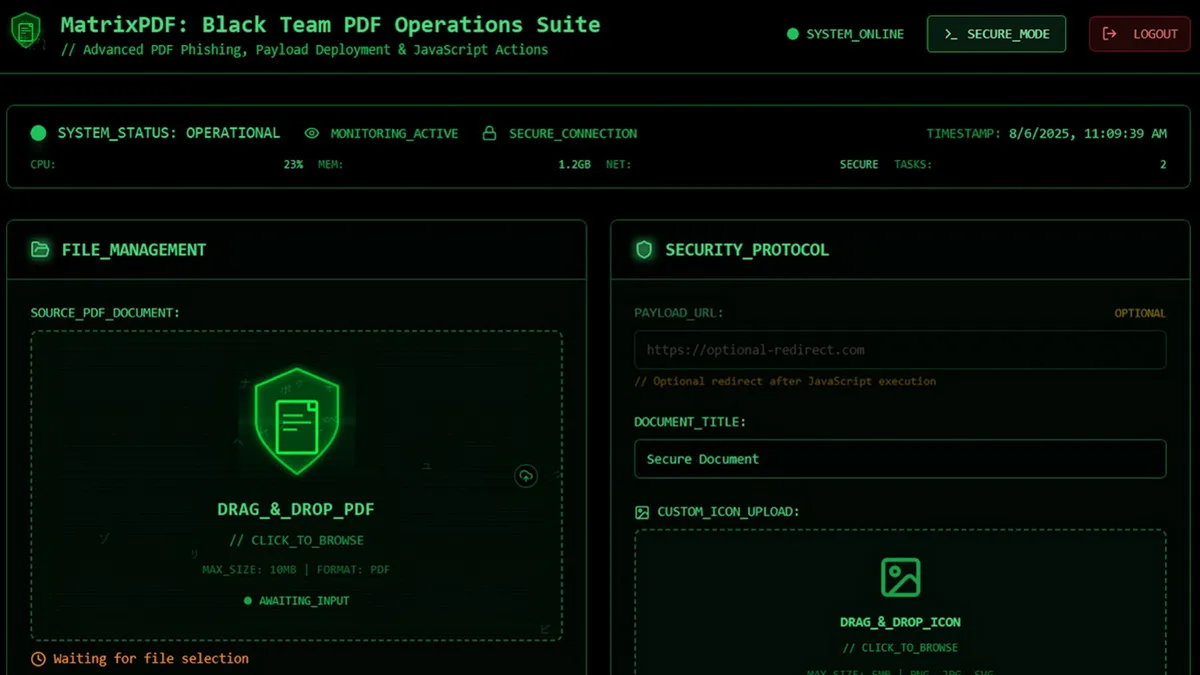
A new phishing toolkit, MatrixPDF, has been discovered that allows attackers to turn ordinary PDF files into interactive lures that bypass email security and redirect victims to sites for credential theft or malware downloads.
Researchers at Varonis who discovered the tool note that MatrixPDF is advertised as a phishing simulator and a solution for black team specialists. However, they emphasize that it was first spotted on hacker forums.
“MatrixPDF: Document Builder — Advanced PDF Phishing with JavaScript Actions is a high-end tool for creating realistic phishing PDFs, intended for black teams and cybersecurity training,” the ad says. “Thanks to drag-and-drop PDF import, real-time preview, and customizable overlays, MatrixPDF enables creating professional-grade phishing scenarios. Built-in safeguards such as content blurring, a safe redirect mechanism, metadata encryption, and a Gmail bypass ensure reliability and deliverability in test environments.”
The toolkit is available under various pricing plans, ranging from $400 per month to $1,500 per year.
Researchers explain that the MatrixPDF builder allows attackers to upload a legitimate PDF file and then add malicious features to it, such as blurring the content, fake “Secure Document” prompts, and clickable overlays that point to an external URL hosting a payload.
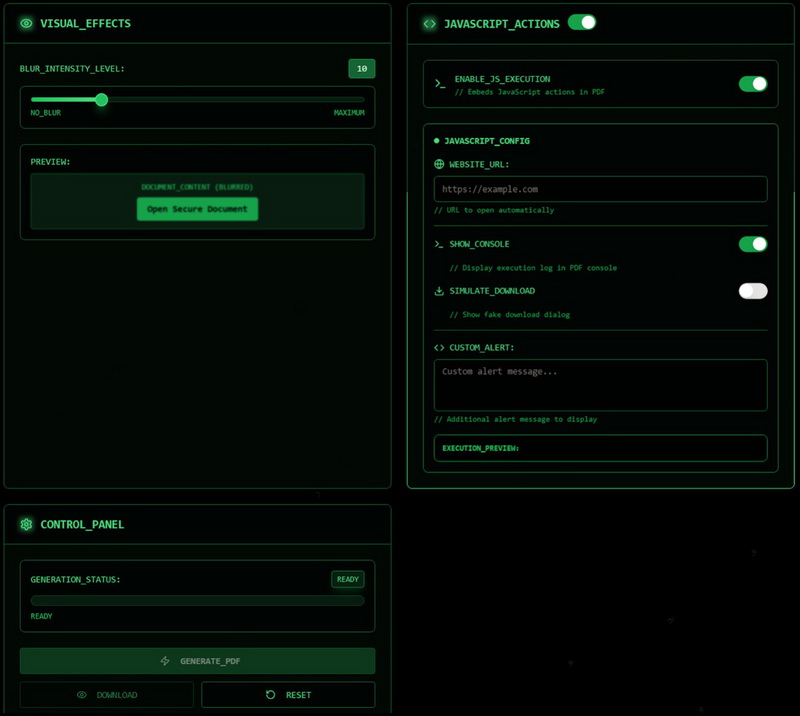
Additionally, MatrixPDF allows the use of JavaScript Actions that trigger when the user opens the document or clicks a button. In this case, the JavaScript attempts to open a website or perform other malicious actions.
The blurring feature makes it possible to create PDF files whose contents appear protected and blurred, and include a button labeled “Open protected document.” When clicked, it opens a website that can be used to steal credentials or distribute malware.
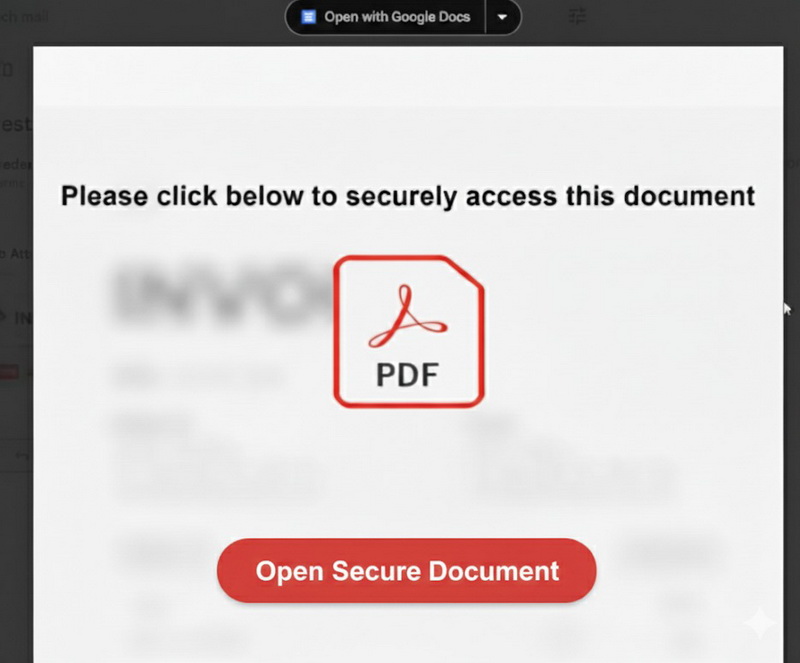
A test conducted by researchers showed that malicious PDFs created with MatrixPDF can be sent to a Gmail inbox, and the email successfully bypasses phishing filters. The reason is that such files don’t contain malicious binaries, only external links.
“Gmail’s PDF viewer does not execute JavaScript in PDFs but does allow following links and annotations,” the experts explain. “In other words, the malicious PDF is crafted so that pressing a button simply opens an external site in the user’s browser. This is a pretty clever trick that allows the attackers to bypass Gmail’s protections: scanning the PDF file itself doesn’t reveal anything suspicious, and the malicious content is only retrieved after the user clicks, which Gmail treats as a user-initiated web request.”
Another test by the researchers demonstrates how simply opening a malicious PDF triggers an attempt to open an external site. This feature is more limited, since modern PDF viewers warn the user that the file is trying to connect to a remote site.
Varonis experts remind us that PDF files remain a popular tool for phishing attacks because they are ubiquitous and email platforms can display them without warnings.