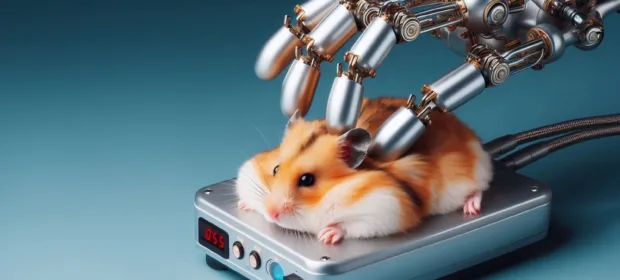
In this article, I’ll walk through how I explored the feasibility of automating the fast-rising game Hamster Kombat. Not every tactic I tried worked out, but you might still find the methods useful in other contexts.
CONTINUE READING 🡒 A Steam game stole money from hundreds of people. A…
Another malicious game has been discovered on Steam — BlockBlasters. Attention to the issue was drawn by the case of streamer Raivo Plavnieks, known as RastalandTV. He was trying to raise money for stage-four cancer treatment, but…
CONTINUE READING 🡒 QR Codes Demystified: How to Create a QR Code with…
QR codes are everywhere these days—major services like WhatsApp, Yandex, and AliExpress use them as an authentication method. But how secure is this approach? Is it possible to craft a QR code that, when scanned, delivers and…
CONTINUE READING 🡒 Scammers Are Creating Fake Websites While Impersonating the FBI
The FBI warned that attackers are spoofing the website of the Internet Crime Complaint Center (IC3) to commit financial fraud or steal visitors’ personal data.
CONTINUE READING 🡒 Cyberattack Disrupts Operations at Several European Airports
A cyberattack affected the operation of check-in systems at several European airports. Passengers faced dozens of canceled and delayed flights. The situation may deteriorate further at a minimum of one major airport.
CONTINUE READING 🡒 Crooked path. New obfuscation techniques for WinAPI calls
All malicious tools try to hide their WinAPI calls: if the program code contains suspicious functions, its execution can be blocked. There are very few documented ways to obfuscate WinAPI calls, but I would like to share with you some promising ideas…
CONTINUE READING 🡒 Canadian authorities announce the liquidation of the TradeOgre crypto exchange
The Royal Canadian Mounted Police (RCMP) has shut down the TradeOgre cryptocurrency exchange. It is reported that more than $40 million in cryptocurrency was seized, allegedly obtained through criminal activity.
CONTINUE READING 🡒 Choosing the Best PE Editor for Windows Executables: A Reverse…
The primary—and hardest—task for a hacker during a software break-in is to identify the protection mechanism and bypass it. For reconnaissance I typically use the WinDbg debugger, and for “patching” the application I rely on the Hiew…
CONTINUE READING 🡒 Researchers Forced ChatGPT to Solve CAPTCHAs
Experts at SPLX, a company specializing in automated security testing for AI solutions, demonstrated that prompt injections can be used to bypass the ChatGPT agent’s protections and force it to solve CAPTCHAs.
CONTINUE READING 🡒 PyPI revokes tokens stolen in the GhostAction attack
The Python Software Foundation team reported that it has revoked all PyPI tokens stolen during the GhostAction supply chain attack that occurred in early September. The specialists emphasized that the attackers did not use the tokens to…
CONTINUE READING 🡒 A Practical Guide to Stable Diffusion XL: Choosing Models, Refiners,…
If you decide to run generative image models on your own machine, you’ll quickly hit a tough choice: there are many of them, and while their outputs are similar, they’re all a bit different. In this article,…
CONTINUE READING 🡒 Beyond the App Store: Installing Third-Party Apps on iOS Without…
Apple tightly controls what users can and can’t do with their devices. On iOS and iPadOS, that control borders on the absurd, to the point where a device’s rightful owner can’t freely install apps. In this article,…
CONTINUE READING 🡒 SI473X SDR Hacks: Building a DIY Receiver and Uncovering Hidden…
Today I’ll walk through how modern broadcast receivers are put together, using the SI473x family—single‑chip SDR receivers—as an example. Along the way, we’ll write our own library to drive these chips. You might ask, why build yet…
CONTINUE READING 🡒 MITRE ATT&CK Matrix: How the Threat Description Language Works and…
MITRE ATT&CK is one of the most widely used frameworks among cybersecurity professionals. In this article, we’ll cover how the knowledge base was created and how it’s structured—how it’s used to describe malware capabilities, profile APT groups,…
CONTINUE READING 🡒 Sailfish OS: A De-Googled, Privacy-Focused Android Alternative for Your Smartphone
Android has dominated the mobile OS market for years, leaving iOS as the only other major player. What about alternatives? In this article, we’ll look at one: Sailfish OS, the mobile operating system from the Finnish company…
CONTINUE READING 🡒 SonicWall data breach: company urges customers to change passwords immediately
SonicWall has warned customers to change their credentials as soon as possible. The reason is that a cyberattack affecting MySonicWall accounts resulted in the compromise of firewall configuration backup files.
CONTINUE READING 🡒 SystemBC malware turns vulnerable VPS into proxies
Experts at Lumen Technologies warned that operators of the SystemBC botnet are hunting for vulnerable VPS instances and turning them into proxies. Roughly 1,500 bots are active within SystemBC each day, providing criminals with a channel for…
CONTINUE READING 🡒 Google patches a Chrome zero-day; the vulnerability is already being…
Google has released updates for Chrome to address four vulnerabilities. According to the company, one of them (CVE-2025-10585) has already been exploited by attackers.
CONTINUE READING 🡒 Silent call. Concealing NTAPI calls from security tools
Since recently, EDR systems have been increasingly frequently using call stack tracing to detect malicious applications and envenom red teamer’s lives. Let’s analyze this powerful technique and find a way to fool EDR and call NTAPI covertly — so that even stack unwinding won’t…
CONTINUE READING 🡒 Building a Custom Android Dialer: Low‑Level Call Control with the…
Android provides a software interface to the phone’s low-level hardware stack. Using it, you can write an app to dial numbers, trigger the transmission of the current coordinates, handle an incoming call, or even silently switch on…
CONTINUE READING 🡒