The OttoKit plugin enables users to connect plugins and external tools (e.g. WooCommerce, Mailchimp, and Google Sheets), automate tasks (e.g. sending emails and adding users), or update CRMs without code.
Wordfence published details of the authentication bypass vulnerability in OttoKit at the end of last week. The bug identified as CVE-2025-3102 (CVSS score 8.1) affects all versions of SureTriggers/OttoKit up to 1.0.78.
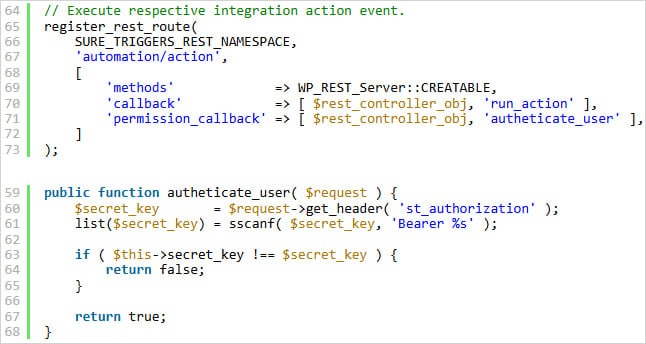
According to BleepingComputer, the vulnerability originates from a missing empty value check in the authenticate_user( function, which handles REST API authentication. Its exploitation becomes possible if the plugin isn’t configured with an API key, and the stored secret_key remains empty.
To exploit this bug, an attacker sends an empty st_authorization header to pass the check and gain unauthorized access to protected API endpoints. In fact, CVE-2025-3102 enables attackers to create new administrator accounts without authentication.
Experts urge users to upgrade to the latest version of OttoKit/SureTriggers (1.0.79) released in early April as soon as possible.
WordPress Patchstack analysts detected attacks exploiting CVE-2025-3102 as early as a few hours after its disclosure. According to experts, hackers exploiting this bug attempt to create new administrator accounts using random combinations of usernames, passwords, and email addresses (which indicates that such attacks are automated).
