If you feel like you’re being watched, you probably are. The sites you visit collect extensive information about your computer, phone, or tablet, as well as the software you use. They don’t just set cookies—they can determine your geolocation, IP address, ISP, OS and browser versions and language settings, local time, and your connection type and speed. They can also see which protocols your browser supports, which plugins are installed, whether JavaScript is enabled, whether the device has a built-in camera or gyroscope, and much more.
Using all this information, every device on the internet can be assigned a unique identifier—a browser fingerprint. Even if you change one or several system settings, you won’t actually change the fingerprint, because it’s derived from many different parameters. If someone is determined, they’ll still be able to recognize you.
Moreover, different browser engines render fonts and individual Unicode glyphs slightly differently. By comparing how text-filled HTML elements appear on web pages in your browser with the default letterforms in catalogs of known typefaces, it’s possible to build font fingerprints. These fingerprints help websites identify any browser—yours included.
Most often, this kind of identification is used to serve ads. That sounds harmless enough, but there are caveats. In 2014, researcher Aleksandr Kogan, commissioned by Cambridge Analytica, built a Facebook quiz app called “This Is Your Digital Life.” Even though only a relatively small number of people took the quiz, the app was able to access not just their profiles but also the profiles of everyone on their friends lists. As a result, data on roughly 80 million Americans was collected— including location, hometown, date of birth, post likes, interests, online activity, preferences, and family connections. All of this happened without users’ knowledge or consent.
These days, when even an ill‑considered “like” on someone else’s post can have unpleasant consequences, sharing that much data with the world is an unjustified risk. The takeaway is clear: use browsers designed with privacy and security in mind. Tor Browser is widely regarded as one of the safest options. However, it’s geared less toward protecting everyday browsing on the public internet and more toward accessing Darknet content and navigating the onion network. For that reason, we won’t be diving into it here.
There are several alternative browsers designed to protect privacy and anonymity online. Let’s look at the most well-known ones and compare their capabilities. To assess what information these browsers expose to the outside world, we’ll use BrowserLeaks. To inspect network traffic, we’ll use the free Portmaster app, which makes it easy to track connections made by specific applications. We’ll run each browser with its default configuration, without changing any settings.
Brave
- Website: https://brave.com
- Engine: Chromium
- Source code: Open-source
- Initial release: 2019
- Platforms: Windows, Linux, Android, iOS, and macOS (including ARM-based)
The Brave browser is built on Chromium and is open source. From a security standpoint, that’s an advantage: anyone with programming skills can review the code and verify there are no backdoors or other potentially risky features.
Brave uses Blink as its rendering engine, V8 for JavaScript, and on iOS it relies on Apple’s WebKit. It’s developed by Brave Software, Inc., a U.S. company based in San Francisco. Brave is available for Windows, Linux, Android, iOS, and macOS (including ARM-based builds). Its first release is relatively recent—November 13, 2019. The developers claim that even with default settings Brave effectively blocks ads, prevents tracking, and in Safe Browsing mode keeps no logs and does not store your IP address.
On first launch, Brave offers to block cookies, which improves browsing security. If you click the button in the top-right corner of the window and choose Settings, the settings screen opens. Privacy options are grouped under the Shields tab.
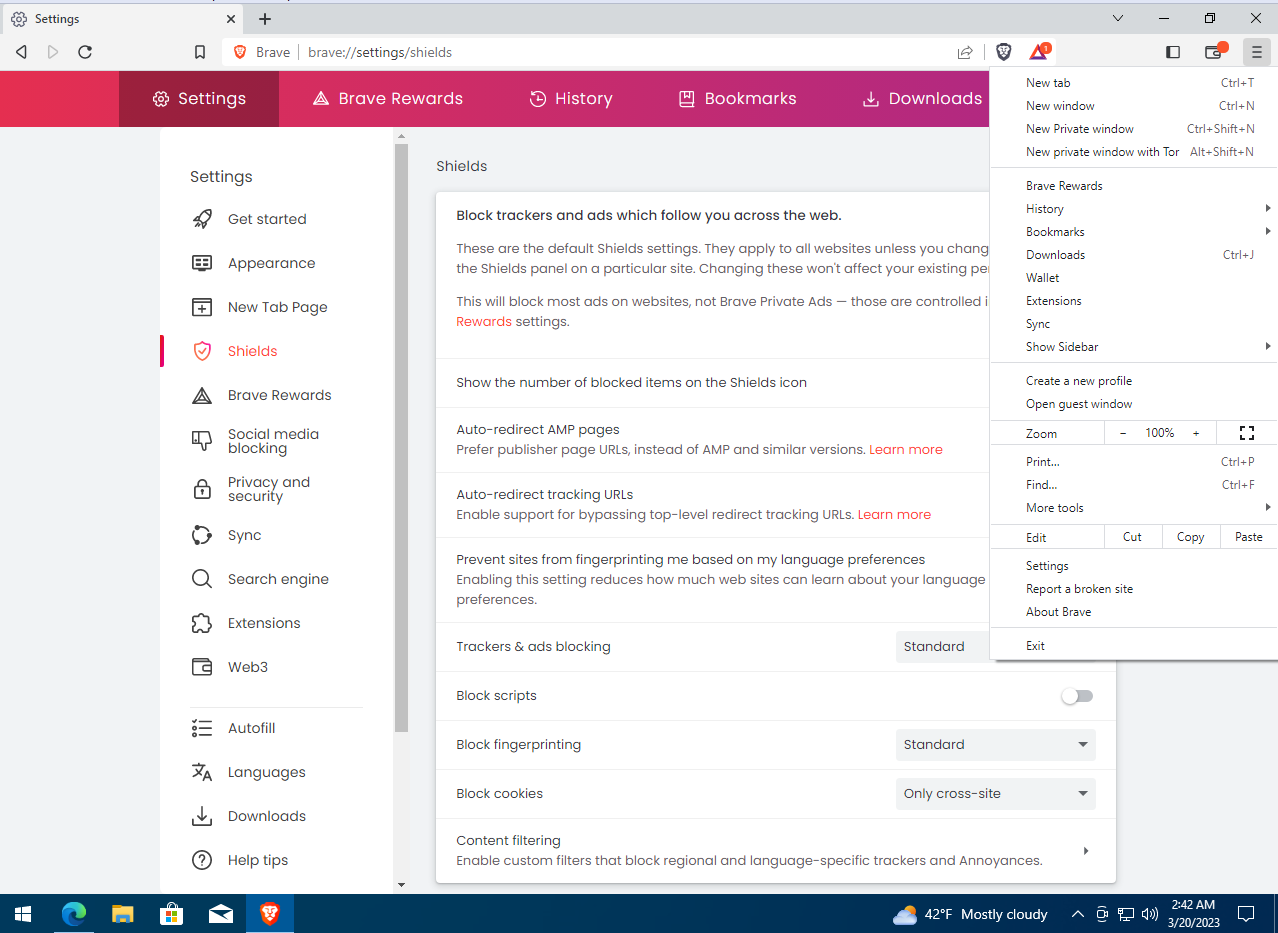
Here you can disable AMP auto-detection (Accelerated Mobile Pages for faster loading of mobile content), fingerprinting protection, and the redirect that prevents ad platforms from tracking your browser.
Below is a menu that lets you choose the privacy level for ad and tracker blocking: Standard (the default), Aggressive, or Disabled. You can also disable all scripts and enable cookie blocking here. Let’s select the Trackers & ads blocking — Aggressive mode.
If you click Content Filtering, you’ll see the list of filter lists Brave uses to block ads and trackers. To view everything, click Show full list. By default, only ten filters are enabled, but there are many more. You can turn them all on, but keep in mind: the more filters you enable, the more content gets blocked—which can hide useful elements on some sites.
Browsers typically store information about which social networks you’re signed into and will expose it to any site that asks. To turn this off, open the Social media blocking tab. By default it lists Google, Twitter, and Facebook, and for some reason LinkedIn exposure is enabled. You can disable it if you don’t want recruiters from Elon Musk’s companies reaching out to you.
On the Search engine tab, you can choose which search engine Brave uses by default. Because Google collects extensive data—logging your searches, link clicks, and activity across sites that embed Google Ads scripts—you may prefer DuckDuckGo for better privacy.
The BrowserLeaks site shows that, by default, Brave has JavaScript and WebGL enabled. WebGL is a JavaScript API for rendering 3D graphics, and it can let some sites determine the type of graphics adapter in your device. As a result, the browser readily exposes current OS and hardware parameters, including whether a microphone and camera are present. It also permits fingerprinting via the Canvas API and through font enumeration. That’s not great for privacy, but mainstream browsers typically leak even more user data.
BrowserLeaks shows that the browser has content filters active that block ads and tracking: there are ten such filters in total (mostly using uBlock). This means the program does, in fact, hinder ad networks from collecting data.
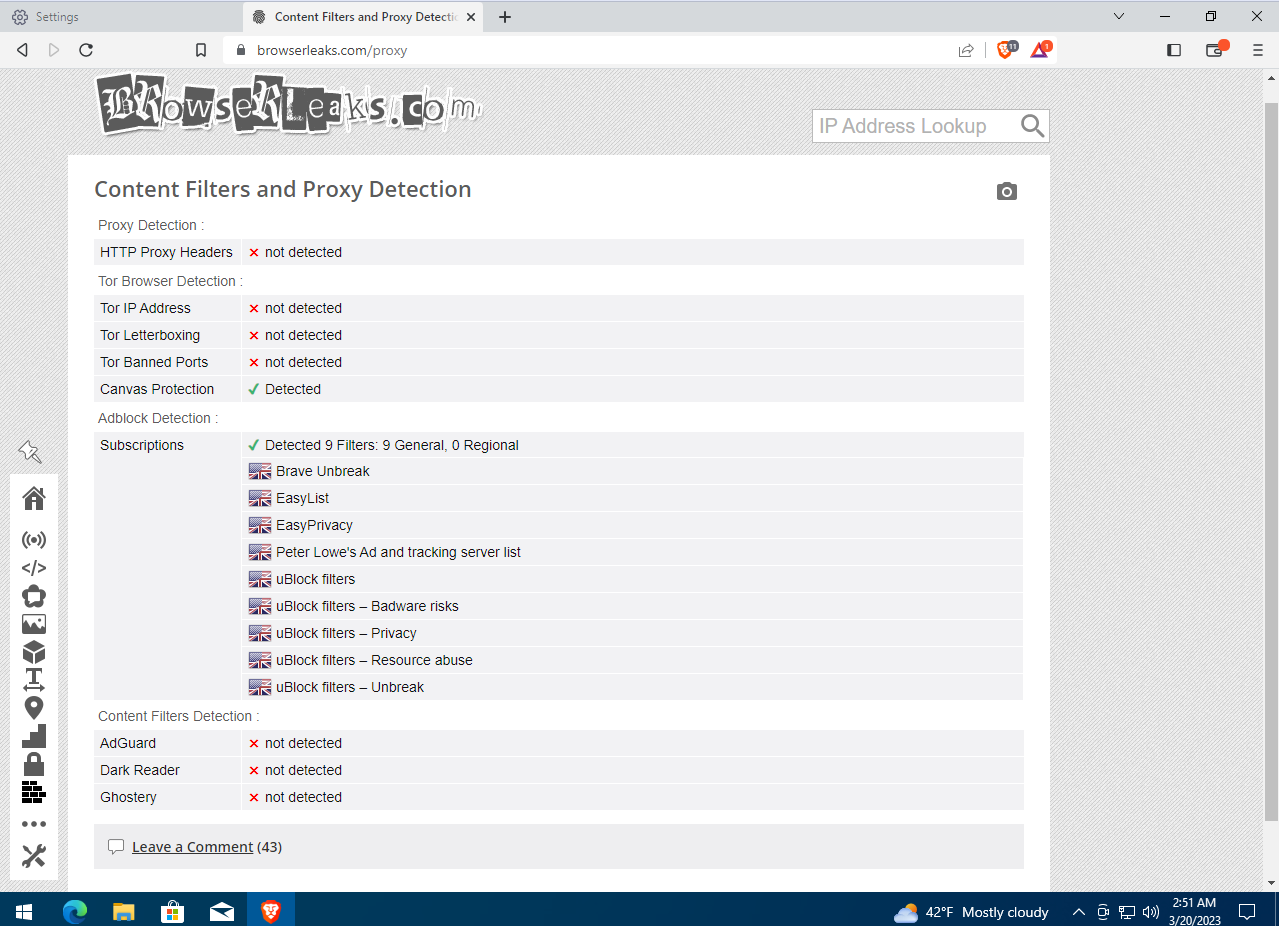
Even so, BrowserLeaks identified our IP address and location with pretty good accuracy—which isn’t safe. Fortunately, Brave has another great feature you won’t find in most privacy-focused browsers. Click the button on the right side of the toolbar and choose “New Private Window with Tor” to open a new browser window that routes your connection through the Tor network.

If we open the BrowserLeaks site in this window, we’ll see that our IP address and geolocation have changed. This lets you hide your real location without using a VPN. However, BrowserLeaks was able to determine that the new IP address belongs to a Tor exit node. Some sites block access from the Tor network, so keep that in mind.
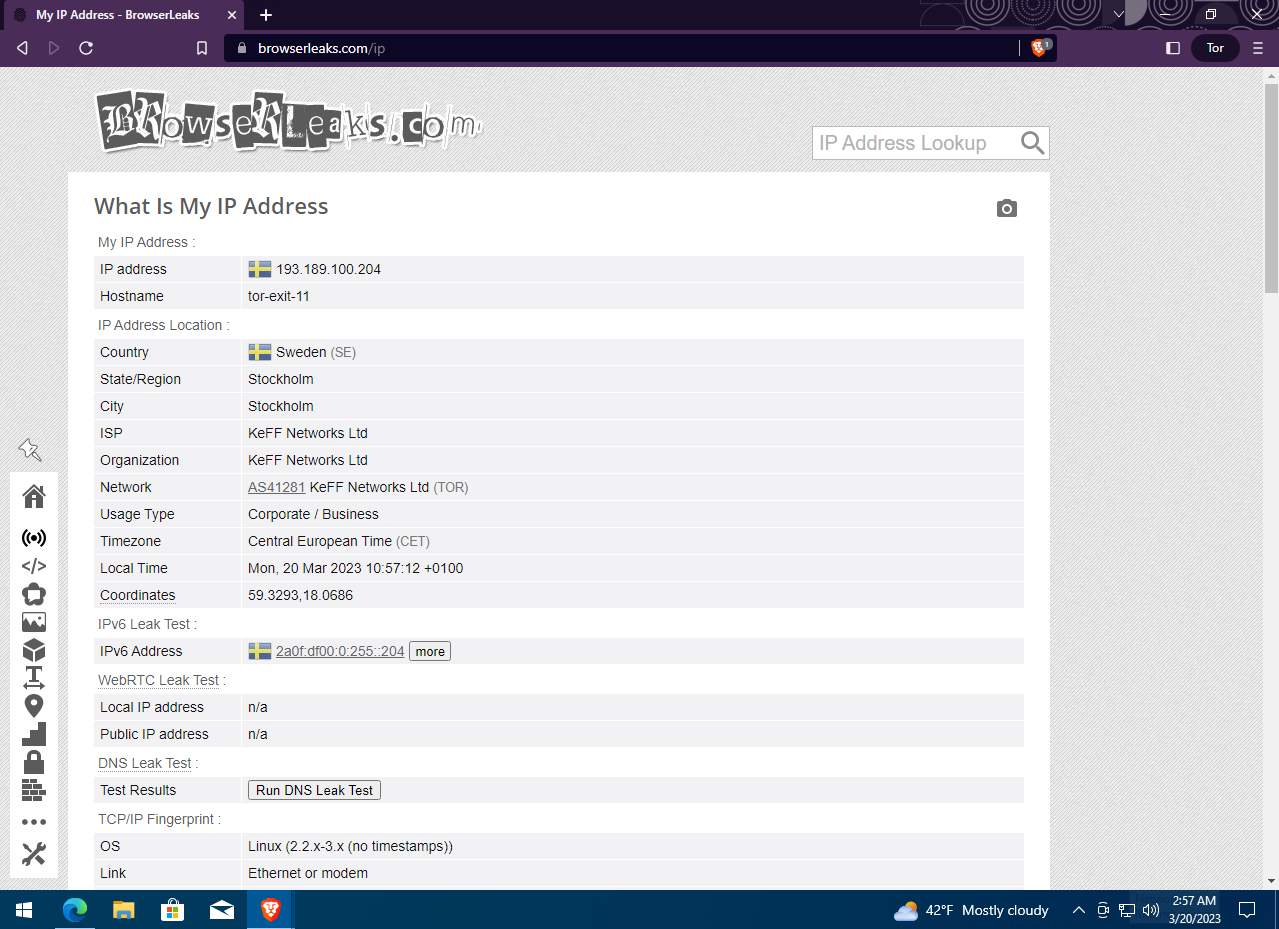
In this window, you can not only browse the regular web anonymously but also access Darknet resources in the .onion space. You no longer need two different browsers—one for private browsing of regular sites and another for the Darknet. Brave alone covers both.
Let’s use Portmaster to see what connections the Brave browser initiates. It regularly reaches out to brave.com update servers and uses its own DNS resolvers to handle queries, in addition to the DNS servers configured in the network settings. The browser doesn’t make any other suspicious requests.
Portmaster also shows that for browsing over Tor, Brave uses a bundled 32-bit Tor engine (version 0.4.7.13) that runs on 64-bit systems as well. This is the current release, published this month, so known vulnerabilities have been addressed and it provides a sufficient level of security.
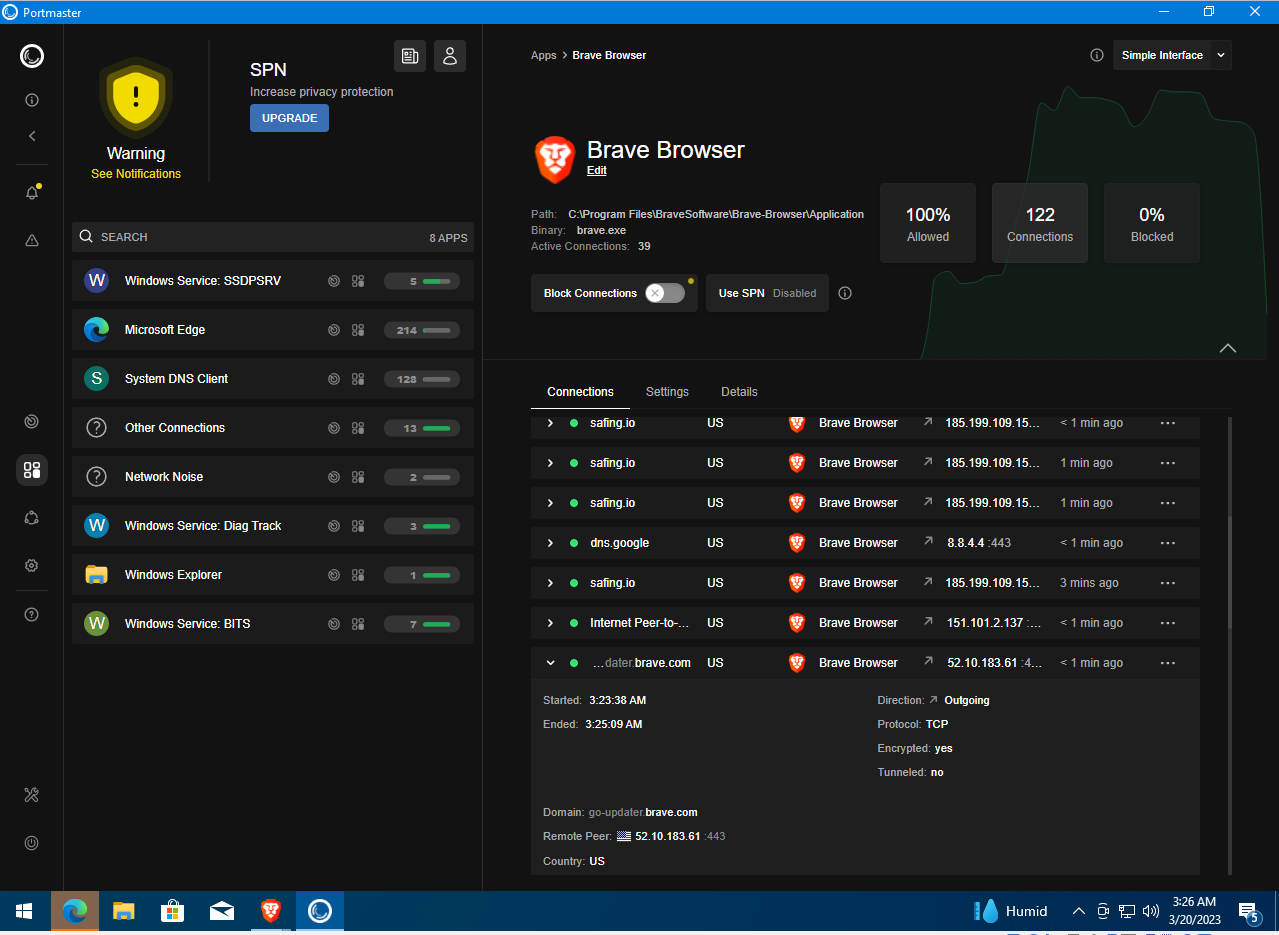
In effect, Brave can replace two browsers at once—a standard browser for private web browsing and the Tor Browser for accessing .onion sites. In use, it feels quite fast, though pages load more slowly in Private Window with Tor because traffic is routed through the Tor network.
Epic
- Site: https://www.epicbrowser.com/
- Engine: Chromium
- Source code: Closed source
- Initial release: 2013
- Platforms: Windows, macOS, Android
Like Brave, the browser is built on Chromium, but it’s a commercial, closed‑source product. It’s been developed since 2013 by Hidden Reflex, an India‑based company. Epic ships with always‑on, comprehensive ad blocking and does not retain browsing history. It also includes anti‑fingerprinting protections and disables form autofill—data entered into web forms isn’t saved locally. You can enable a built‑in proxy to mask your location. Epic blocks cookies and other tracking mechanisms, preventing sites from profiling the browser and collecting data for targeted ads. Versions are available for Windows, macOS, and Android.
One neat feature of Epic is that it lets you set privacy options per site, and there are plenty of them. To adjust these, open the site, click the umbrella icon, then select “View site settings.”
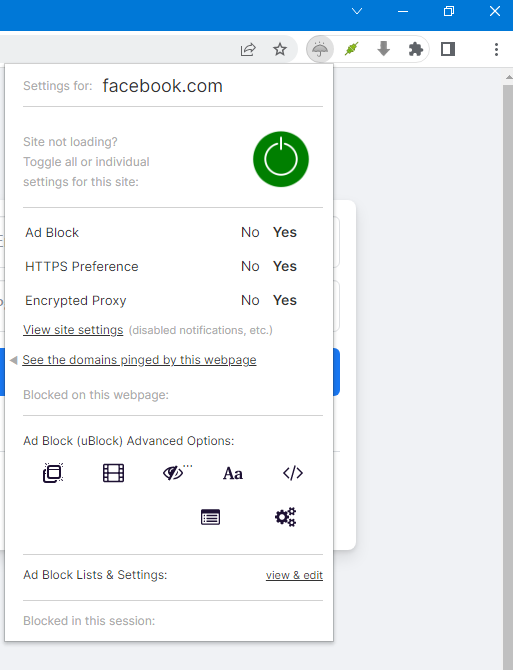
For the site currently open in your browser, you can block geolocation and prevent it from detecting whether your computer has a camera, microphone, or other sensors. You can also toggle JavaScript, image loading, and ad blocking on a per‑site basis. This is especially handy when you generally need JavaScript, or when anti‑tracking breaks sign‑ins, but you still want to keep it enabled on other sites.
Let’s turn on Epic’s Encrypted Proxy mode, visit BrowserLeaks, and see what we get.
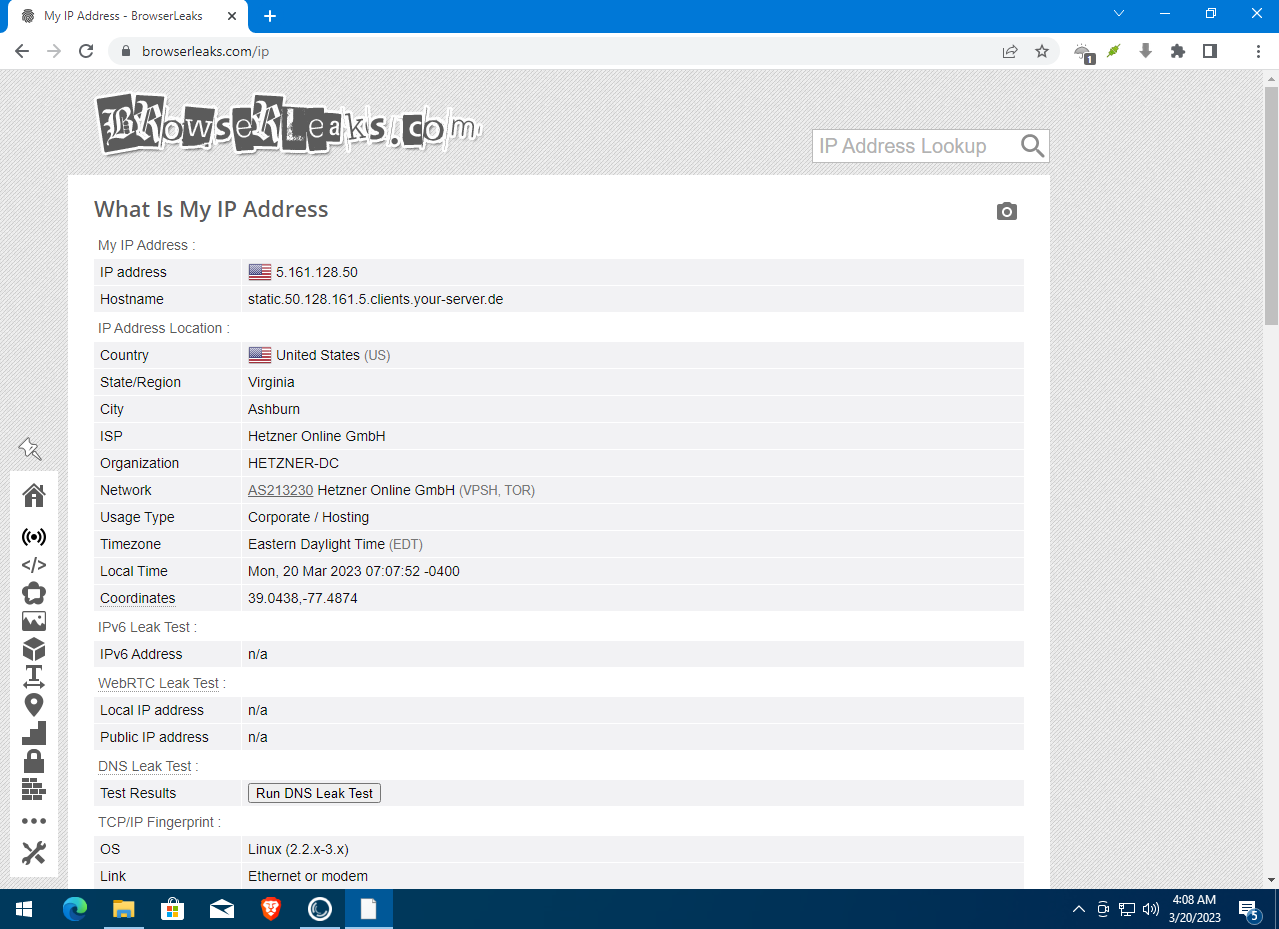
Great, our IP address has changed and BrowserLeaks couldn’t determine our location accurately. Now it shows us in Ashburn, Loudoun County, Virginia. We could visit Ashburn Park. I wonder if they allow feeding the squirrels?
To change Epic’s global settings, click the button on the right side of the toolbar and select Settings. The options here are the same as in regular Chrome and in the usual places. For example, you can configure how cookies are handled and clear your browsing history. In the Security and Privacy section, choose what data the browser shares with websites, and in Site Settings, disable geolocation for all sites at once.
Now let’s use Portmaster to see what connections the Epic browser establishes.
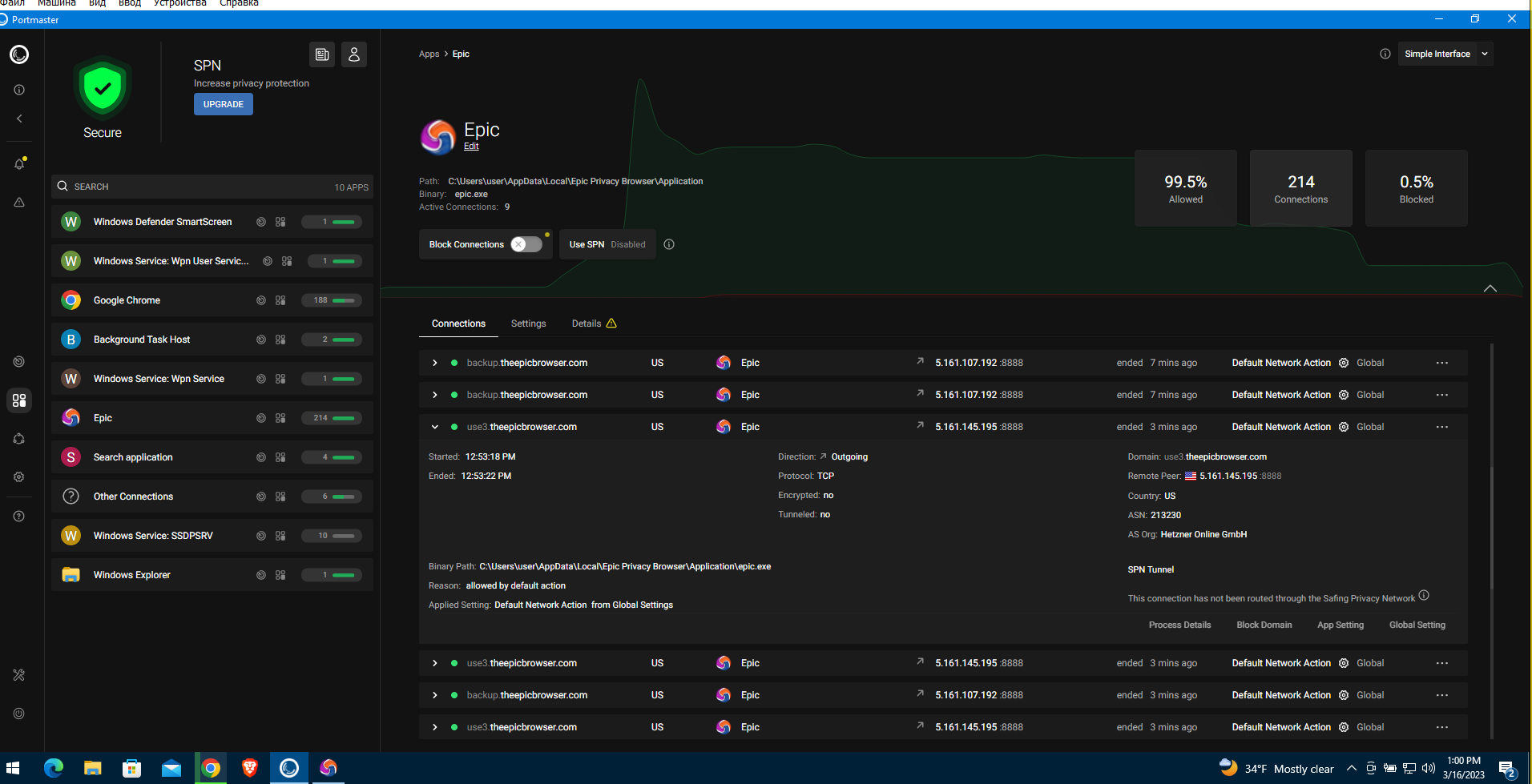
The browser actively communicates with the service domain theepicbrowser. using the Safe Privacy Network technology. If you inspect these packets in Wireshark, you can see that Epic regularly phones home to its developers, and the data sent via the Safe Privacy Network is encrypted. Apparently, Epic Browser transmits some telemetry to the company Hidden Reflex.
Epic has another interesting feature the developers hype on first launch — Epic Video Downloader. If you’re a pirate… uh, I mean a fan of videos or music, this feature lets you download clips from websites straight to your computer. Let’s try it, starting with YouTube. I found a great video with “metal ladies” dedicated to Atomic Heart. Open Video Downloader, copy the URL… Epic fail!
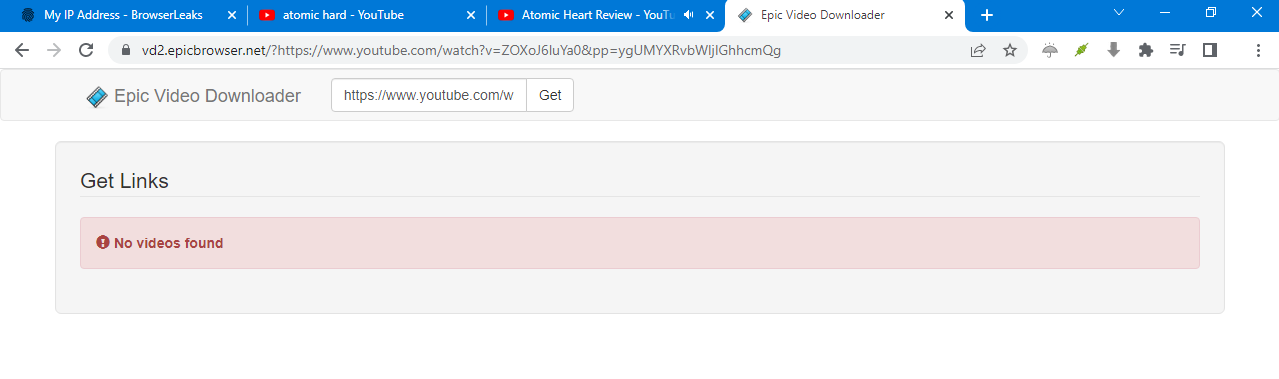
Okay, maybe Google is protecting its videos. Just in case, let’s check the browser settings: proxy is off, JavaScript is enabled. Let’s try the same on Vimeo. Another epic fail!
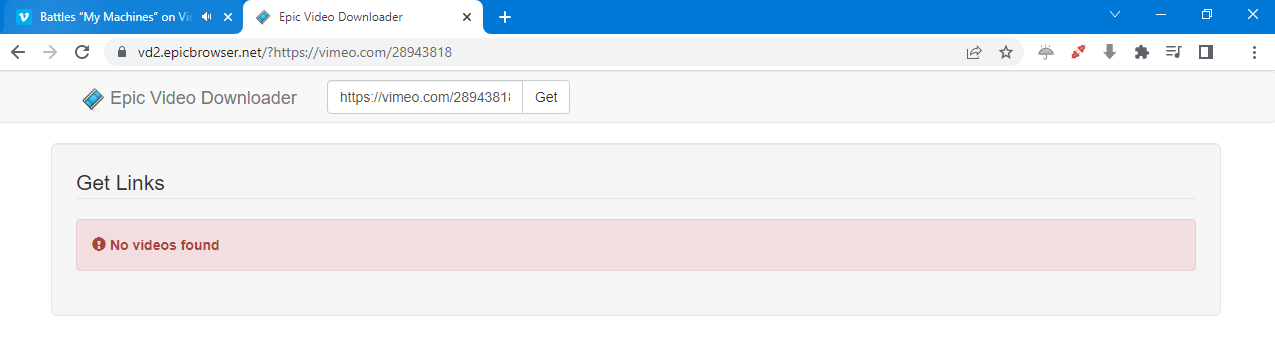
No doubt, the video download feature is useful. Unfortunately, it doesn’t seem to work—at least not on the most popular video platforms. Overall, Epic Browser does a good job blocking tracking and ads, and the Encrypted Proxy is a handy privacy tool for masking your real IP address. But if you’re paranoid, the closed-source code could still hold unpleasant surprises.
Avast Secure Browser
- Website: https://www.avast.com/secure-browser
- Engine: Chromium
- Source code: Closed source
- Initial release: 2016
- Platforms: Windows, macOS, iOS, Android
This is a security-focused browser from Avast Software, the company behind the Avast antivirus. It’s built on Chromium and is available for Windows, macOS, iOS, and Android.
The first version of this browser was released in 2016. It was originally called SafeZone and shipped with the paid edition of Avast Antivirus, but later became available for anyone to download. Anyone except users in Russia and Belarus—if you try to download the browser from those countries, it won’t work. That said, with a proxy or VPN, people haven’t reported issues downloading it.
The browser includes anti-tracking and anti-fingerprinting features that, according to the developers, make it harder to identify and track users. Avast Browser is also based on Chromium and is closed-source. Its interface will be familiar to anyone who uses Google Chrome, but unlike stock Chrome, Avast Browser adds a few extra buttons. For example, Privacy Guard is a panel where you can enable tracking and ad blocking for the current site.
The Extensions button is the standard Chrome control for managing plugins. The Security & Privacy Center button opens the browser’s privacy settings. Here you can enable or disable Privacy Guard and Web Shield—a web antivirus that protects users from fake and phishing sites. You can also turn off the Password Manager, which stores site passwords in encrypted form and lets you sign in with a single click.
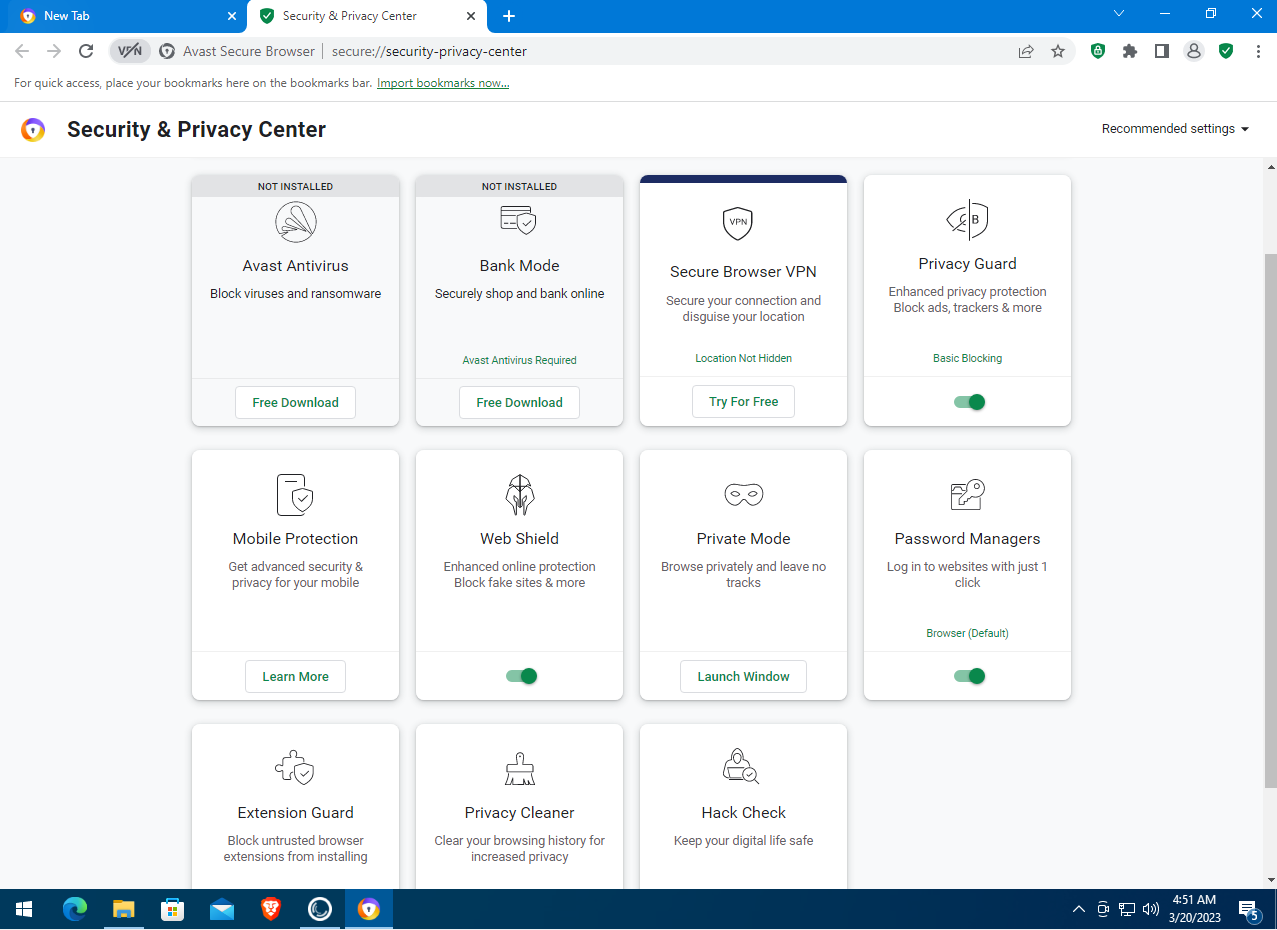
By default, Privacy Guard is set to Basic Blocking. But we want more privacy! Click the Privacy Guard button, then Privacy Guard Settings to adjust the configuration. Choose Strict Blocking to fully block browser fingerprinting, tracking, ads, and monitoring by websites and social networks… Oops!
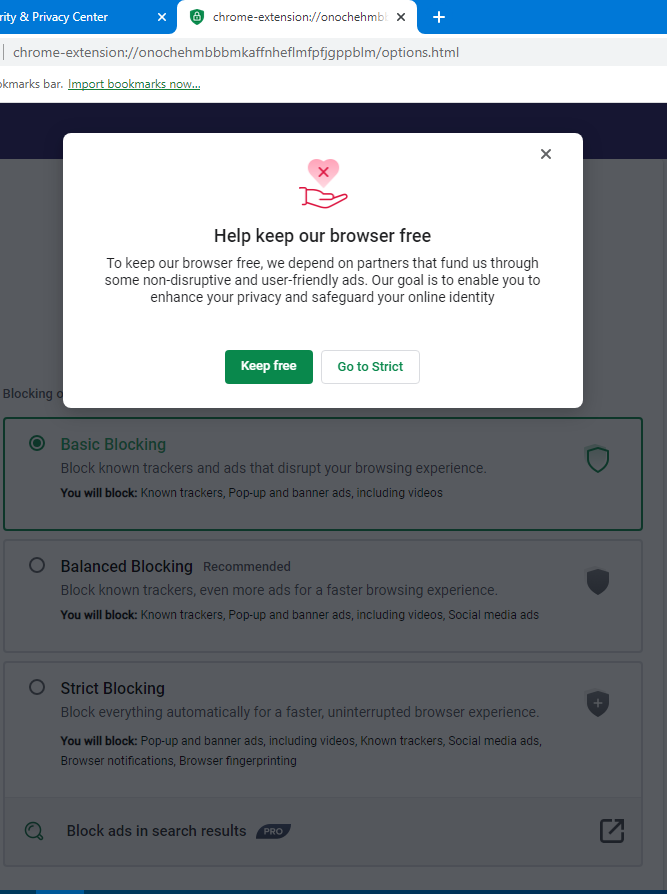
The browser basically tells you that the folks at Avast need to make a living, so it will still let some ads and partner “tracking stuff” through. In other words, Avast’s browser privacy protections stop right where that privacy can be monetized. Nothing personal—just business.
Alright, suppose we can do without full-fledged protection, but let’s at least try to hide our real location using Protected VPN—the built-in proxy Avast offers. Let’s try turning it on… Uh, what’s this?
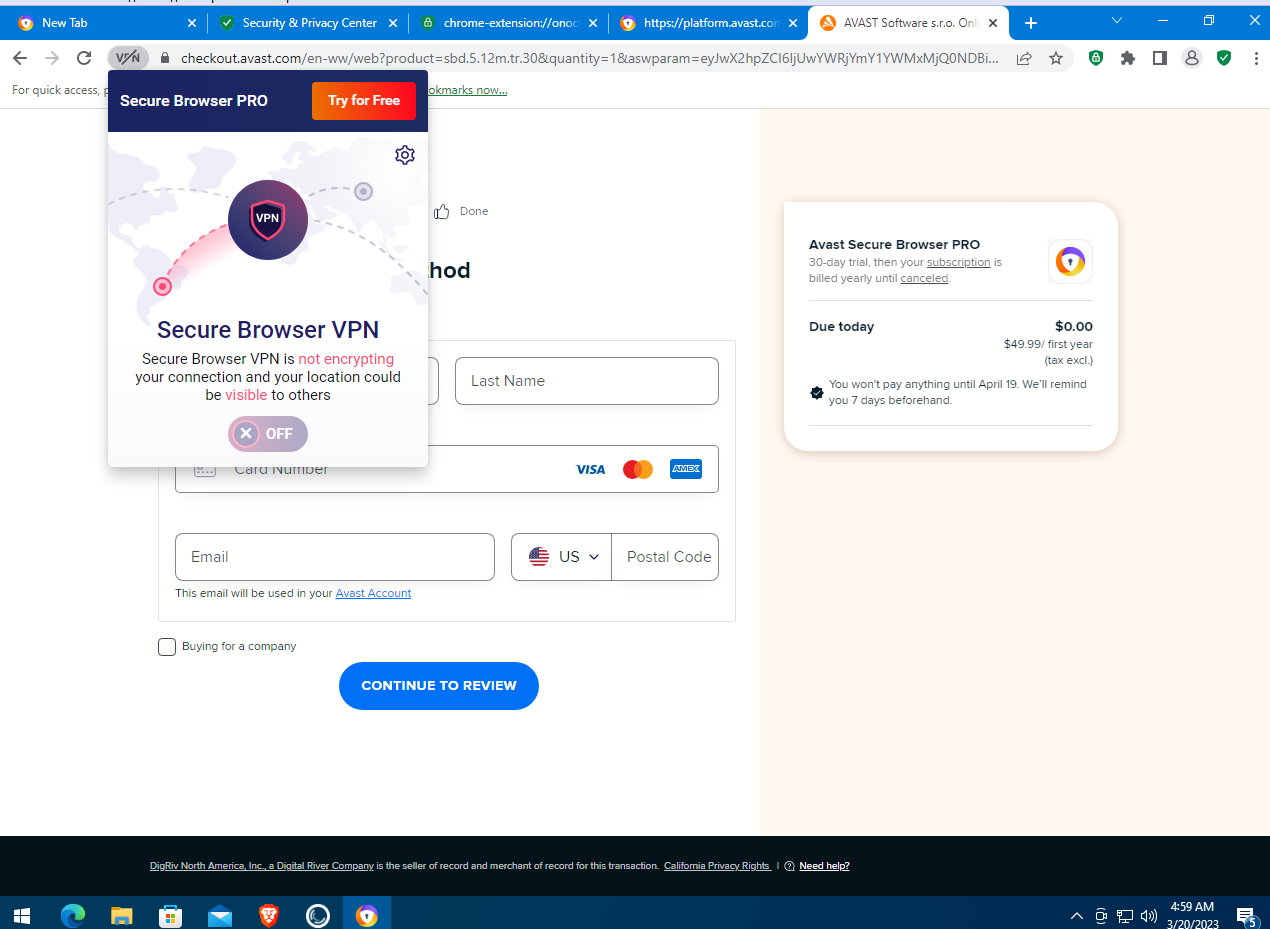
Turns out it’s a paid feature, but they’re offering a 30-day free trial. The catch is you have to enter your credit card details or use PayPal to try this supposedly unique, one-of-a-kind capability. Remind me—weren’t we talking about privacy?
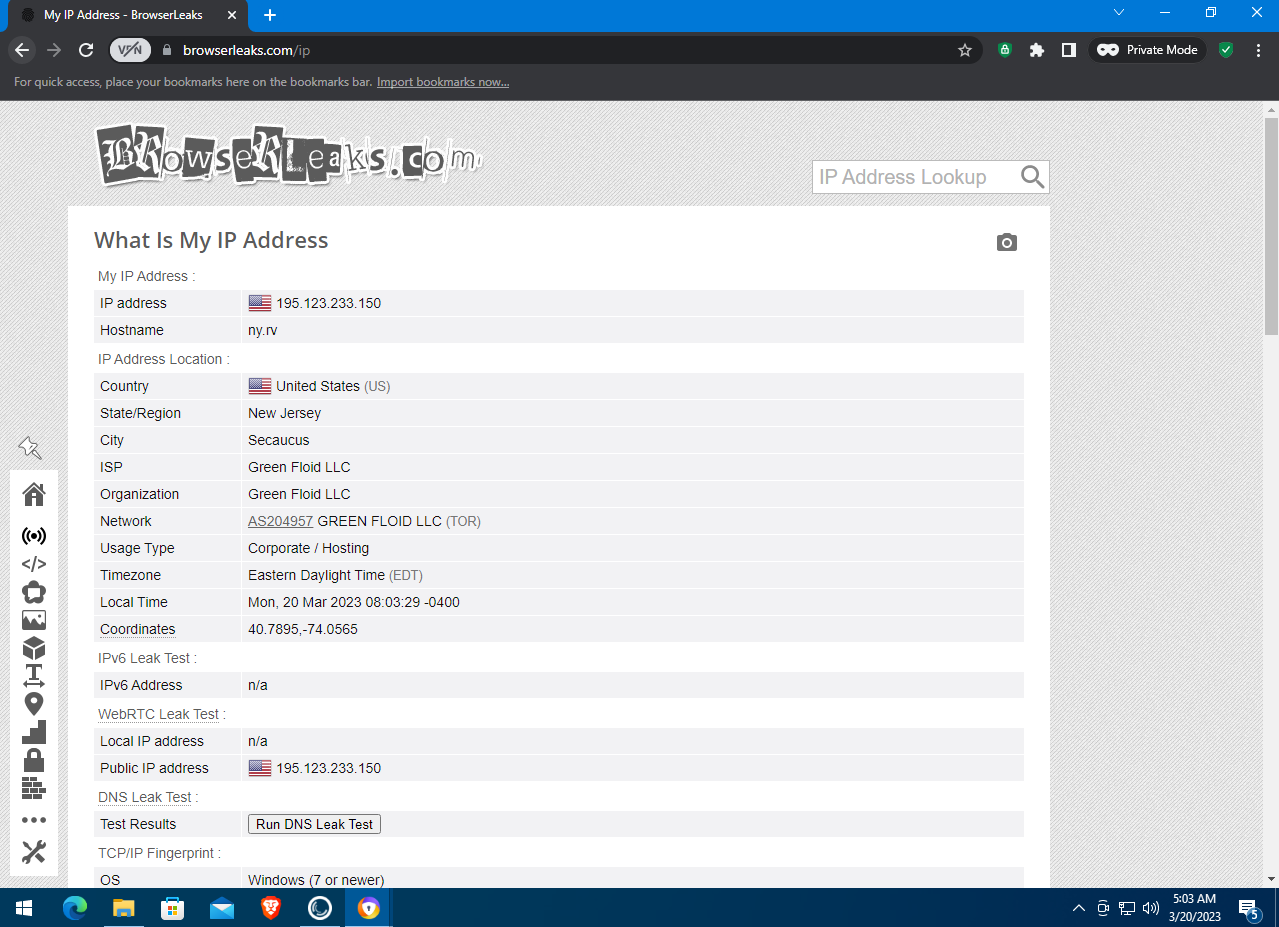
Go to the Security & Privacy Center and open a private browsing window: Private Mode — Launch Window. Now open the BrowserLeaks site in that private window. No surprises overall: the browser exposes the same amount of data as any other browser with JavaScript enabled. The IP address is detected; you can block geolocation sharing in the pop-up prompt.
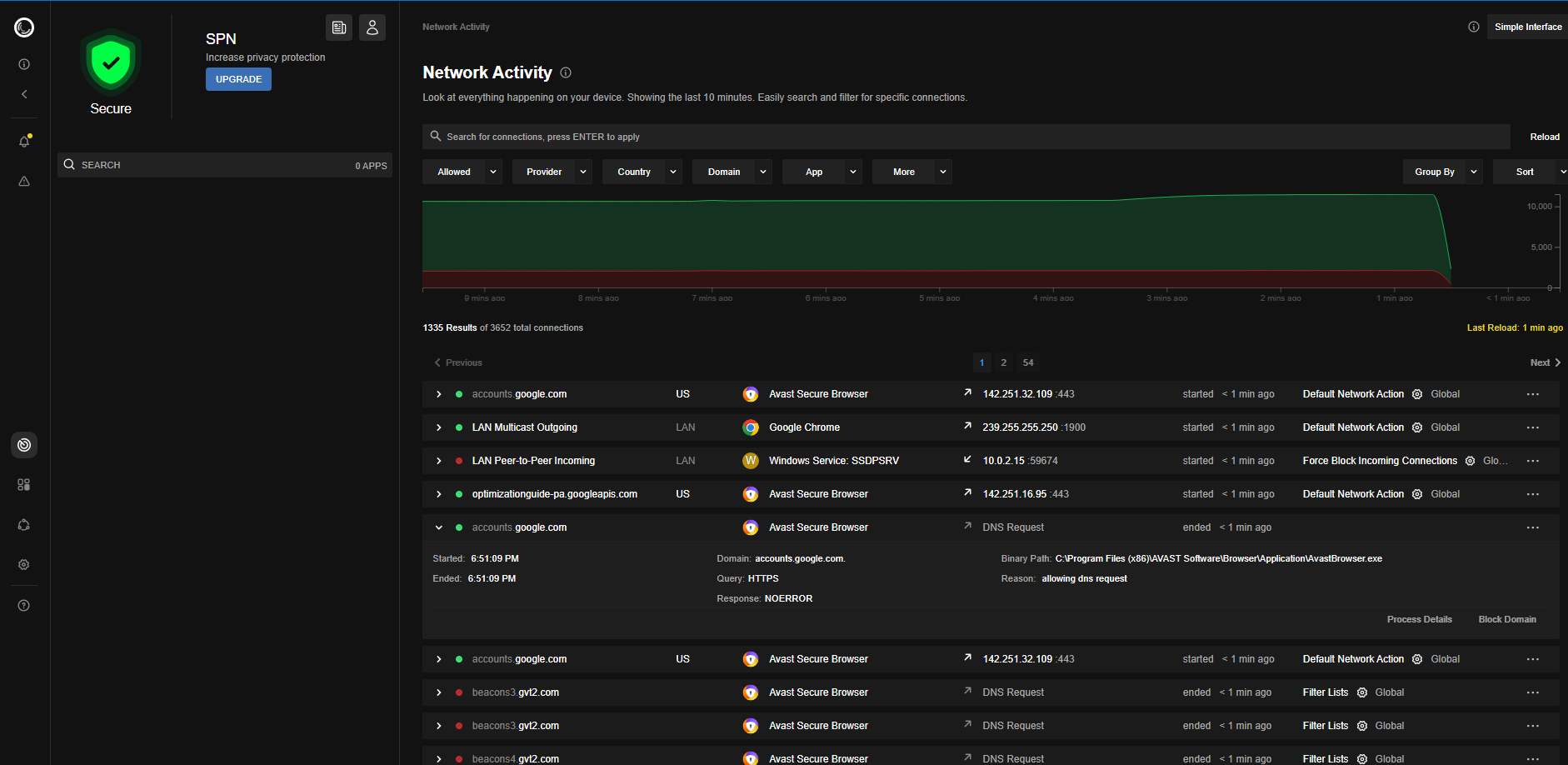
If we inspect Avast Secure Browser’s traffic in the Portmaster app, we’ll see numerous connections to Avast servers. It appears the browser is collecting telemetry.
Overall, Avast Secure Browser offers the same features you get in other free privacy-focused browsers—but it puts some of them behind a paywall.
Comodo Dragon
- Website: http://www.comodo.com/home/browsers-toolbars/browser.php
- Engine: Chromium / Firefox
- Source code: Proprietary
- Initial release: 2010
- Platforms: Windows
Another browser from the antivirus vendor Comodo Group. It comes in four editions: Comodo Dragon (Chromium-based) and Comodo IceDragon (Firefox-based), each available in 32- and 64-bit builds. I opted to install the 64-bit Comodo Dragon (Chromium-based).
Comodo Dragon uses Comodo’s own DNS servers instead of your ISP’s, which can improve security and privacy. During installation, you can choose whether to use your ISP’s DNS or Comodo’s DNS, and how to apply it—either system-wide for all connections at all times, or only when this browser is running.
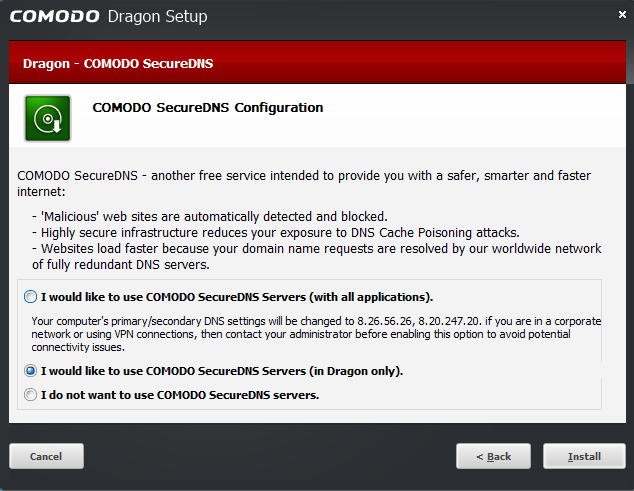
When you browse HTTPS websites, Comodo Dragon performs additional checks on SSL certificates using its own service and alerts you if a certificate isn’t sufficiently trustworthy.
Comodo includes its own built-in antivirus engine that scans websites for malicious code. While Comodo Dragon doesn’t send any data to Google services, it does track user behavior and transmits that information to Comodo Group’s own services, as disclosed in the EULA. The EULA also states that a user’s IP address is treated as confidential only within California; as a result, the browser generates log files that track users identified via cookies globally, or via IP addresses outside California. The agreement further permits Comodo Group to share the collected data with its affiliates and business partners.
If you visit the BrowserLeaks site in a browser, you’ll see that Comodo Dragon blocks precise geolocation by default.
Portmaster logs that the browser regularly connects to its own server comodo., apparently to transmit telemetry and other user-behavior data. That said, a substantial share of connections to known advertising services and tracking systems is indeed blocked. Although the browser is based on the open-source Chromium project, Comodo Dragon’s own source code is closed.
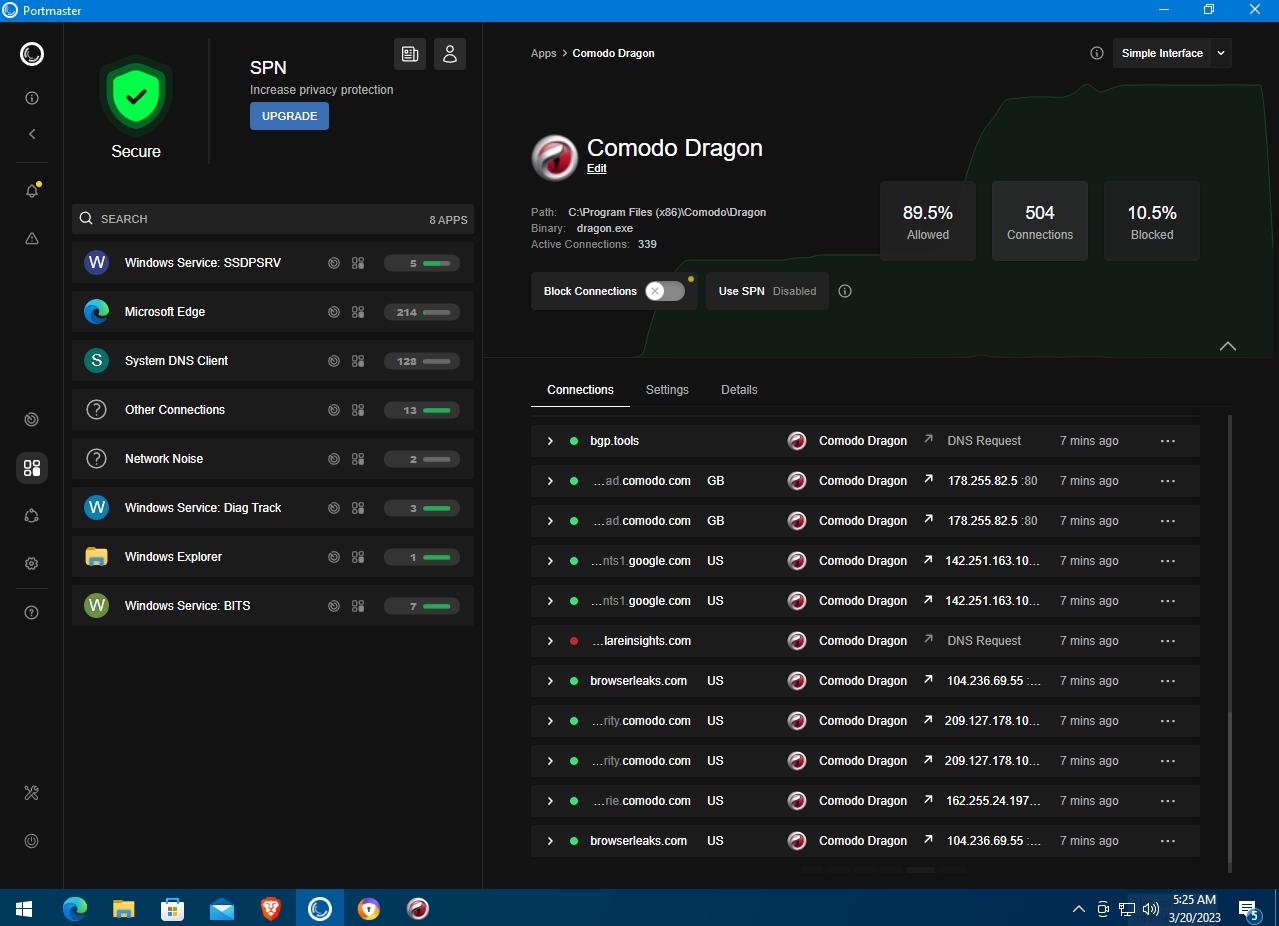
Comodo Dragon blocks ads and tracking and includes built-in antivirus features, but because it’s a closed‑source product from a commercial company, no one really knows what’s under the hood.
Waterfox
- Website: https://waterfox.net
- Engine: Gecko (Firefox-based)
- Source code: Open source
- Initial release: 2011
- Platforms: Windows, macOS, Linux
Unlike the other browsers we’ve covered, Waterfox is built on Firefox rather than Chromium, so it may appeal to those who are accustomed to that browser.
In the Windows version, this browser is 64-bit. The installer offers Standard and Custom setup modes; in Custom you can choose the installation folder and where to place the browser shortcuts… and that’s about it. Not many settings!
Visually, this browser looks a lot like Firefox; there are no major differences in the interface. The settings window is essentially identical, except it has a Look and Feel tab instead of More from Mozilla. The tab we care about most—Privacy & Security—is also the same as in stock Firefox, with all options in their usual places. There are no additional or special privacy features here.
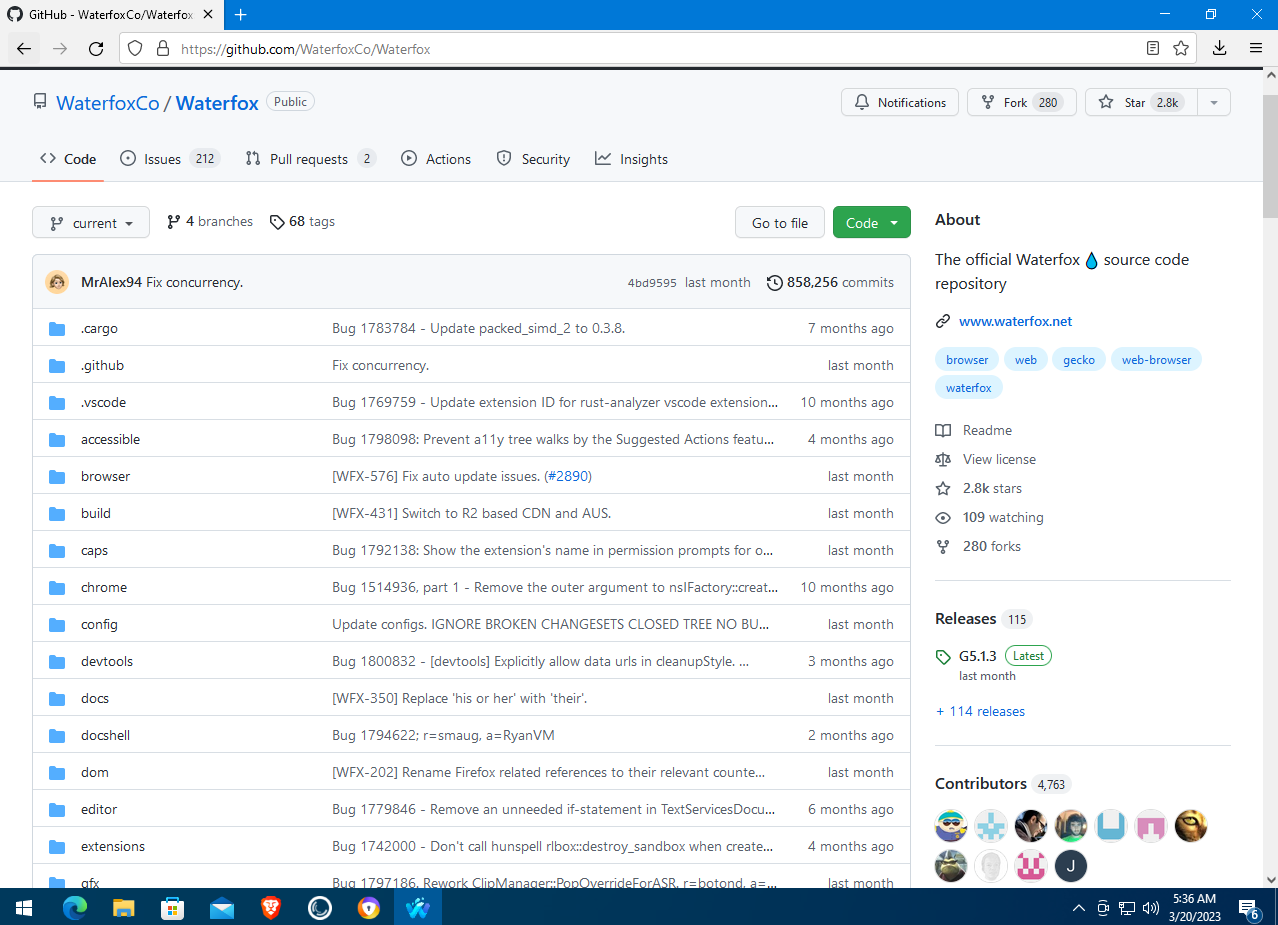
Waterfox’s source code is available on GitHub. The project now has over 4,700 contributors, which is quite a lot. Back in 2011, it was maintained by just one person—Alex Kontos—who was 16 at the time. In 2019, the advertising company System1 acquired the rights to Waterfox.
On the BrowserLeaks site, Waterfox shows essentially the same results as regular Firefox. Notably, it identifies the browser as Firefox version 102.0, while the current native Firefox release is 111.0. This suggests the Firefox codebase underpinning Waterfox is somewhat outdated, though not by much.
The developers claim that Waterfox blocks tracking and prevents ads on the sites you visit. However, if you inspect the browser’s connections in Portmaster while opening the same pages as in other browsers, you’ll see numerous requests to Google analytics domains (like gstatic.com and googletagmanager.com) and other data collection services. By default, Waterfox doesn’t block these.
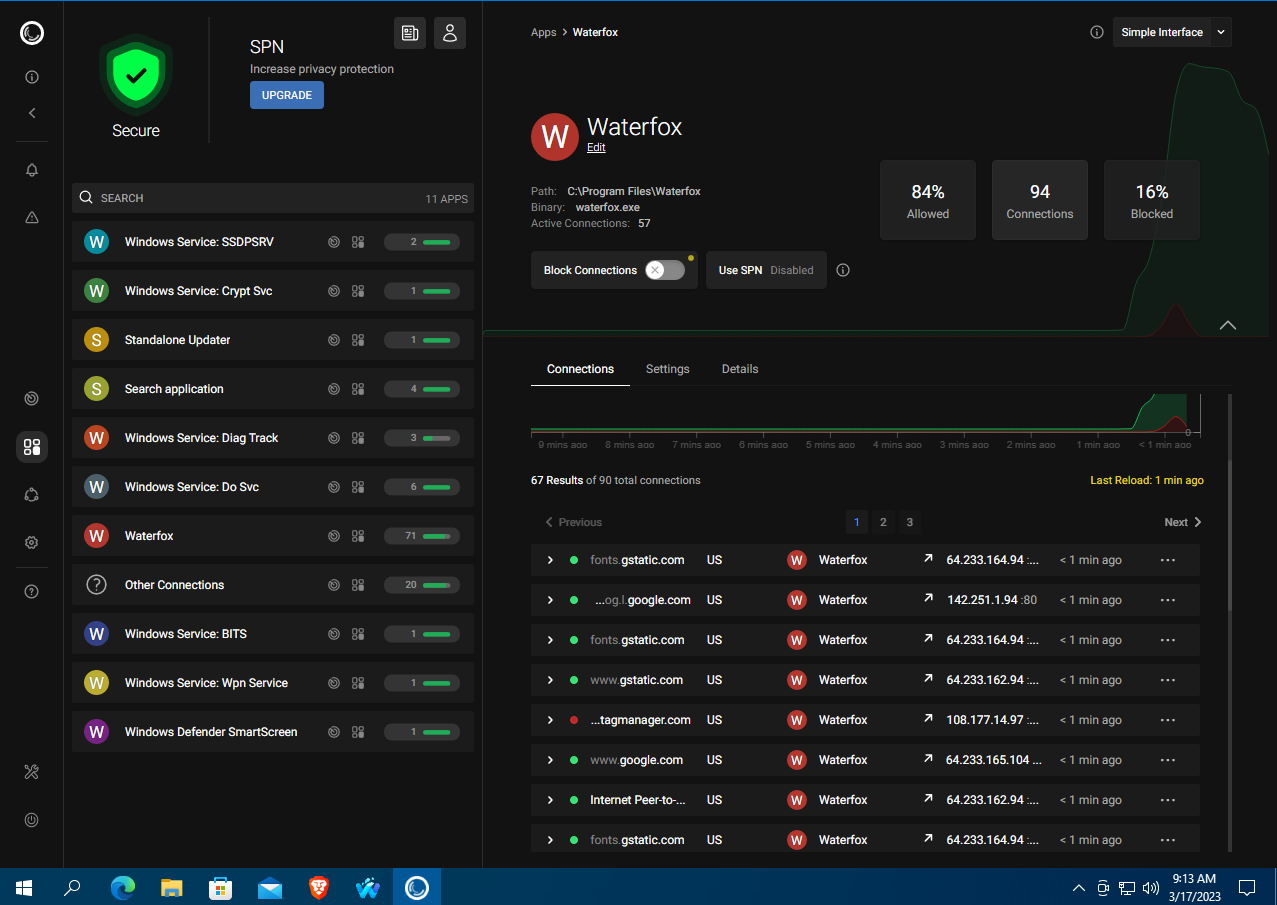
Still, an ad blocker in a browser owned by an advertising company sounds a bit odd, doesn’t it? Since Waterfox is based on Firefox, it supports the full Mozilla extension ecosystem, including privacy tools, ad blockers, and proxy extensions. But you can do all the same with regular Firefox.
Iron
- Website: https://www.srware.net/iron/
- Engine: Chromium
- Source code: closed-source
- Initial release: 2008
- Platforms: Windows, macOS, Linux, Android
Iron is a browser developed by the German company SRWare based on the Chromium source code. Both 32-bit and 64-bit versions are available for Windows, and the interface is localized into many languages, including Russian.
The Iron project launched in 2008 as an attempt to build a Chrome‑like browser that, unlike the original, doesn’t share telemetry or other data with Google. The current version also includes a built‑in ad blocker. Another key difference from Chrome is the absence of Google Updater. On the plus side, that saves bandwidth and system resources because there isn’t another background process running. On the minus side, Iron doesn’t support automatic updates—you have to download updates from the website and install them manually.
Iron uses its own Secure DNS Resolver service to filter ads and unsafe content.
The browser is surprisingly fast—pages feel like they load even quicker than in regular Chrome. That said, with default settings it exposes the user’s IP address and location. There’s an “Anonymous VPN” link in the toolbar that leads to the SRWare site, but the service is offered only as a paid option.
After installing the browser, you’ll see an Iron Config and Backup icon on your desktop—the browser’s configuration tool. To use it, first close all open Iron windows.
The Enable extended Privacy checkbox on the Configuration tab blocks certain outbound requests to websites, such as content update checks. On the one hand, this reduces the risk of exposing sensitive information. On the other, some sites may not work properly when this option is enabled.
The Backup and Restore tabs let you save and restore the browser’s settings when needed. The UserAgent tab lets you change the user agent string the browser uses to identify itself to websites. You can select a different user agent (for example, Safari) or several different ones, and with a button click generate a shortcut that launches the browser with that user agent.
Using the Import from Chrome tab, you can bring over all your data—form entries, browsing history, and passwords—into Iron from Chrome, if you’ve used Chrome before.
In Portmaster, the Iron browser shows up as Chrome. You can see that some sites send requests to Google’s analytics/statistics servers, but Iron blocks them.
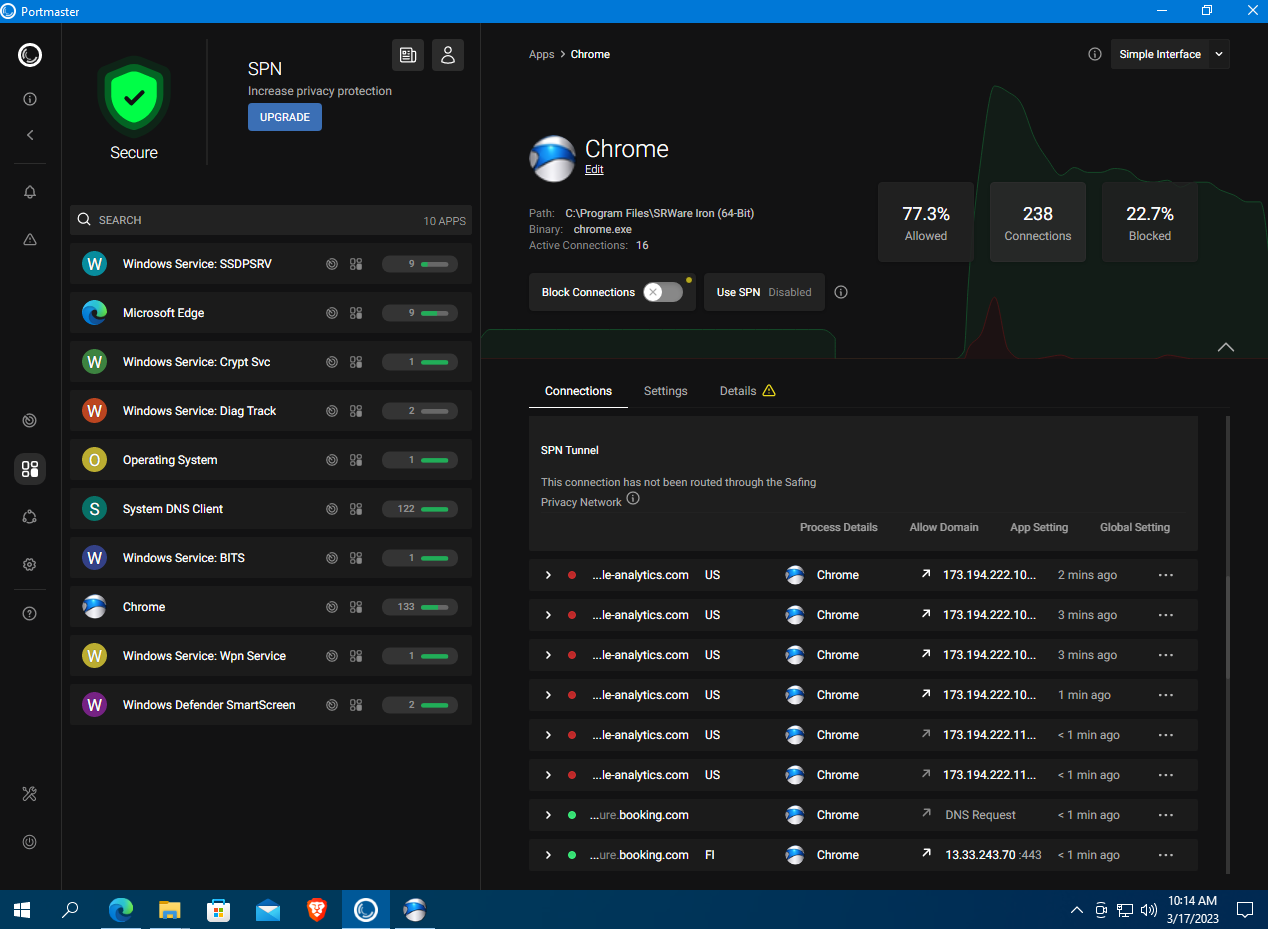
Overall, the browser leaves a good impression: it’s fast and uses Secure DNS for ad and tracker blocking. On the downside, it’s closed-source and lacks a built-in VPN. That said, since it’s based on Chromium, you can install free extensions from the Chrome Web Store, including ones that enable proxy connections.
LibreWolf
- Website: https://librewolf.net
- Based on: Firefox
- Source code: open-source
- Initial release: 2021
- Platforms: Windows, macOS, Linux
LibreWolf is a privacy- and security-focused fork of Firefox built by independent developers. It’s relatively new but has been gaining traction lately. The browser is open source; you can find the code on the project’s website.
You can download a 64‑bit Windows build of the browser as a standard installer or, alternatively, as a portable app in a ZIP archive.
If you’re already a Firefox user, the interface will feel familiar. One thing you’ll notice right away is that LibreWolf uses DuckDuckGo as the default search engine, though you can switch to other privacy‑focused options in the settings, such as Searx or Qwant. Overall, the browser’s settings mirror Firefox’s; I didn’t find any unique options in the configuration window.
According to the developers’ site, this browser is designed to protect against tracking and fingerprinting and includes a range of additional security tools. The project states that LibreWolf does not collect telemetry, and it comes with the free uBlock Origin extension preinstalled for ad blocking and content filtering, which you can also use with standard Firefox.
LibreWolf disables the built-in password manager for security reasons, but you can use third-party Firefox extensions instead. The browser also ships with Enhanced Tracking Protection enabled, which blocks certain third-party scripts that aren’t already caught by the uBlock Origin extension.
Because LibreWolf uses hardened security settings, persistent logins on some sites may occasionally get reset. To stay signed in to a site—for example, VKontakte—add it to the exceptions (allowlist) in the browser settings.
BrowserLeaks shows that this browser is more secure than stock Firefox—for example, WebGL support is disabled.
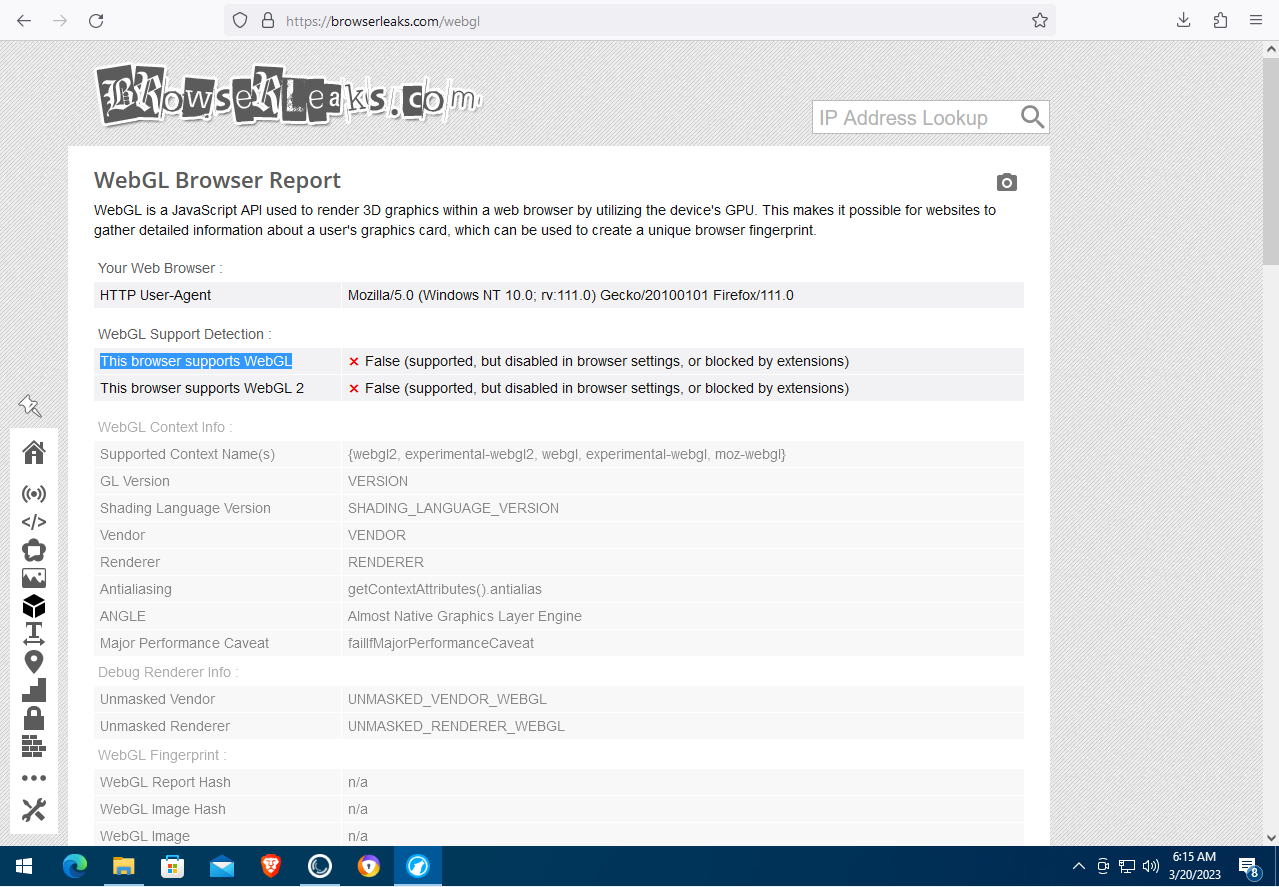
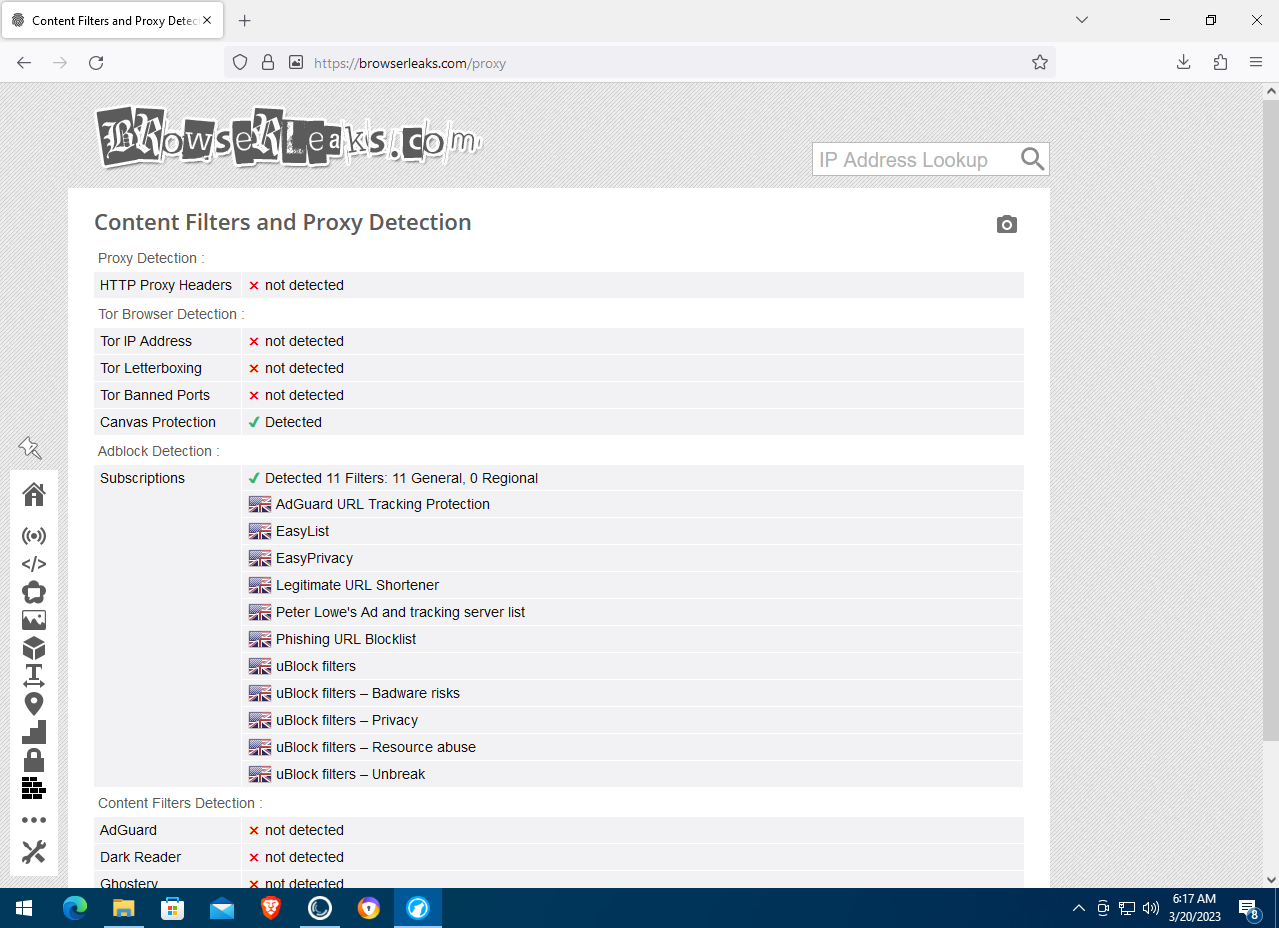
Precise geolocation is disabled, 11 content filters are active to block trackers and ads, and Canvas Protection is enabled—an anti-fingerprinting feature that analyzes how graphics are rendered in the browser.
In Portmaster, the LibreWolf browser doesn’t show any suspicious connections. There are outbound connections, but they’re made by the uBlock Origin extension to fetch filter lists and to verify site certificates.
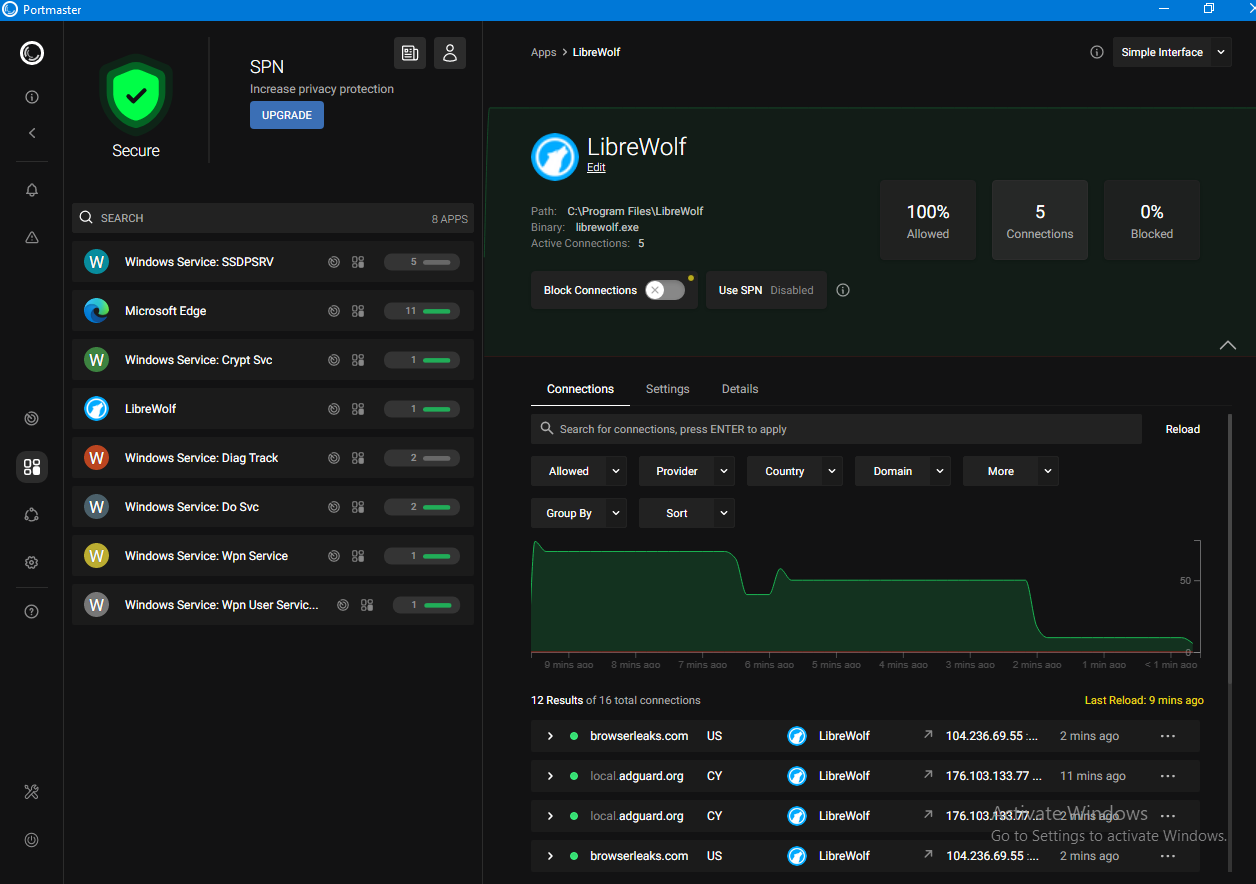
The developers’ FAQ also notes that LibreWolf initiates certain network requests to check whether the user is receiving push notifications from sites they’re subscribed to.
Overall, the browser made a good impression. It has the familiar, user-friendly interface Firefox fans are used to and performs quite fast.
Final Verdict
Time for some subjective conclusions. In our view, Brave deserves the top spot among privacy-focused browsers. It’s open-source, user-friendly, secure, and even comes with built-in Tor support.
We’d rank LibreWolf second. It’s also an open-source browser, its capabilities can be extended with extensions, and it may appeal more to those accustomed to Firefox.
The bronze medal goes to the Epic and Iron browsers. They’re commercial closed-source products, but they’re fairly fast and offer a wide range of settings. Epic also includes a content downloader, but it doesn’t work on YouTube.
The other privacy-focused browsers discussed in this article—including those from antivirus vendors—we’d rank at the bottom of the list. That doesn’t mean they’re bad; they either lack useful features found in other products, or those features are paywalled, whereas alternative browsers offer them for free.
