All fake Reddit pages use the same social engineering trick: they show a discussion thread on a specific issue. In most cases, the alleged thread creator asks for help with downloading a certain tool; while some ‘Good Samaritan’ offers help by supposedly uploading the required software to WeTransfer and posting a link to it. To make the scam look more credible, a third user thanks the ‘Good Samaritan’.
Unsuspecting users who click on such a link are taken to a fake WeTransfer site that mimics the popular file-sharing service. The “Download” button there downloads the Lumma Stealer payload from weighcobbweo[.]top.
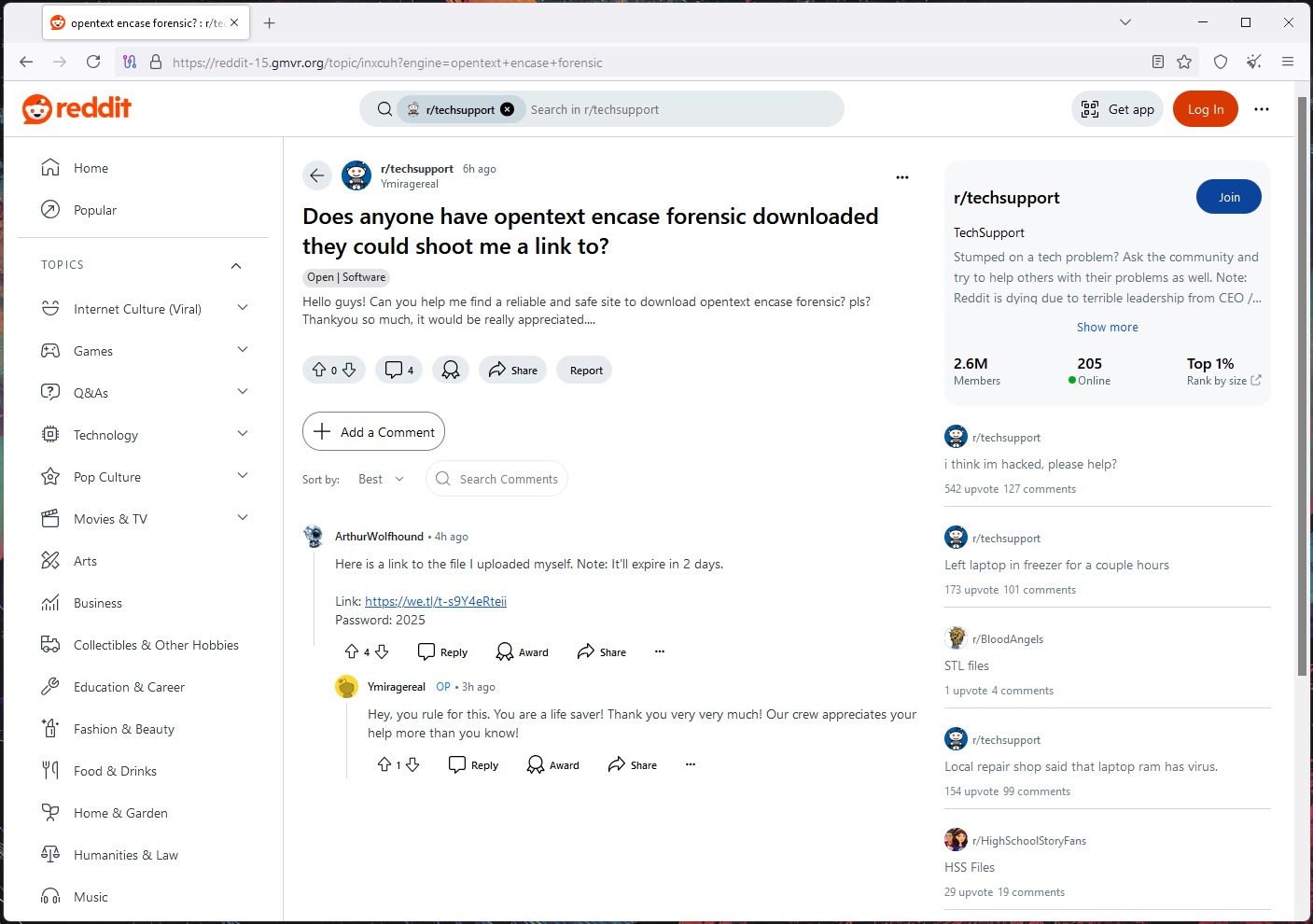
Addresses of rogue sites used in this campaign contain the name of the brand they pretend to be (e.g. Reddit) followed by random numbers and symbols. Most of such fake sites use top-level domains (.org and .net).
The Sekoia analyst published a list of web pages used in this scam. In total, it includes 529 pages disguised as Reddit and 407 pages impersonating WeTransfer.
The number of victims lured to such fake resources remains unknown but Bleeping Computer notes that attacks can begin with malicious advertisements, SEO poisoning, malicious sites, messages sent via social networks and instant messengers, etc.
According to Netskope Threat Labs, malefactors actively spread Lumma Stealer using fake CAPTCHAs. Such attacks exploit the ClickFix (ClearFake or OneDrive Pastejacking) attack vector, which is quite popular among cybercriminals nowadays.
Victims are tricked into visiting rogue websites and running malicious PowerShell commands, thus, manually infecting their systems with malware. In most cases, malefactors require users to pass a fake CAPTCHA test or a verification procedure – allegedly, to solve a browser issue or join a channel.
