Google representatives said that hackers created a fake account in the Law Enforcement Request System (LERS). This company platform is used by law enforcement agencies to submit official data requests.
CONTINUE READING 🡒 WebSDR: A Browser-Based Gateway to Software-Defined Radio (SDR)
They say that once you dip your toes into SDR (software-defined radio), you fall down the rabbit hole—buying all sorts of gear and tinkering with it. If that warning doesn’t scare you off, the WebSDR site is…
CONTINUE READING 🡒 Vendor spent a year fixing a flaw that allowed unlimited…
Security researchers from SEC Consult, part of Eviden, reported that the payments company KioSoft spent more than a year fixing a serious vulnerability affecting some of its NFC cards.
CONTINUE READING 🡒 10 Facts You Didn’t Know About the Python Programming Language
Python is a programming language with a relatively low barrier to entry, which is why many beginners choose it. Still on the fence about learning Python? Here are ten facts that can help you put your doubts…
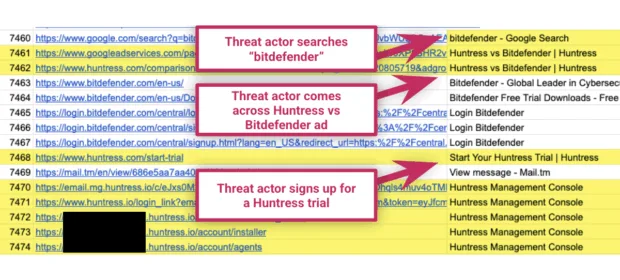
CONTINUE READING 🡒 Huntress researchers tracked a hacker who installed their product
Last week, the cybersecurity company Huntress published research based on the fact that an attacker had installed a trial version of its product. However, the company ended up facing criticism, as many raised concerns about the extent…
CONTINUE READING 🡒 HybridPetya ransomware can bypass UEFI Secure Boot
ESET specialists discovered a new piece of ransomware, HybridPetya, which can bypass UEFI Secure Boot protection to install a malicious application in the EFI system partition. It is believed that HybridPetya was inspired by the destructive Petya/NotPetya…
CONTINUE READING 🡒 Using Open vSwitch to Segment and Isolate VMs with VLANs
Virtualization has long been a staple of nearly every enterprise infrastructure. Any admin has either used a hypervisor or at least experimented with one. We’ve already covered how to deploy a virtualization host, so today we’ll focus…
CONTINUE READING 🡒 Spy among penguins. Writing a custom Linux rootkit
Linux rootkits have been known for quite some time; they feature highly sophisticated architecture, can effectively intercept system calls, and disguise their presence in the system. Today you will learn how to write your own Linux rootkits and get an understanding of key…
CONTINUE READING 🡒 5 Essential OSINT Tools: Building a Network Reconnaissance Toolkit
OSINT (open-source intelligence) can be incredibly useful, especially during incident investigations. Most people know the theory—what to look for and where—but in practice the data sets are so large that going through them by hand is impossible,…
CONTINUE READING 🡒 Windows Malware 101: Creating a Simple Proof-of-Concept in Assembly
Building viruses is a great reason to learn assembly. And while you can technically write a virus in C, that feels un-hacker-like and just plain wrong. The text that follows is a piece by Chris Kaspersky that…
CONTINUE READING 🡒 Python Generators and Iterators: How They Work and When to…
These days, data is steadily becoming the “new oil” in terms of value. The catch is that the volumes we have to process are growing by the hour. Plenty of it won’t fit on a hard drive…
CONTINUE READING 🡒 8 Practical Ways to Use Android’s Fingerprint Scanner for Security…
Official fingerprint reader support arrived in Android 6.0, yet many people still think it’s only for unlocking the phone. In fact, if you know your way around Tasker, you can map it to virtually any action.
CONTINUE READING 🡒 Critical Chrome Vulnerability Earned Researcher $43,000
Google has patched a critical use-after-free vulnerability in the Chrome browser that could lead to code execution. The security researcher who discovered it received a $43,000 reward under the bug bounty program.
CONTINUE READING 🡒 GhostAction attack exposed 3,325 secrets
Another supply chain attack has been discovered, dubbed GhostAction. The malicious campaign targeted GitHub and resulted in the compromise of 3,325 secrets, including PyPI, npm, DockerHub, and GitHub tokens, as well as Cloudflare and AWS API keys.
CONTINUE READING 🡒 U.S. Leads the Global Spyware Investment Market
According to an Atlantic Council study, the spyware industry is booming as investors increasingly turn their attention to this ethically questionable yet highly profitable field. Most of the funding goes to companies in the United States and…
CONTINUE READING 🡒 Deploying Snort IDS and Writing Intrusion Detection Rules
Attackers can compromise even the most hardened systems, and administrators may go months without noticing an intruder who has gained a foothold and is exfiltrating data. To prevent this and detect attacks, there are intrusion detection systems…
CONTINUE READING 🡒 DDoS protection company hit by a 1.5 billion packets-per-second attack
An unnamed European company specializing in DDoS protection became the victim of such an attack itself, with a peak rate of 1.5 billion packets per second (PPS). Experts from FastNetMon, who handled the mitigation, reported that the…
CONTINUE READING 🡒 More than 600 domains distributing the DeliveryRAT Android Trojan have…
Experts from F6 and RuStore report that they have discovered and blocked 604 domains that were part of the hackers’ infrastructure used to infect mobile devices with the DeliveryRAT trojan. The malware disguised itself as popular food…
CONTINUE READING 🡒 Pixel Camera and Google Photos to get deepfake detection tools
Google announced that it is integrating C2PA Content Credentials technology into the Pixel 10 camera app and Google Photos, so users can distinguish authentic images from those created or edited using artificial intelligence.
CONTINUE READING 🡒 Total Commander Reverse Engineering: Bypassing Protection in All Versions
Total Commander (formerly Windows Commander) is a popular graphical file manager for Windows. You can find plenty of methods to crack it on warez sites. Their perennial downside is how kludgy they are: every time a new…
CONTINUE READING 🡒