Kerio Control is a comprehensive network security solution used for VPN, bandwidth management, reporting, monitoring, traffic filtering, antivirus protection, and intrusion prevention.
The CVE-2024-52875 vulnerability was discovered in mid-December 2024 by independent researcher Egidio Romano who explained that this bug opens the way for severe one-click RCE attacks.
“User input passed to these pages via the “dest” GET parameter is not properly sanitized before being used to generate a “Location” HTTP header in a 302 HTTP response. Specifically, the application does not correctly filter/remove linefeed (LF) characters. As such, this can be exploited to perform both Open Redirect and HTTP Response Splitting attacks, which in turn might allow to carry out Reflected Cross-Site Scripting (XSS) and possibly other attacks,” – Egidio Romano.
Shortly after that, GFI Software released updates fixing the problem (version 9.4.5 Patch 1). But three weeks later, Censys experts warned that more than 23,800 Kerio Control instances remain vulnerable.
At the beginning of January 2025, Greynoise analysts recorded attempts to steal devices’ CSRF tokens using the PoC exploit created by Egidio Romano.
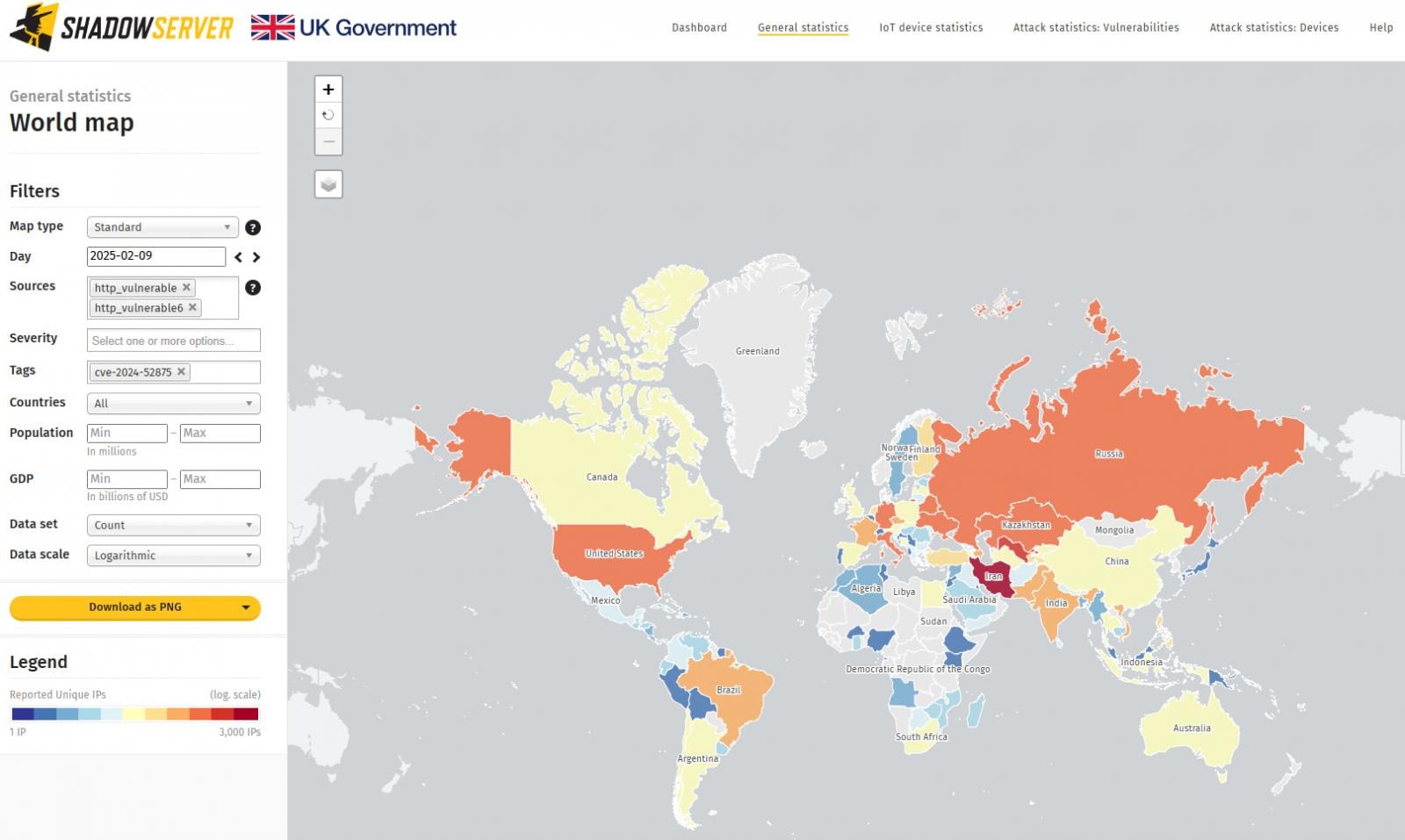
According to The Shadowserver Foundation, the situation has worsened in the past month: 12,229 Kerio Control firewalls are still vulnerable to CVE-2024-52875 attacks. Most of them are located in Iran, USA, Italy, Germany, Russia, Kazakhstan, Uzbekistan, France, Brazil, and India.
Security experts remind that a PoC exploit is available for the CVE-2024-52875 vulnerability, and its exploitation is fairly simple. In other words, even novice hackers can deliver CVE-2024-52875 attacks.
GFI Software strongly advises customers to install Kerio Control version 9.4.5 Patch 2 released on January 31, 2025 that contains additional security fixes.
