely entry points into an organization.
Broad, sustained use of the MITRE ATT&CK knowledge base will help unify the cybersecurity community’s approach—essentially giving everyone a common language.
It’s important to remember that the last two letters in ATT&CK stand for Common Knowledge—meaning things that are already known. The matrix is built from real-world intrusions and serves as a behavioral reference for which TTPs were used. It’s undeniably a great, easy-to-use knowledge base with strong backing. Still, the paradox is that it will never fully capture every adversary technique, even though it strives to do exactly that.