Kaspersky Lab experts have discovered a new wave of attacks by the RevengeHotels group. A distinctive feature of this campaign is that many of the new malware samples were created using AI.
CONTINUE READING 🡒 Former FinWise Bank employee gained access to data on 689,000…
The American bank FinWise has warned, on behalf of a partner company, that it suffered a data breach. It is reported that last year a former employee of the financial institution gained access to confidential data even…
CONTINUE READING 🡒 De-Googling Android: Using Android Without Google Play, YouTube, or Google…
Google collects a ton of data from your smartphone—location, app activity, contacts, calendar, search history, app-data backups—just to name a few. You don’t strictly have to link your phone to a Google account, but if you don’t,…
CONTINUE READING 🡒 BreachForums admin resentenced: Pompompurin gets three years in prison
The former administrator of the hacker forum BreachForums, 22-year-old Conor Brian FitzPatrick (Conor Brian FitzPatrick), also known as Pompompurin, has been sentenced to three years in prison. A federal appeals court overturned the earlier sentence handed down…
CONTINUE READING 🡒 224 Google Play apps used for ad fraud
Google Play removed 224 malicious applications that were linked to the SlopAds ad fraud scheme and were generating 2.3 billion ad requests per day.
CONTINUE READING 🡒 Microsoft and Cloudflare Took Down the RaccoonO365 Phishing Service
Microsoft and Cloudflare announced the takedown of the RaccoonO365 Phishing-as-a-Service (PhaaS) operation, which was used to steal thousands of Microsoft 365 credentials.
CONTINUE READING 🡒 Which Operating System Is Most Vulnerable? Security Comparison of iOS,…
We often write about mobile OS security—publishing details on newly discovered vulnerabilities, outlining defensive weak spots, and explaining methods of compromise. We’ve covered surveillance of Android users, malicious apps baked right into firmware, and the uncontrolled exfiltration…
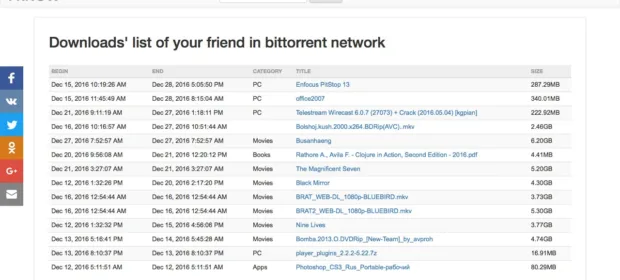
CONTINUE READING 🡒 I Know What You Downloaded: A Website That Tracks Who…
The site’s name translates to “I Know What You Downloaded.” Its creators built a system that monitors public torrents to log lists of files downloaded via BitTorrent and the IP addresses of peers. If you download torrents…
CONTINUE READING 🡒 Jaguar Land Rover has still not resumed production following a…
The automaker Jaguar Land Rover (JLR) still hasn’t recovered from the ransomware attack that occurred in early September. The company is losing £5–10 million per day (₽574,000,000–1,148,000,000). This incident is becoming one of the largest cyberattacks in…
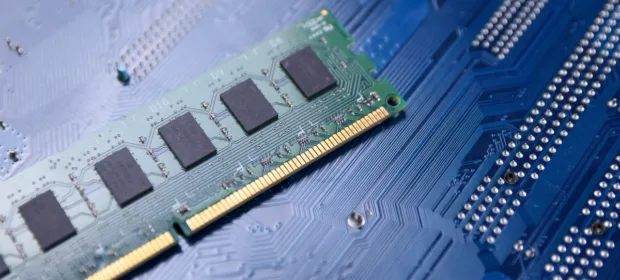
CONTINUE READING 🡒 Phoenix Attack Bypasses DDR5 Protections Against Rowhammer
A new Rowhammer attack variant has been developed that can bypass the latest protection mechanisms in SK Hynix DDR5 chips. The attack, dubbed Phoenix, can obtain root privileges on DDR5-based systems in under two minutes.
CONTINUE READING 🡒 IMSI-Catchers Explained: Mobile Network Interception FAQ, Detection, and Protection
By now, everyone knows public Wi‑Fi hotspots aren’t safe. That doesn’t stop everyday users from relying on them—often without any VPN—even though VPN features are built into many security suites these days. A long‑standing “safer” alternative has…
CONTINUE READING 🡒 Self-propagating malware infected more than 180 npm packages
Researchers discovered that more than 180 npm packages had been compromised and infected with self-propagating malware aimed at infecting other packages. The campaign, dubbed Shai-Hulud, likely began with the compromise of the @ctrl/tinycolor package, which is downloaded…
CONTINUE READING 🡒 Samsung patches a 0‑day exploited in attacks against Android users
Samsung has patched a zero-day RCE vulnerability that was already being exploited in attacks against devices running Android.
CONTINUE READING 🡒 Reverse Engineering Fundamentals: Hands-On Executable Analysis in IDA Pro
In this article, we’ll dive into an in-depth static analysis using IDA Pro—the go-to disassembler for hackers and security professionals. We’ll start with the basics and steadily work our way forward, cutting through the thicket of code…
CONTINUE READING 🡒 Pirate sentenced to four years in prison for distributing unreleased…
The U.S. Department of Justice reported that a former employee of an unnamed multinational company, Steven Hale, was sentenced to four years in prison for stealing hundreds of DVD and Blu-ray discs containing unreleased films and posting…
CONTINUE READING 🡒 WhiteCobra group creates VSCode extensions that steal cryptocurrency
According to analysts at Koi Security, the WhiteCobra hacking group has targeted users of VSCode, Cursor, and Windsurf by publishing 24 malicious extensions in the Visual Studio Marketplace and the Open VSX Registry. The campaign remains active,…
CONTINUE READING 🡒 Apple Warns French Users About Spyware Attacks
CERT-FR reported that at the end of last week Apple warned users that their devices had become the target of attacks using spyware.
CONTINUE READING 🡒 TrueNAS CORE vs TrueNAS SCALE vs OpenMediaVault: Choosing the Right…
Despite the abundance of off‑the‑shelf NAS devices from major vendors, the urge to build and tune your own NAS shows no sign of fading. The options are dizzying: TrueNAS Core, TrueNAS Scale, openmediavault, specialized setups with Unraid…
CONTINUE READING 🡒 600 GB of source code and documents linked to the…
Researchers from the Great Firewall Report team report that the largest data leak in the entire history of the “Golden Shield,” also known as the “Great Firewall of China,” has occurred.
CONTINUE READING 🡒 Hackers set up a fake account on Google’s law enforcement…
Google representatives said that hackers created a fake account in the Law Enforcement Request System (LERS). This company platform is used by law enforcement agencies to submit official data requests.
CONTINUE READING 🡒