All information is provided for reference only. Victoria uses low-level operations, the meaning of which is described in the manual. The editorial board and the author shall not be liable for any possible harm.
[/panel]From MS-DOS to Windows 10
Victoria was conceived as a means of advanced diagnostics of storage devices (then hard drives, and today also SSDs) and management of their operating settings through low-level commands. Belarusian programmer Sergei Kazansky spent ten years developing it and releasing his own set of utilities for data recovery. During this time, there have been many commercial releases of Victoria, several free versions, and one unofficial one, which we will pay special attention to.
Victoria was originally a disk utility for MS-DOS written in assembler. The ancient operating system was a better fit than Windows because it is easier to provide exclusive access to the disk in a single-tasking environment. With the advent of support for the porttalk.sys driver, Victoria versions 4.xx have learned to work in the multitasking WinPE environment, as well as in Windows from XP to 10 of any bit depth. It has become easier to launch, the actions in the graphical interface have become more visual, and the operating mode itself has changed. But here is the problem: without understanding the new features of the program, some users began to lose data and entire disks instead of restoring them. Therefore, the latest official version 4.46b has advanced “foolproofing”.
By default, only non-destructive operations with storage devices are available in it. This is not just a read-only mode like other utilities that access HDD/SSD via Windows driver. Victoria also blocks the ability to change HPA (and mess up disk geometry), accidentally run low-level formatting, and “shoot yourself in the foot” in more sophisticated ways when it first starts.
[panel]Universal soldier
Victoria is the most versatile utility. It accesses any type of storage device (HDD, SSD, USB Flash) and with any ATA-compatible interface. Its job is to transmit ATA commands to any device that supports them. Therefore, everything said about Victoria work with disk drives is also true for solid-state drives, with the exception of what relates to their design features. It is clear that for an SSD it is pointless to watch the spindle spin-up time and try to control the speed of head positioning – it has neither one nor the other. However, it is quite possible to test and even restore SSD using Victoria.
[/panel]Victoria 4.47
This version was made in 2013 by Moscow programmer Oleg Shcherbakov. He patched the latest official build of Victoria 4.46b. It is better to download it here. On this site Shcherbakov published it together with the source codes of the patches. Other resources can distribute whatever they want under the guise of the new “Victoria”.
[panel template=info]At the time of writing, the abandoned website of the Victoria program developer was infected. Therefore, instead of the URL www.hdd-911.ru specified in the program documentation, a link to an alternative source for downloading the Victoria utility is provided.
[/panel]Although Victoria is far from a new program, it contained critical errors that required correction. One of them made it impossible to run Victoria on 64-bit versions of Windows. Another reason could be problems when working with large disks. If the volume was over a terabyte, Victoria 4.46b simply spent all the virtual memory on rendering and color-coding the LBA blocks being checked. In version 4.47 Shcherbakov fixed all this.
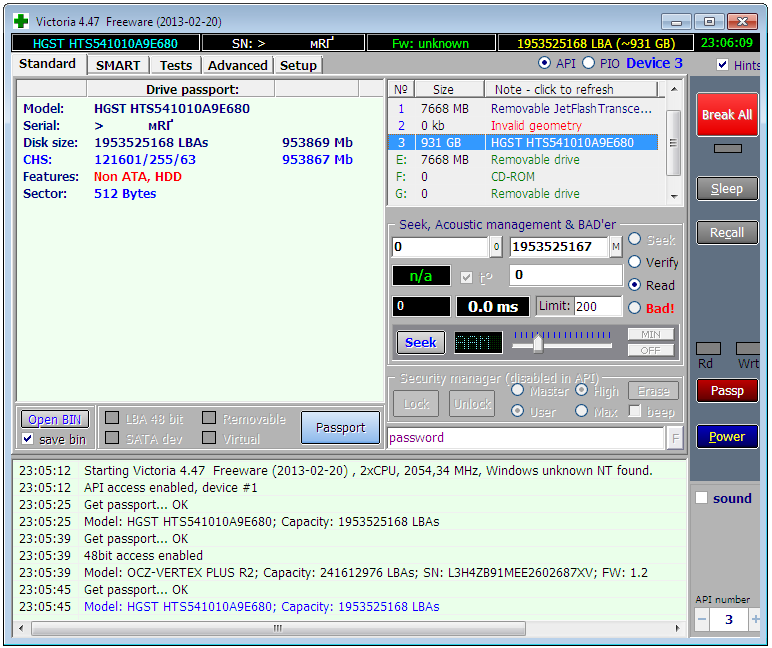
PIO vs API
Victoria has two modes of operation: PIO (port input/output) and API (application programming interface). In PIO mode, the drive controller is polled by the program via the porttalk.sys driver. If you select API, the operating system tools will be used. Disk performance drops in PIO mode because DMA and high-level read/write optimizations are not supported. However, PIO mode allows you to use all the capabilities of Victoria and send any ATA commands directly to the disk controller, bypassing the OS and standard drivers. It is through PIO that data recovery labs most often work with disks. Victoria supports both drives with a modern SATA interface and older ones – PATA (aka IDE). Victoria can also work with external drives (features will be described below).
Having selected the PIO mode, at the beginning of work it is necessary to scan the bus and identify disk controllers using the PCI-Scan button. To the right of it, a disk port selection window is displayed. Internal ones are usually detected without problems, but for external drives you will first have to find out their port. This can be done in the hardware properties or in any diagnostic program (for example, AIDA64). After this, you need to manually set the port in Victoria. Also, when scanning, you can check the All dev (all devices) box and use the exclusion method to find the required disk in the list of found ones.
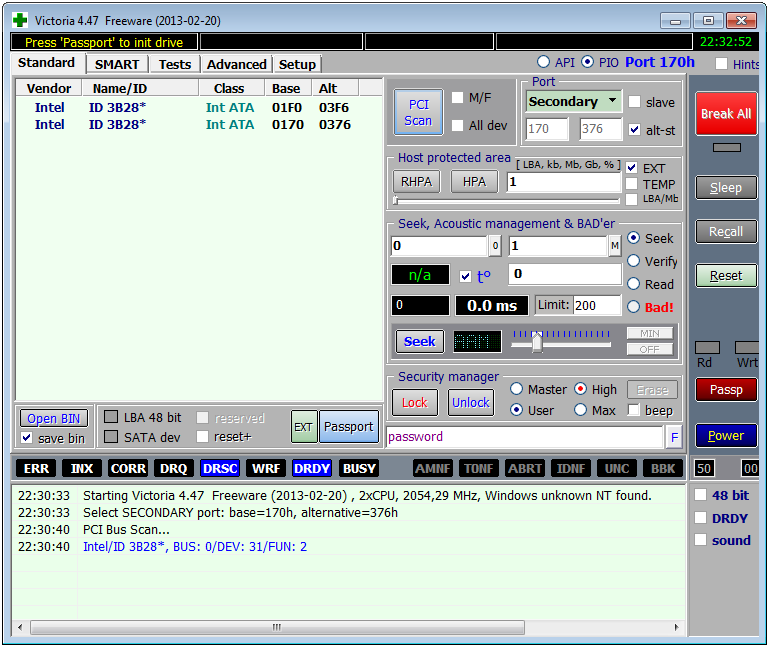
It is advisable to use PIO mode specifically for low-level commands. Simple searching for bad sectors and reassigning them to the spare of disk area is much faster (but less reliable) in API mode.
The API mode has the following limitations: you cannot set or remove ATA passwords, and working with the Host Protected Area and viewing registers is also disabled. If any of these functions are needed, you can switch to PIO mode. It happens that PIO mode is not available. This happens when using older versions of Victoria on 64-bit OS. Another reason may be errors in working with the porttalk.sys driver or selecting the SATA AHCI mode. The guaranteed way out of this situation is as follows.
- Burn a bootable USB flash drive with WinPE x86 and place the Victoria program on it by simply copying it.
- Connect the required drive to the SATA/PATA port, if you haven’t done so yet.
- Disconnect all other HDDs or SSDs (optional).
- We go into CMOS setup, switch the SATA controller mode from AHCI to compatible (compatible, native or IDE).
- Load WinPE. If necessary, we install additional drivers, including porttalk.
- We launch Victoria in PIO mode, initialize the required HDD or SSD and execute the required command.
Settings can be set via GUI or in the vcr40.ini file. This same file will help to remove the blocking of work with the primary port. It is enabled by default to protect the system disk from accidental modification. To be able to select Primary in the list of ports, you need to do two things:
- Disable the “non-destructive functions only” option and close the program.
- In the
[section of the vcr40.ini file, add the lineATA Port] Enable, save the changes and restart the program.PM=1
Porttalk
The latest versions of Victoria can automatically install the porttalk driver, but it is completely useless on 64-bit systems. The thing is that for the sake of greater security they removed a couple of functions that are necessary for porttalk and Victoria to work. Therefore, the porttalk driver (and, accordingly, the PIO mode) only works in 32-bit versions of Windows, where the Ke386SetIoAccessMap and Ke386IoSetAccessProcess functions are available.
External storage devices
External drives are regular laptop (2.5″) or desktop (3.5″) models in containers with USB and FireWire interfaces. They are equipped with various controllers with the common name “SATA bridge”. Many of these bridges do not broadcast low-level commands. Therefore, Victoria can immediately work with some external drives in PIO mode just like with internal disks, but with others you will have to suffer first. In the simplest case, it will be enough to remove the disk itself from the case (do not open the hermetic block!) and connect it directly to the port.
[panel]Rare beast: SATA hard drive without SATA port
Western Digital and possibly other manufacturers released some external hard drives with a soldered SATA-USB bridge. That is why they do not have a regular SATA connector. However, they can still be connected directly to the port by soldering a SATA cable to the pins on the board of drive. To understand whether your drive belongs to this series, you will have to google the model number and look for datasheets.
[/panel]Passwords
One of the most popular low-level commands in PIO mode is working with passwords. According to the specifications, access to the disk can be restricted using a password. It is set by the user from the BIOS or using external utilities. There is also a master password preset by the manufacturer. The disk can only be locked using a user password. If you forget it, the blocking can be removed using the master password.
Depending on the security level you set, the result of entering the master password will be different. At the high level, the master password acts as the user password. It just unlocks the disk and that is it. If the maximum security level (max) is set, then entering the master password instead of the user password will unlock the disk only after completely erasing all data on it (secure erase).
Working with ATA passwords is further complicated by the fact that, according to the standard, they always consist of 32 bytes (no matter what length you set them to). Extra characters are ignored, and missing ones are added automatically. The problem is that different programs complete them differently. The standard security utilities on some laptops are especially guilty of this. Instead of traditional zeros (or at least spaces), they use non-printing characters. The code 00h cannot be entered from the keyboard at all (even via {ALT}+code). There is only one way out: do not enter the password in the program window, but read it from a file. Any symbols can be written to a file using a hex editor.
Often the user cannot unlock the disk even when entering the correct password. If you change your laptop or lose the standard utility, any other one (for example, HDDL) will add its own characters to the password up to 32 bytes.
Preliminary password modification is also possible. In many laptops it is actually encrypted before being sent to the controller. These are usually the simplest logical operations, but that does not make it any easier. The user thinks that there is a password known to him, while in reality the controller accepts a completely different one. If you have tried all the options of the supposed user and standard master passwords, but have not achieved a result, then there is only one way out – take the drive to the lab, where they will work with it in technological mode.
[panel]How to get back a lost terabyte
Sometimes it is very helpful to be able to operate Victoria in PIO mode with HPA (Host Protected Area) – a service memory area in which the disk geometry is recorded. It defines the capacity of the drive by specifying it as a number of LBA blocks.
I had an interesting case in my practice. Received a standard complaint: “the computer won’t turn on” (read: the OS won’t boot). The owner complained that he had been suffering for about a month. First, he visited all the service centers, then invited different service technicians – to no avail. I arrived, looked and also thought hard. All components are in good working order. The disk is detected in the BIOS, but it does not boot. Launched Linux from a flash drive. The hard drive is visible, but the logical partitioning utilities show a strange picture: 64 MB total capacity and one partition with an unknown file system.
And then I realized that the HPA on the hard drive had simply failed. As a result, a terabyte disk became defined as a 64-megabyte stub. I switched the SATA ports mode from AHCI to compatible in CMOS setup, took a flash drive with WinPE and launched Victoria in PIO mode. Then I sent the NHPA command (restore factory volume).
Usually in such cases it is possible to instantly restore the passport value of LBA blocks, but this time the miracle did not happen. So I found a service utility for this series of hard drives and sent a similar HPA recovery command from it. A terabyte of data came back from oblivion on the next reboot.
Why did Victoria let us down? I guess because this disk had some specific features unknown to me or the universal program.
[/panel]Bad sectors
Victoria is most often used to find and fix bad sectors. If the disk is HPA is OK and there is no password protection, but no utilities can read files from it in a reasonable time, then it is time to check the surfaces. Victoria can do this in any mode (PIO/API) using sector-by-sector reading (read), writing (write) and writing with verification (verify).
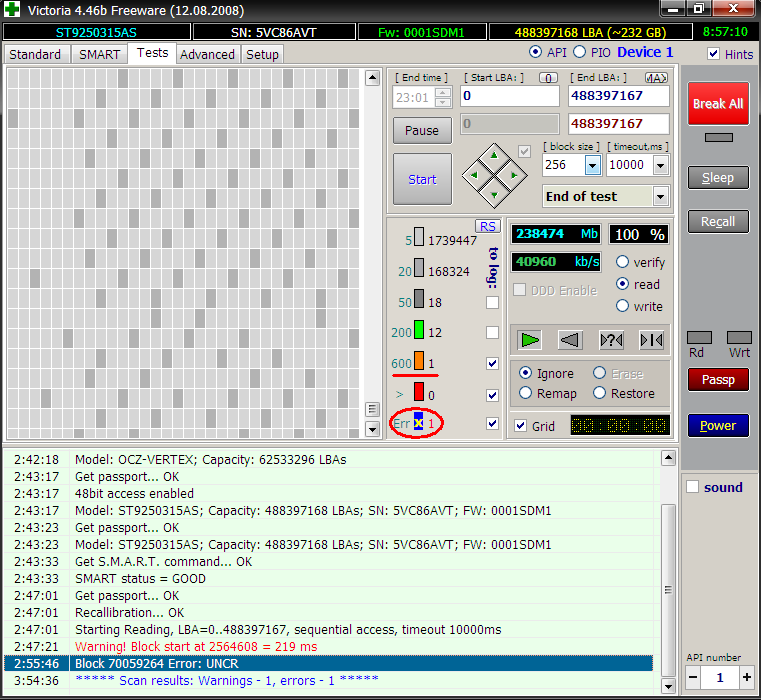
When recovering data, you can use read-only mode, but its options also vary. The simplest of them is sequential: from the first block to the last. The start and end LBA values can be specified manually, which is convenient for many reasons. Firstly, this makes it possible to test disks of any size by simply performing the test in fragments of up to one terabyte. Secondly, you can recheck the suspicious area and rule out external factors. Victoria analyzes the time of access to the sector. Typically, for new drives it does not exceed 5 ms for 80% of sectors. Sectors with a polling time of less than 50 ms are also considered normal. Those for which it is measured in hundreds of milliseconds are candidates for bad sectors.
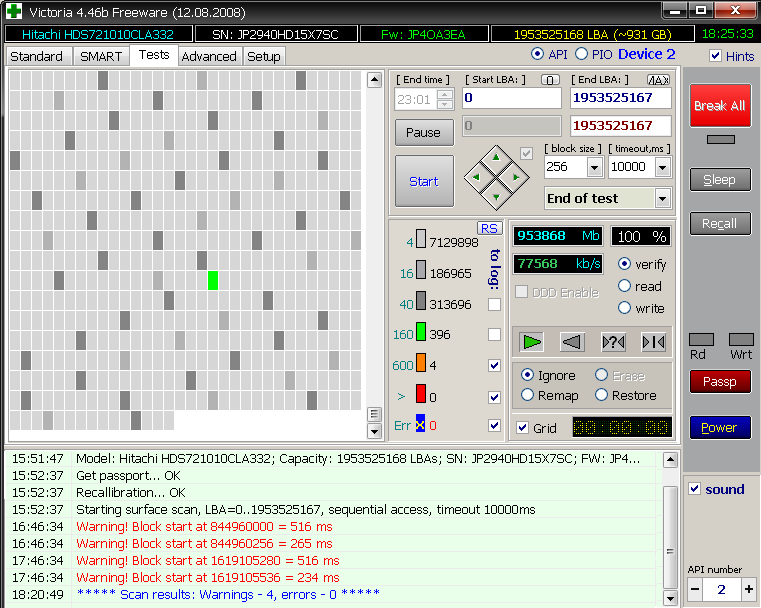
If the sector was read after several seconds, then this is a clear bad block. The disk controller must detect such sectors independently during downtime and replace them in the address table with healthy sectors from the reserve area. However, in practice this does not always happen. Victoria can ask the hard drive to do such an operation (Remap) for those sectors that have not responded to requests for too long. Formally, some information is lost during this procedure, but in reality it was already lost at the moment when the sector became faulty.
The paid version of Victoria had a Restore function available – an attempt to read data from a bad sector at any cost and then rewrite it to a good sector. However, the program has not been officially supported since 2008, so it is unlikely that you will be able to purchase its full version. Free Victoria has helped me out more than once by restoring HPA, resetting passwords, and eliminating bad sectors that caused other data recovery programs to freeze.
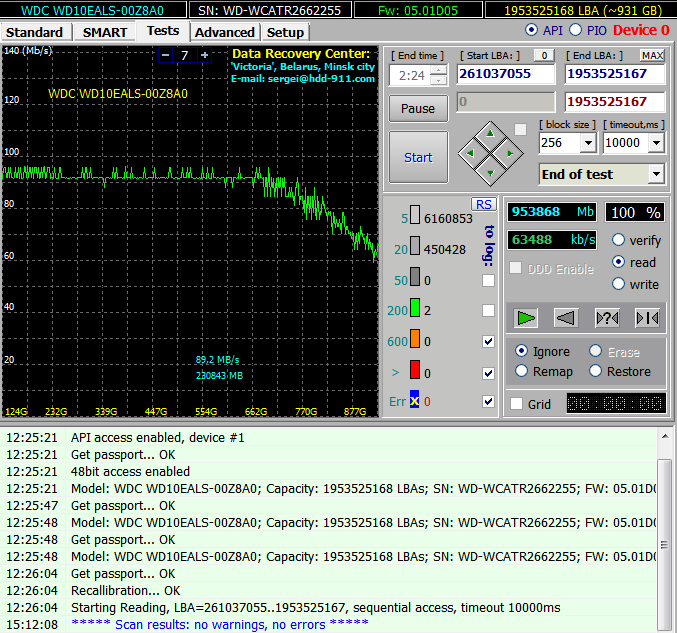
How Free Victoria Saved a Secret Job
I will share one more story with you. Laboratory at a research institute, present day. The analytical instrument is controlled from a computer that came with it. The computer has very specific software pre-installed that the developers no longer support. The distribution is not on the disk or on the website. There is only one installed program and it stopped working. The laboratory carried out the research under a multi-year government contract. Without the miracle device, the employees found themselves tied hand and foot. We suffered and found out that the problem was with the disk. Due to its ancient history it became covered with problems and normal work became impossible. An attempt to clone a disk by skipping bad sectors was unsuccessful – the cloning program hung completely. We ran the disk through the Victoria test with the Remap function. We have pre-selected the necessary settings. By the evening of the same day, we successfully removed the disk image, and then restored everything from it to a new hard drive. The device came to life, the contract was completed on time.
[/panel]Victoria’s Additional Features
Victoria analyzes the state of the drive in detail and can eliminate almost any failure in its operation. Actually, this is what distinguishes Victoria from many other utilities. While most programs simply display SMART attributes, it can force entire sets of self-diagnostic tests to run.
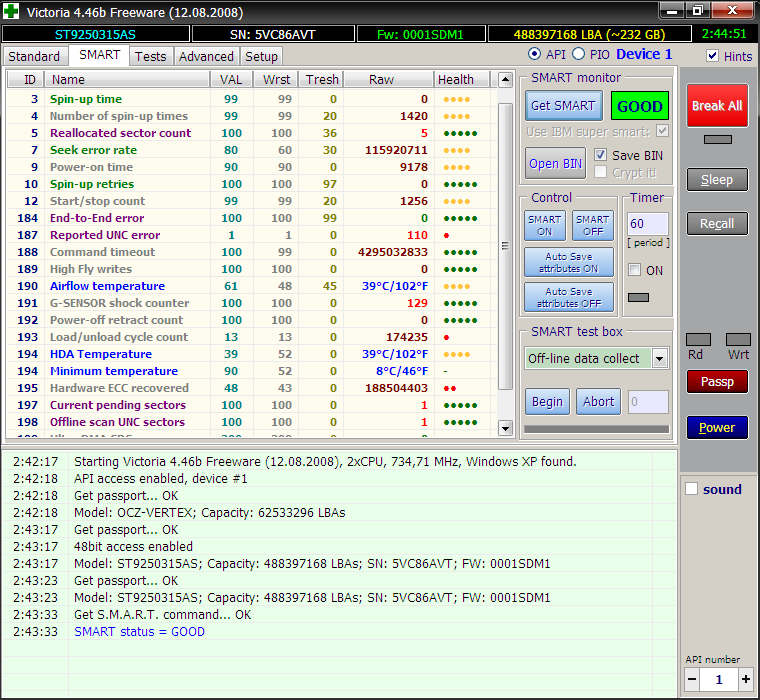
Victoria has four methods and three types of surface testing (twelve modes in total). In each one, it automatically counts the total number of defective blocks and writes their addresses to the log. Like a disk editor, Victoria can show the contents of sectors and allows you to change them. In PIO mode, Victoria displays information about logical partitions on the drive even if it is not detected at all in BIOS. No utility with API access is capable of this. Additionally, Victoria can manage the acoustic noise level of the disk (AAM), adjusting the speed of its heads during search, run low-level formatting, change the HDD volume and perform benchmarks. It can even be used to check the physical interface (the status of cables and ports). At home, it will save an HDD or SSD in many difficult situations, except for severe mechanical damage that requires opening the hermetic block. The laboratory will cope with them too, using Victoria as one of the proven utilities.
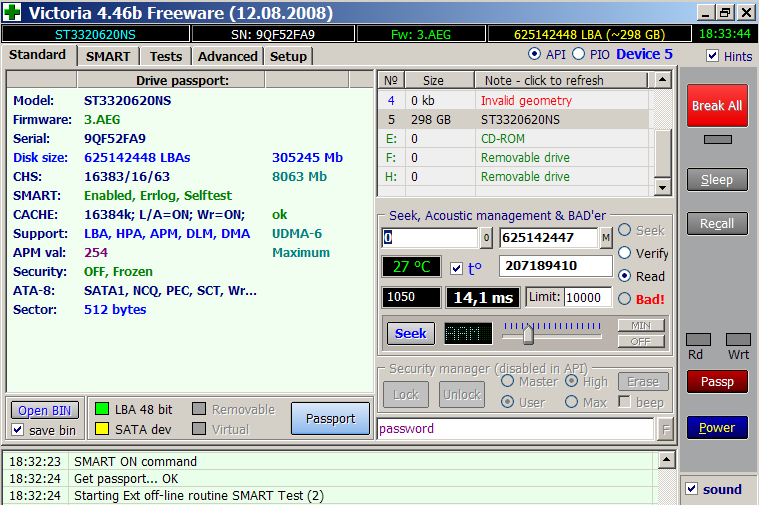
Conclusions
There is much more that can be written about Victoria, but for details I will still have to refer you to the Russian-language documentation. And, since the versions of the program differ in all sorts of subtleties, I recommend reading the manuals for versions 3.5.2, as well as 4.46b and 4.47.
[panel template=www]Other free utilities for checking different types of storage devices and recovering data from them
Old versions of disk utilities
Foreign utilities for restoring drives in step-by-step wizard mode
[/panel]