In addition, most subscribers have already automated the certificate renewal procedure and don’t require special notifications.
“Providing expiration notification emails means that we have to retain millions of email addresses connected to issuance records. As an organization that values privacy, removing this requirement is important to us. Providing expiration notifications adds complexity to our infrastructure, which takes time and attention to manage and increases the likelihood of mistakes being made. Over the long term, particularly as we add support for new service components, we need to manage overall complexity by phasing out system components that can no longer be justified,” – Let’s Encrypt.
The organization recommends using Red Sift Certificates Lite to monitor certificate expiration dates; this service is free of charge for up to 250 certificates. Other monitoring options include Datadog SSL Monitoring and TrackSSL.
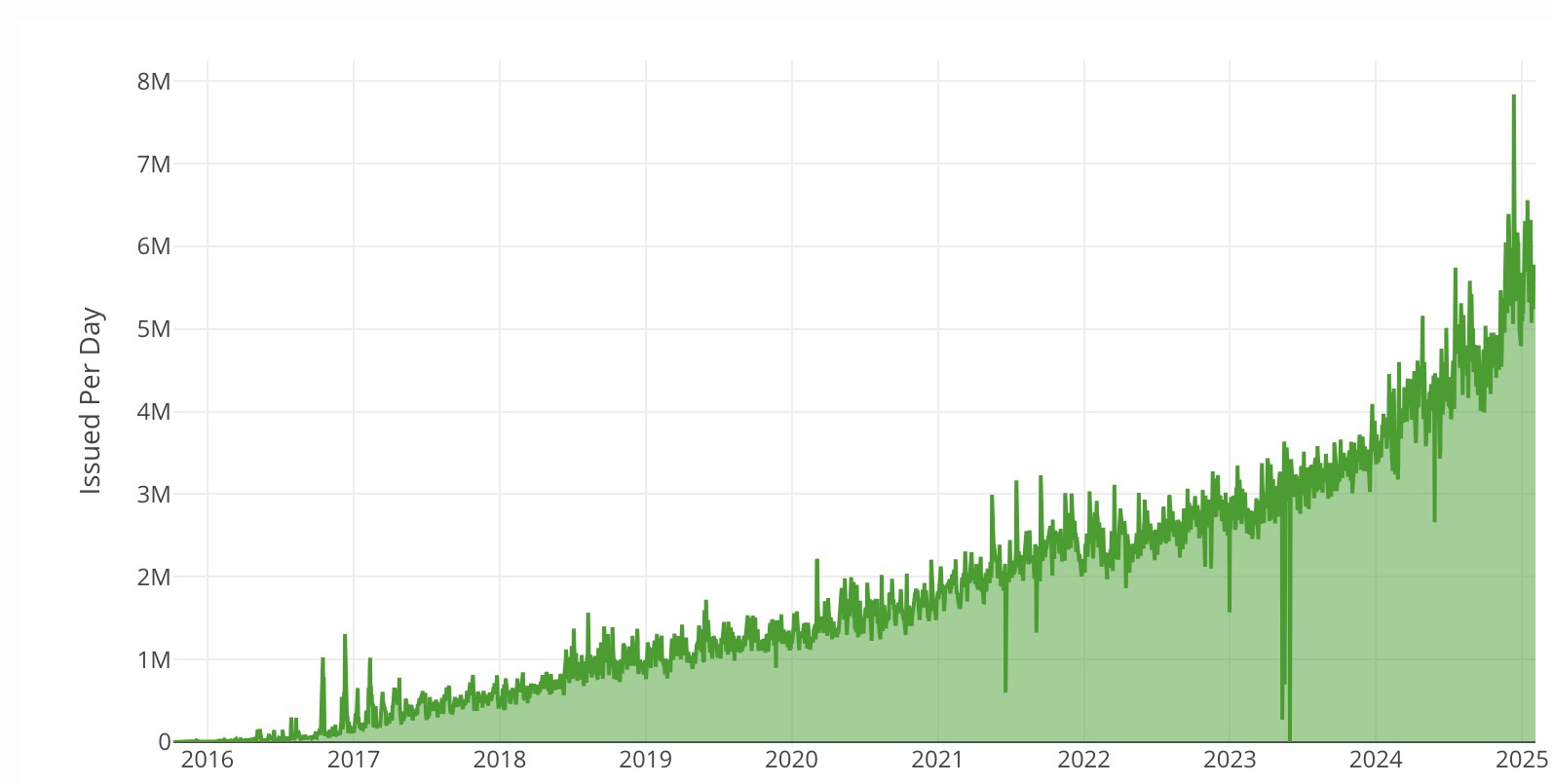
According to the official Let’s Encrypt statistics, some 8 million certificates were issued daily as of December 2024. The number of HTTPS-protected pages has been steadily growing and exceeded 82% in January 2025.