warning
Experience indicates that most breaches are executed using the simplest methods. The author is merely discussing technical hacking capabilities and is not encouraging any illegal activity. The only way to effectively defend against network attacks is to engage in them yourself and see things from the attacker’s perspective. Otherwise, any audit becomes a superficial compliance check.
Toolkit
All you need for a quick start is a basic Android smartphone or tablet. If you’re not trying to hack into a specific, well-protected network but just want to connect to a nearby secured Wi-Fi, this will suffice.
Initial wireless reconnaissance can be performed on devices running Android 2.3–4.4, and starting with Android 5.0, it’s possible to execute basic WPS PIN attacks even without root access. You just install a couple of apps and press a “do the job” button. However, as always, the real intrigue lies in the details.
Preparing for the Attack
There are numerous common attacks on Wi-Fi access points and specific exploits for certain models with particular firmware versions. Typical attacks include methods like cracking the WPS PIN, calculating WEP and WPA2 keys by analyzing captured packets, and forcing the access point to switch to a weaker encryption algorithm (such as WEP instead of WPA).
Social engineering methods have a special place in cyber tactics: for example, creating fake Access Points (APs) that mimic the targeted network to capture real passwords or to execute various Man-in-the-Middle (MitM) attacks. Additionally, techniques such as deauthorization/jamming of wireless clients and Denial-of-Service (DoS) attacks are used as independent objectives.
The most versatile method of attacking an access point is by cracking its WPA2 key using individual messages (M1-M4) from captured handshakes. This approach almost always works but requires significant resources, especially time. Capturing handshakes is always done in monitor mode, which not all Wi-Fi chips and drivers support. To speed up the collection of handshakes, packet injection is needed. This function deauthorizes clients connected to the AP, prompting them to frequently resend handshakes. However, only a few Wi-Fi modules support packet injection.
With rare exceptions, the pre-installed drivers in smartphones don’t even allow for the activation of monitor mode, and alternative drivers for built-in chips are not always available. Therefore, hackers often use external USB Wi-Fi adapters with hacker-friendly chips (primarily from Atheros and Ralink) for hacking purposes. For more details, refer to the article “Choosing a Budget Adapter for Wi-Fi Hacking”.
However, there’s a workaround that doesn’t require purchasing hardware or dealing with driver headaches. Many access points with robust security (like WPA2 PSK CCMP) sometimes have WPS enabled—a secondary method of authentication using a PIN code. This PIN often remains at its default setting and can be easily calculated.
Theoretically, an eight-digit WPS PIN can have 100 million combinations, but only 10 million of those are unique because the last digit is a checksum and depends on the other seven digits. In practice, however, only about 11,000 combinations need to be tested due to vulnerabilities in the algorithm itself (similar in concept to those found in the LM hash, more details here).
Brute-forcing 11,000 PIN codes can take about half a day under good signal conditions, as each attempt takes between two to ten seconds. Hence, in practice, attackers use the fastest methods to exploit WPS vulnerabilities—targeting default PIN settings and their reduced entropy (pixie dust attack). To counteract brute-force attempts and connecting to fake access points, a hash exchange between the AP and client devices is implemented. These hashes are supposed to be calculated based on the WPS PIN and two random numbers. However, in practice, many routers either generate predictable numbers or leave them as zeroes, drastically reducing entropy. This flawed implementation undermines the intended security enhancement. Additionally, some manufacturers set the WPS PIN as a derivative of other known values (such as the MAC address), making these access points very easy to compromise.
The relevance of WPS attacks is further highlighted by the fact that, in some access points, the Wi-Fi Protected Setup feature is enabled by default and cannot be turned off using standard methods. Due to flawed firmware, there may be no option in the device’s settings menu to control this, or the enable/disable switch is ineffective. This is likely one reason why there are still plenty of easy targets among the many “secured” wireless networks in any city.
Reconnaissance
The entire process of wardriving can be divided into two stages: gathering information about access points and then attempting to breach them. There are numerous ways to scan wireless networks with a smartphone, but they differ significantly in the level of detail they provide. Some apps only display the SSID and signal strength, similar to a system app, while others show all parameters of the detected access points. Notably, they indicate the type of security used and allow filtering the list by various criteria.
Among such applications, I would recommend using WiFinspect. It was developed under the guidance of Dr. Tom Clothia from Birmingham University in 2012. The current version 1.2 allows you to conduct audits in compliance with the PCI DSS 2 data security standards. With it, you can obtain detailed information about the operating modes of detected Wi-Fi access points, perform basic penetration tests using default passwords, and learn a lot about connected devices. The app is free and contains no ads, but most of its features require root access.
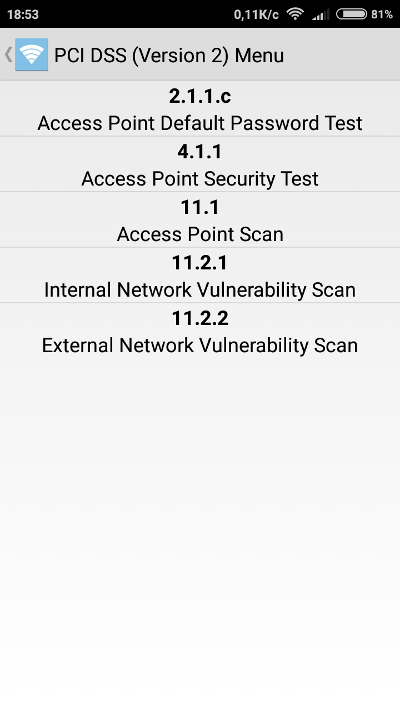
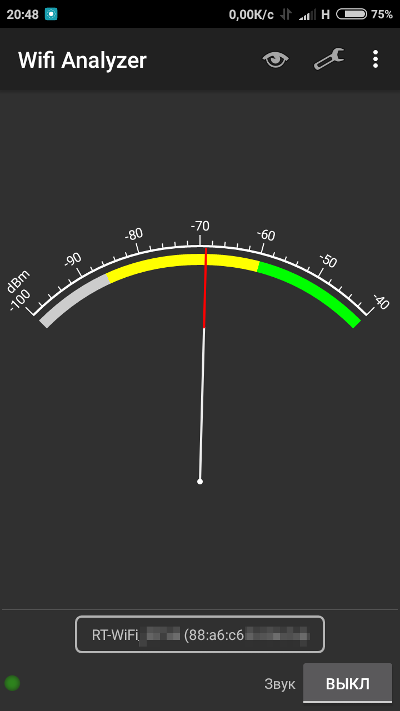
Another popular application that complements WiFinspect is Wifi Analyzer. This app is capable of scanning both 2.4 GHz and 5 GHz bands and operates without needing superuser permissions. Wifi Analyzer displays a wealth of information, including the channel number of the selected access point, its MAC address, the manufacturer (determined from the MAC), and provides detailed descriptions of encryption types. To access this, simply enable “Show full security level” in the settings. The app does have one downside: intrusive ads in all of Wifi Analyzer’s screens. These ads can be removed using AdAway (which requires root access) or by purchasing the paid version.
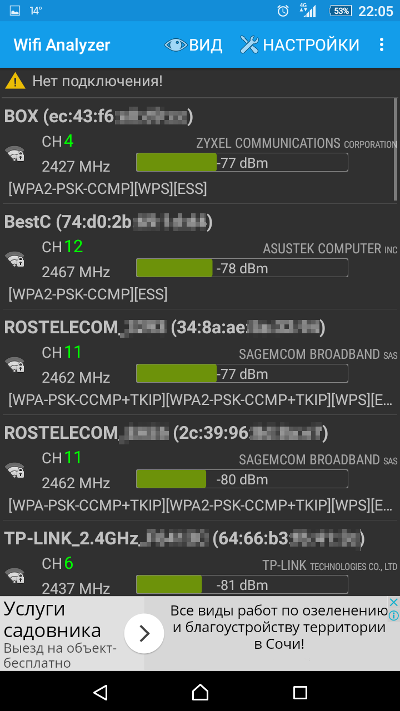
Both applications complement each other perfectly and work on almost any device with Android 2.3 and newer. They are convenient tools for scanning the airwaves and pre-selecting targets. All detected access points (APs) can be sorted by signal strength and security level, making it easy to identify the most accessible APs.
There is an open-source WiFiAnalyzer available on Google Play. It’s free, ad-free, can filter access points by their security type, and even attempts to estimate the distance to them in meters (as if they were all broadcasting in a straight line). However, it lacks a “fox hunting” mode – continuous signal level measurement for a selected access point. Otherwise, the app is similar to others.
info
It’s interesting that some owners simply hide the SSID of their wireless network without bothering to set up proper authentication. Others configure strict authentication for the 2.4 GHz band but completely overlook the parallel 5 GHz network. Among dual-band access points, you can find these “semi-secure” setups.
Pitfalls
The effectiveness of reconnaissance depends on the wireless communication module installed in the smartphone. This module may have both hardware and software limitations. Hardware limitations relate to the receiver’s sensitivity and its support for various IEEE 802.11 standards. Not all smartphones are equipped with dual-band Wi-Fi. Software limitations are often determined by the driver used and the region set on the device.
We will discuss drivers in the next section, but for now, let’s focus on a less obvious point: different regions around the world have allocated their own frequency ranges within the same standard. For example, the 802.11b/g/n standard uses frequencies ranging from 2412 to 2484 MHz, broken down into 14 channels with a 5 MHz step between the base frequencies. However, in Russia, the use of the 14th channel is prohibited, and channels 12 and 13 are not recommended because, with channel widths of 20–40 MHz, there’s a high risk of interference on prohibited frequencies. A similar situation exists in Ukraine and other former Soviet Union countries. As a result, nearly all Wi-Fi-enabled equipment intended for the CIS region effectively operates only on channels 1–11 or even 1–10.
Savvy tech enthusiasts sometimes take advantage of this cautiously (and not always legally) to suit their needs. For instance, one company uses channels 12–13 to connect its wireless video surveillance equipment, reducing interference from nearby access points. Meanwhile, wardrivers simply change regional settings to gain access to “restricted” channels. Hint: all 14 channels are currently permitted in Japan.
info
While you can technically set up wireless communication on non-standard frequencies (below 2412 MHz) using 802.11b/g/n standards, this would require specialized equipment and a license—not just approval from the local radio frequency center. The likelihood of an individual obtaining such documentation is virtually zero.
The First Encounter
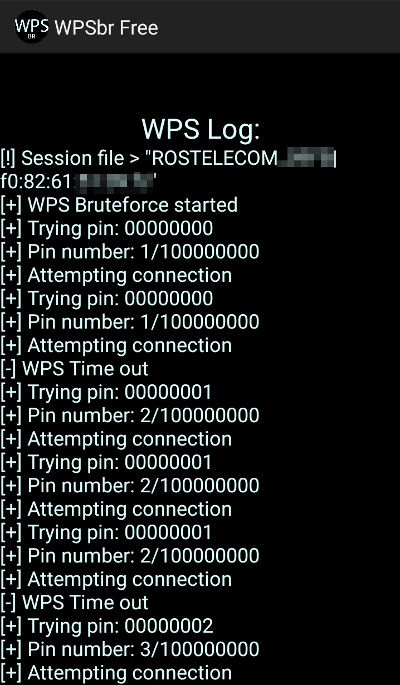
Google Play is filled with apps for brute-forcing WPS pins, as this is the only type of attack that works on any rooted phone (up to Android 4.4) and even unrooted ones (starting with Android 5.0). However, most of these apps are poorly made, and their practical usefulness is highly questionable. For instance, WPSbr Free unnecessarily attempts all 100 million pin combinations, checking them twice even with a strong signal. This exhaustive approach would take approximately 16 years, but most access points (APs) will block such a direct attack much sooner. After a few incorrect pin attempts, the client device may be blacklisted, requiring a MAC address change to continue the brute-force attack.
The WPSApp program offers a more refined way to select PINs. It filters out all detected access points, keeping only those with active WPS, and sorts them by decreasing Signal-to-Noise Ratio (SNR).

All potentially vulnerable access points in WPSApp are marked with a question mark. For these, the app suggests trying one of five default PIN codes. The developer didn’t complicate things with a brute-force script and instead recommends doing it manually, offering two methods—one requiring root access and one not.
If the default PIN code is already known (calculated as a derivative of the MAC address using the ComputePIN algorithm), then that access point is marked with a green checkmark.
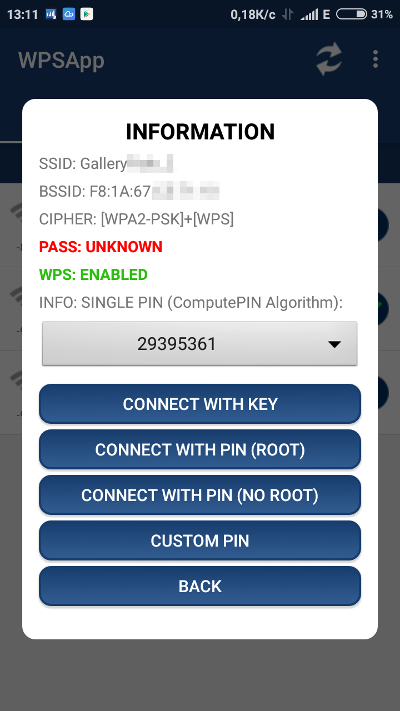
If the PIN code works, you’ll immediately get the Wi-Fi password (WPA-PSK), no matter how complex or lengthy it is. You can save the password and move on to the next access point. After a while, your phone will be able to use Wi-Fi where it used to only have 3G/4G connectivity.

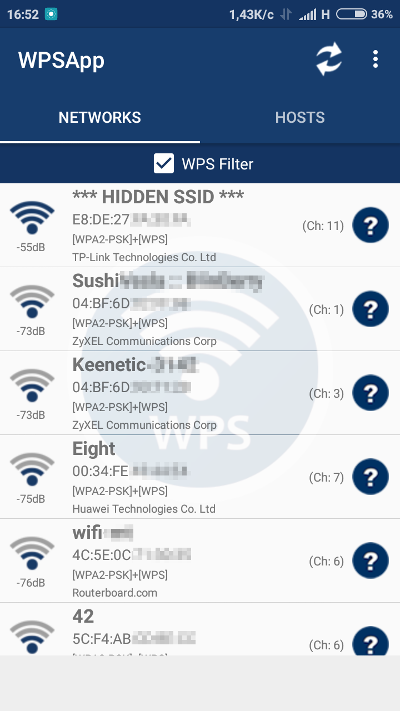
A slightly more advanced tool is WiFree WPS. Essentially, it combines features from WPS PIN and Router Keygen. It includes a larger database of default router PINs and passwords and has an automated function to cycle through them. Additionally, it displays saved Wi-Fi passwords and all current connection settings.
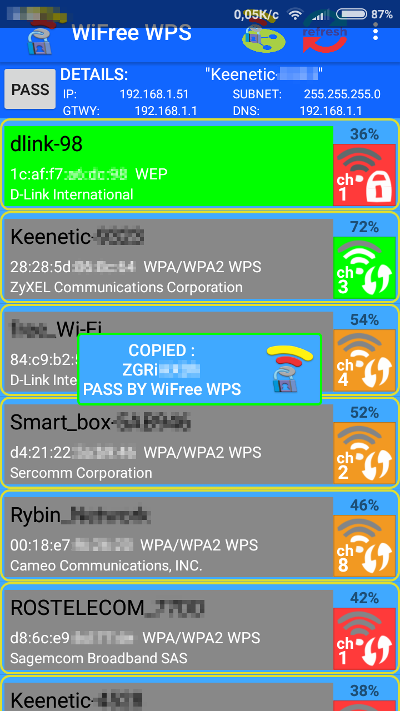
The program’s interface is somewhat clunky, but it provides plenty of useful information. It assesses the security type, manufacturer, and signal strength of all detected access points. Access points most likely to be hacked are marked in green. Those that require trying out 10-20 standard PINs are shown in gray, while those that are difficult to breach, for example due to a very low signal level or lack of WPS PIN authorization, are marked in red. WiFree WPS offers two attack modes: with root (requiring a patch and BusyBox) and without root (works on Android 5.0 and above, and is faster than similar programs).
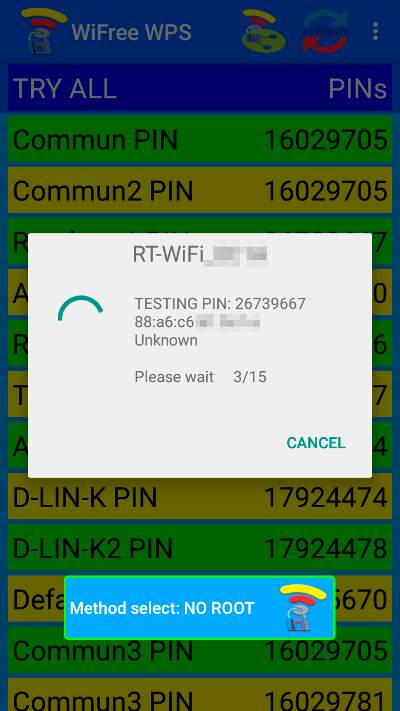
If the program’s database lacks default PIN codes for devices from a particular manufacturer, that access point will be highlighted in red. You can attempt to connect by manually entering the WPS PIN. However, several factors might impede successful crack attempts: weak signal strength, button-activated WPS authorization mode, changes to the default PIN, or MAC address filtering.
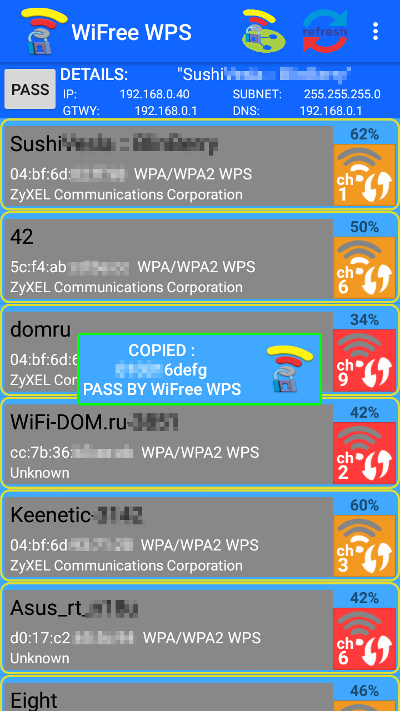
After you’ve cracked the WPS PIN and discovered the access point’s password, you can connect to it and explore the wireless network. For this, I recommend using the free toolset Fing — Network Tools.
The application features a clean and intuitive interface, with menu items that are self-explanatory. For instance, you can scan an access point and learn a wealth of details about it.
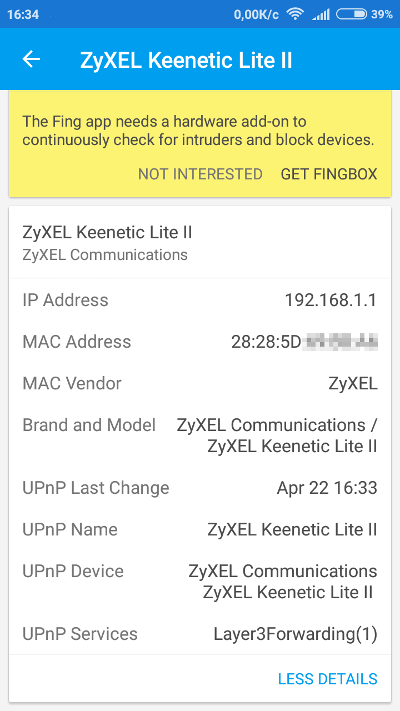
Next, send out ARP packets to discover all connected devices in the wireless network, including your smartphone.

Check the available services and open ports on any node within this network.
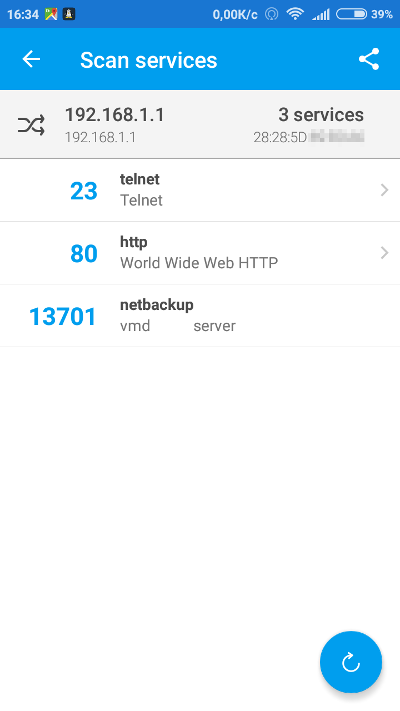
Fing even offers to connect directly to any of them, for instance via Telnet.
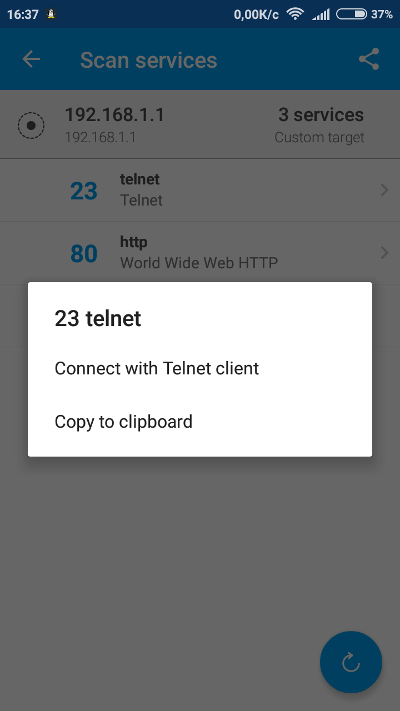
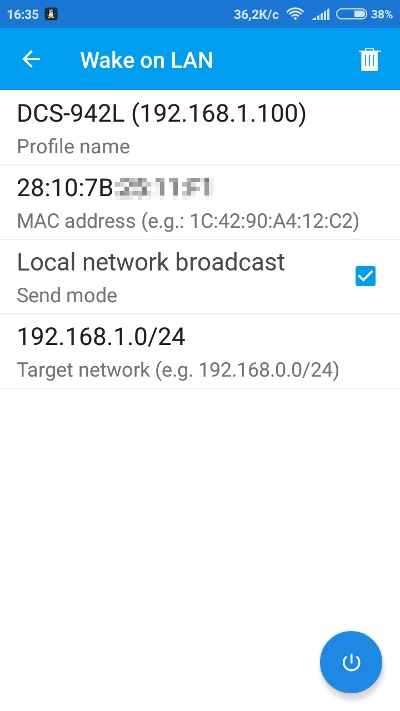
There is a lot of room for creativity here. You could even remotely power on a sleeping device if it supports Wake-on-LAN technology or initiate a group wake-up with a broadcast WOL request.
Finding the Sweet Spot for Signal Reception
The success of any attack on an access point depends on the strength of its signal, specifically the signal-to-noise ratio (SNR) that you measure at a given location. In practice, if the signal level is below -75 dBi, it’s better to find an area with a stronger reception or look for other targets. It’s not always wise to move closer to the access point in hopes of achieving a more stable connection. Sometimes, you’ll find yourself closer to a source of interference (like a microwave or another access point on a nearby channel), and a strong reflected signal can be picked up around a corner or in a completely unexpected location. Using the continuous signal level measurement mode in Wifi Analyzer can help you locate it.
What’s Next?
In the next article, we will discuss how to bypass certain restrictions and delve into more advanced attacks using sophisticated tools. For advanced attacks, you’ll need root access, a set of console utilities (BusyBox), manually installed programs not included in BusyBox, a terminal emulator, USB-OTG (software and cable), external USB Wi-Fi adapters with specific chipsets, wireless module drivers that support monitor mode (mandatory) and packet injection (preferable), kernel patches, Linux distributions prepared for chroot, and a lot of patience.
