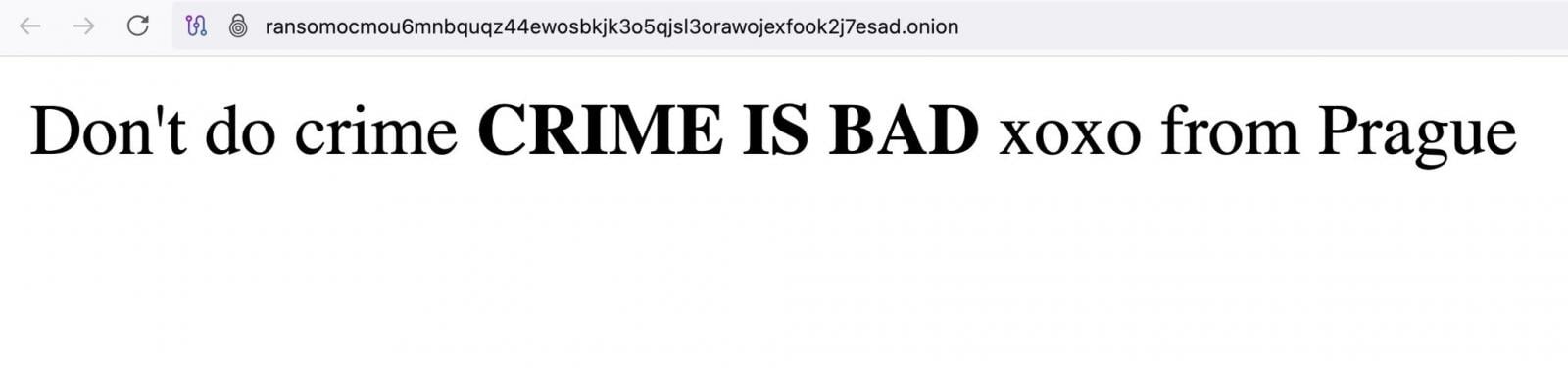
Apparently, Everest operators took down their website after the attack: the resource cannot be loaded and displays an “Onion site not found” error message.
It’s not yet known how the attackers gained access to the Everest website and whether it was actually hacked. Tammy Harper, Senior Threat Intelligence Researcher at Flare, and other experts believe that a potential WordPress vulnerability could be exploited in this attack.
According to Harper, Everest used a WordPress template in their blog, and this could be the case.
The Everest ransomware group has been active since 2020. Over the past years, it completely changed its tactics: from ‘standard’ data thefts for subsequent extortion to the use of ransomware that encrypts compromised systems.
In addition, Everest resells gained accesses to organizations’ networks to other hacker groups and cybercriminals.
Over the five years of activity, Everest published information about 230 victims on its darknet website. The resource was used to implement a classic double extortion scheme: hackers forced victims to pay a ransom under the threat of disclosing stolen sensitive data.
In August 2024, the United States Department of Health and Human Services warned that Everest is increasingly frequently targeting healthcare organizations in the US.
US authorities implicate Everest in several attacks, including data leaks from NASA and the Brazilian government.