In any phishing campaign, the main goal of the attacker is to fool the victim into disclosing personal information that must never be disclosed to strangers. In the case of drainers, users are prompted to grant the smart contract permission to interact with their funds.
info
Most drainers work with blockchains that support smart contracts and attack users of Ethereum-like networks: Ethereum, Base, Polygon, Optimism, etc. However, some drainers target Solana, and a drainer targeting Bitcoin has appeared recently.
Let’s say you want to connect your MetaMask wallet to a project’s website to earn some cryptocurrency (e.g. to purchase a new token while it’s cheap). You click the Connect button, enter your password, and sign the approval transaction (i.e. grant the smart contract permission to access your wallet).
That’s the catch: instead of a legitimate contract, the drainer makes you sign a malicious smart contract that grants it permission to siphon off your funds. In other words, you voluntarily agree to give away all your money!
How can this happen? The trick works best during airdrops (i.e. distributions of new tokens). They attract plenty of people willing to get some cryptocurrency whose price can grow tenfold over time. Sometimes, such distributions are indeed conducted to pump up a new token. At that moment, the user is driven by so-called ‘fear of missing out’ (FOMO).
The victim is in a hurry and might forget to check who has created the page they are interacting with and what exactly this smart contract does. The malicious website can be completely copied from a legitimate one; while the purpose of such a smart contract is to take money instead of giving it.
Drainers are gaining momentum
In 2024, an important milestone was passed: drainers surpassed regular ransomware in terms of distribution rates and revenue. Of course, ransomware continues to plague big business, but many scammers have rushed to new — yet unoccupied — niches.
First drainers were distributed via DarkNet platforms in the form of scripts. According to Kaspersky Lab, 55 unique forums related to drainers were recorded in 2022. In 2024, the number of such resources reached 129 (i.e. it more than doubled in two years).
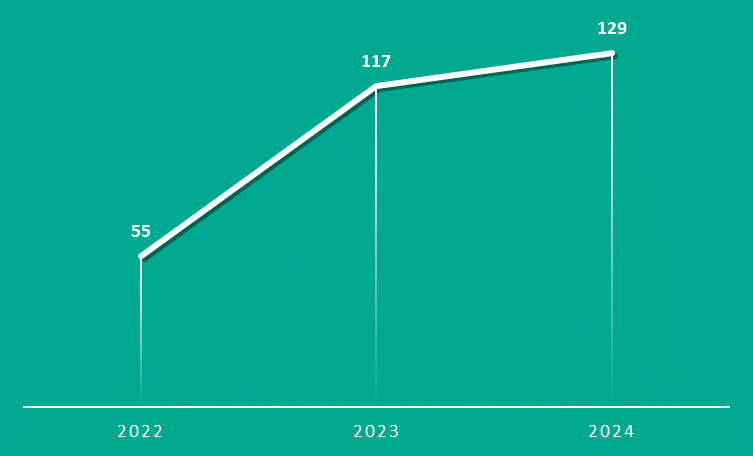
And this statistics applies only to such a specific and essentially useless place as the dark web. Currently, all communication takes place on Telegram and Discord.
The following major drainers were active in 2024: Angel, Inferno, Pink, Ace, Cerberus, Nova, Medusa, MS, CryptoGrab, and Venom. Currently, Angel and Ace are most active among them, but a new player has emerged: Vanilla. So far, this drainer remains poorly researched since it uses a private model: it’s difficult for an ‘ordinary’ scammer to gain access to Vanilla.
According to Scam Sniffer, a company that analyzes cryptocurrency frauds, the total losses caused by drainers amounted to 494 million USD in 2024.
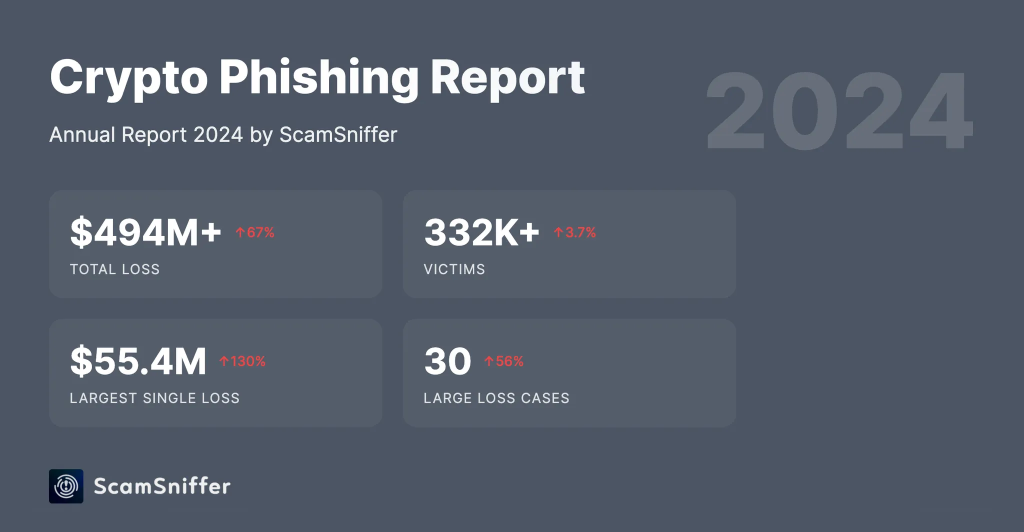
And this figure reflects only major thefts that were accounted for! Since drainers are mostly targeting ordinary users, petty thefts (e.g. a few thousand dollars) aren’t even recorded in this statistics. In other words, 494 million USD is only the lower limit; while the real amount is much greater.
In 2024, 330 thousand major players fell prey to drainers. The record theft in that year was 55 million USD. In total, there were some 30 large-scale malicious campaigns: one and a half times more compared to 2023.
In the first quarter of 2024, amounts siphoned off by drainers have grown almost sixfold (the ransomware market has only doubled over this period).
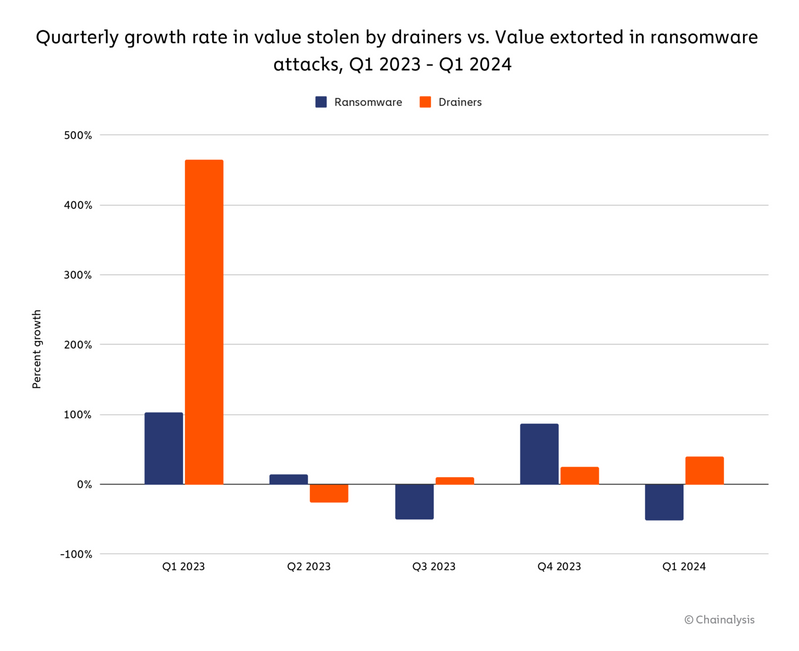
What do these figures mean? Since the malicious industry is so easy to enter, scammers previously engaged in email phishing (i.e. guys luring people to rogue bank pages) and other traditional scams are flocking there.
Cybercriminals apply their malicious skills to cryptocurrency traders and gain enormous profits. Using drainers, even an ordinary scammer can ‘earn’ 100 thousand dollars per month and more.
It might seem that just a few months of such ‘work’ can provide you with an apartment, a car, and regular vacations in Thailand. Take a risk once, and then you can leave the game! But, of course, no one leaves this ‘business’ after two months because of its supernatural profitability.
Why is it so easy?
Unlike ransomware that primarily targets companies, drainers attack ordinary users and can potentially reach any person dealing with cryptocurrencies.
Drainers have become so popular because of their wide coverage and ease of entry into this malicious industry. In addition, the crypto world operates with big money, and its users easily dispose of their funds.
A ransomware operator has to contact a company, negotiate the conditions, and organize the transfer of money and decryption, which means a lot of hassle. By contrast, a drainer steals money immediately.
Similar to many other scam types, drainers are distributed using the SaaS (Software-as-a-Service) model. They are even called DaaS (i.e. Drainer-as-a-Service).
The industry features a characteristic division of labor. It involves malware developers, workers (ordinary employees), as well as recruiters, traffic arbitrage specialists, and providers of various accessorial services.
Of course, the main job is performed by developers: they create malware and continuously optimize its usage, deployment, and scaling. Generally speaking, drainers are classical IT products.
How to conduct a campaign
To conduct a phishing campaign, the attacker needs the following components:
- domains for future sites whose names must be similar to the name of the copied project;
- hosting;
- landing (a page impersonating a legitimate project);
- drainer code (usually this is JS code stored on the site);
- control panel that shows the number of users lured to the rogue page and tracks their behavior; and
- personal security tools (VPN, Proxy, and SockPuppet accounts).
Professional cybercriminals usually deploy a fully-functional C&C server enabling them to control drainer’s behavior.
All that remains is to bring victims to the malicious page. At this point, traffic arbitrage specialists also known as arbitrageurs join the game. Their task is to direct users to a phishing page. This can be achieved in different ways: from Google ads to direct communication with users in comments and posts. Sometimes scammers even clone official support channels of legitimate projects.
As a result, attackers gain a real sales funnel: a path that victims go through.
Splitting stolen money
20–30% of the loot goes to the operators; the rest goes to the workers (i.e. those who directly scam people). Workers’ profit depends on their qualification. Beginners pay 30% to operators; while the most experienced ones, 10–15%.
Worker’s qualification is determined based on stolen funds: beginner (up to 10 thousand dollars), middle-level (25–50 thousand dollars), or professional (100 thousand dollars and up).
Traffic arbitrage
Special tutorials are used to spread knowledge among workers. A tutorial can be purchased, sold, or exchanged. To gain access to various tutorials, special communities are created.
I managed to gain access to several such tutorials. Interestingly, their texts clearly indicate that these documents were written using neural networks.
Generally speaking, the same traffic generation scheme used in regular phishing is employed (with some cryptocurrency-specific adjustments).
A worker essentially does the same job as any online advertising specialist. Worker’s goal is to increase the number of people visiting phishing pages. To achieve this, they search for users who are interested in Web3 and DeFi projects, have crypto wallets, or are looking for airdrops, swaps (token exchanges), and exchangers.
Demographic analysis and geolocation analysis (i.e. standard targeting techniques familiar to all advertisers) are used. Workers are also responsible for ‘website design’ (by cloning pages of existing projects). They even use marketing techniques such as A/B testing.
Now let’s examine several high-profile thefts performed using drainers.
Attack on Arkham Intelligence
Arkham Intelligence specializes in blockchain analytics. It operates a cryptocurrency exchange platform and a popular tool that enables users to track transactions. For example, traders use it to find out how much an asset costs and where it’s traded.
In 2023, Arkham Intelligence issued its own token and launched an airdrop of coins. However, attackers created multiple rogue profiles on X.com to redirect users to phishing pages containing drainers.
The bots were tenacious and evaded blocking for a long time. They impersonated Arkham activity and distributed malicious links.
The rogue links redirected users to pages indistinguishable from the Arkham website; the only difference was that not a single button worked on the phishing websites except for “Wallet Connect”.
The investigation showed that Angel Drainer was used in that attack. Interestingly, the client JS code settings contained the string Angel .
Enormous numbers of such rogue websites were created; their lifespan amounted to a few weeks (a few months as a maximum). Angel Drainer makes it possible to quickly copy landings and deploy them on new domains. The process is so simple that the worker only has to give a few commands to the bot in a Telegram chat to launch a new website.
Attack on SEC
An even larger scale can be achieved if the attackers manage to capture a real account of some reputable company or a government organization.
This is exactly what happened with the U.S. Securities and Exchange Commission (SEC). On January 9, 2024, its X.com account was hijacked using SIM swapping, an account takeover fraud involving the reissue of a SIM card linked to a specific account. SEC officials simply forgot about security and didn’t enable multi-factor authentication on their corporate account.
info
SIM swappers and drainers closely cooperate with each other. Swappers are massively providing drainers with hijacked accounts.
The attackers published a post claiming that the SEC officially permits investing in Bitcoin without buying cryptocurrency on such exchanges as Binance or Coinbase.
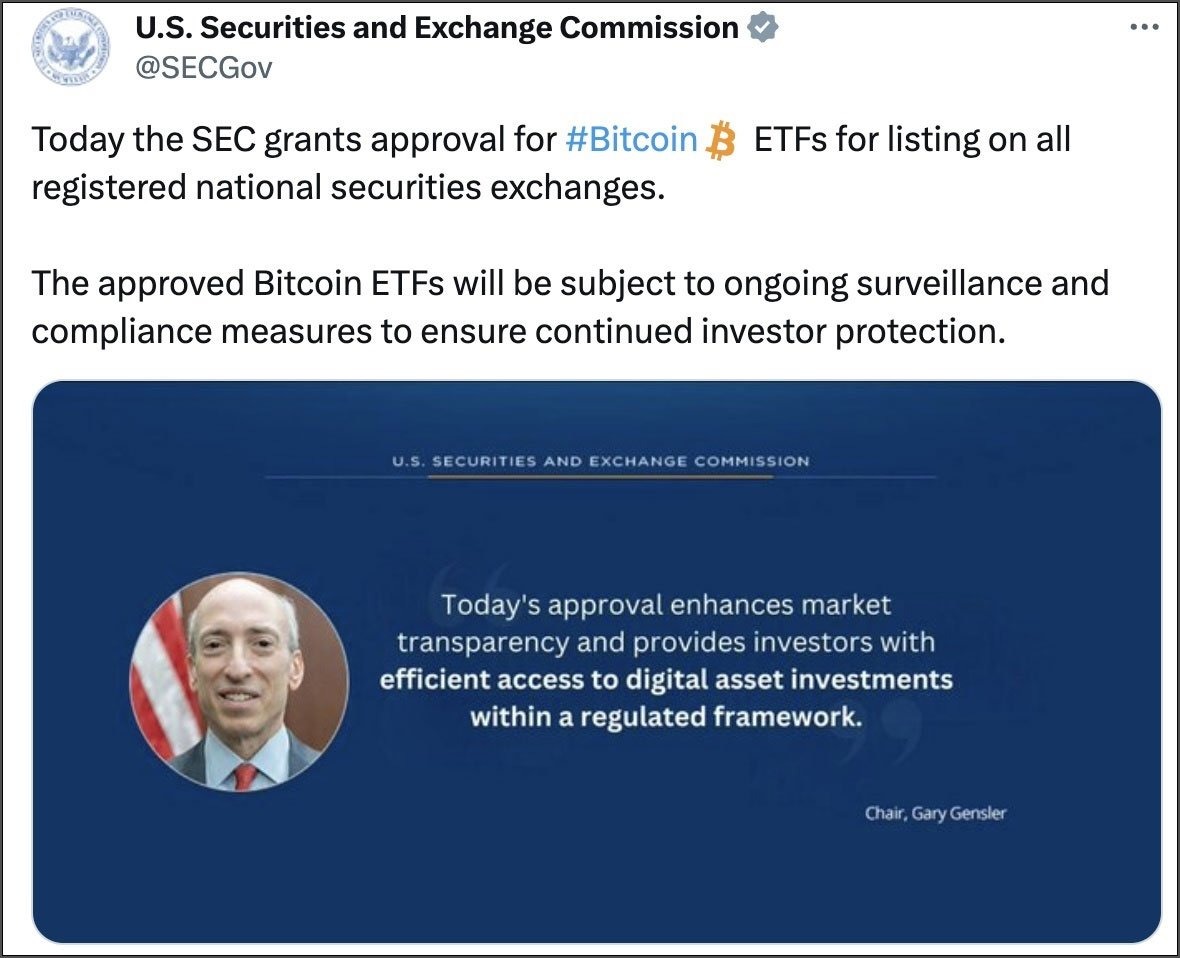
This caused a stir because investors had been waiting for such a decision from the SEC for a long time and expected it to be made in just a few days. Then the cybercriminals announced an official airdrop from the SEC — on a special website containing a drainer.
Interestingly, this publication caused a rise in the Bitcoin exchange rate: it increased by a thousand dollars.
Attack on Lottie-Player
Sometimes drainers are distributed using not only simple phishing techniques, but sophisticated hacker attacks. Take, for example, the story of Lottie-Player. It was a classical supply-chain attack very popular among hackers.
The target of this attack was the Lottie-Player graphics rendering plugin commonly used on Web3 project websites to create animations using JavaScript.
Lottie-Player versions from 2.0.5 to 2.0.7 were infected. A backdoor was embedded into the code published on NPM; using a specially crafted JSON, it allowed attackers to inject Ace Drainer into legitimate websites.
To deliver this attack, the malefactors hacked the GitHub account of a senior Lottie-Player developer. After that, they released three compromised updates in just three hours.
As a result, the Ace Drainer code was injected into websites offering users to connect a wallet (e.g. Trust Wallet or MetaMask), but instead of connecting it to the platform, Ace Drainer tricked victims into granting their permission to siphon off all their funds.
One of the main victims was the 1inch Web3 platform, but its owners claim that only the decentralized application (DAPP) was damaged in the attack; while the Wallet application remained intact.
In fact, the attackers have monetized their work (i.e. hacking victim’s account) by purchasing and injecting Ace Drainer. Ordinary workers definitely wouldn’t be able to perform such a trick.
Scamming the scammers
Scammers wouldn’t be scammers if they didn’t scam each other. One day, the developer of Pink Drainer realized that his deanonymizing is inevitable and decided to get out of the game and withdraw the loot.
Cryptocurrency gained as a result of scams cannot be simply sold. To withdraw funds, the scammer has to launder them first; otherwise the exchanger might suspect something and freeze the money.
info
To prevent terrorism sponsoring and breaches of the law, exchangers use scoring and don’t accept ‘dirty’ crypto. This is called AML (anti-money-laundering) score.
There are many money laundering techniques; Pink Drainer attempted to use one of them and fell prey to a scam.
The scammer hammered into the simplest type of fraud: so-called address poisoning. This type of attack might seem incredibly stupid, but sometimes it works.
Attackers generate cryptocurrency addresses similar to the victim’s address and send the victim a minimum amount of money so that the rogue address appears in the transaction history.
From the user perspective, this looks as follows: you send, say, 100 USD to some other wallet (e.g. to an exchanger), and 5–10 minutes later you receive several small transfers from allegedly the same wallet that, in fact, only has a similar address (e.g. with identical beginning and ending).
The idea is that the next time you would select the last address from the transaction history and send money not to yourself, but to the attacker.
This is exactly what Pink Drainer did: selected the last transaction and sent 10 ETH (some 15,000 USD at that time) to some unknown colleague.
Conclusions
The simplicity and popularity of draining make this type of scam a persistent threat. No doubt, techniques used to inject malicious payloads will evolve over time.
Most drainers are targeting ‘young’ blockchains. For example, Ethereum-based networks are well-protected; while Solana doesn’t have such security mechanisms yet.
New types of drainers are expected to appear: some scammers already create applications for Google Play and App Store instead of websites.
Be vigilant and think twice before pressing a button!
