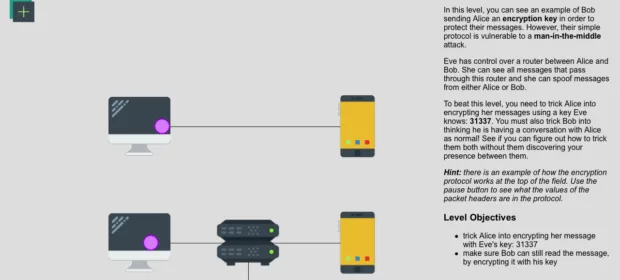
If you’re just getting into hacking, it helps to learn how networks work and what the basic attack types look like. If you feel shaky on the topic and want to walk through common scenarios in detail…
CONTINUE READING 🡒 Author: apismenny
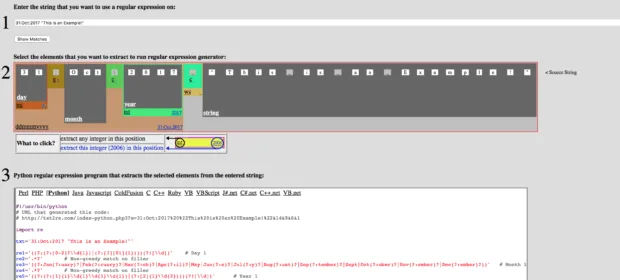
txt2re: Regex Generator for People Who Hate Writing Regular Expressions
Regular expressions let you parse strings and text files quickly and elegantly—but only if you know the syntax well and have some experience. Otherwise, they turn into an eldritch horror, and prolonged exposure may cost you your…
CONTINUE READING 🡒 macOS Setup Guide: Hidden Settings, Essential Apps, and Under-the-Hood Tweaks…
You’ve probably heard the line that Apple makes all the decisions for you and there’s nothing you can really customize in macOS. The first part is true; the second, in my view, is utter nonsense. macOS has…
CONTINUE READING 🡒 What Data Google Has on You—and How to Export It…
As everyone knows, Google stores a vast amount of data about its users, a point it’s constantly criticized for. In response, Google built a tool that lets you export and download all your data. The service is…
CONTINUE READING 🡒 Top 5 Web-Based Emulators for Classic Operating Systems and Retro…
Modern computers and browsers have reached impressive performance levels. Ten years ago, an interactive web app felt like a marvel; now JavaScript powers not just games, but even full-fledged emulators of vintage computers. We’ve picked a few…
CONTINUE READING 🡒 iSH: A Pocket Linux Environment for iOS
Apple’s restrictions on iOS and its apps haven’t stopped people from trying all sorts of things with the system. iSH is one of the latest attempts to shoehorn a Linux shell onto the platform, and it runs…
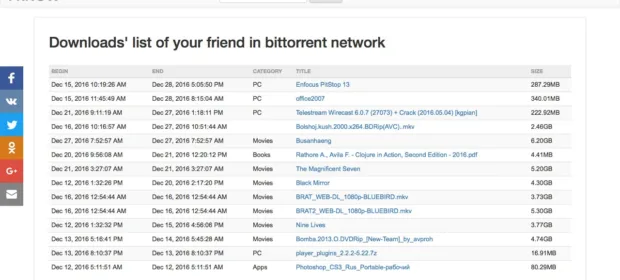
CONTINUE READING 🡒 I Know What You Downloaded: A Website That Tracks Who…
The site’s name translates to “I Know What You Downloaded.” Its creators built a system that monitors public torrents to log lists of files downloaded via BitTorrent and the IP addresses of peers. If you download torrents…
CONTINUE READING 🡒 WebSDR: A Browser-Based Gateway to Software-Defined Radio (SDR)
They say that once you dip your toes into SDR (software-defined radio), you fall down the rabbit hole—buying all sorts of gear and tinkering with it. If that warning doesn’t scare you off, the WebSDR site is…
CONTINUE READING 🡒 Setting Up a Personal Cloud with Nextcloud: Is It Worth…
“Should I install some software to make it easier to organize files on the server, share them, and access them from my phone?” I thought, and that’s when everything started to unfold! Even though my initial needs were modest, I decided to first take…
CONTINUE READING 🡒