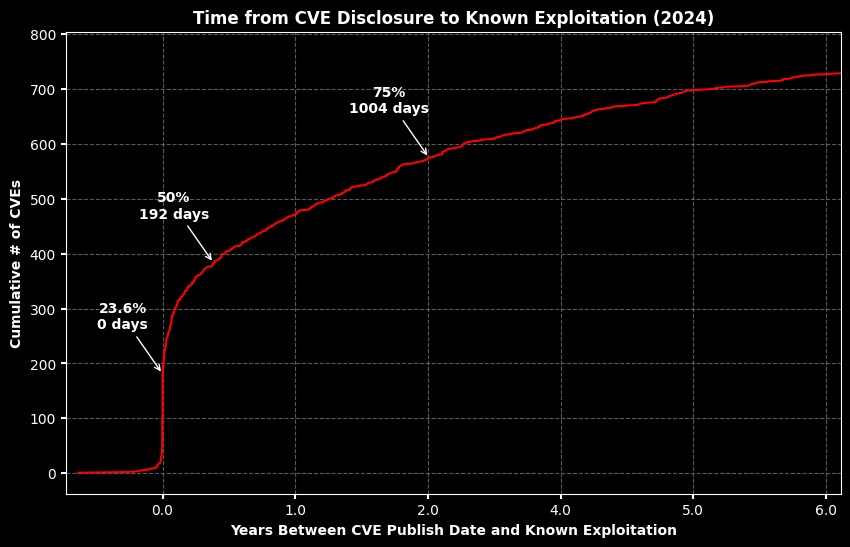
Interestingly, 23.6% of KEVs were exploited on the day their CVEs were publicly disclosed or even earlier.
This is somewhat less compared to 2023 (26.8%), and experts believe that exploitation attempts can occur throughout the entire vulnerability’s lifecycle despite all the hype around zero-day bugs.
“During 2024, 1% of the CVEs published were reported publicly as exploited in the wild, aligning closely with historical trends outlined in our State of Exploitation Report. This number is expected to grow as exploitation is often discovered long after a CVE is published,” – VulnCheck.
in November 2024, VulnCheck analysts had already warned that some 400,000 potentially vulnerable hosts could be affected by attacks exploiting just 15 vulnerabilities in products of such vendors as Apache, Atlassian, Barracuda, Citrix, Cisco, Fortinet, Microsoft, Progress, PaperCut, and Zoho.
VulnCheck’s recommendations to organizations exposed to such risks are as follows:
- evaluate their exposure to these technologies;
- enhance visibility into potential risks;
- leverage robust threat intelligence;
- maintain strong patch management practices; and
- implement mitigating controls (e.g. minimize internet-facing exposure of vulnerable devices wherever possible).
