The attack occurred in early January 2025 and was quite sophisticated. For instance, the attackers possessed personal nonpublic information about their victims and used phishing links wrapped recursively in Postmark tracking links to conceal the final destination.
The obfuscation technique used in this attack was first described in October 2024 by well-known JavaScript developer Martin Kleppe involved with the JSFuck project.
The encoding employs two different Unicode filler characters, the Hangul half-width (U+FFA0) and the Hangul full width (U+3164), to represent the binary values 0 and 1, respectively. In the payload, each group of 8 such characters forms a single byte, representing an ASCII character.
The obfuscated code is stored as a property in a JavaScript object, and since the Hangul filler characters are rendered as empty spaces, the payload is invisible. Such attacks are difficult to detect because empty spaces reduce the chance that security scanners notice the threat.
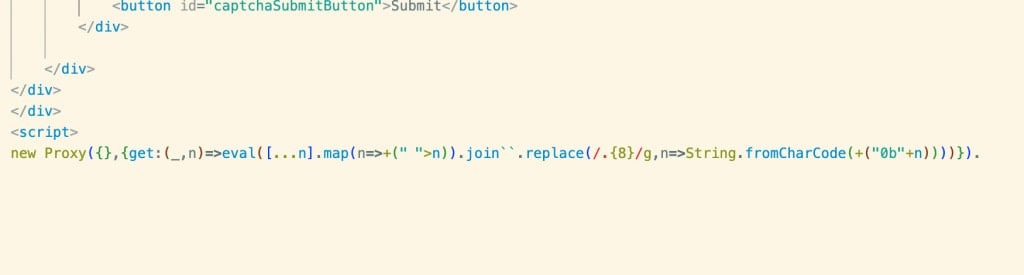
According to Juniper Threat Labs, the payload is executed with a short bootstrap code when the property is accessed through a Proxy get() trap: a Python function takes the Unicode string of Hangul filler characters and restores the original JavaScript code.
In addition, attackers employ other obfuscation techniques, including base64 encoding and anti-debugging, to evade analysis.

“The attacks were highly personalized, including non-public information, and the initial JavaScript would try to invoke a debugger breakpoint if it were being analyzed, detect a delay, and then abort the attack by redirecting to a benign website,” – Juniper Threat Labs.
Juniper Threat Labs reports that two domains used in this campaign were previously related to the Tycoon 2FA phishing kit. If so, the above-described obfuscation technique can quickly become commonly used by cybercriminals.
