This attack was first spotted by VX-underground specialists; this is a new variant of the ClickFix (ClearFake or OneDrive Pastejacking) attack vector. Various ClickFix modifications are pretty common nowadays. Typically, victims are tricked into visiting fraudulent websites and running malicious PowerShell commands, thus, manually infecting their systems with malware. For instance, malefactors require users to pass a fake CAPTCHA test or a verification procedure – allegedly, to solve display problems or join the channel.
Currently, the attackers are exploiting the recent news that US President Donald Trump has pardoned Ross Ulbricht, founder of the darknet marketplace Silk Road shut down in 2013.
Scammers use fake X (formerly Twitter) accounts to impersonate the Free Ross movement and direct users to supposedly official Ulbricht Telegram channels.
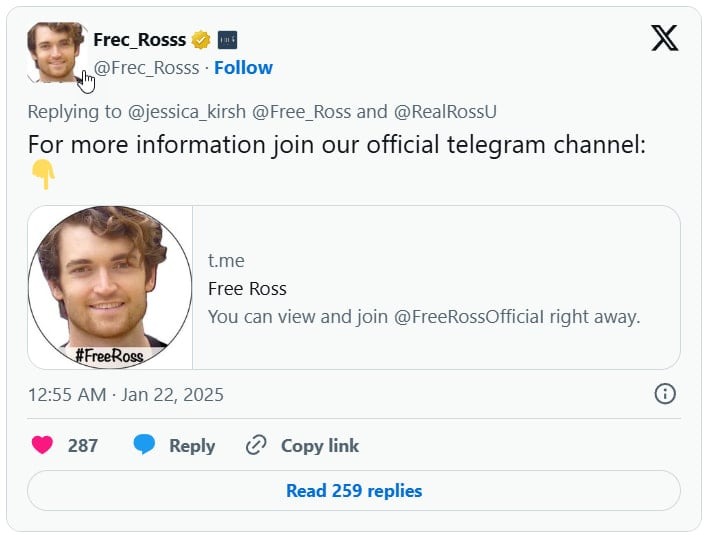
After clicking on such a link, victims are prompted to pass a verification test called Safeguard Captcha.
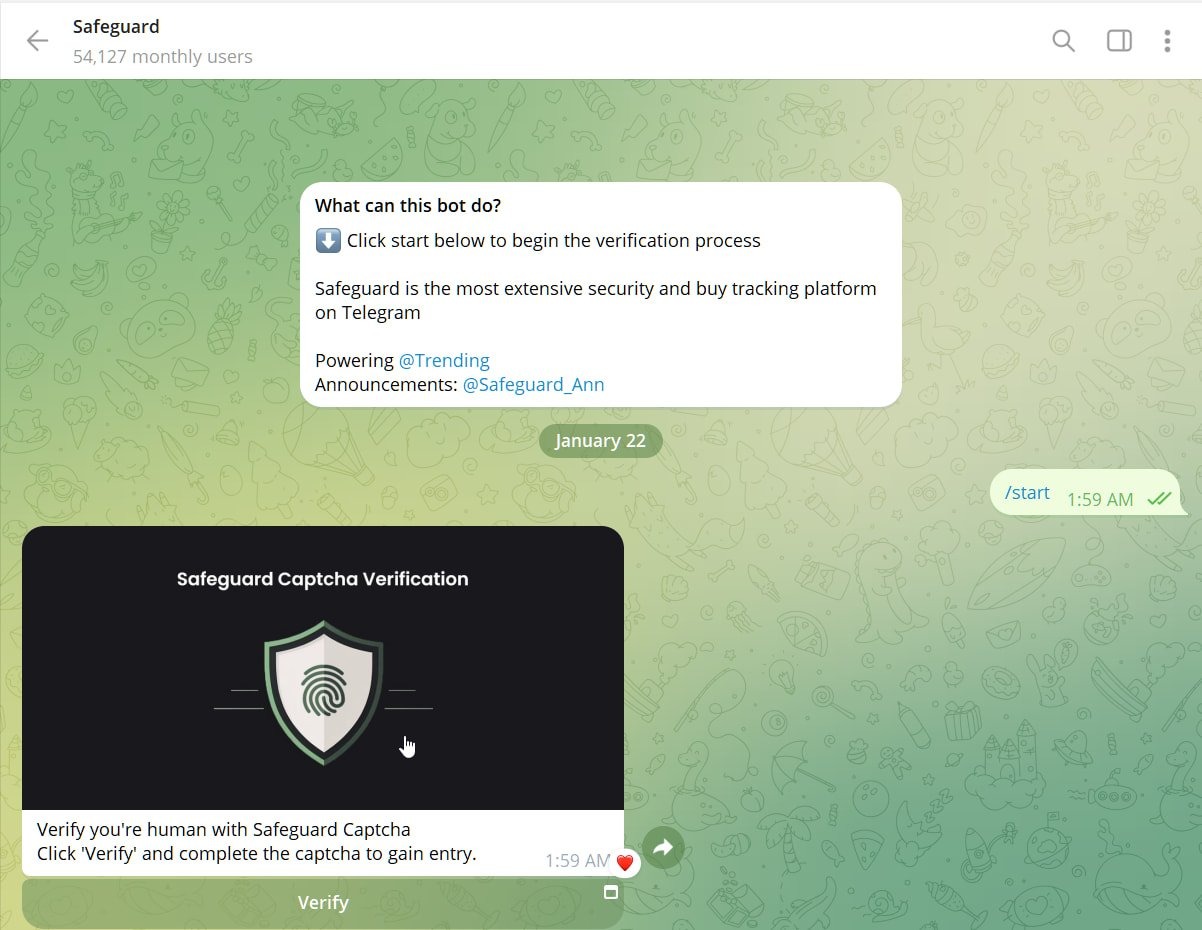
This Telegram app automatically copies a PowerShell command to the victim’s clipboard, and the user is prompted to open the Windows Run dialog and execute it to pass authentication.
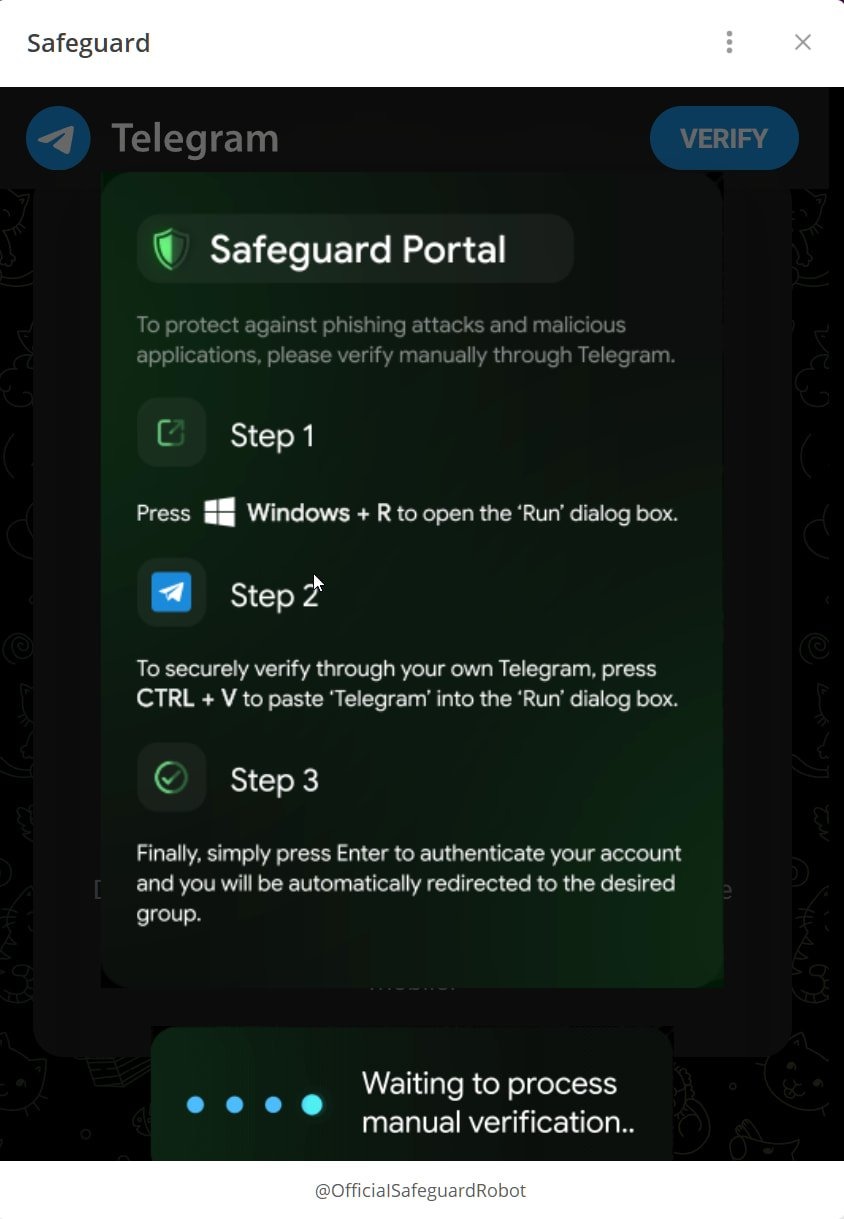
According to Bleeping Computer, the code from the clipboard downloads and executes a PowerShell script that, in turn, downloads a ZIP archive from the openline[.]cyou website. This archive contains multiple files, including identity-helper.exe, which, according to VirusTotal, is nothing else but the Cobalt Strike downloader.
Security experts remind that under no circumstances should you run commands copied from the Internet in the Windows Run dialog box or in the PowerShell terminal (especially if you have no idea of what’s going on); while any obfuscation should ring the alarm bell.
