warning
This article is published solely for educational purposes, and neither the author nor the editorial team bears responsibility for any harm that may result from using the materials in this publication. Gathering information about a person’s private life without their consent is illegal. OSINT is the practice of finding, in open sources, data that people themselves have left publicly accessible. Even then, violating someone’s privacy may still be unlawful.
In this article, I’ll showcase five tools for analyzing public data from social media and Telegram.
1. YaSeeker
YaSeeker lets you pull information on any Yandex account. Just enter the user’s nickname, and the script does the rest. It’s a handy tool for finding someone by their handle, as long as you know they have a Yandex account.
I’ll be installing all the tools in this write-up on Kali Linux, but the process shouldn’t differ on other Debian- or Ubuntu-based distros.
Download YaSeeker from GitHub and install the dependencies.
git clone https://github.com/HowToFind-bot/YaSeeker.git
cd YaSeeker
pip install -r requirements.txt
Since Yandex isn’t keen on handing data to just anyone (at least officially), you’ll need to supply the tool with cookie files so it can pass as a real user. The easiest way is to register a throwaway Yandex account and install a browser extension that can export cookies in Netscape format.
With the extension enabled, go to Yandex and save cookies. (if the extension asks which site to save cookies for, choose “Current Site”). It’s easiest to save the file directly to the YaSeeker directory. Make sure to name it exactly cookies., because you can’t configure the path to the cookie file.
Now that we’ve got the cookies we need, we can use the script. Just run it with python3 and pass the username you want to learn more about as an argument.
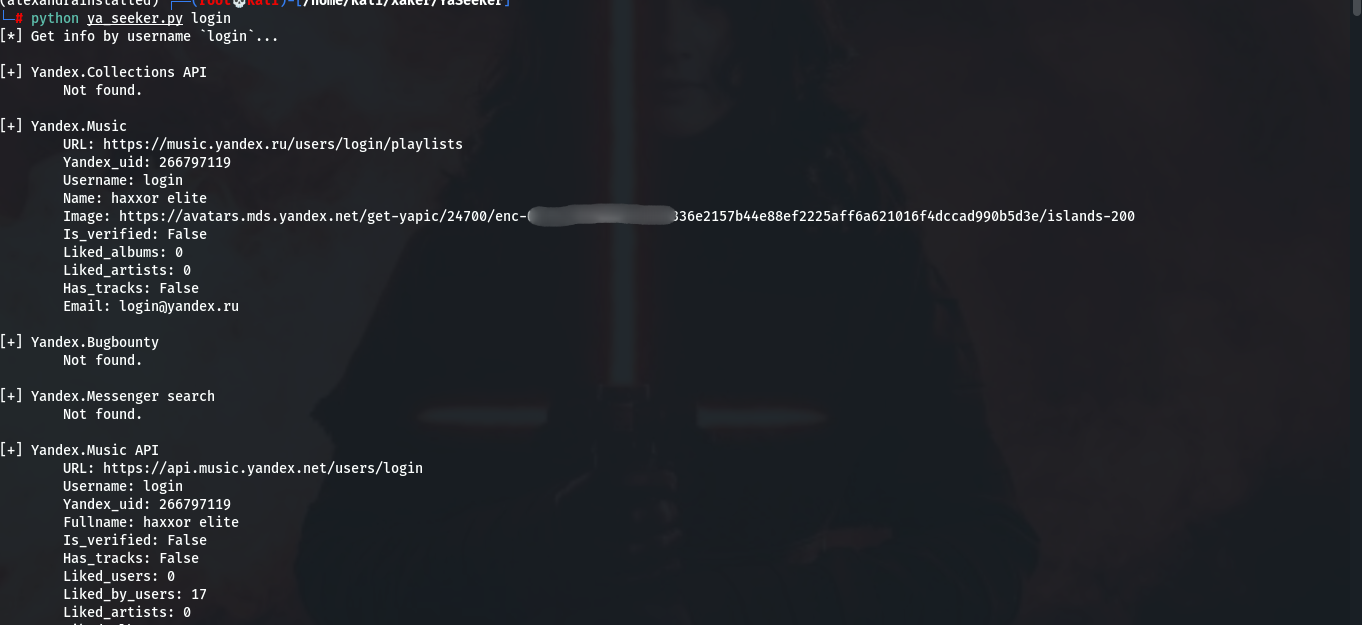
The tool reports which Yandex services the account holder uses. For investigations in the Russian-language segment of the internet, YaSeeker can be very useful, and it’s worth adding to your toolkit—especially if you automate its execution alongside similar tools in a single script.
2. Enola Holmes
Enola is a counterpart to the far more widely known tool Sherlock. Its creators proudly named it after Sherlock’s sister, Enola Holmes. This implementation is written in Go and runs a bit faster.
Enola can search for usernames across nearly 400 services and has a much more user-friendly interface than Sherlock.
Installation can be done in two ways: the simple route, or the Go-enthusiast route. I’m in the latter camp, so I’ll take the slightly longer path.
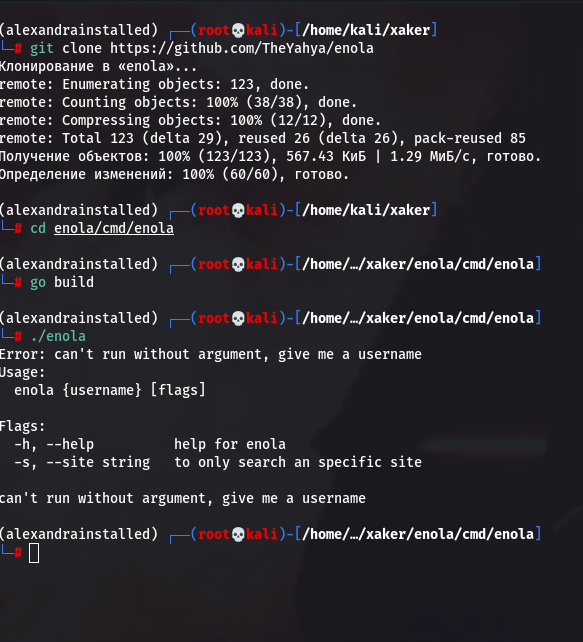
First, clone the repository:
git clone https://github.com/TheYahya/enola.git
Then navigate to the enola/ directory and build the binary with go .
An executable named enola will be created; you can run it with: ./.
An alternative installation method also requires Go (version 1.19 or later), but it’s just a single command:
go install github.com/theyahya/enola/cmd/enola@latest
You can now launch Enola and see how it handles finding a random username from a chat.
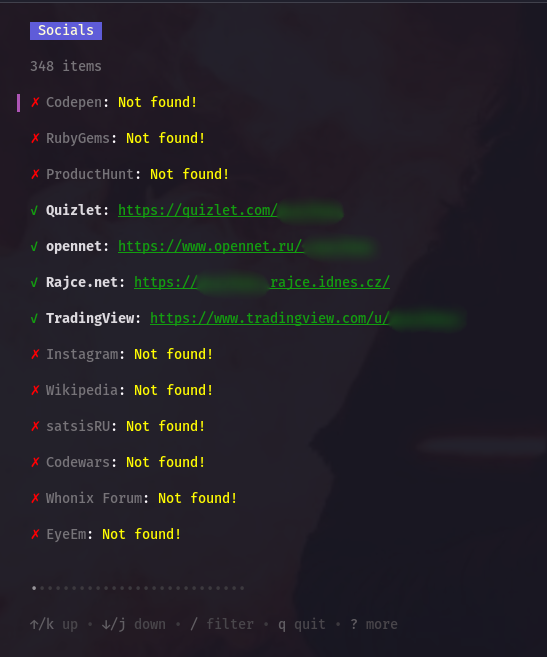
As you can see, it’s easy to use, with hotkey hints available on the bottom bar. Other advantages: it starts up quickly and shows results instantly.
3. Telegram-bot-dumper
This tool comes in handy when you’ve obtained a Telegram bot token—for example, if you’re investigating an infection by malware that was controlled via a Telegram bot. The script retrieves all chats between the bot and its users, including not just text messages but all media files as well. So Telegram-bot-dumper is not only an OSINT tool, but also a generally useful utility.
To get this working, you’ll need to obtain the API_ID and API_HASH for a Telegram app, so it’s best to use a burner account—better safe than sorry. You wouldn’t want your personal account getting banned if something goes sideways, right?
Download and install the tool like any Python app: clone the repository, change into its directory, and install the dependencies.
git clone https://github.com/soxoj/telegram-bot-dumper
cd telegram-bot-dumper
pip install -r requirements.txt
Before running, open the dumper. file in any editor and set the API_ID and API_HASH variables to your own values.
Run:
python3 dumper.py --token <token>
The script will download the entire available history and then keep listening for new messages. To stop it, just press Ctrl-C.
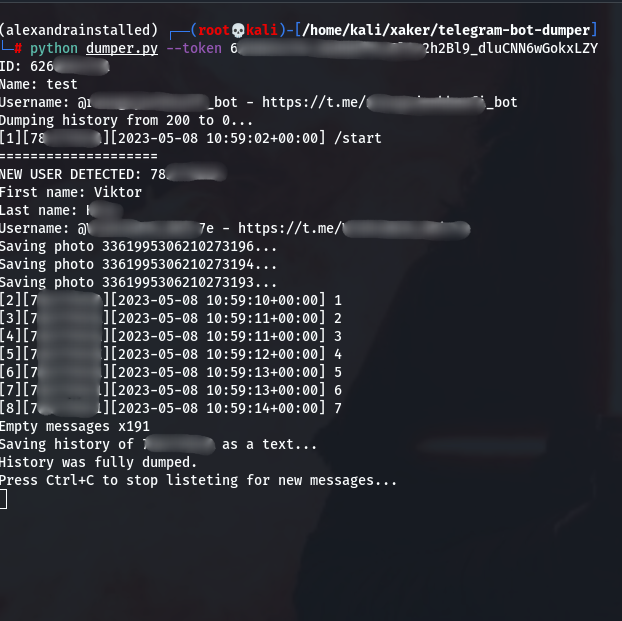
Unfortunately, the tool can’t detect when a user has deleted part of the conversation and may end up dumping an incomplete history. To mitigate this, use the --lookahead parameter, where N is the number of additional batches of 200 messages (the default batch size) the tool will try to dump. Note that you still won’t be able to recover deleted messages, but you may have a better chance of retrieving earlier ones.
At a minimum, the script helps assess the scope of the incident (the volume of data stolen during the attack), and in attacks orchestrated via a Telegram bot, it can also reconstruct the timeline.
4. Socid-extractor
Socid-extractor can pull profile data from many of the services supported by Enola, but does so with a level of detail comparable to YaSeeker. It shows rich details, not just whether the user has an account on a given service.
Important note: it generally doesn’t use the services’ native APIs, so the amount of data is smaller than it could be; in return, the script runs very fast and doesn’t require the tedious setup of obtaining API keys from hundreds of services.
It makes sense to run Socid-extractor in tandem with other similar tools—such as YaSeeker.
You install Socid-extractor the same way:
git clone https://github.com/soxoj/socid-extractor
cd socid-extractor
pip install -r requirements.txt
Now we can review information about the person we’re interested in. As an example, let’s use VK (VKontakte).
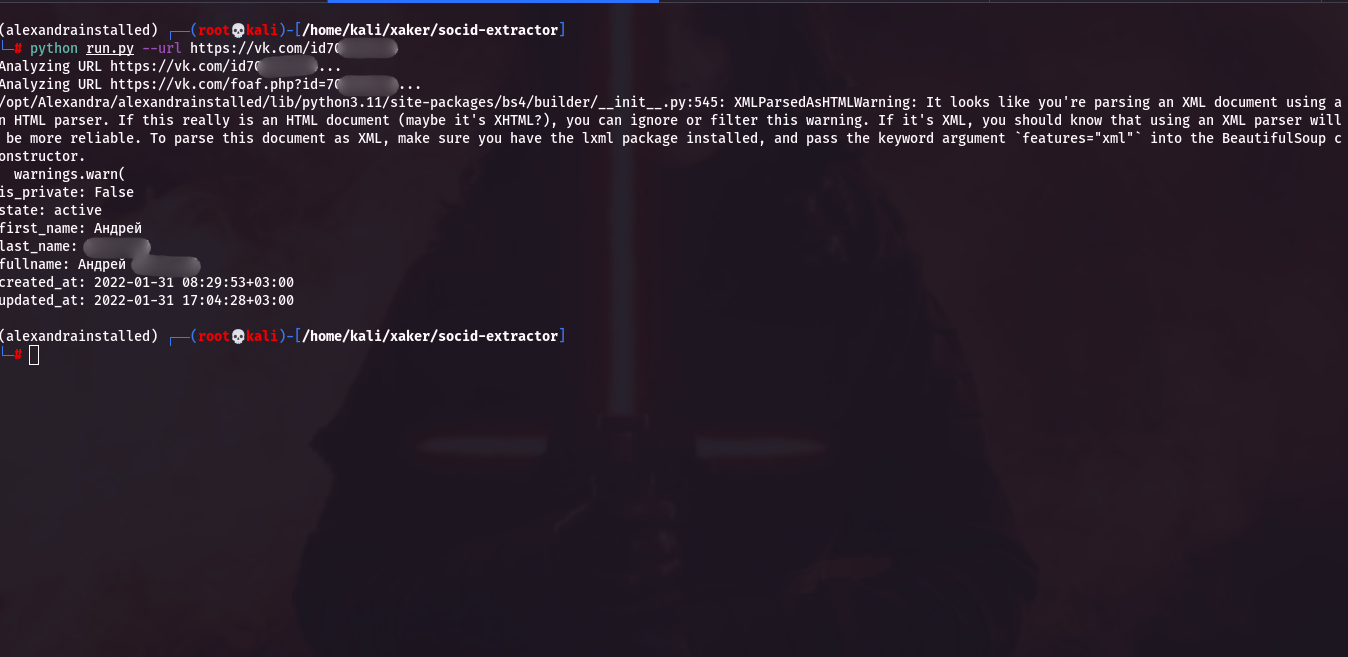
The tool returned the user’s first and last name, registration date, last update, and flags indicating whether the account is active and private. That’s plenty for a first pass at data collection.
5. TelAnalysis
To top it off, I’ve got an interesting tool for analyzing Telegram chats. More specifically, TelAnalysis parses a chat history file and does everything without relying on the Telegram API or the Telegram app, unlike many scripts that work with Telegram data.
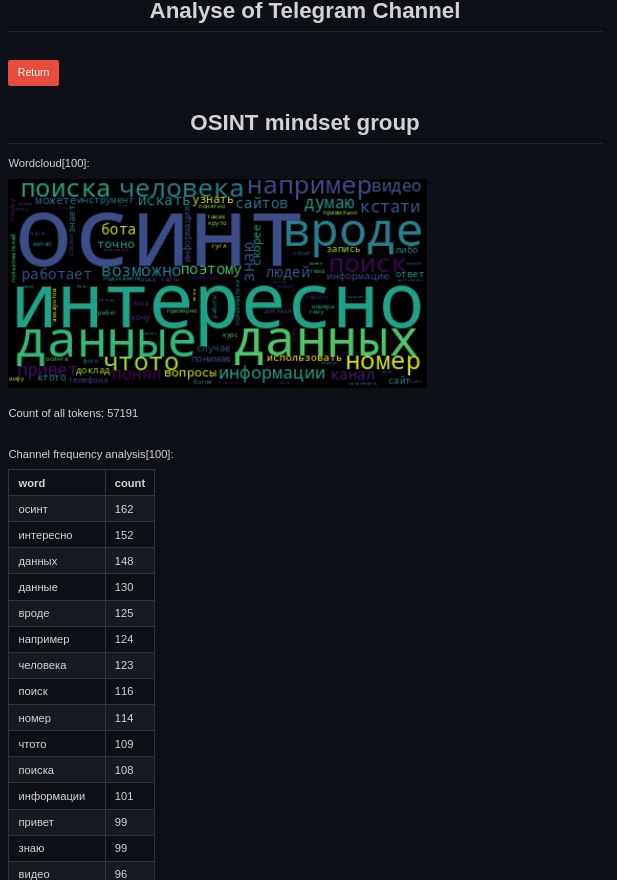
TelAnalysis primarily performs static chat analysis: it builds a list and a network graph of the most active participants, produces a ranked list of the most frequent words, and generates a word cloud (an image where word size reflects popularity). It can also display general information about each user. Additionally, you can generate per-user top-word lists to see who’s interested in what.
This tool’s interface is a bit different from the previous ones: only the server runs in the console, and all user interaction happens in the browser.
Install TelAnalysis using the standard method and run the main. file:
git clone https://github.com/krakodjaba/TelAnalysis.git
cd TelAnalysis
pip install -r requirements.txt
python3 main.py

In the console, the script will output just a link to the dashboard. When you open it, a minimalist interface will load in your browser. Just upload the JSON dump of the chat you want to analyze.
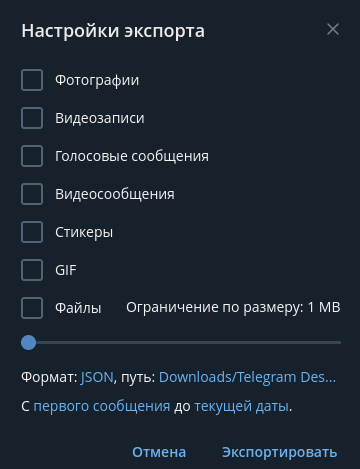
Creating the JSON dump is straightforward: open the official Telegram client, find the chat you’re interested in, click the three-dot menu in the top-right corner, and select “Export chat history.” In the export settings (see the screenshot below), choose the JSON format and the destination folder. You don’t need to export files, images, or your favorite voice messages—TelAnalysis only accepts text, so exporting anything else is a waste of time.
Now save the exported file in a convenient location and upload it to the dashboard.
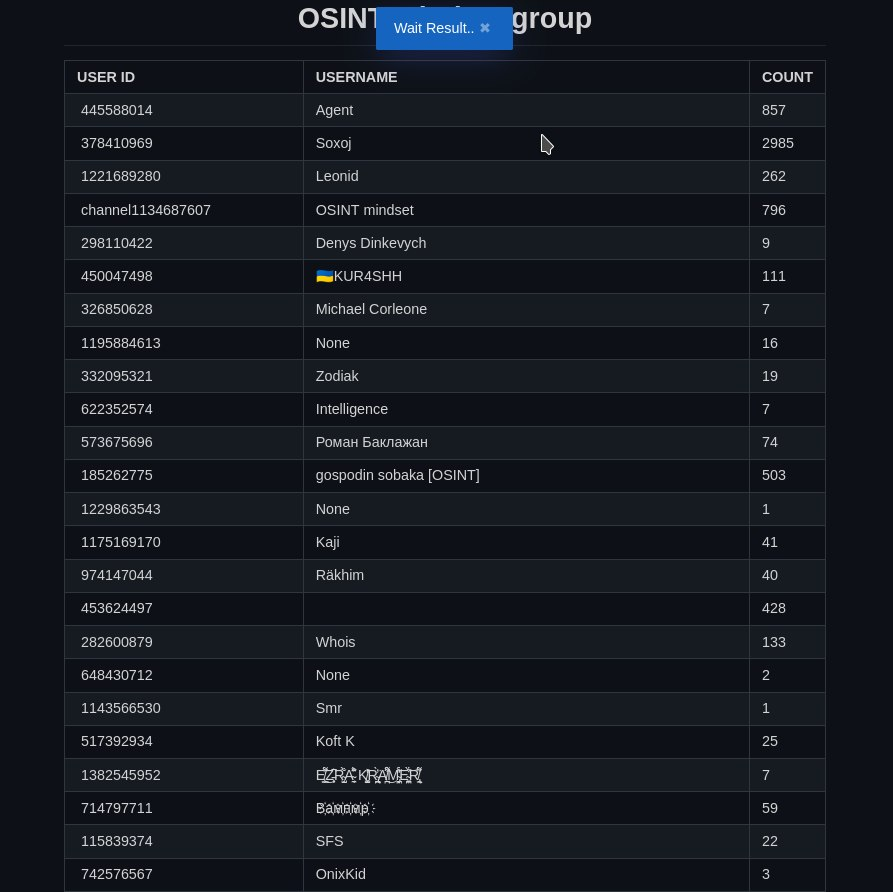
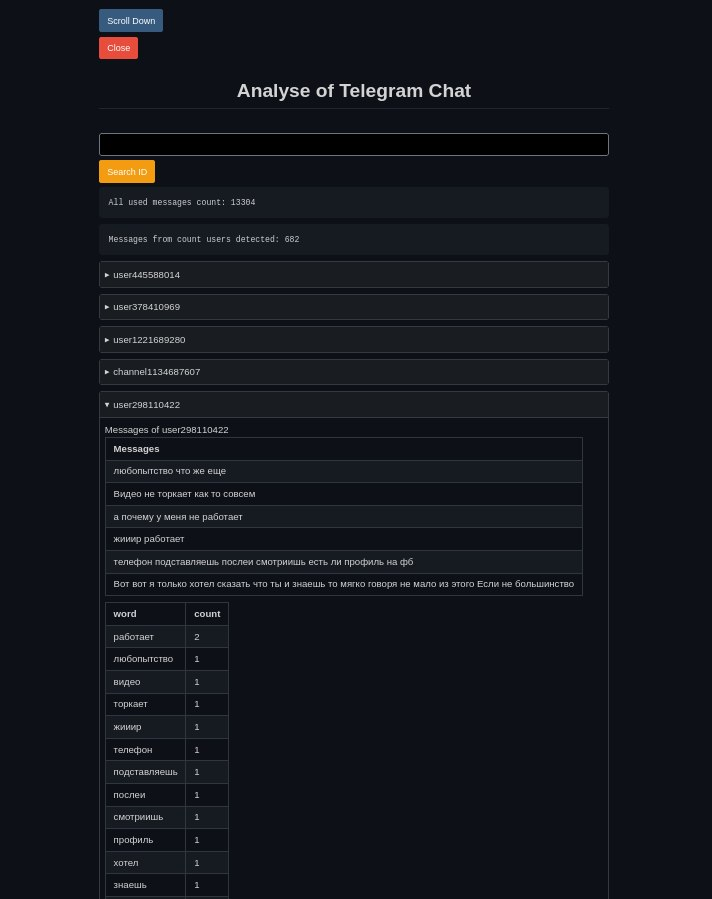
The user list shows who has posted in the group and how much, and it also includes an ID so you can track messages from the same person even if they change their username.
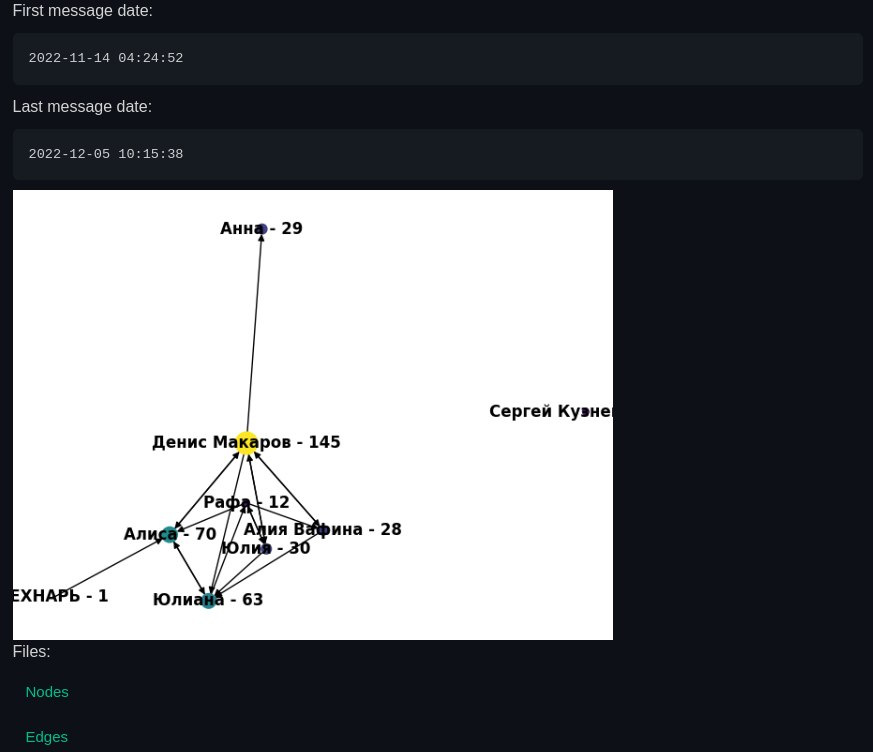
The graph doesn’t look great, but the relationships between users are visible.
Now let’s generate a tag cloud. It doesn’t look great either, mainly because stop words haven’t been removed. That’s easy to fix, though. If you decide to tackle it, don’t forget to open a pull request to the author.
The last feature lets you display messages by user ID. Personally, I haven’t found a use for it yet, since Telegram already has a more convenient search by sender.
Conclusion
The tools we covered today are hardly the only ones out there, and you might know options that are even better or more useful. If so, don’t hesitate to send us a link by email (contacts — below) or drop a comment. Any feedback is valuable—who knows, we might have enough for another installment of this roundup.
