iCloud Calendar invitations are being used to send phishing emails, disguised as purchase notifications, directly from Apple’s mail servers. This tactic increases the likelihood of bypassing spam filters.
Reporters at Bleeping Computer report that earlier this month a reader shared a malicious email that masqueraded as a $599 payment receipt, supposedly charged to his PayPal account. The email included a phone number in case the recipient wanted to dispute the charge or make changes.
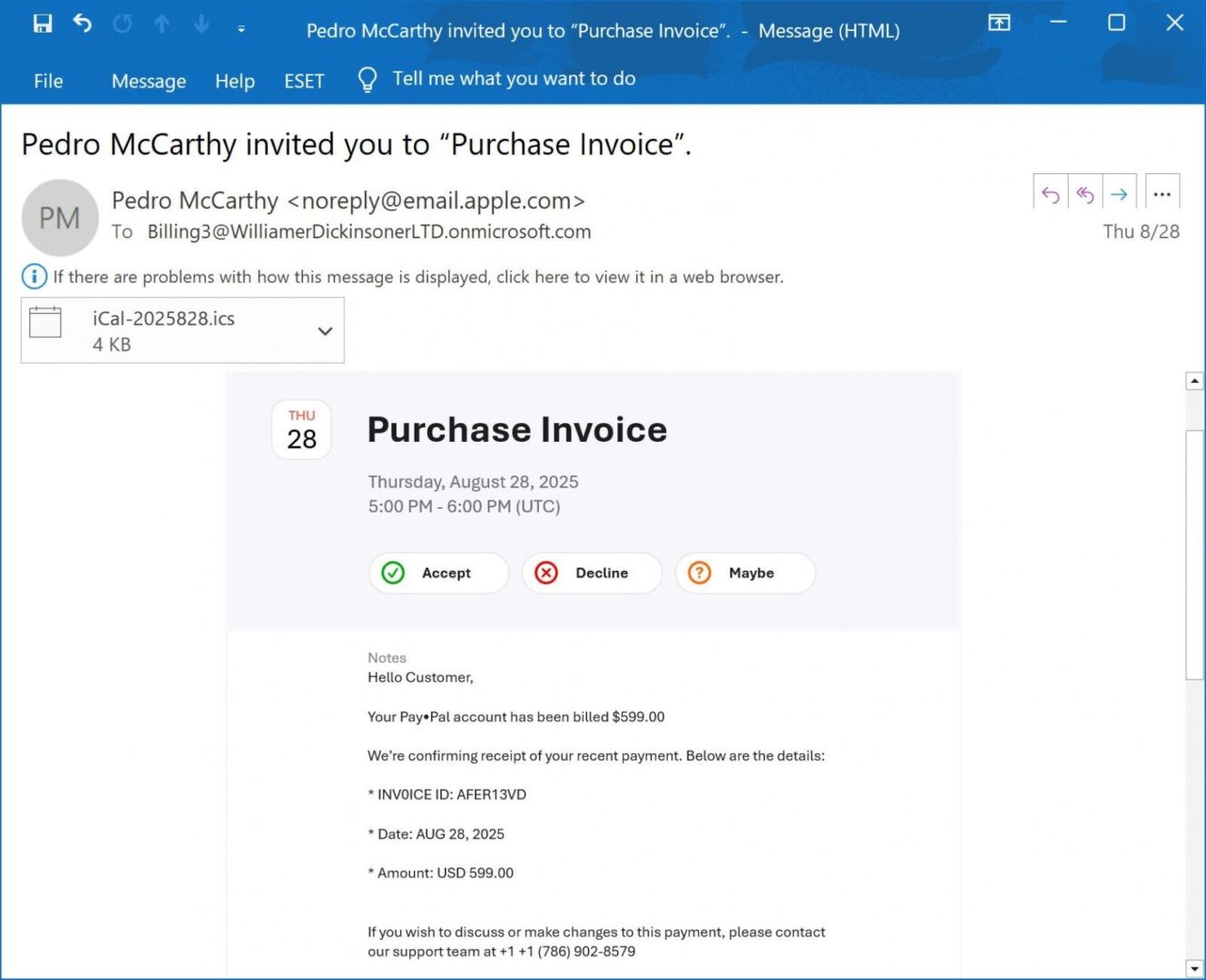
The purpose of these emails is to deceive users into thinking their PayPal account has been compromised and that fraudsters are using their money to make purchases. The attackers aim to scare the recipient into calling the number of a fake “support” line.
During the call, the scammers keep intimidating the victims, insisting that the account has indeed been hacked. The attackers then offer to connect remotely to the victim’s computer (supposedly to issue a refund) or ask them to download and run some software. Naturally, the criminals ultimately use the obtained remote access to steal money from the user’s bank accounts, deploy malware, or steal data from the compromised machine.
However, in this case, what was strange was that the phishing email came from the address noreply@email.apple.com, passing all the SPF, DMARC, and DKIM security checks. In other words, the message did in fact originate from Apple’s mail server.
The journalists explain that the email was actually an iCloud Calendar invitation. The attackers simply added the phishing text to the Notes field and then sent the invitation to a Microsoft 365 address they controlled.
When an event is created in iCloud Calendar and external people are invited, an invitation email is sent from Apple’s servers at
(email.apple.com) on behalf of the iCloud Calendar owner. Such an email comes from the address noreply@email.apple.com.
In an email obtained by Bleeping Computer, the invitation was addressed to a Microsoft 365 account (Billing3@WilliamerDickinsonerLTD.onmicrosoft.com).
Researchers believe that this campaign is similar to another scam discovered in the spring of 2025. The thing is, in both cases the Microsoft 365 address to which the invitation is ultimately sent is actually a distribution list that automatically forwards any incoming messages to all other members of the group.
Because the original malicious email originates from Apple’s mail servers, when forwarded by Microsoft 365 it would fail SPF verification. To prevent this, Microsoft 365 uses the Sender Rewriting Scheme (SRS) to rewrite the return path to a Microsoft-associated address, which allows the message to pass the checks.
Although there was nothing special about the phishing message itself, abusing the legitimate iCloud Calendar invitation feature and Apple’s mail servers helps attackers trick spam filters, since the emails come from a trusted source.
Representatives of BleepingComputer informed Apple about this fraudulent scheme but have not received a response from the company.
