In one of our earlier articles, we explored ways to expose all kinds of resources as files and directories—WebDAV, BitTorrent, SSH, and even GPU memory. But what if we want access not to a remote or local…
CONTINUE READING 🡒 Microsoft says the Windows update didn’t damage SSDs or HDDs
Microsoft representatives said the company has not found any connection between the August security update KB5063878 and customer complaints about crashes and data corruption issues affecting SSDs and HDDs from various manufacturers.
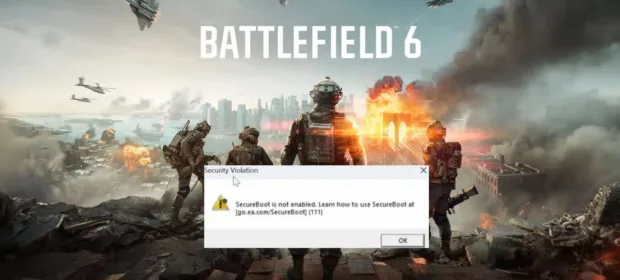
CONTINUE READING 🡒 Battlefield 6 anti-cheat requires Secure Boot
In August, Electronic Arts (EA) announced that players in the Battlefield 6 open beta on PC would need to enable Secure Boot in Windows and BIOS settings. The decision sparked debate and criticism, as many were unwilling…
CONTINUE READING 🡒 Computer Vision with Python: Training a Neural Network for Digit…
Numeric CAPTCHAs used to be a great way to filter out bots, but you hardly see them anymore. You can probably guess why: neural networks now solve them better than we do. In this article, we’ll look…
CONTINUE READING 🡒 Vulnerability Scanning with Kali Linux: Penetration Testing Essentials
Vulnerability scanning is the process of identifying and analyzing critical security weaknesses in a target environment. It’s sometimes referred to as a vulnerability assessment. Vulnerability scanning is a core function of a vulnerability management program focused on…
CONTINUE READING 🡒 Building a Mobile App with Firebase: Google’s Free, Powerful Backend-as-a-Service
Google’s new Firebase can cover most mobile developers’ needs—and even solve problems you don’t have yet. It’s free within a generous tier, and you’ll have to try hard to exceed it. In this article, I’ll start outlining…
CONTINUE READING 🡒 Vicious exploitation. Searching for buffer overflow vulnerabilities with Angr
Angr, a powerful symbolic emulator, makes it possible to seize control over execution of someone else’s code; all you have to do is specify the search direction. Today you will learn how to find similar holes in applications using Angr; in addition, you will write an inline…
CONTINUE READING 🡒 Build a Custom, Debloated Windows 10 ISO the Easy Way
Building your own OS distributions is a favorite pastime among Linux enthusiasts. It’s often assumed that Windows users don’t get to enjoy anything similar. Not quite: there are ways to strip unnecessary components from a Windows 10…
CONTINUE READING 🡒 60+ Gift Ideas for Hackers: Best Geeky Gadgets for Friends…
We’ve rounded up 60+ gadgets, so you’re bound to find something to delight your geeky friends for New Year’s or any other occasion—or (we’ve all been there!) a great way to spend the gift cash from relatives…
CONTINUE READING 🡒 Positive Technologies: Attacks via GitHub and GitLab Hit Record Levels
By posting fake projects on popular developer platforms (GitHub and GitLab), attackers trick users into executing malicious payloads that fetch additional components from a hacker-controlled repository. As a result, remote access trojans and spyware are downloaded onto…
CONTINUE READING 🡒 Jon von Tetzchner speaks out against AI in browsers
Jon von Tetzchner, head of the Norwegian company Vivaldi Technologies, which develops the browser of the same name, shared his thoughts on integrating AI into browsers. In von Tetzchner’s view, the industry’s attempts to merge AI models…
CONTINUE READING 🡒 Corosync and Pacemaker: Best Practices for Deploying a High‑Availability (HA)…
Getting a service to handle heavy traffic is a challenge every sysadmin runs into sooner or later. It’s best to put high-availability mechanisms in place ahead of time—before critical nodes start failing. In this article, I’ll cover…
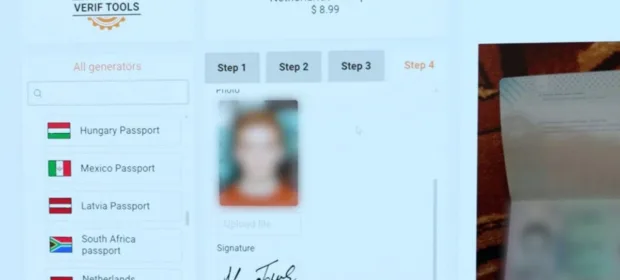
CONTINUE READING 🡒 Law enforcement shuts down VerifTools, a service for creating fake…
The FBI and Dutch police report the shutdown of the VerifTools marketplace, which specialized in creating fraudulent documents. Law enforcement seized the service’s servers located in Amsterdam.
CONTINUE READING 🡒 NX hit by a supply chain attack; hackers stole thousands…
The maintainers of NX warned users about a supply chain attack dubbed s1ngularity that occurred on August 26, 2025. The compromise of one developer’s token allowed the attackers to publish malicious versions of the popular npm package…
CONTINUE READING 🡒 Unmasking Shingled Magnetic Recording in Western Digital and Seagate HDDs
Until recently, the savvy user—the kind who doesn’t mind spending a few days on forums—knew this as gospel: Seagate’s consumer drives use SMR (shingled magnetic recording), which is bad, and Western Digital’s don’t. Lots of people based…
CONTINUE READING 🡒 Nevada government agencies shut down after a cyberattack
Last weekend, the U.S. state of Nevada was hit by a large-scale cyberattack. As a result, for several days authorities have been grappling with the aftermath of the incident, which disrupted government websites, phone systems, and online…
CONTINUE READING 🡒 Crypto drainers. New scam empties crypto wallets automatically
Drainers represent a new type of phishing that is currently ravaging the cryptocurrency world. It’s growing at an incredible speed and has already surpassed ransomware in terms of prevalence and stolen funds. This article provides an insight into drainers, their operational principle, and the market that emerged on their…
CONTINUE READING 🡒 From Android 1.0 to 8.0: How the World’s Most Popular…
Ten years ago, Google’s engineers released the first Android SDK and the first emulator, letting anyone get a feel for the new OS. Back then, few people took it seriously. Which makes it all the more interesting…
CONTINUE READING 🡒 Anthropic: Hackers used Claude in a large-scale cyber operation
Anthropic reports that it has disrupted a large-scale malicious operation in which attackers used Claude in July 2025 to steal personal data and commit extortion. The ransoms demanded by the hackers at times exceeded US$500,000.
CONTINUE READING 🡒 Crypto Mining Made Easy: Automate Your Operations and Optimize Performance
Lately, the mining landscape has changed fundamentally. With around a thousand altcoins now, focusing on a single cryptocurrency has become too risky. Exchange rates and mining difficulty are constantly in flux. Keeping up and manually switching to…
CONTINUE READING 🡒