The AI-powered Enhanced Protection was first spotted back in November 2024; at that time, its description in Chrome Canary changed from “proactive protection” to “AI-powered protection”.
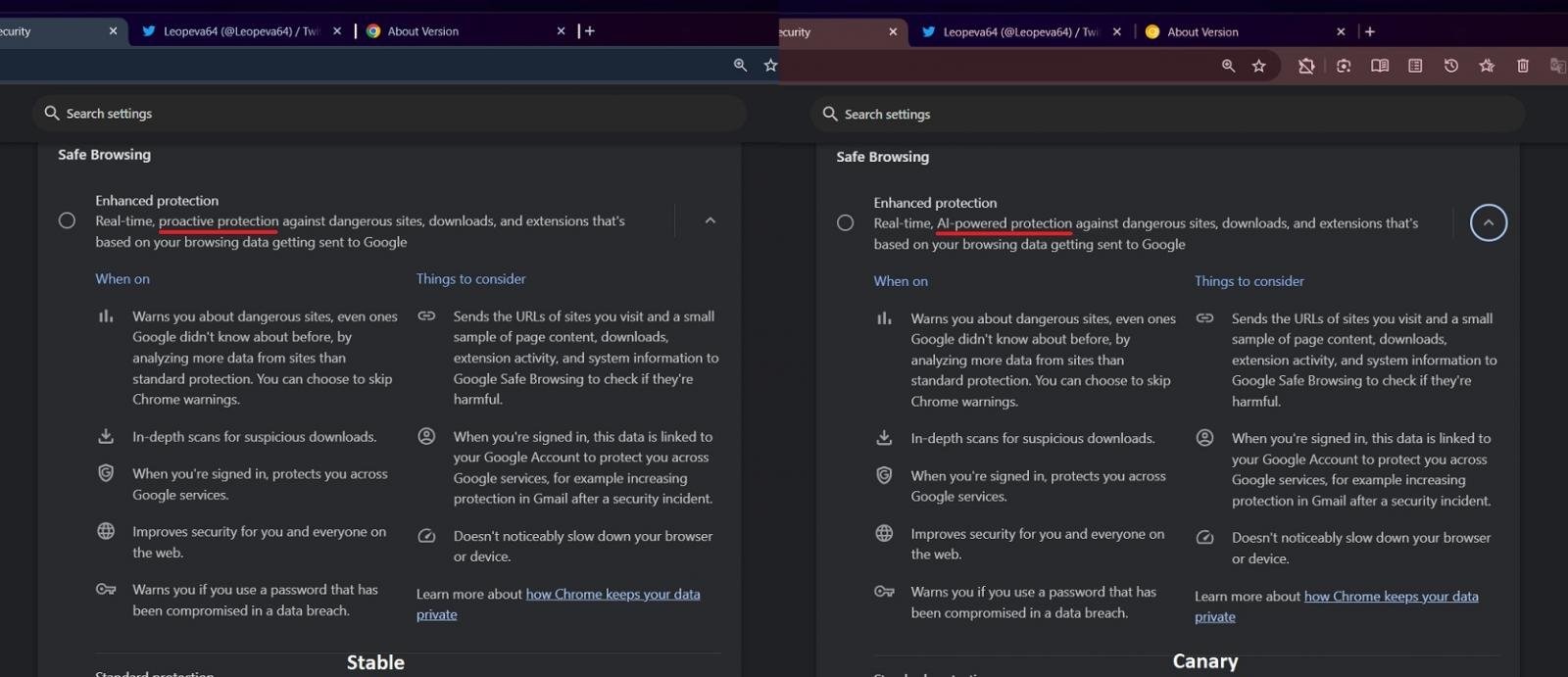
Now, after several months of testing, this update has been applied to the stable version of the browser on all platforms.
It’s not entirely clear though how the updated function differs from the old version without AI.
Last week, Google reported that Enhanced Protection employs AI to identify patterns in real time and notify users of potentially dangerous sites not detected by Google in the past. In addition, the AI performs deep scans of suspicious downloads.
“And now, more than 1 billion Chrome users are using this mode, making them two times as safe from phishing and other scams when compared to Safe Browsing’s Standard Protection mode,” – Google.
