A couple of years ago, there was an article in “Hacker” about unusual methods of storing and transferring files. Since then, a new method has been gaining popularity, referred to as “fog” or “descending cloud” (not to be confused with bitcoin fog—a transaction obfuscation method). The idea is that the functions of a cloud provider are not performed by a specific data center, but by thousands of computers in a peer-to-peer network. Each one allocates part of its idle resources, and its owner receives compensation for this. For instance, they might share some free space on their disk and bandwidth for access to it.
Certain “cloud-like” file synchronization services have gained popularity, such as BitTorrent Sync (now known as Resilio Sync) and its open-source counterpart Syncthing. However, these services are only effective for replicating data between trusted nodes. They face conceptual limitations and a lack of financial incentive for participants, which prevents them from scaling up to global P2P storage solutions.
Other developers of distributed systems have taken it upon themselves to address the issue. The main idea behind these startups is often to create a fog computing network integrated with blockchain and hashing. To achieve this, the system is placed in a P2P network that unites all interested participants. Some can obtain any conceivable amount of disk space at low cost, while others can offer a portion of their storage in exchange for compensation. Blockchain serves a dual purpose here: ensuring data integrity and simplifying transactions.
Blockchain in Data Storage
Blockchain technology is often associated with cryptocurrency, as it was initially widely used for its creation. However, it has many other applications. Essentially, blockchain is a type of distributed database where all records are stored in a chain of blocks. These records can pertain to any kind of interaction (transactions) between participants—not necessarily financial. They can also include records of files stored in a peer-to-peer network.
Regardless of the content, blockchain chains are fully or partially duplicated across all nodes of the peer-to-peer network, which provides a range of properties:
- Complete or partial decentralization. Data is literally stored everywhere, with no single location where the NSA could seize it or where it might be wiped out by a tsunami;
- High redundancy. In a P2P network, the disappearance of some nodes doesn’t matter—you can still retrieve your files from others without even noticing a problem;
- High fault tolerance. The likelihood of the entire peer-to-peer network failing at once is nearly zero. Some nodes will remain accessible, and others will synchronize with them at the earliest opportunity;
- Protection against accidental and intentional data modifications. A distributed database doesn’t have the vulnerabilities typical of a local DB. No malicious actor can damage it or overwrite existing blocks;
- Broad bandwidth. The connection speed in a P2P network increases as new and faster nodes join.
All these features are provided by public key cryptography and the specified complexity of computing hashes of a certain type.
Cryptocurrencies and Other Crypto Concepts
Blockchain helps protect data from tampering, accidental distortions, censorship, and most types of attacks that traditional (local) databases are vulnerable to. Additionally, it provides an easy way to account for machine resources and the ability to reward their provision.
Many attempts have been made to combine Bitcoin with BitTorrent. In addition to the original Bitcoin algorithm, its forks have also been tried for this purpose. For example, Primecoin was appealing because instead of performing meaningless hash calculations, it searched for specific sequences of prime numbers, the general form of which was described by Alan Cunningham.
The Primecoin algorithm was used in the data storage service Datacoin. Participants earned the Datacoin cryptocurrency as a reward for providing storage space. This is mentioned in the past tense because overall interest in the project has significantly waned. While the idea itself was decent, the poor execution is evident from the Datacoin price charts.
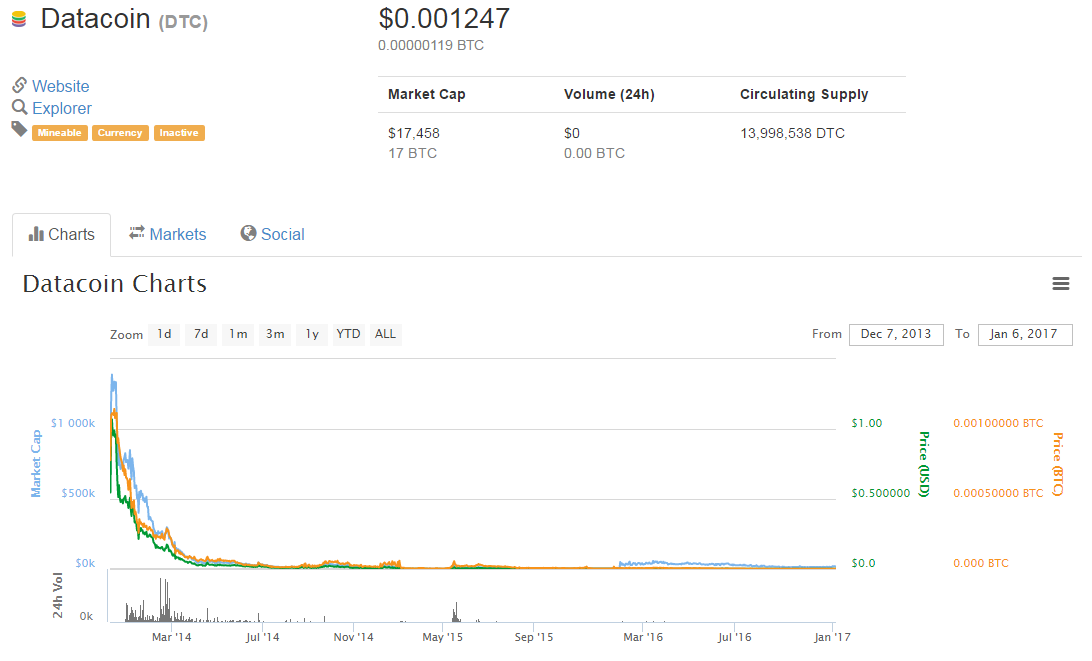
The creators of the Filecoin project also proposed paying for storage space with cryptocurrency (PDF). However, their Twitter account hasn’t been updated for a year, and the latest post on their official blog dates back to July 2014.
A different approach to data storage was utilized by a group of researchers from Microsoft Research. They considered it technically impossible to combine cryptographic security with “useful” computations and proposed their own cryptocurrency, Permacoin. Unlike Datacoin, Permacoin rewards are not given for the storage space itself but rather for downloading and long-term storage of fragments of a distributed database. Periodic checks are conducted on the uploaded content via hashes, serving as the basis for awarding cryptocurrency to specific participants in the peer-to-peer network.
Currently, Storj Labs, a young company from Atlanta, is proving most effective at reselling third-party disk space. Three years ago, its founders introduced a “new” method of distributed file storage, modestly naming it after the company. The company is still going strong, and the value of the Storjcoin X cryptocurrency is slowly rising, potentially increasing further with each new mention in the media.
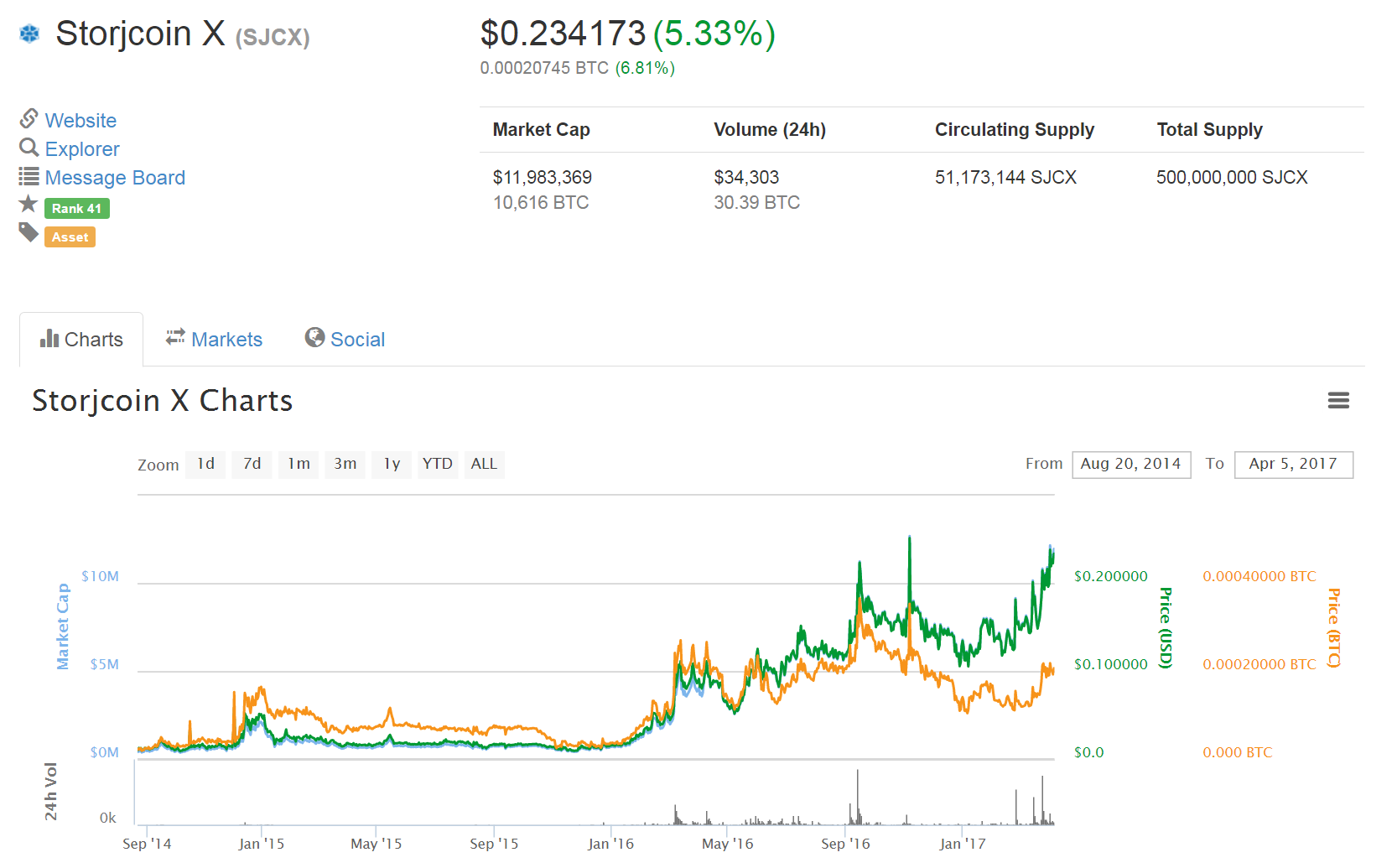
The general principle of Storj’s “revolutionary method” is similar to others: user files are divided into blocks, encrypted, linked into a blockchain, and distributed across nodes in a peer-to-peer network. The differences lie in the important details.
Firstly, no one in their right mind plans to store actual files on the blockchain. Otherwise, a couple of porn collections would have bogged down the entire peer-to-peer network right from the start. The size of the chain would grow to terabytes, and synchronization times would become infinite. Therefore, instead of the files themselves, only their metadata is sent to the blockchain. Currently, the metadata volume in Storj is less than a kilobyte per file, regardless of its size. This means that storing records for a million files on the blockchain would require no more than a gigabyte. This is more manageable, but still somewhat excessive. The Storj team is exploring methods to compress metadata more efficiently to shrink the distributed database even further. It is feasible to reduce its size by two to three times, but for now, it works well enough.
Secondly, all code in Storj is open source. No secrets—just take a look. Thirdly, Storj is well-documented. In August 2014, Storj Labs co-founder and CEO Shawn Wilkinson, along with Jim Lowry, published an article titled “Metadisk: A Blockchain-Based Decentralized File Storage Application” (PDF), where they outlined the fundamental principles of the future Storj.
The main goal of the project was to create a “fundamentally new and accessible platform for distributed file storage” that is more reliable and cost-effective than traditional cloud solutions based on large data centers. This led to the development of Metadisk—a simple application for a wide range of users, along with software interfaces that allow for the integration of P2P storage into any project. They are unified by Storj, a service that has nearly reached a usable level today. The current state of Storj is detailed in a more recent research paper by Wilkinson and his colleagues (PDF).
Other interesting aspects of Storj relate to its cryptocurrency of the same name. Initially, Storj used Datacoin, but eventually introduced its own—Storjcoin X (SJCX). Typically, in any blockchain, currency is generated through mining, which requires significant computational resources. The creation of a new block is considered proof of work (PoW), and virtual coins are awarded for this effort. The earned cryptocurrency can be transferred within the same decentralized network, traded across different networks (via exchanges), or exchanged for traditional currencies.
Storj operates on a completely different model. The entire cryptocurrency SJCX was issued before the project’s public launch in 2014. All 500 million coins were already created through pre-mining, leaving nothing left to mine now. Consequently, in the absence of other significant factors, the value of SJCX is expected to increase in proportion to the growth of the peer-to-peer network. This is a deflationary model— the exact opposite of inflationary systems we encounter daily. Inflation reduces the purchasing power of traditional currencies as the money supply increases.
The total number of SJCX tokens is strictly limited by the algorithm, and the demand for these tokens is increasing. If the concept of distributed data storage becomes successful, the value of SJCX is likely to continue rising.
The absence of mining theoretically allows for renting out storage space on any device with a processor. Currently, there are ready-made clients for Windows, Debian Linux, and macOS. However, since the source code is open, it can be ported to just about anything, including NAS and routers with firmware like OpenWRT and DD-WRT.
Migration to Ethereum
In March 2017, the owners of Storj announced their plan to move their cryptocurrency from the Bitcoin blockchain to Ethereum. Shawn Wilkinson provides a detailed list of Ethereum’s advantages over Bitcoin and promises to release a detailed migration plan soon. It is currently known that holders of SJCX will receive new coins in exchange for their old ones at a 1:1 ratio.
Today, an increasing number of distributed databases and unique services are connected to the Ethereum blockchain. The Russian Bank commissioned the FinTech Association to create a client identification system called Masterchain. Acronis has developed a universal software-defined storage (SDS) solution. Meanwhile, Microsoft offers an Ethereum Blockchain as a Service (EBaaS) model, which any developer can easily try.
You can learn more about Ethereum and the concept of smart contracts from the July 2016 issue of “Hacker.”
Connecting to Storj
Joining the Storj network and renting out your drive is simple. Visit the Rent your drive section on the project’s website, download the Storj client for your operating system, and start it up. Some antivirus programs may flag the Windows Storj client, but this appears to be a false positive due to the heuristic detection reacting to an unusually distinctive program.
When you first launch Storj Share, you’ll need to enter a wallet number to receive Storjcoin X. This number is formatted like a Bitcoin address, so you can either use an existing one or create a new one, for instance, on Counterparty. The authentication process there is quite tedious. The server generates a password phrase consisting of twelve random words, which you then need to enter one by one using an onscreen keyboard. It’s believed that this enhances security, but it’s also quite a hassle, and modern keyloggers can still bypass these methods.
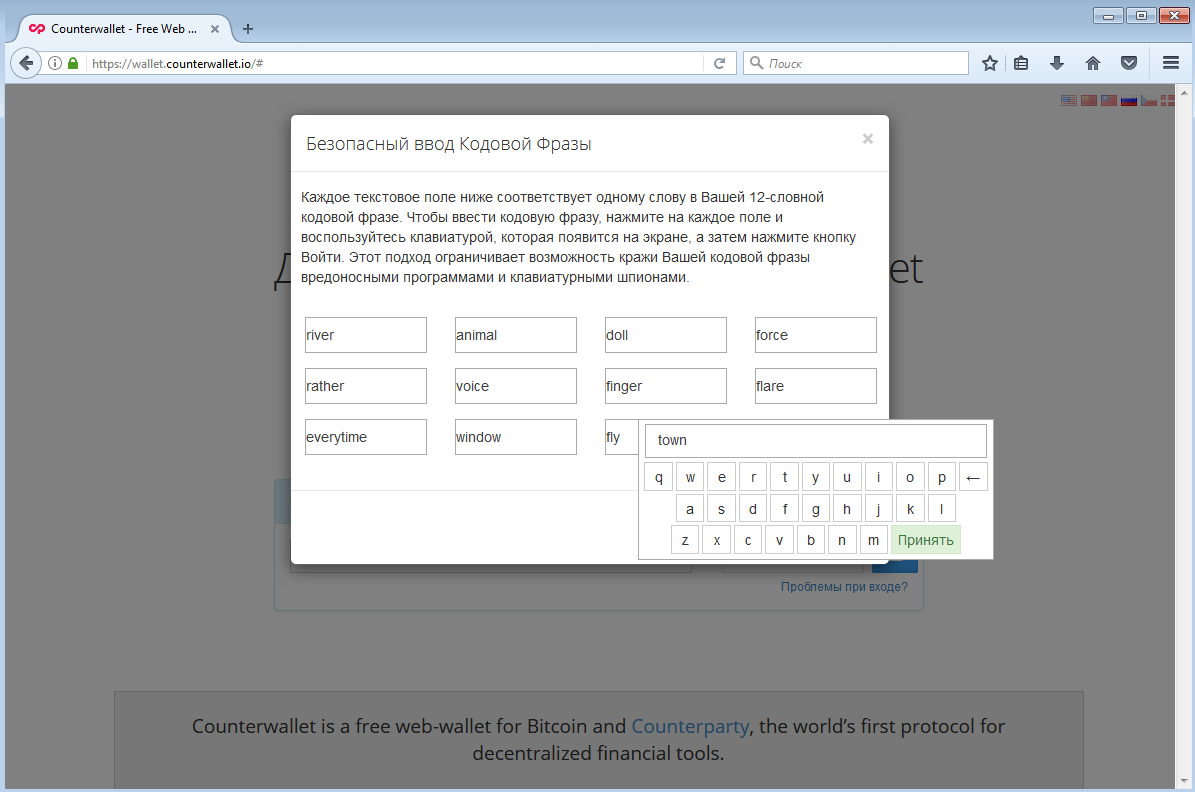
After entering the address, you just need to complete a few simple configurations and click the Start button. In the basic settings, specify the amount of disk space to be rented out and the path for storing other people’s files (more precisely, encrypted blocks).
For storage purposes, it’s most practical to use regular hard drives—not just because of their cost-to-capacity advantage. The Storj Share client accesses the disk several times per second, which means that a flash drive or SSD won’t last long.
A notification appears at the bottom of the window indicating that telemetry is enabled by default. You can disable it in the advanced settings, where you can also configure startup options, program behavior, and network connectivity.
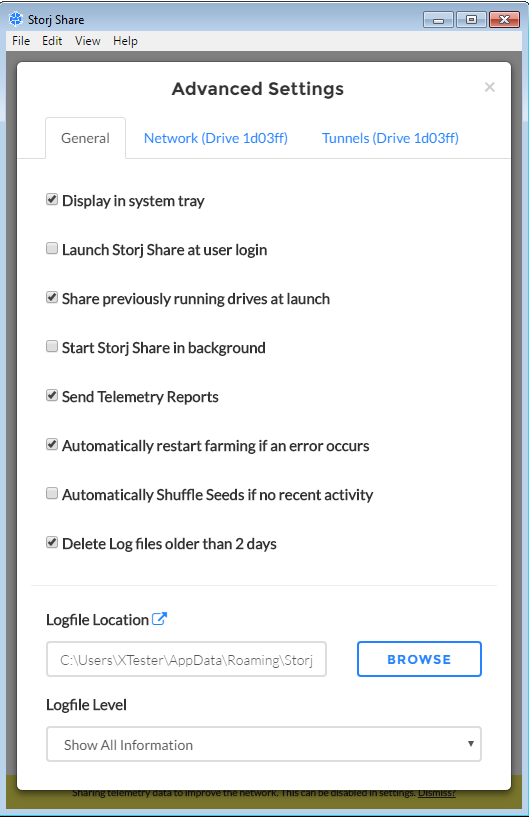
When you launch the StorjShare.exe process, it establishes dozens of connections, primarily to the storj. server and Amazon AWS cloud servers. In the Storj Share window, you will first see an increasing number of peers, followed by the allocation of storage space filling up.
You can take a look at the Storj log to see how it operates. Initially, the client sends a request to locate nodes, followed by an exchange of identifiers and keys. The network nodes are registered through storjtross.ddns.net.
From this point on, you can forget about Storj for a few days. The main thing is to ensure that the task manager shows three active Storj Share processes at the same time and that the main window displays the green message Storj .
After some time, your node will undergo numerous checks, after which it may (or may not) become part of the network. This depends on the amount of space you have allocated, how long it remains available, and the connection speed. It is also essential to configure automatic synchronization of system clocks with NTP servers. Even a second’s discrepancy is enough to disrupt timestamps in the blockchain, which could result in your node being excluded from Storj.
Earnings for the Patient
For our tests, we allocated 10 GB on one computer and 50 GB on a mini-server available around the clock. By local standards, this is nothing—real enthusiasts allocate terabytes for Storj. The total number of nodes in the Storj network is still relatively small (just over ten thousand), but it continues to grow. Besides regular users, there are “farmers” who have bought large-capacity drives hoping to make quick money. An online calculator promised them nearly a dollar a year for each gigabyte, but the issue lies in the fine print. Spoiler alert: the farmers won’t even break even on their investments.
Storj payouts are currently made once a month, so you might see a zero balance for quite a while. Many users stop sharing gigabytes after a week, assuming the app isn’t working or they’ve been scammed. It took a week of continuous operation before Storj started downloading fragments of other people’s files from the P2P network.
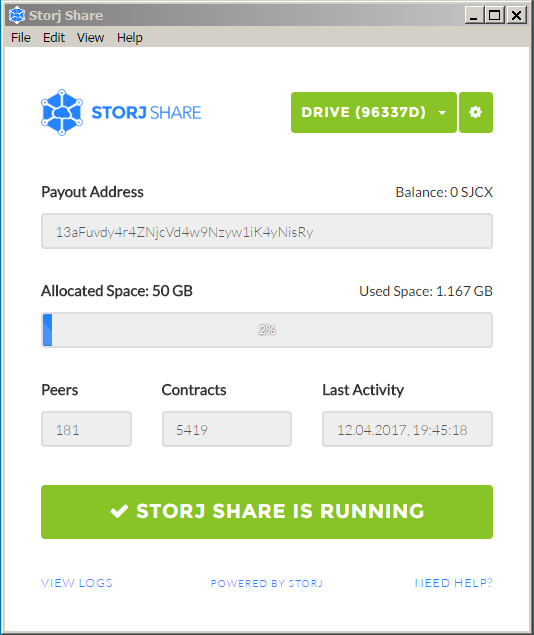
You can realistically profit from renting out storage only if you already own all the necessary hardware, have access to free electricity, and unlimited high-speed internet. This means you’re not paying for anything and only reselling resources that you already have for some reason but aren’t using. This scenario is common for botnet operators and network administrators: clusters, servers, and even regular work computers are rarely utilized to their full capacity. A home user pays for everything themselves, so Storj won’t be a source of profit for them. At best, it may provide some entertainment and partially cover the electricity bill.
The original idea behind Storj was to earn a bit of cryptocurrency using idle resources. For example, if you have a terabyte hard drive that’s only two-thirds filled with movies, it will spin just the same whether it’s full or empty. You could keep filling it with media content, or you could delete watched movies and rent out a few hundred gigabytes.
If you’re considering selling a kidney to buy a RAID array and start a large-scale disk rental business, you might want to hold off. Firstly, you might still need that kidney, and secondly, when you calculate the investments and monthly expenses, the profitability becomes questionable. I’m sure that if you’re interested, it might be cheaper to just buy SJCX on the exchange while the rate is still low.
Storj: A Developer’s Tool
The creators of Storj are confident that it will also capture the interest of developers. Its open API allows for the seamless integration of “fog storage” as an alternative to cloud storage for any project.
“Compared to cloud services, Storj Labs offers faster speeds, enhanced security, and a more cost-effective data storage solution. Any developer can use the Storj network with simple tools, without needing to be an expert in distributed networks or encryption,” stated Wilkinson.
Even the code of the official Storj Share client can be easily modified using Developer Tools.
Storj Labs received $3 million during its pre-launch funding phase, largely for its compelling concept. A portion of the funds was used for pre-mining, the bulk went towards project promotion, and only the remainder was spent on server rentals and the project development itself. Among the investors were Google Ventures and Qualcomm Ventures, for whom investing a million or two in yet another startup is a common practice. If the startup fails, it’s no big deal, but if it succeeds, they gain control over it and prevent a potential competitor from emerging.
For others, there’s a significant downside here. Developers of Storj receive actual money from venture funds and clients, but they pay their “landlords” (meaning you and me) in their own cryptocurrency, and not immediately. While it’s true that more real money is being offered for it on exchanges, the developers hold significant sway over the exchange rate.
Even though decentralization theoretically provides all the benefits of a P2P network, in practice it’s only partial. While all user nodes are equal among themselves, if the main servers fail, the entire Storj network would soon go down as well.
The appealing deflationary model also has a downside: the creators of Storj have full control over their cryptocurrency and conduct transactions with clients in dollars. Currently, they charge one and a half cents per gigabyte per month and an additional five cents per gigabyte of traffic. New customers are enticed in the usual way: after registering, they’re promised 25 GB of storage for a year and 25 GB of traffic monthly.
In its current form, this business model seems questionable to us. A more realistic way to profit from Storj might be to launch your own project involving “cloud,” “fog,” “liquid-drop” or any other kind of file hosting. Then, develop user-friendly client applications and set a reasonable pricing for the services. This approach is more challenging than simply dreaming about free Storj coins trickling down to spinning disks, but unlike a crypto-utopia, it may actually work.