Malicious apps of the SpyLoan family usually disguise themselves as legitimate financial instruments or credit services: users are offered low-interest loans with a quick approval procedure, but the terms of such loans are often very deceptive or patently false. In addition, these apps steal data from victims’ devices, thus, enabling the attackers to engage in predatory lending, blackmail, and extortion.
All SpyLoan apps request excessive privileges on the victim’s device, including access to its camera (allegedly to upload KYC photos), calendar, contacts, SMS, location, sensor data, etc. As a result, operators of such apps can steal sensitive data from infected devices.
Cyfirma researchers discovered in the Google Play Store an app called Finance Simplified that was downloaded more than 100,000 times. The app pretends to be a financial management tool.
According to the experts, in some countries (primarily in India), this app exhibits malicious behavior by stealing data from users’ devices. In addition, Cyfirma discovered a number of other malicious APKs that appear to be part of the same malware campaign: KreditApple, PokketMe, and StashFur.
Even though the app has already been removed from Google Play, it might still run in the background collecting sensitive information from infected devices, including:
- contacts, call logs, SMS messages, and device data;
- photos, videos, and documents from internal and external storages;
- victim’s location (updated every 3 seconds), location history, and IP address;
- the last 20 text messages copied to the clipboard; and
- credit history and SMS messages related to banking transactions.
According to numerous user reviews on Google Play, the Finance Simplified app offers lending services, and then its operators attempt to extort money from borrowers refusing to pay enormous interest rates.
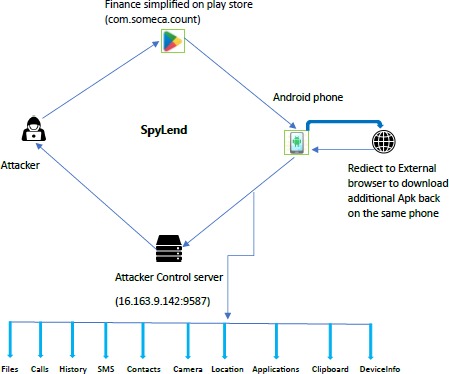
The stolen data are primarily used to blackmail people who have applied for a loan using Finance Simplified, but they can also be used for financial fraud or sold to other cybercriminals.
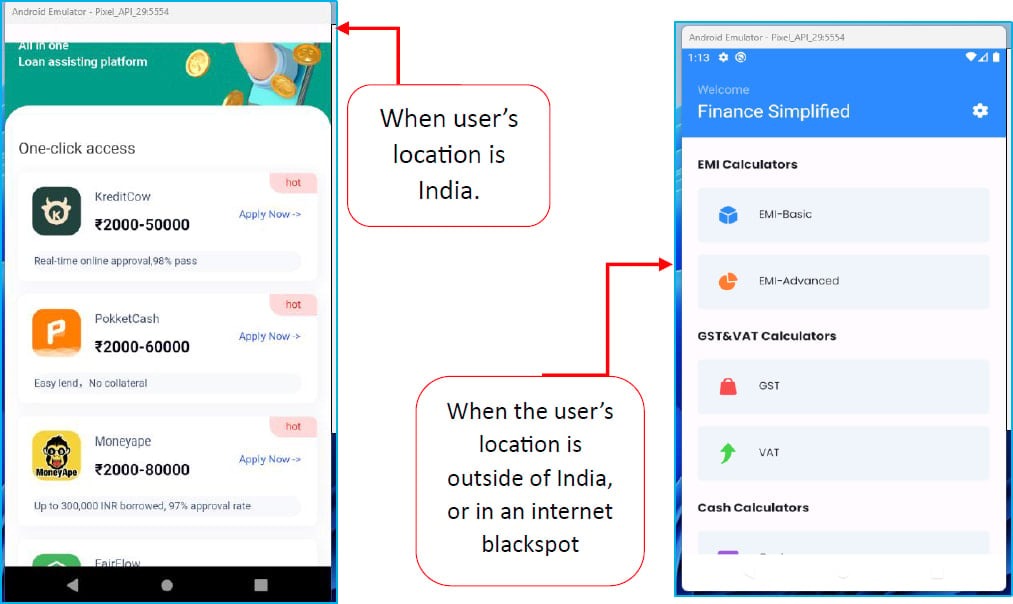
To avoid detection on Google Play, Finance Simplified used a WebView to redirect users to an external website where they downloaded the loan APK hosted on Amazon EC2. Interestingly, the additional APK was downloaded only if the user was located in India.