Since we mainly analyze Windows executables and dynamic libraries, I limited the selection to PE editors that run on Windows. If a tool also supports other operating systems and their executable formats (e.g., ELF), that’s a nice bonus, but it isn’t particularly important for our purposes here.
We’ll choose tools based on sensible, transparent factors: functionality, price, ease of use, and update frequency. There’s no point in considering ancient solutions designed to edit binaries for MS-DOS or Windows 9x. If an editor is commercial, we’ll use the trial version and explicitly note which features are available there. But the ultimate yardstick will be whether it can crack a real crackme.
Instead of wasting time building a test target, we’ll use an existing one—passCompare35. That’s what we’ll use to try out different tools. Honestly, to crack our simple crackme, a PE editor doesn’t need a huge feature set: just navigate to the specified address and patch the instruction (ideally in a disassembly view). Manually poking bytes in a hex dump isn’t my idea of fun (probably not yours either), so we’ll count a built-in disassembler as a must-have feature.
As you’ll recall, with the debugger we found the address of the instruction (see part four of the Fundamentals series) that controls program flow when a password is entered. And using the info from part three, we converted that virtual address to a file offset on disk. So by going to address 0x402801 in the executable and replacing the test instruction with xor, we end up with a program that accepts any password. Enough talk—let’s do it!
PE-Explorer

Developer: Heaventools Software
Site: http://www.heaventools.ru/pe-explorer.htm
Latest release date: October 2009
Price: $129 — personal license
At number one is the widely used PE Explorer. Unlike its sibling, Resource Tuner, it can edit not only an application’s resources but also its code. Despite its age, it still works reliably on Windows 10. Unfortunately, PE Explorer only supports 32-bit files, and attempting to open a 64-bit binary results in an error.
The utility packs a lot of capability: it shows every element of the PE header, identifies which DLLs are referenced, predicts program behavior and how it interacts with other modules, and can even unpack binaries packed with UPX, UPack, or NSPack. It also lets you view and edit PE sections, inspect import and export tables, and verify the presence and integrity of a digital signature. As the icing on the cake, it includes a full-fledged disassembler.
That’s the claim—now let’s see how it holds up in practice. Since it’s a paid product, I used the 30-day trial. There was no indication of any feature restrictions.
Launch the editor and open our test application right away. PE-Explorer first displays information about the PE file header. To view details on other sections, just click the buttons on the toolbar. Click the Disassembler icon to open the dialog for selecting supported instruction sets—SSE, SSE2, and so on. Choose what you need and start the process by clicking Start .
In the window that opens, most of the space is taken up by the disassembly listing, with a hex dump just below it. If you select the Strings tab in the lower pane, you’ll see all the strings in the target application. You could use search to find the correct password there, but you’d have to sift through a hefty list of strings, so let’s keep that approach as a last resort.
Since we used the debugger to find the address of the instruction that controls the program’s execution flow, let’s look up this address in PE Explorer: press Ctrl+F (or Search → Find) and enter the address to search: 402801.
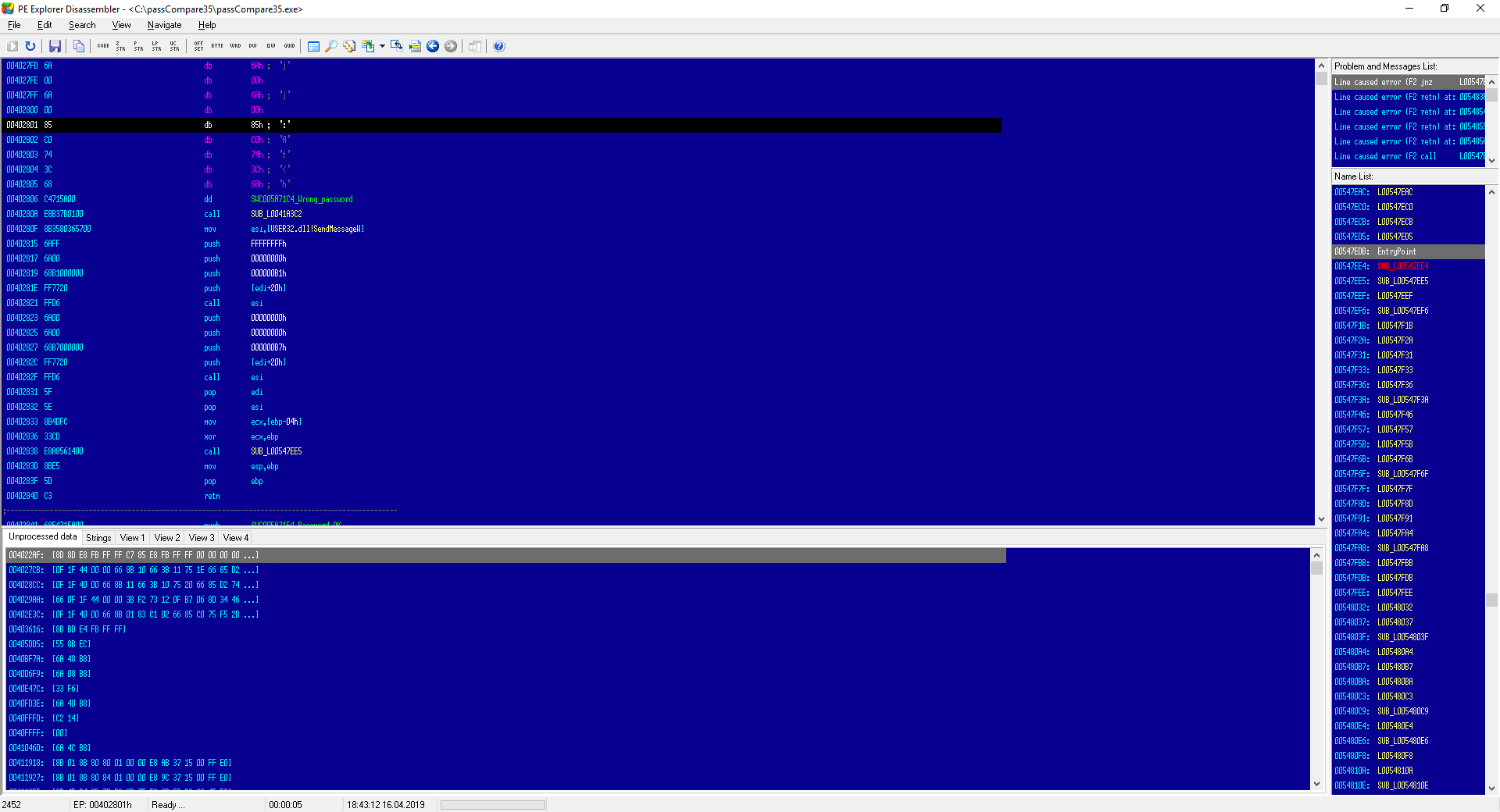
Well, I’m a bit disappointed with the disassembly result. Even the debugger shows a test instruction at that spot, but here I only see the beginning of its hex encoding: 0x85. And I can’t edit the code! What’s the point of all these features if the tool won’t let me do the most basic thing?
I can’t even chalk this shortcoming up to demo limitations, since there’s no clear information on how it differs from the paid version. I’ll concede that for its intended use—static analysis of an application and its execution flow—it likely performs well. However, it doesn’t meet our requirements, so I’m crossing PE-Explorer off the shortlist.
FlexHex

Developer: Heaventools Software
Website: http://www.heaventools.ru/flexhex-hex-editor.htm
Latest release date: July 2018
Price: $59.95
I think the developer deserves another shot, so let’s look at another Heaventools Software utility—the FlexHex hex editor. It’s a tool for editing arbitrary files, processes, or devices in binary, ASCII, and Unicode. According to the authors, it can handle truly massive files—up to 8 exabytes. It also supports a wide range of data types: bytes, words, doublewords, quadwords, various signed and unsigned decimal values, and 32- and 64-bit integers.
Users can define complex data types themselves—structs, unions, arrays, enums, strings, and any combinations thereof. The tool promises direct editing of any values, including hexadecimal and string data, as well as modifications to memory regions and typed data. It supports bitwise operations (NOT, AND, OR, XOR on data blocks) and, of course, arithmetic operations: addition, subtraction, multiplication, division, and modulo.
FlexHex’s standout feature is its ability to compare entire files or individual blocks. Comparison maps make the process more intuitive and easier to visualize.
All well and good, but how will the tool handle the crack—our simple little challenge? The absence of a disassembler immediately suggests we’ll have to work in hex. Launch FlexHex and use it to open our crackme.
First, let’s try to find the offset 402801. Click Navigate → Go To, select Address in the list on the left, and enter the value to search for in the Enter address field. Make sure the Hex mode is enabled, then click Go To.
However, the search result takes us well beyond the application’s bounds. Note that the last readable characters are at offset 0x3659F0. If you think back, you’ll recall the PE header lists the image base (module load address) as 0x400000. And here it isn’t even being taken into account!
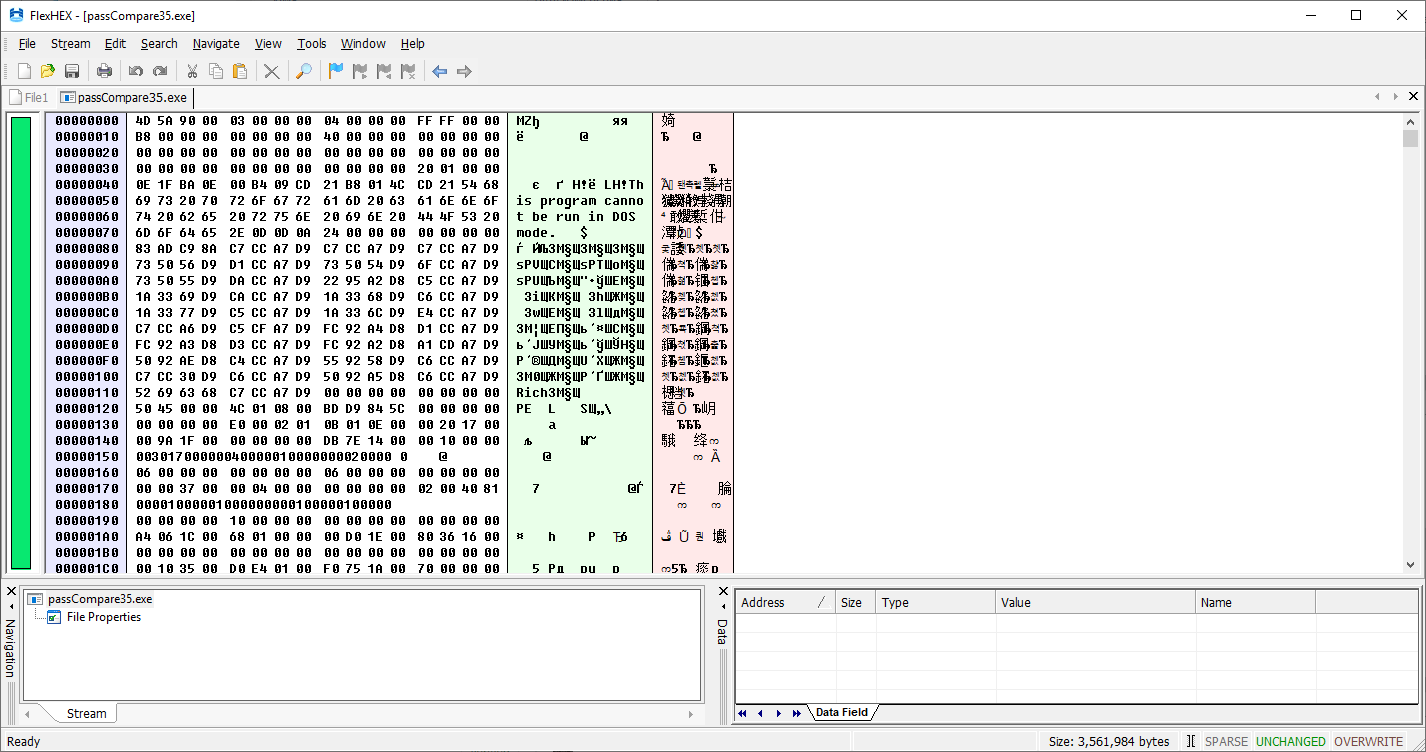
Alright, as Grandpa Lenin said, we’ll “take a different path.” Strictly speaking, FlexHex doesn’t understand the PE format, so it can’t be considered a full-fledged PE editor. That leaves us with patching the bytes by hand. From the same debugger where we found the password-check instruction, we’ll take a unique byte sequence: 85 . It corresponds to the following assembly instructions:
test eax, eax
jz 0x402841
push 0x5A71C4
I chose such a long pattern to avoid false positives. The key byte 0x74 here is the opcode for the JZ instruction. To turn it into JNZ, just change it to 0x75. As a result, we get a program that accepts any password except the correct one.
Using Search → Find, open the dialog and set the search type to Hex Bytes and choose the direction. In the input field, enter our byte sequence: 85 . We have a match! Now place the cursor on 74, press Delete, and type 75 in its place. Save your changes and close the editor. Test the “patched” application—it should now work noticeably better. 🙂
Overall, I wouldn’t say this editor is particularly user-friendly or well-suited to the realities of a professional reverse engineer’s workflow. Personally, I wouldn’t shell out my hard‑earned $60 for it.
Radare2

Developer: pancake
Website: https://radare.org/
Latest release: October 2018
License: LGPL
Next up is a massive cross-platform application made up of many modules and maintained by a large community of professional developers and enthusiasts. Interestingly, it all started as a lone hacker’s project. Today, Radare2 is a full-fledged framework for analyzing and reverse-engineering any binary files, including executables.
Radare2 follows the Unix philosophy: do one thing and do it well. As a result, it consists of several narrowly focused utilities, brought together under one roof via the Cutter GUI wrapper, written in Qt. The framework includes a debugger with support for a wide range of architectures: x86-64, ARM, MIPS, and many others.
You can write Radare2 scripts in multiple languages, including Python, Go, and others. Beyond Windows, Linux, and macOS, the framework also runs on Android and iOS (though you’ll need to jailbreak the latter). Not bad for a tool that originally targeted Unix-only environments!
Let’s use it to tackle our crackme. You can download the Cutter GUI along with its bundled tools from GitHub. After you select a file for analysis, the program will prompt you to set the parameters it will use to open the binary. These include architecture, word size (32/64-bit), operating system type, CPU type, endianness, load mode, whether to use virtual addressing, and so on. After that, the framework will take a few seconds to analyze and process the file.
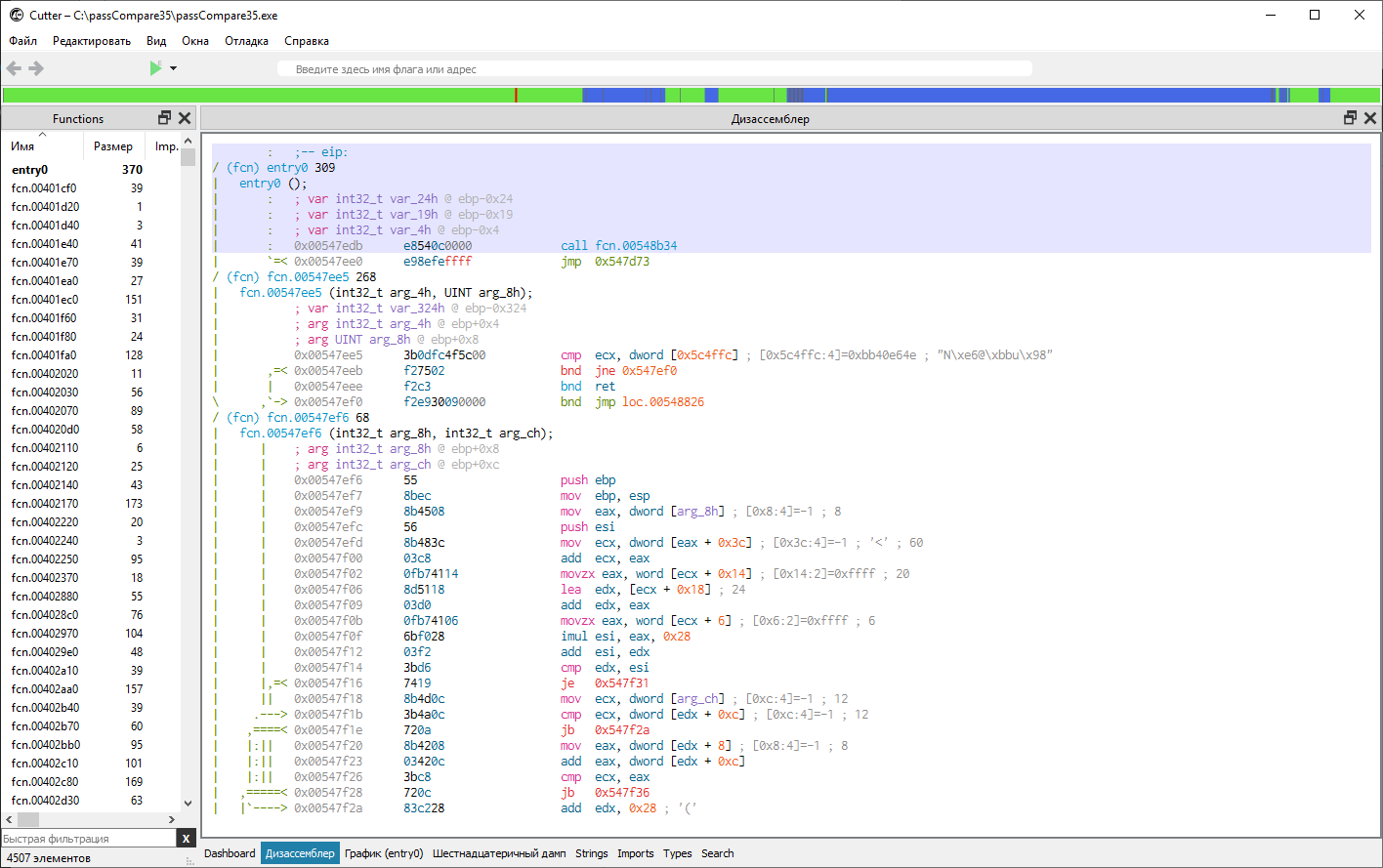
By clicking the buttons at the bottom of the window, we can switch between tabs: disassembler, hex dump, and more. That’s encouraging. With any luck, one of these views will let us crack this crackme. Enter the address 0x402801 into the search bar at the top of the window.
Unfortunately, the results once again lead us into inaccessible territory. Searching for the byte sequence 85 didn’t help either. The query in the Search tab failed in both cases.
I won’t rule out that I didn’t dig deep enough into Cutter and Radare2, but I couldn’t get the hack working with these tools. That said, keep in mind that Radare2 isn’t just a simple editor—it’s a full-fledged disassembler intended for somewhat different tasks.
PE-bear
Developer: hasherezade
Website: https://hshrzd.wordpress.com/pe-bear/
Latest release date: January 2019
Price: Freeware
After numerous user requests and a four-year hiatus, the author resumed development of this PE editor in 2018. You can find the repository on GitHub. It features a GUI built with Qt and includes a built-in disassembler. There’s also a clear, highly detailed summary of the PE header and related metadata. You can open multiple binaries at once, with a convenient comparison view.
That tool isn’t suitable for our scenario: it lacks features for searching and editing binary files. Still, I liked the YouTube channel, so I decided to include the utility in the list.
Hiew
Developer: Eugene Suslikov
Website: http://www.hiew.ru/
Latest release: February 2019
Price: 555 RUB
I have to admit, by this point the PE editors on the market were starting to disappoint me. None of the ones I looked at support jumping to an offset relative to the module’s load base (RVA). On top of that, I’d really like to edit assembly code and have a search function to save time and effort. Let’s see if Hiew can deliver all that—a tool whose first release dates back to the early 1990s.
Originally, the program was free, so you can still download version 6.50 from the developer’s site. But that’s really only worth it for nostalgia—there’s little practical value. That release was made for MS-DOS and won’t run on Windows 10.
It’s worth noting that Hiew doesn’t rely on any third-party libraries, SDKs, or APIs; it’s implemented entirely at the native level. In other words, the developer avoids depending on operating system services. That’s why, up to version 7.0, the program ran not only on Windows but also on MS-DOS and OS/2. Support for the latter platforms was dropped as it was no longer practical.
In its current 8.67 release, Hiew is a true Swiss Army knife: it packs an exceptionally broad feature set that can handle almost any task a user throws at it. Key capabilities include viewing and editing files in text, hexadecimal, and disassembly modes; a built‑in x86‑64 assembler and disassembler; a powerful 64‑bit calculator; and support for executable files in a wide range of formats.
In addition, the utility lets you work with logical and physical disks, perform block-level operations of arbitrary size (including read, write, delete, and move), run multi-file search and replace, and do pattern-based searches in the disassembler.
That’s already an impressive list, but for those who want even more, you can create Hiew External Modules to tailor the editor to your needs. Unfortunately, most of the features mentioned don’t work in the demo version, so I decided to buy a license—the cost is absolutely justified in this case.
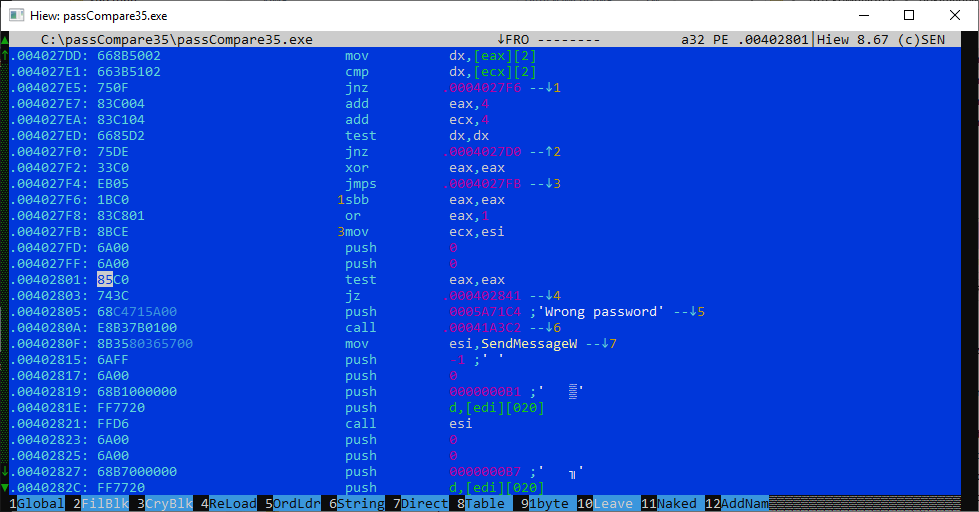
Alright, let’s crack our little crackme with Hiew—just for demonstration. Launch hiew32.exe and, in the file selector, choose our target, passCompare35.. Open the disassembler with F4 and select the Decode mode. Note the offset: it starts at 400000, the module’s base address. Jump to 0x402801 by pressing F5. You’ll land right where we need to be, on the verification instruction test, which we’ll patch to xor. Press Enter again to apply the change, then F9 to write it to disk. Done—quick and clean!
010 Editor

Developer: SweetScape Software
Website: https://www.sweetscape.com
Latest release: December 2018
Price: $49.95
Another paid editor with a full one-month trial. Is it worth the money? The feature set is actually quite impressive. It offers advanced support for binary templates, including searches by a specified structure or high-level language constructs (such as if, for, or while). You can perform byte-by-byte comparisons of two files and generate histograms to visualize the data.
Additionally, the tool promises to help with analyzing and modifying process memory. Some features can be automated by writing scripts in its built-in C‑like language. Overall, it definitely deserves your attention—and it almost feels wrong to limit today’s overview to a basic example.
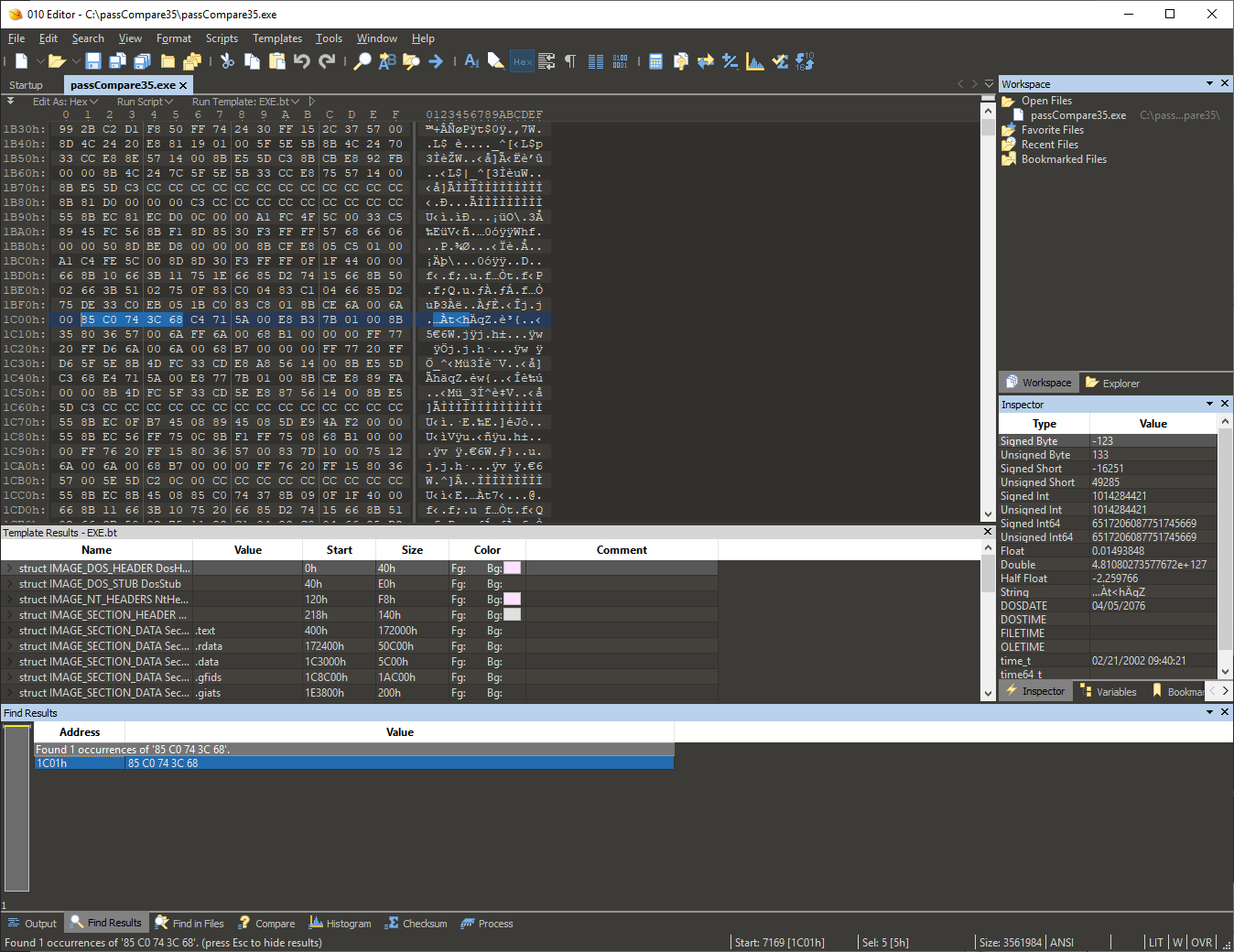
Open our file passCompare35. again and find the code snippet we need. Remember, the magic bytes look like 85 . Replace the middle byte and don’t forget to write the changes to disk. Test the patched program and make sure it behaves exactly the way we want. Next!
XVI32

Developer: Christian Maas
Website: http://www.chmaas.handshake.de/
Latest version release date: June 2012
Price: freeware
%divTo wrap up, let’s test a popular hex editor that’s available for free. According to its author, the tool has seen widespread success, is listed as recommended tooling in the Hacker’s Guide, and is even used at Microsoft. Otherwise, there’s nothing particularly unique about it, so we’ll quickly check whether it can handle a basic crack and then sum up the results.
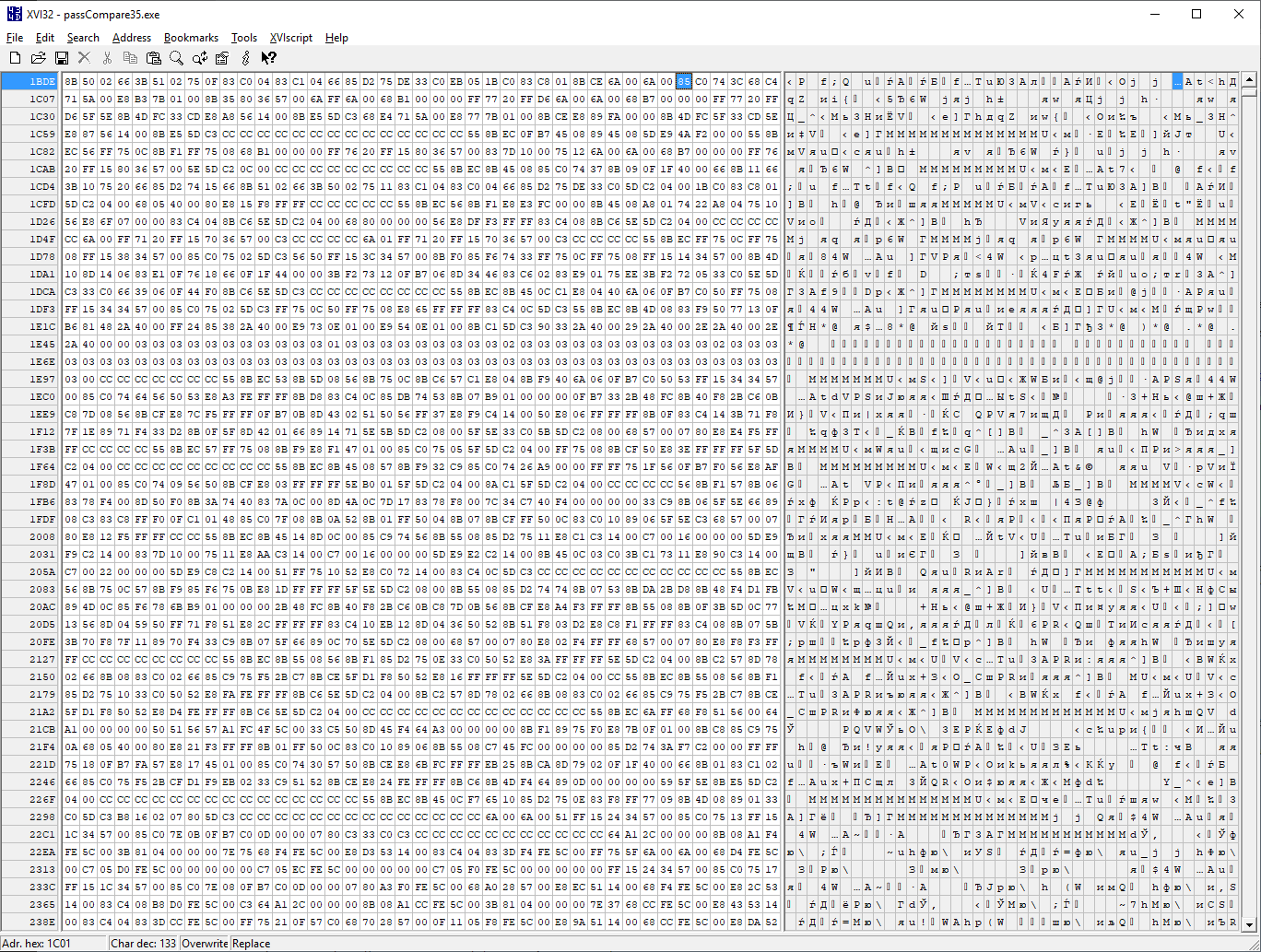
We open our crackme and use the familiar Ctrl-F to search for the byte sequence. The tool quickly finds the fragment, and all that’s left is to swap in the replacement. Done. So easy it’s almost a letdown.
Conclusion
Our review covered both commercial and free tools. Each had its own twist—a standout feature that set it apart from the rest (even if it was just the author’s YouTube channel). Since I prefer to locate the cracking routine with a debugger, all I need in an editor is to jump to the discovered address and patch the necessary instructions. After testing seven popular utilities in this article, I concluded that the good old Hiew best meets my needs.
