Fraudsters are exploiting unsecured Milesight industrial routers to send out phishing SMS messages. Sekoia specialists discovered that such campaigns have been ongoing since 2023.
Routers from the Chinese company Milesight IoT Co., Ltd. are IoT devices that use cellular networks to connect traffic lights, electricity meters, and other remote industrial devices to central nodes. They are equipped with SIM cards that operate on 3G/4G/5G cellular networks and can be controlled via text messages, Python scripts, and web interfaces.
Sekoia researchers report that the analysis of “suspicious network traces” detected by the company’s honeypots led to the discovery of a cellular router being used to send SMS messages with phishing URLs.
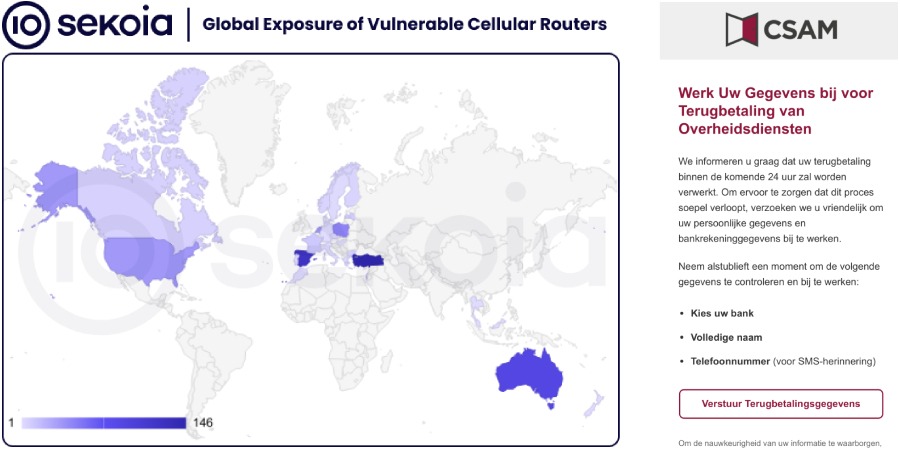
In the course of further investigation, the researchers found more than 18,000 such devices accessible over the internet. At least 572 of them provide unrestricted public access to their APIs. It is also noted that the vast majority of the discovered routers are running firmware that is more than three years out of date and contains known vulnerabilities.
Researchers report that they sent requests to unauthenticated APIs that returned the contents of routers’ incoming and outgoing SMS messages. Among these messages, they identified several malicious campaigns that have been ongoing since October 2023 and are linked to phishing.
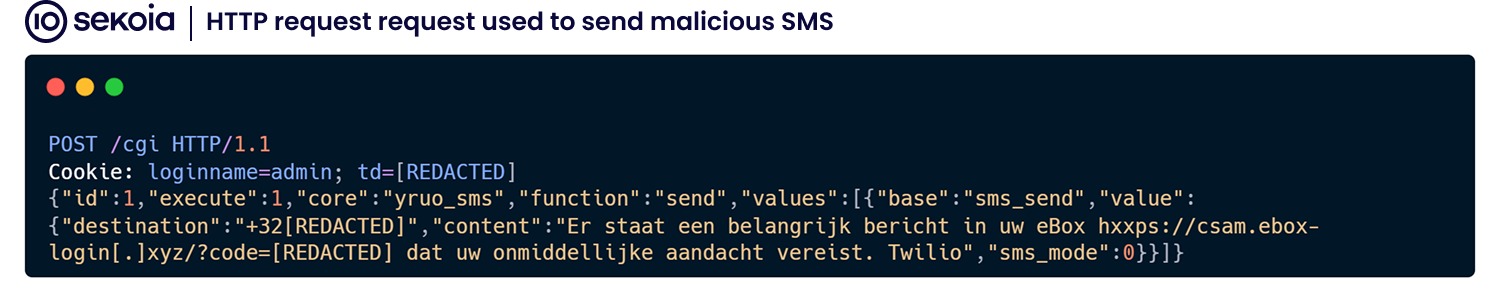
Fraudulent messages were sent to phone numbers in multiple countries, with Sweden, Belgium, and Italy hit the hardest. SMS recipients were asked to sign in to various accounts, often linked to government services, supposedly to “verify their identity.” The links in the messages led to phishing sites that harvested victims’ credentials.
The phishing sites used JavaScript that blocked the loading of malicious content if the page was opened on a non-mobile device. On one site, JavaScript was used to disable right-click and the browser’s debugging tools. This was presumably done to complicate analysis and reverse engineering.
Analysts also noticed that some sites were recording visitor activity via the GroozaBot Telegram bot. It is known that the bot is operated by a handler using the nickname Gro_oza, who speaks Arabic and French.
“In this case, the campaigns were carried out by exploiting vulnerable cellular routers — a relatively primitive but effective delivery channel,” the researchers write. “Such devices are especially attractive to attackers because they allow SMS to be sent in a decentralized manner across different countries, complicating both detection and blocking.”
Experts emphasize that attacks via Milesight routers demonstrate that large-scale phishing operations can be carried out even using simple and readily available infrastructure. Given the strategic value of such equipment, it is highly likely that similar devices are being exploited in other campaigns.
It is still unclear how attackers are compromising Milesight devices. One theory is the exploitation of the CVE-2023-43261 vulnerability, which was fixed in 2023 with the release of firmware version 35.3.0.7. Indeed, the vast majority of the identified devices were running 32-series firmware or earlier.
However, according to the researchers, this version does not align with a number of facts uncovered during the investigation. In particular, some of the compromised devices were running firmware that is not vulnerable to CVE-2023-43261.
