How it works
To intercept traffic, analyzers can use packet redirection or enable promiscuous mode—a network adapter setting that disables address filtering so the NIC accepts every frame regardless of its destination. Under normal conditions, an Ethernet interface filters at the data link layer: the NIC only accepts broadcast traffic and frames whose destination MAC address matches its own. In promiscuous mode, that filtering is disabled, so other frames aren’t dropped, allowing a sniffer to capture the data.
In theory, you can capture every packet on the local network segment where the sniffer is running, but that leaves you with far too much data to analyze and log files that quickly balloon to ridiculous sizes. A better approach is to configure the tool to capture only specific protocols (HTTP, POP3, IMAP, FTP, Telnet) or to inspect just the first 100 bytes of each packet—where the most interesting bits usually are, such as the target host address, usernames, and passwords. Modern sniffers can even monitor encrypted traffic.
Traffic analyzers are often used for legitimate purposes—network diagnostics, troubleshooting, malware detection, or monitoring what users are doing and which sites they visit. But when it comes to assessing network perimeter security or conducting penetration tests, a sniffer is an indispensable tool for reconnaissance and data collection. Sniffers exist for various operating systems; you can even deploy such software on a router to inspect all traffic passing through it. Today, we’ll look at the most popular and widely used traffic analyzers for Microsoft Windows.
Wireshark
- Developer: Wireshark Foundation
- Website: https://www.wireshark.org
- License: Free
Anyone who’s ever dealt with network traffic analysis has probably heard of this tool. Wireshark’s popularity is well deserved: first, it’s free; second, it has all the features you need to capture and analyze data in transit for most day-to-day tasks. It’s a staple for malware analysts, reverse engineers, system administrators, and, of course, penetration testers.
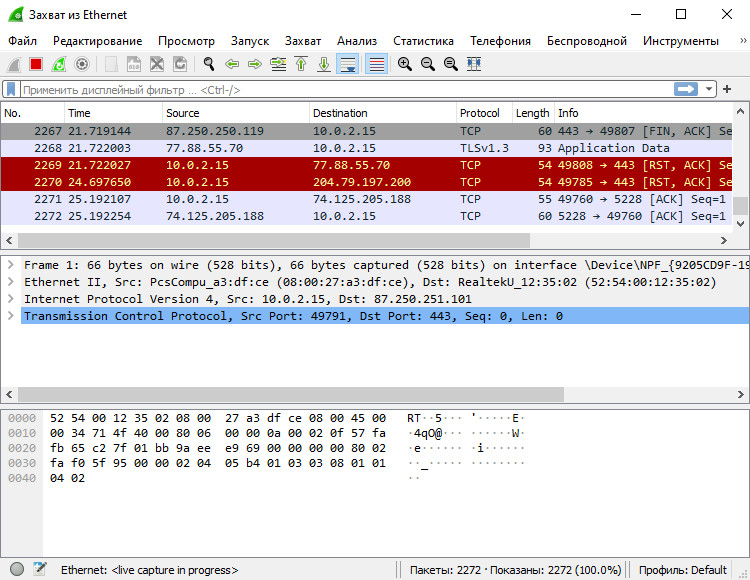
The analyzer offers a Russian UI and supports a wide range of network protocols (listing them all here would be pointless; you can find the full list on the official website). In Wireshark, you can drill down into every captured packet and inspect its headers and payload. The app provides convenient navigation across packets, with flexible search and filtering, and a powerful statistics engine. Saved data can be exported in multiple formats; you can also automate Wireshark with Lua scripts and add extra modules for traffic parsing and analysis—including ones you develop yourself.
Beyond Ethernet, the sniffer can capture wireless traffic (802.11/Wi‑Fi and Bluetooth). The tool lets you analyze VoIP traffic and reassemble TCP streams, and it supports analysis of tunneled traffic. Wireshark is excellent at protocol dissection, but to make sense of the results you’ll need a solid understanding of the protocols themselves.
One drawback of Wireshark is that reassembled streams aren’t treated as a single contiguous buffer, which makes further processing difficult. When analyzing tunneled traffic, multiple dissectors are invoked, and in the UI each subsequent one overwrites the previous one’s output—making traffic analysis in multi-layer tunnels effectively impossible.
Overall, Wireshark isn’t just popular—it’s a solid tool that lets you inspect the contents of packets on the wire, measure transfer speeds, and pinpoint bottlenecks in your network infrastructure. However, unlike commercial solutions, it lacks convenient visualization tools. And while it’s possible, extracting credentials like logins and passwords from traffic in Wireshark isn’t exactly straightforward—yet that’s a common task in penetration testing.
CommView
- Vendor: TamoSoft
- Website: https://www.tamos.ru/products/commview/
- License: Commercial; license purchase or subscription
Among today’s packet sniffers, CommView is one of the oldest and most respected veterans; the magazine Hacker wrote about it back in 2001. The project is still alive and actively maintained: the latest version to date is from 2020. Although it’s a commercial product, the vendor offers to download trial version, which lets you see it in action—the trial captures traffic for five minutes and then asks you to pay.
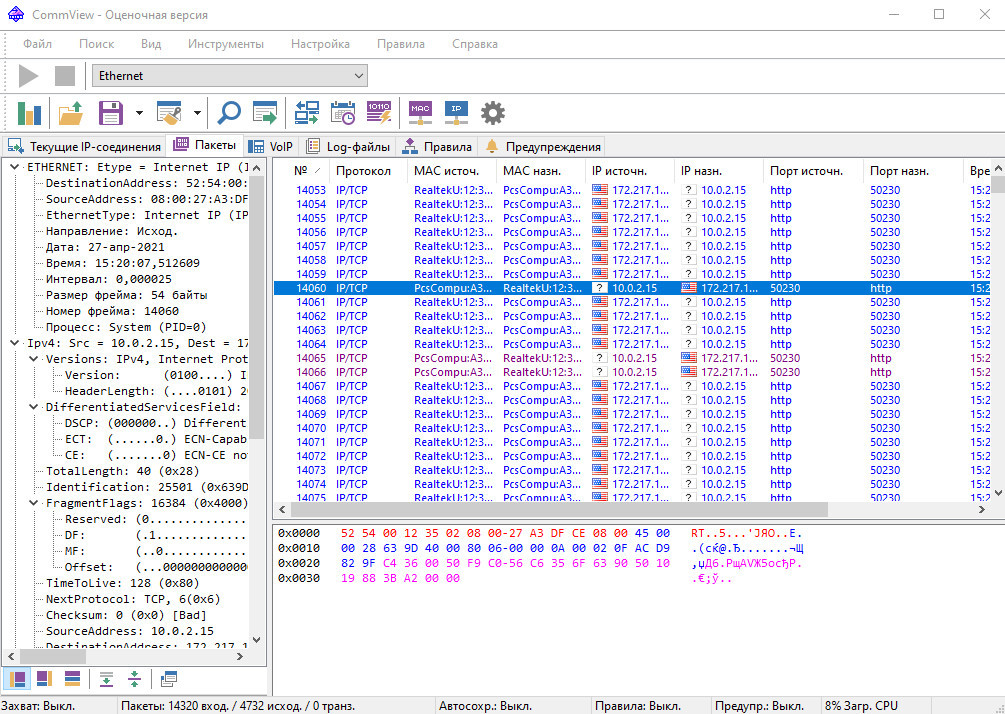
The program offers a Russian-language interface, which can be a deciding factor for users who don’t speak English. CommView’s key strength is its flexible, customizable packet filtering: you can select specific protocols for the app to monitor and sort packets by various attributes, such as size or header fields. It supports a wide range of protocols, handles the most common application-layer protocols, and can reassemble TCP sessions and UDP streams. CommView also lets you analyze traffic down to low-level protocols such as TCP, UDP, and ICMP, and view raw data. The program displays headers of captured packets and collects detailed IP traffic statistics. Saved data can be exported in 12 different formats, from .txt and .csv to formats compatible with other analyzers like Wireshark.
In addition to NIC traffic, CommView can monitor VPN connections and traffic passing through modems—analog, cellular, ADSL, ISDN, and others—by installing a dedicated driver. It can also capture VoIP traffic and SIP telephony sessions. The application includes a packet generator that lets you send packets of a specified length, with custom headers and payload, to a selected Ethernet interface. There’s also a convenient log viewer that opens log files in a separate sniffer window and allows searching within their contents.
The tool is undoubtedly very handy and useful—if it weren’t for the steep licensing costs. For a professional pentester, buying it is likely justified, but if you just want to take a quick look at a network, you can look for alternatives—cheaper or even free options.
Intercepter-NG
- Vendor: Unknown
- Website: http://sniff.su
- License: Free
This is another venerable tool — the magazine “Hacker” wrote about it back in 2012. Since then, this homegrown project hasn’t disappeared from the internet like many of its competitors; it has continued to evolve and improve — the latest release of the sniffer dates to 2020. There’s an Android build available as an APK, and even a Unix console (CLI) version.
Intercepter-NG relies on the NPcap utility and, according to the developers, carries a portable version with it. In practice, however, it was either left out or doesn’t work on Windows 10 — to get the sniffer running, I had to download NPcap from https://nmap.org/npcap/ and install it manually.
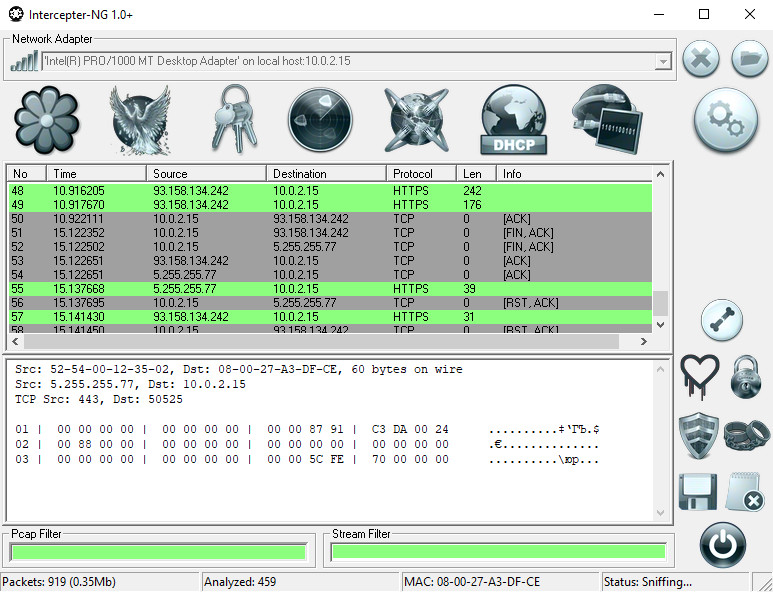
Intercepter-NG has a pretty slick user interface and lets you inspect traffic in several modes. There’s a standard packet view with payloads, where you can filter using pcap rules or use Follow TCP Stream for a deep dive into a specific session. There’s also a Messengers Mode, where the tool tries to intercept messenger traffic—mainly the old-school ICQ, MSN, Yahoo, and AIM—but it also supports the Jabber protocol. With Telegram, though, no luck: the sniffer simply didn’t see it.
There’s a Passwords mode that displays credentials (usernames and passwords) captured from network traffic over protocols like FTP, HTTP, SMTP, POP3, IMAP, LDAP, Telnet, and others. The Resurrection mode can reconstruct files transferred via HTTP, FTP, SMB, IMAP, POP3, and SMTP; however, only files from completed TCP sessions can be recovered successfully.
Intercepter-NG also includes a set of additional, very handy tools. There’s a simple DHCP server and a NAT service that can relay ICMP, UDP, and TCP traffic between different Ethernet segments. It offers several network scanners (ARP, DHCP) and an intelligent gateway discovery feature. Another useful component is a module for running Man-in-the-Middle (MitM) attacks. It supports spoofing (covering DNS/NBNS/LLMNR), ICMP Redirect, DNS over ICMP Redirect, SSL MitM, SSLStrip, and more.
The tool can scan a specified port range to find applications listening on those ports and analyze the protocols associated with them. You can switch the sniffer into an aggressive mode where it captures all TCP packets without any port filtering, which helps reveal services running on nonstandard or administrator-reassigned ports. The downside is that in this mode the application slows to a crawl and may periodically hang.
The current version of Intercepter-NG includes a built-in tool for exploiting Heartbleed—a flaw in the OpenSSL cryptographic library that allows unauthorized reading of memory on servers or clients, including extraction of a server’s private key. The package also adds a brute-force utility and the multi-threaded vulnerability scanner X-Scan. In other words, Intercepter-NG is evolving from a simple network analysis app into an all-in-one toolkit that lets you, without switching tools, scan a network for open ports and unpatched vulnerabilities, capture credentials, and brute-force targets.
Among Intercepter-NG’s drawbacks is that Kaspersky and Windows Defender flag it as malicious, causing it to be blocked even while downloading from the vendor’s site. So to work with the sniffer you’ll need to disable your antivirus, but that’s a small price to pay for access to such a feature-rich tool.
SmartSniff
- Developer: NirSoft
- Website: http://www.nirsoft.net/utils/smsniff.html
- License: Free
A lightweight sniffer that works with TCP, UDP, and ICMP. Requires installing the WinPcap driver and the Microsoft Network Monitor Driver version 3.
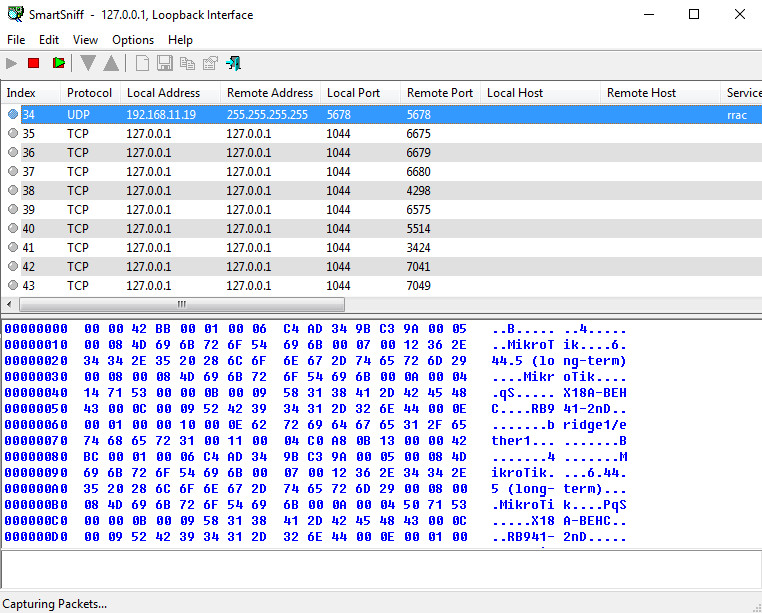
The project was originally built for Windows 2000/XP (which shows in its UI), but it’s still around—the last release of the sniffer dates back to 2018. The utility captures traffic passing through the local machine and lets you inspect packet contents—that’s basically all it does.
tcpdump
- Vendor: Tcpdump Group
- Website: http://tcpdump.org
- License: Free (modified BSD license)
A C-based console utility, originally developed for Unix and later ported to Windows, which uses WinPcap. It requires administrative privileges to function properly. Among Windows users, the open-source version of tcpdump called WinDump is more popular and can be downloaded for free from https://www.winpcap.org/windump/.
Burp Suite
- Vendor: PortSwigger
- Website: https://portswigger.net/burp
- License: Free (Community Edition)
Another popular tool among pentesters for web application security testing. Burp ships with Kali Linux, and there’s also a 64-bit Windows version. It’s often called the pentester’s Swiss Army knife—when it comes to finding vulnerabilities and auditing web app security, it’s hard to beat. Burp Suite includes features for sending modified requests to remote hosts, brute forcing, fuzzing, discovering files on the server, and much more.
As a sniffer, Burp isn’t a general-purpose tool—it only monitors traffic between the browser and a remote web application via an intercepting proxy. To handle HTTPS, you need to install Burp’s CA certificate on the system. Still, for certain tasks, that can be sufficient.
Burp Suite intercepts all the requests and responses your browser sends and receives, letting you analyze the traffic of various web applications, including online messengers and social networks. If the target environment a pentester is examining exposes HTTP or HTTPS services, there’s hardly a better tool for testing them. But using Burp purely as an HTTP/HTTPS sniffer is like hauling potatoes in a Lamborghini—it’s built for far more than that.
Conclusion
To paraphrase a popular song, sniffers come in all shapes and sizes—and each is better suited to specific tasks. For web app research and intercepting local HTTP traffic, nothing beats Burp Suite. If you need to hunt for issues in your own LAN or list the remote hosts a program talks to, Wireshark is a great fit. And for attacking network infrastructure, you can use Intercepter-NG, which comes with a full toolkit for penetration testing.
