This week, Microsoft released the September updates, which addressed 81 vulnerabilities across the company’s products. Among them were two zero-day vulnerabilities whose details were disclosed before the patches were released.
CONTINUE READING 🡒 Apple introduces iPhone memory protection to combat sophisticated attacks
This week, Apple introduced the iPhone 17 and iPhone Air, which will be equipped with a new memory protection feature designed to keep devices safe against sophisticated spyware attacks.
CONTINUE READING 🡒 Getting Started with VR: A Comprehensive Guide to Virtual Reality…
Public interest in VR waxes and wanes, but the tech keeps getting better. If you’re thinking about picking up a VR headset, this guide is for you: we’ll break down the strengths of what’s on the market…
CONTINUE READING 🡒 The largest supply-chain attack in history netted the hackers less…
The largest attack in the history of the npm ecosystem affected about 10% of cloud environments. However, experts concluded that the attackers made practically nothing from this breach.
CONTINUE READING 🡒 Pirate revenues are falling, and movie descriptions are hidden in…
Experts at F6 reported that in the first half of 2025, revenues of illegal video content distributors fell by 14.5% compared to last year (to $16.6 million) and by 26.5% compared to the same period in 2023.…
CONTINUE READING 🡒 Ghidra vs IDA Pro: What the NSA’s Free Reverse Engineering…
In March 2019, the U.S. National Security Agency (NSA) released a reverse‑engineering toolkit called Ghidra. I’d first come across the name a couple of years earlier in WikiLeaks leaks and was very curious about what the NSA…
CONTINUE READING 🡒 Former WhatsApp Employee: 1,500 Engineers Had Access to Users’ Personal…
Attaullah Baig, who allegedly headed WhatsApp’s security department from 2021 to 2025, has filed a lawsuit against parent company Meta (an organization recognized as extremist and banned in the Russian Federation). Baig claims he was fired for…
CONTINUE READING 🡒 Adobe Commerce and Magento Vulnerability Enables Account Takeover
Adobe has disclosed a critical bug (CVE-2025-54236) that affects the Commerce and Magento platforms. Researchers have dubbed this vulnerability SessionReaper and describe it as one of the most serious in the entire history of these products.
CONTINUE READING 🡒 Android Performance Optimization: Eliminate App Lag, Jank, and Long Loading…
Performance is one of the most critical aspects of a mobile app. Your app can be as feature-rich, polished, and useful as you like, but if it feels sluggish, failure is almost guaranteed. The good news is…
CONTINUE READING 🡒 Plex urges users to reset passwords due to a data…
The streaming multimedia platform Plex is warning customers that they need to change their passwords immediately. The company suffered a data breach during which an attacker managed to steal users’ authentication data from the database.
CONTINUE READING 🡒 Enthusiasts launch the Darwin Awards for AI
Nominations are now open for the Darwin Awards in artificial intelligence (AI Darwin Awards). The creators of the award aim not to mock AI itself, but the consequences of using it without due caution and attention.
CONTINUE READING 🡒 Gridcoin: Earn Cryptocurrency Rewards for Scientific Computing
While some people mine crypto, others crunch scientific data. Until recently, you had to choose between profit and altruism, since most distributed computing projects don’t offer payouts. Now there’s a third‑party rewards program, and it’s already showing…
CONTINUE READING 🡒 12 misissued certificates were issued for Cloudflare’s 1.1.1.1 DNS service
Last week it emerged that the little-known certificate authority Fina issued 12 unauthorized TLS certificates for 1.1.1.1 (Cloudflare’s popular DNS service) from February 2024 to August 2025, without the company’s permission. The certificates could have been used…
CONTINUE READING 🡒 The s1ngularity attack affected 2,180 GitHub accounts
According to specialists at Wiz, who examined the recent s1ngularity attack targeting NX, the incident had far-reaching consequences. The breach of NX led to the exposure of data from 2,180 accounts and affected 7,200 repositories.
CONTINUE READING 🡒 EU fines Google $3.5 billion for advertising market abuses
The European Commission has fined Google €2.95 billion ($3.5 billion) for abusing its dominant position in the digital advertising technology market and favoring its own adtech services over competitors.
CONTINUE READING 🡒 How to Install VirtualBox on Tails OS and Route VM…
Tails is the best operating system if your goal is to maximize your anonymity online. But it has a few quirks, and one of them is that you can’t properly install VirtualBox using the standard tools. We’ll…
CONTINUE READING 🡒 npm packages with over 2.6 billion weekly downloads have been…
Researchers warn of the largest supply chain attack in history. Attackers injected malware into hugely popular npm packages, with more than 2.6 billion weekly downloads (including JavaScript libraries like chalk and strip-ansi). To carry out this attack,…
CONTINUE READING 🡒 iCloud Calendar used to send phishing emails from Apple servers
iCloud Calendar invitations are being used to send phishing emails, disguised as purchase notifications, directly from Apple’s mail servers. This tactic increases the likelihood of bypassing spam filters.
CONTINUE READING 🡒 DIY USB HID Attack Device: Building and Programming a BadUSB…
USB’s versatility creates a broad attack surface: researchers at Ben-Gurion University have identified nearly three dozen ways to weaponize USB. In this article, we’ll examine one of the most effective approaches—automating keystroke injection using a DIY HID-class…
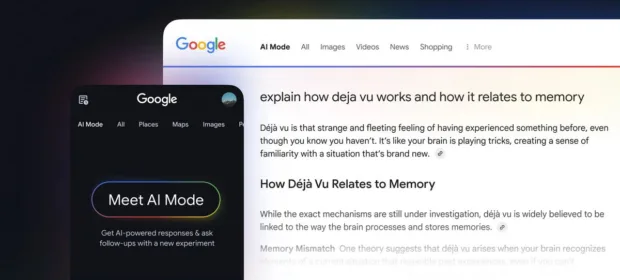
CONTINUE READING 🡒 Google may enable AI mode in Search by default
Google plans to make it easier for users to access AI mode by allowing them to set it as the default in Search (instead of traditional links).
CONTINUE READING 🡒