Operators of the Medusa ransomware offered a large sum of money to a BBC employee and wanted to use them as an insider for a cyberattack on the media company.
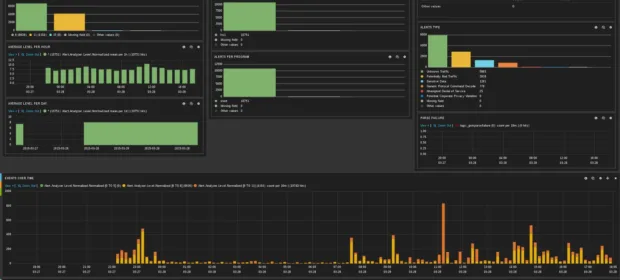
CONTINUE READING 🡒 Building an Open-Source SIEM for Log Analysis: Tools, Architecture, and…
Even a small organization can have a variety of security tools, and their log formats can differ significantly, complicating operations. In this article, I’ll show how to use free and open-source software to structure and normalize logs…
CONTINUE READING 🡒 Akira ransomware hacks SonicWall SSL VPN and bypasses multi-factor authentication
Arctic Wolf experts warn that Akira ransomware attacks on SonicWall SSL VPN devices continue to evolve. Hackers are successfully logging into accounts even with multi-factor authentication (MFA) enabled using one-time passwords (OTP). It is believed that the…
CONTINUE READING 🡒 Microsoft Edge to block third-party malicious extensions
Microsoft specialists announced that they are preparing a new security feature for the Edge browser that will block malicious extensions installed outside the official store.
CONTINUE READING 🡒 Hackers are already exploiting a new 0‑day in GoAnywhere MFT
Experts warn that hackers are actively exploiting the critical CVE-2025-10035 vulnerability in Fortra’s GoAnywhere MFT, disclosed earlier this month. The bug allows remote command execution without authentication.
CONTINUE READING 🡒 Passive Reconnaissance: OSINT Tools and Techniques for Stealthy Information Gathering
The success of a penetration test largely depends on how well you profile the target. What services and software does it use? Which ports and protocols are exposed? Who does it communicate with, and through what channels?…
CONTINUE READING 🡒 Raspberry Pi 500+ unveiled: 16 GB RAM and an SSD…
A few years ago, the Raspberry Pi 500 (and 400) were created for people who use Raspberry Pi as a general-purpose computer rather than a hobby device. Now the developers are taking that concept further with the…
CONTINUE READING 🡒 New version of the XCSSET macOS malware discovered, targeting Xcode…
Microsoft Threat Intelligence researchers have discovered a new variant of the XCSSET malware for macOS. The new version monitors the system clipboard to intercept cryptocurrency transactions and achieves persistence using a new method.
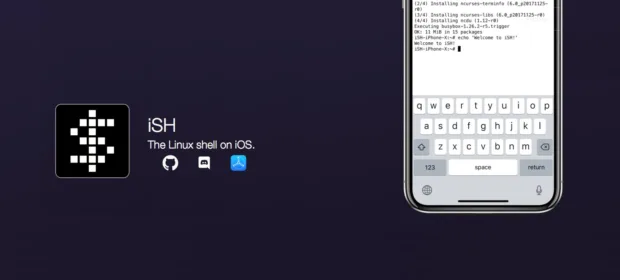
CONTINUE READING 🡒 iSH: A Pocket Linux Environment for iOS
Apple’s restrictions on iOS and its apps haven’t stopped people from trying all sorts of things with the system. iSH is one of the latest attempts to shoehorn a Linux shell onto the platform, and it runs…
CONTINUE READING 🡒 InstallShield from the inside. Examining installer’s virtual machine in x64dbg
This article discusses the InstallShield virtual machine and its operation in dynamics. To dissect InstallShield, I’m going to use my favorite debugger x64dbg; the installer embedded into a technical application will be used as an example.
CONTINUE READING 🡒 Open Redirect Vulnerability: How Attackers Exploit It for Phishing and…
Open Redirect vulnerabilities let attackers send users to a phishing site or trick them into downloading a rootkit disguised as legitimate software. Despite how serious these flaws are, even Google is in no rush to patch them.…
CONTINUE READING 🡒 Building an ESP32 Packet Sniffer: Wi‑Fi Packet Capture and Bluetooth/BLE…
It all started when we kicked off a bug and vulnerability hunting project at GS-Labs. The target hardware was quirky—no way to get root, and no trusty Ethernet either. And hackers, as you know, hate flying blind.…
CONTINUE READING 🡒 Linux Hardening: Essential Tools for Comprehensive Security Auditing
In this article, we’ll explore the key utilities for Linux hardening—tools for assessing a Linux system’s security posture and validating configurations from an information security perspective. We’ll not only review the tools but also provide practical examples…
CONTINUE READING 🡒 How to Build an Unconventional Raspberry Pi Media Center: A…
In the six years since the Raspberry Pi appeared, countless guides have shown how to turn it into a home media center. The problem is, the classic media-center setup on a Pi is so underwhelming it loses…
CONTINUE READING 🡒 Hackers attacked tech and legal organizations in the US using…
Google researchers report that suspected Chinese hackers used the Brickstorm malware in espionage operations targeting U.S. organizations in the technology and legal sectors. The attackers remained hidden in the compromised companies’ networks for about 400 days.
CONTINUE READING 🡒 PyPI users warned again about phishing attacks
The Python Software Foundation team is once again warning developers who use the Python Package Index (PyPI) about a phishing campaign. The attackers are using domain spoofing to harvest credentials.
CONTINUE READING 🡒 Two malicious packages found on Crates.io, the Rust repository
Two malicious packages, totaling about 8,500 downloads, have been discovered in the official Rust repository. The malware scanned developers’ systems to steal private cryptocurrency keys and other secrets.
CONTINUE READING 🡒 Computer Vision Explained: Core Algorithms Every Data Scientist Should Know
Computer vision is the field that tackles problems involving the analysis of images and video. At their core, these tasks all boil down to answering the question: what’s in the picture? Despite its apparent simplicity, that question…
CONTINUE READING 🡒 A zero-day vulnerability threatens two million Cisco devices, and hackers…
Numerous Cisco devices are vulnerable to an actively exploited zero-day vulnerability (CVE-2025-20352) in IOS and IOS XE. The issue allows attackers to remotely trigger a denial-of-service condition or execute code on vulnerable devices.
CONTINUE READING 🡒 ShadowV2 botnet uses misconfigured Docker containers for DDoS attacks
Darktrace researchers have discovered a new DDoS botnet that infects misconfigured Docker containers and then sells access to customers so they can launch attacks themselves.
CONTINUE READING 🡒