Researchers warn of the largest supply chain attack in history. Attackers injected malware into hugely popular npm packages, with more than 2.6 billion weekly downloads (including JavaScript libraries like chalk and strip-ansi). To carry out this attack, the hackers compromised a maintainer’s account using a phishing attack.
On the evening of September 8, 2025, maintainer Josh Junon, also known by the handle Qix, reported that his accounts had been taken over during an attack and that he was aware of the compromise.
He said he received a phishing email from support@npmjs[.]help — a domain registered on September 5, 2025. The website hosted at that address masqueraded as the legitimate domain npmjs.com.
In the emails, which other maintainers also received, the attackers claimed that the account would supposedly be blocked on September 10, 2025, unless immediate action was taken.

“As part of our ongoing commitment to account security, we ask all users to update their two-factor authentication (2FA) credentials. Our records show that it has been more than 12 months since your last 2FA update,” the phishing message read. “To maintain the security and integrity of your account, please complete the update as soon as possible. Please note that accounts with outdated 2FA credentials will be temporarily locked after September 10, 2025 to prevent unauthorized access.”
As noted by Bleeping Computer, npmjs[.]help contains a login form that transmits all entered credentials to the following URL: https://websocket-api2[.]publicvm[.]com/images/jpg-to-png.php?name=[name]&pass=[password].
“I apologize to everyone; I should have been more careful,” Junon writes. “This is not like me at all. I’ve had a hectic week. I’ll try to fix all of this.”
The npm team has already begun removing malicious versions of the compromised packages published by the attackers.
The compromised packages where Qix was a developer or maintainer collectively account for more than 2.6 billion downloads per week. They’re not only used directly, but also serve as dependencies for thousands of other packages:
- backslash@0.2.1 (0.26 million weekly downloads);
- chalk@5.6.1 (299.99 million weekly downloads);
- chalk-template@1.1.1 (3.9 million weekly downloads);
- color-convert@3.1.1 (193.5 million weekly downloads);
- color-name@2.0.1 (191.71 million weekly downloads);
- color-string@2.1.1 (27.48 million weekly downloads);
- wrap-ansi@9.0.1 (197.99 million weekly downloads);
- supports-hyperlinks@4.1.1 (19.2 million weekly downloads);
- strip-ansi@7.1.1 (261.17 million weekly downloads);
- slice-ansi@7.1.1 (59.8 million weekly downloads);
- simple-swizzle@0.2.3 (26.26 million weekly downloads);
- is-arrayish@0.3.3 (73.8 million weekly downloads);
- error-ex@1.3.3 (47.17 million weekly downloads);
- has-ansi@6.0.1 (12.1 million weekly downloads);
- ansi-regex@6.2.1 (243.64 million weekly downloads);
- ansi-styles@6.2.2 (371.41 million weekly downloads);
- supports-color@10.2.1 (287.1 million weekly downloads);
- proto-tinker-wc@1.8.7 (1,100 weekly downloads);
- debug@4.4.2 (357.6 million weekly downloads).
“By compromising Qix, the attackers gained the ability to distribute malicious versions of packages on which countless applications, libraries, and frameworks indirectly depend,” warn security researchers from Socket. “Given the scale and the packages affected, this appears to have been a targeted attack designed to maximize coverage across the entire ecosystem.”
According to specialists at Aikido Security, who are also investigating the incident, after seizing control the attackers updated the packages, injecting 280 lines of malicious code into the index.js files that acts as an interceptor and is capable of capturing network traffic and application APIs.
The malware affects only users who access the compromised applications via the web, tracking addresses and cryptocurrency transactions, which are then redirected to wallets controlled by the attackers themselves.
Researchers report that the malware injects itself into the browser and monitors crypto wallet addresses as well as transfers of Ethereum, Bitcoin, Solana, Tron, Litecoin, and Bitcoin Cash. It replaces recipient addresses with attacker-controlled ones and intercepts transactions before they are signed. Reportedly, this is implemented by hooking JavaScript functions such as fetch, XMLHttpRequest, and wallet APIs (window.ethereum, Solana, and so on).
“The packages were updated with code that runs on the client side, stealthily intercepting crypto and web3 activity in the browser, manipulating wallet interactions, and altering payment addresses so that funds and confirmations are redirected to attacker-controlled accounts without any obvious signs to the user,” Aikido Security explains. “The danger of this malware is that it operates on multiple levels: it alters content displayed on websites, interferes with API calls, and manipulates what applications believe they are signing.”
Bleeping Computer notes that compromising an application in connection with this supply-chain attack required a number of conditions to be met:
- a new installation was performed between 9:00 and 11:30 AM ET (Eastern Time), when the packages were compromised;
- during that time, the package-lock.json was created;
- the compromised packages were among the direct or transitive dependencies.
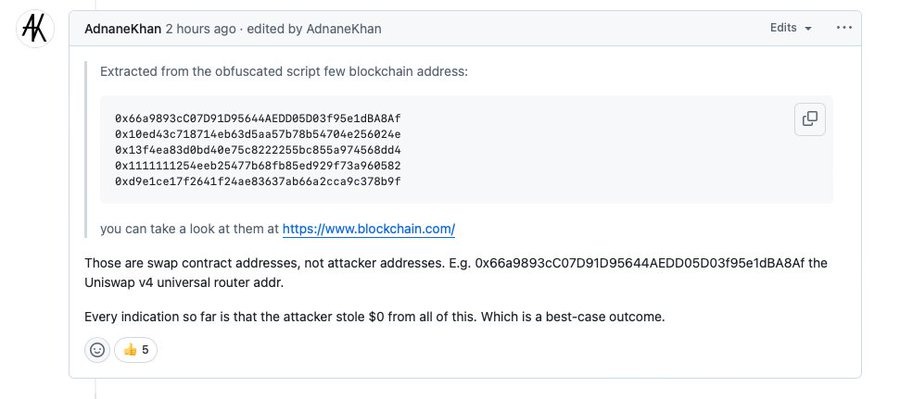
At the same time, experts from the nonprofit Security Alliance (SEAL) and researchers at VXUnderground write that the attack can hardly be called successful. According to researchers, the attackers behind the largest supply chain attack in history “made” anywhere from a few cents to $50 from it.
Experts report that a bug crept into the malware’s code, causing the attackers to substitute not their own cryptocurrency wallets but the addresses of Uniswap and other swap contracts (instead of the actual recipients’ addresses). In other words, the stolen funds were essentially sent to nowhere.
Nevertheless, Ledger’s CTO Charles Guillemet published an urgent warning and advised users who don’t have hardware wallets to avoid on-chain transactions until the consequences of the attack are fully understood.
“The infected packages have already been downloaded over a billion times, which could put the entire JavaScript ecosystem at risk. The malicious payload silently swaps crypto addresses on the fly to steal funds. If you use a hardware wallet, pay attention to every transaction before signing, and you will be safe. If you don’t use a hardware wallet, refrain from any on-chain transactions for now. It’s not yet clear whether the attackers are stealing seed phrases directly from software wallets,” Guillaume warned.
