warning
The crypto market changes rapidly, so the recommendations here will need adjustment over time. Keep up with the news and start with small investments to gain firsthand experience without exposing yourself to significant financial risk.
Dreams and Nightmares of a Crypto Miner
Not long ago, a novice miner could “set it and forget it.” You’d pick a coin you thought had the best upside—maybe two at most: a primary and a fallback. Then you’d work out the optimal rig configuration for its hashing algorithm, or just rent ready-made nodes from a cloud mining provider. Next came configuring and launching the miner itself—a command-line tool tailored to each algorithm. After that, you’d set up critical alerts and only occasionally check whether the virtual coins were trickling into an equally virtual account.
Sure, plenty of people checked their stats ten times a day and woke up in the middle of the night, but that’s psychology, not technology. Back when Litecoin was still the “silver standard,” you didn’t need to constantly babysit the process. What you needed was patience—and not even that much.
Initially, projections promised a rapid payback and profits within a few months (a year at most). But as time went on, the more popular the chosen cryptocurrency became, the more the per-node mining rate fell, driven by the rapidly increasing difficulty of finding a valid hash for each new block.
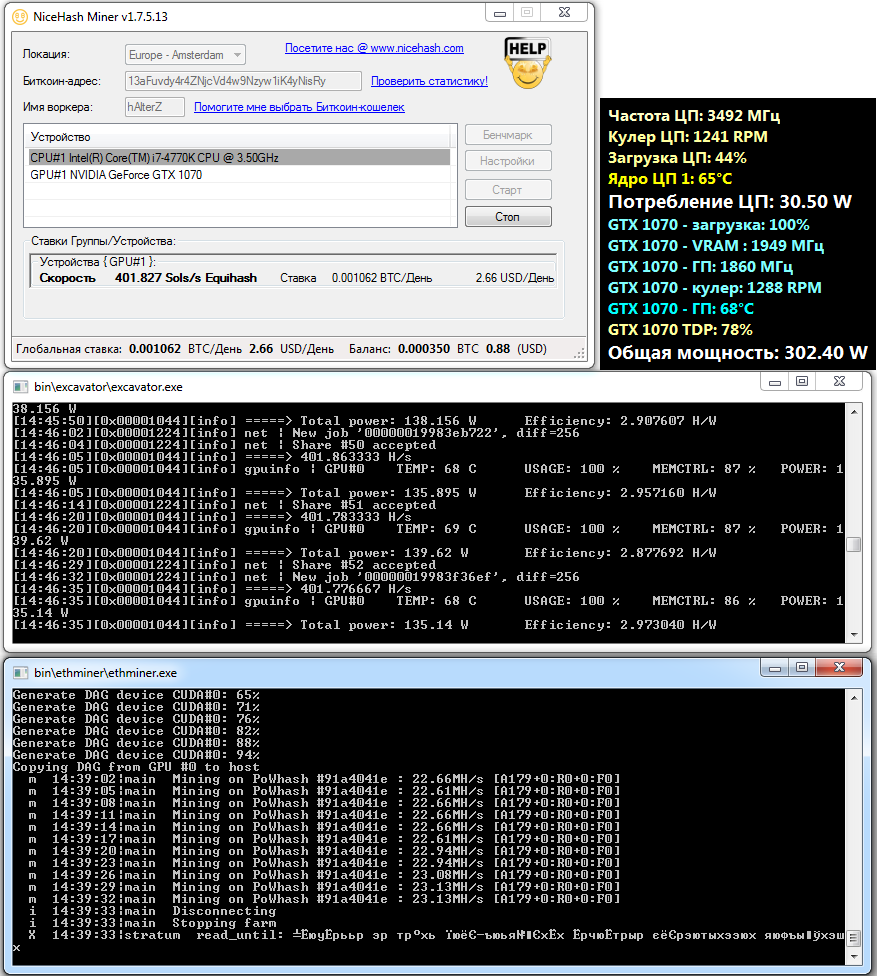
When I started writing this piece, it looked like the “Excavator” was mining at a healthy clip. It was pulling in 5.76 USD per day, and for a single, not-so-high-end graphics card, that would be a solid return.
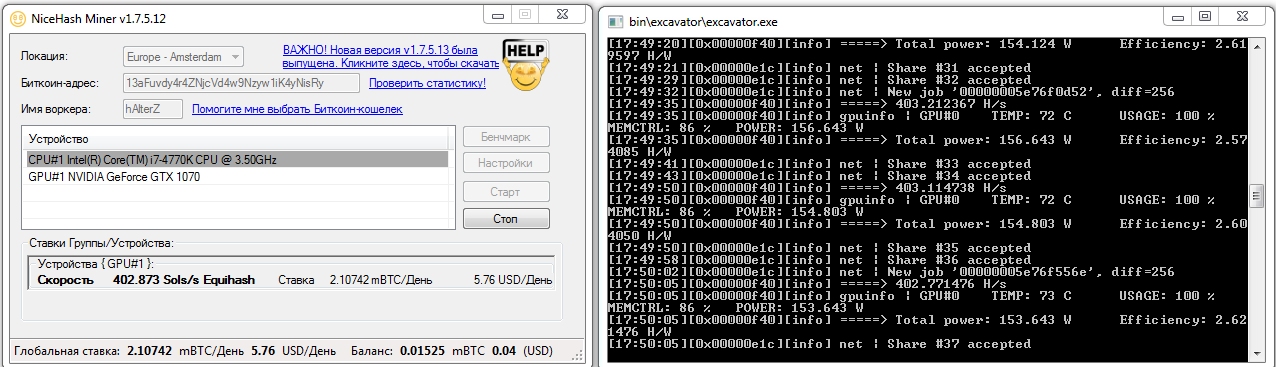
But that was just a temporary effect of market speculation. Once the hype faded and prices stabilized, the same rig with the same settings was bringing in only 2.13 USD per day. At times it was basically idling, since profitability dropped below 1 USD a day. The same thing happened with other cryptocurrencies, just at different times. So you could cut losses by switching to mining other coins at the right moment.
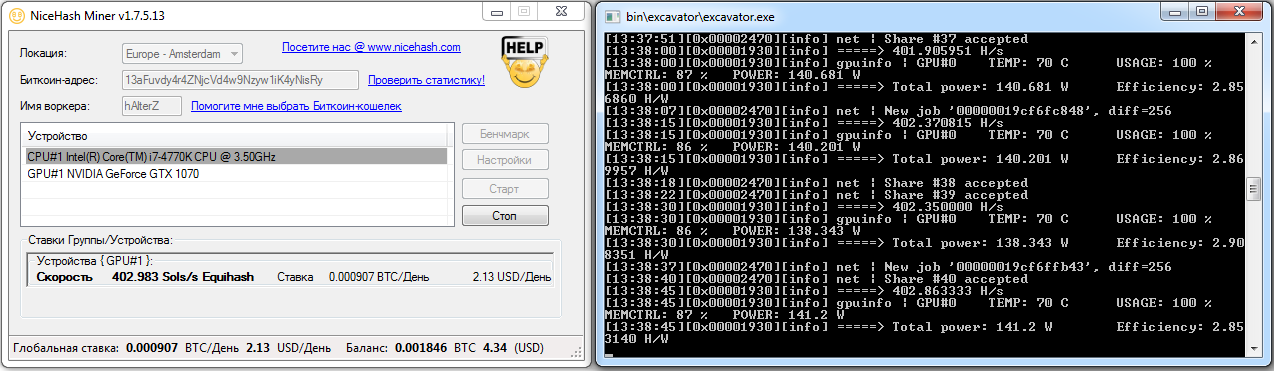
Cloud operators even added a new FAQ entry explaining the steady decline in payouts. In absolute terms, the hashrate of the purchased system stayed the same, but its share of the total network hashrate often dropped faster than the online profitability calculators had projected.
On top of that, electricity rates kept rising, and new chips and algorithms were coming out. Market volatility adds to the uncertainty, leading to hours or even days when mining your chosen cryptocurrency is plainly unprofitable.
For example, in one short test run I mined about 18 rubles’ worth of Decred, while the electricity for the same period cost 23 rubles. In other words, I paid more than I earned from mining. Should I have paused? If so, for how long? Switched to another cryptocurrency? Which one? Fortunately, I no longer have to agonize over those questions in the middle of the night when another alert goes off. There are universal, multi-coin mining systems that aren’t tied to a single altcoin and help reduce financial risk.
Claymore’s Dual Miner
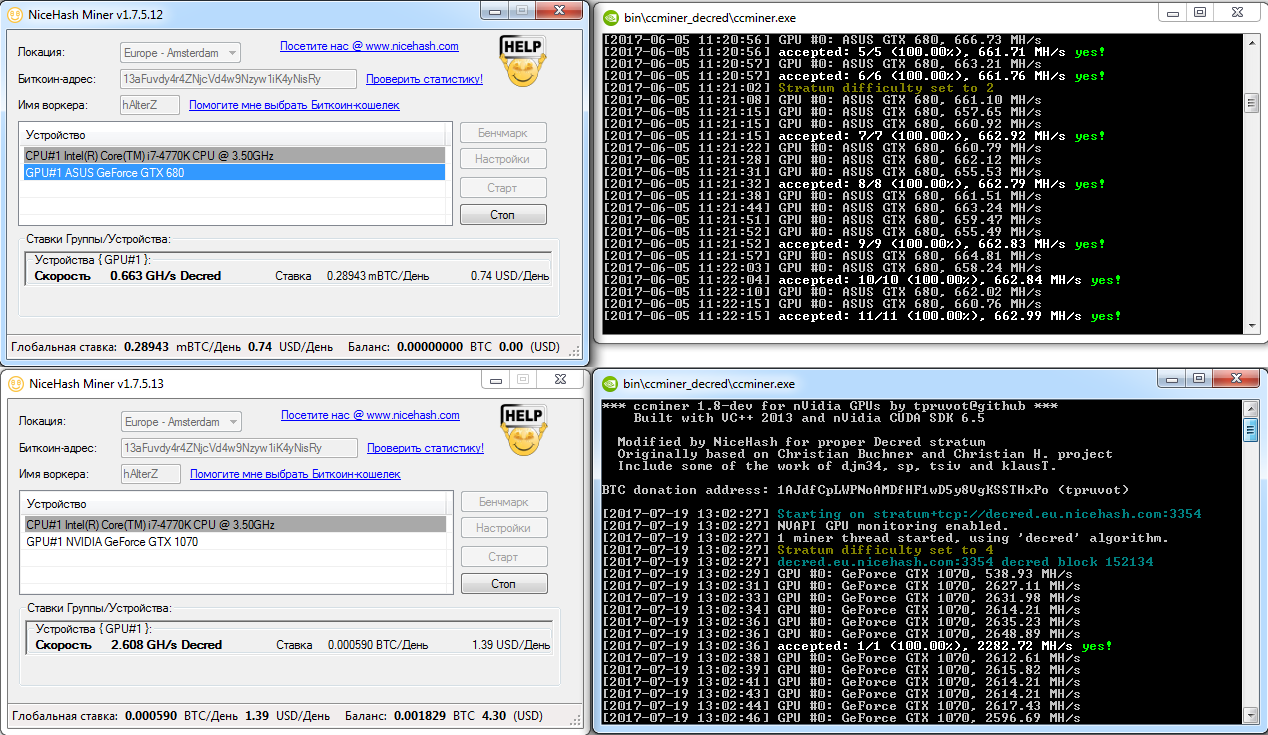
This miner can run dual-mining: Ethereum as the primary coin, plus your choice of Decred, Siacoin, LBRY, or Pascal as the secondary. The second coin is mined in parallel with ETH on the same hardware with little to no impact on hashrate. It achieves this through heavy code optimization (including inline assembly), better GPU utilization, support for the Stratum protocol instead of HTTP (which reduces job fetch/submit latency), and other tweaks. Builds are available for Linux and Windows.
Dual Miner lets you run AMD and Nvidia GPUs side by side in the same mining rig and shows detailed per‑card stats. That’s very handy for spotting bad hardware and configuration mistakes. In the example below, the mixed rig has seven GPUs labeled GPU0–GPU6 with different settings. GPU5 is unstable even though there’s still TDP headroom—the fan is only at about 50% and the temperature is well below critical.
Starting Claymore’s Dual Miner from the command line is as easy as it gets. In the archive you download from GitHub, you’ll find batch files with self‑explanatory names. For example, start_eth+sia. will launch simultaneous mining of Ether and Siacoin. To use it, edit the file first—open it as a plain text file and replace the YOUR* placeholders with your wallet address, worker name, email, and other details.
According to the documentation, Claymore’s Dual Miner supports GPUs from both vendors released in the past six years. Because it uses architecture-specific assembly optimizations for GCN, AMD cards of comparable class generally outperform Nvidia in this miner. However, stable operation is typically reported only on newer AMD GPUs based on GCN 3.0 and above; older generations often crash. Fans of the “green team” are better off choosing miners with CUDA optimizations, which we’ll cover next.
The fly in the ointment: the miner has a built‑in developer fee (1% for single‑coin mining and 2% for dual mining). In other words, 72 seconds out of every hour your rig mines for the developer. In practice it can be higher, because it occasionally “forgets” to switch back to your wallet (https://github.com/nanopool/Claymore-Dual-Miner/issues/55). This bug (or feature) doesn’t hit everyone, but its nature raises questions.
The exception is Decred. This coin can be mined with no dev fee, but it’s currently the least profitable. If you run the miner with the --nofee option, the fee won’t be charged either, but your hashrate will drop, so you won’t come out ahead — that’s an intentional limitation.
The miner supports remote management over a JSON protocol. Again, that’s a double-edged sword: you’re relying on the developer’s reputation and trusting that no one but you will be able to control your miner.
You might remember the cautionary tale of the Antminer ASICs. In April 2017, a backdoor was found that allowed remote tracking and shutdown of miners. So much for “anonymity”! So much for “full control”!
These days, browsers themselves often block downloads of Claymore’s Dual Miner. On VirusTotal, 31 out of 61 engines flag it as potentially dangerous software or a trojan, and Chrome simply blocks the download as malicious. The miner’s source code is closed and protected against debugging, which makes it very hard to analyze. Don’t let the fact that you’re downloading it from GitHub fool you — proprietary/closed-source projects show up there too.
NHM
There’s another option that’s extremely easy to get started with and more versatile: the NiceHash Miner (NHM) pool client. It supports Claymore’s Dual Miner as an optional component, and also works with open-source miners, including CUDA‑optimized ones. NHM doesn’t skim a developer fee, and it typically isn’t blocked by antivirus software—AVs may only flag specific miners when NHM downloads them automatically.
NHM is open source. Using it is basically just installing it and clicking “Benchmark” and “Start,” but I recommend applying a few security tweaks first. Even if you use a different program, the basics are the same.
Secure Mining
During cryptomining, GPUs run outside their intended operating envelope and overheat quickly. Current draw, core voltage, heat output, and other parameters often exceed the manufacturer’s recommendations. Unlike gaming, mining holds the load at 100% 24/7. And it’s not just the shader cores under stress: the MOSFETs and other VRM power components can exceed 120°C during nonstop hashing, while the stock cooler can’t keep up. This operating mode shortens the GPU’s lifespan and delivers only a deceptive performance boost, as computational errors begin to appear over time. Those errors aren’t always caused by heat alone—they’re a natural consequence of prolonged operation at the edge of the hardware’s limits.
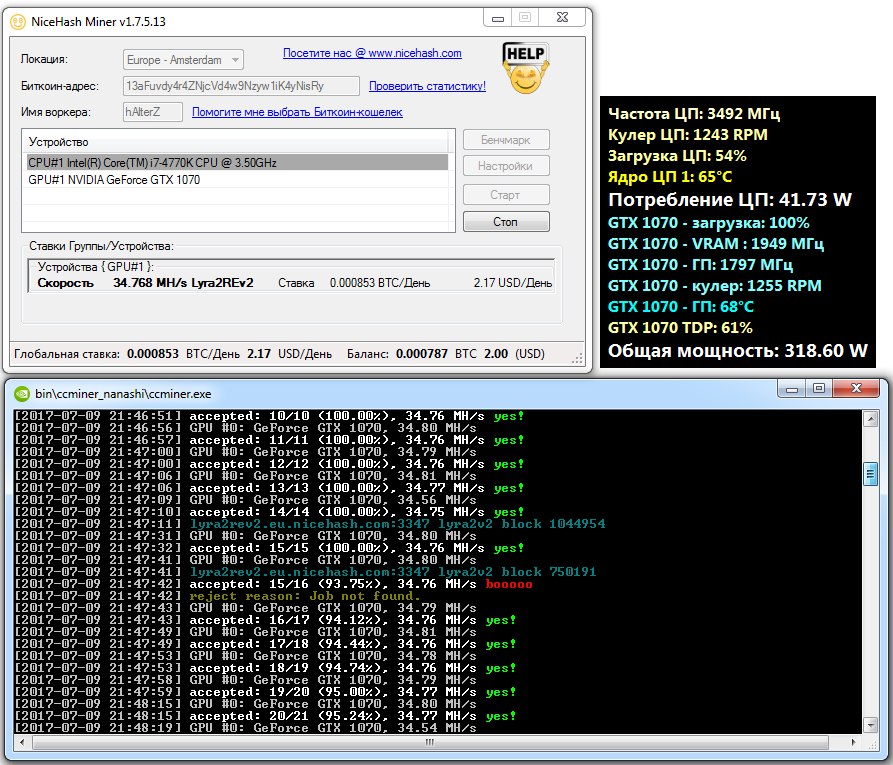
In the example below, I raised the temperature limit by just 1°C. That increased the GPU’s power draw by 15 W and significantly reduced its energy efficiency, with virtually no effect on compute speed.
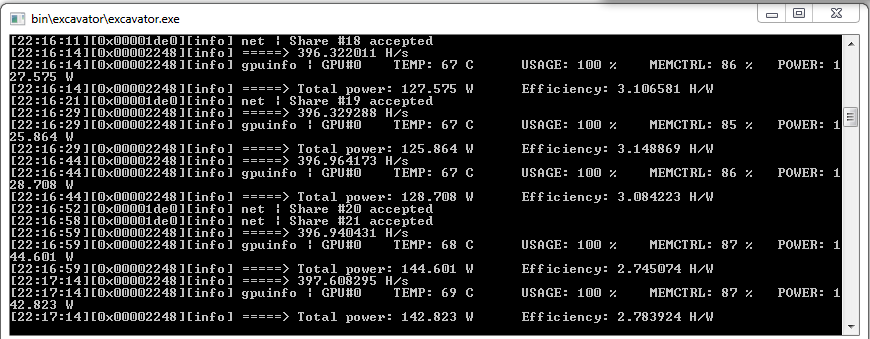
For long, stable mining, cap the TDP or set a maximum GPU temperature. You can do this with vendor tools like ASUS GPU Tweak, MSI Afterburner, and similar utilities. Choose values that keep the card within safe thermals and at a tolerable noise level—typically up to about 80°C. Chips can survive higher temps on paper, but datasheets list short-term absolute maximums for the GPU die, not sustained operating limits. Without a temperature cap, you risk more than just thermal errors—you can cause real hardware damage (dielectric layer breakdown, desoldering of SMD components) and even a fire. Even fairly expensive graphics cards have literally gone up in blue flames in the hands of greedy miners.
After you lock down your security settings, download NiceHash Miner from GitHub: https://github.com/nicehash/NiceHashMiner/releases/. During installation, your browser or antivirus may complain. In my tests these were false positives and Riskware flags. Many trojans try to drop a miner on other people’s machines to steal compute time, often disguised as “optimized” miners that users install themselves. Because of that, antiviruses now flag most mining software, but not all alerts are equal: PUP/Riskware is one thing; Trojan/Backdoor is another. Stay vigilant.
After installation, NiceHash Miner will auto-detect your GPUs and download per-algorithm miners with OpenCL and CUDA support. Some are open source and generally safe; others are proprietary and could contain backdoors. NHM will ask which ones you want to download. I declined the proprietary miners and recommend you do the same. You can review or change this under Settings → General → Enable third-party miners.
In the Bitcoin Address field (on the main window), enter your wallet address. If you don’t have one, you can quickly create a wallet online (https://counterwallet.io) or install an offline wallet on your computer or phone (https://bitcoin.org/ru/choose-your-wallet).
Run the built-in NHM benchmark. The standard test takes a few minutes and estimates miner profitability in BTC/day and USD/day. Prices are fetched automatically, but remember they’re just current snapshots. The market changes by the minute, so don’t read too much into the first numbers.
NHM will also auto-select the most profitable algorithm at the moment and start it right away (unless you unchecked Start mining after benchmark); the others serve as fallbacks. NHM will switch to them if the main algorithm’s profitability drops below a threshold. You can set that under Settings → General → Min. profitability USD/day.
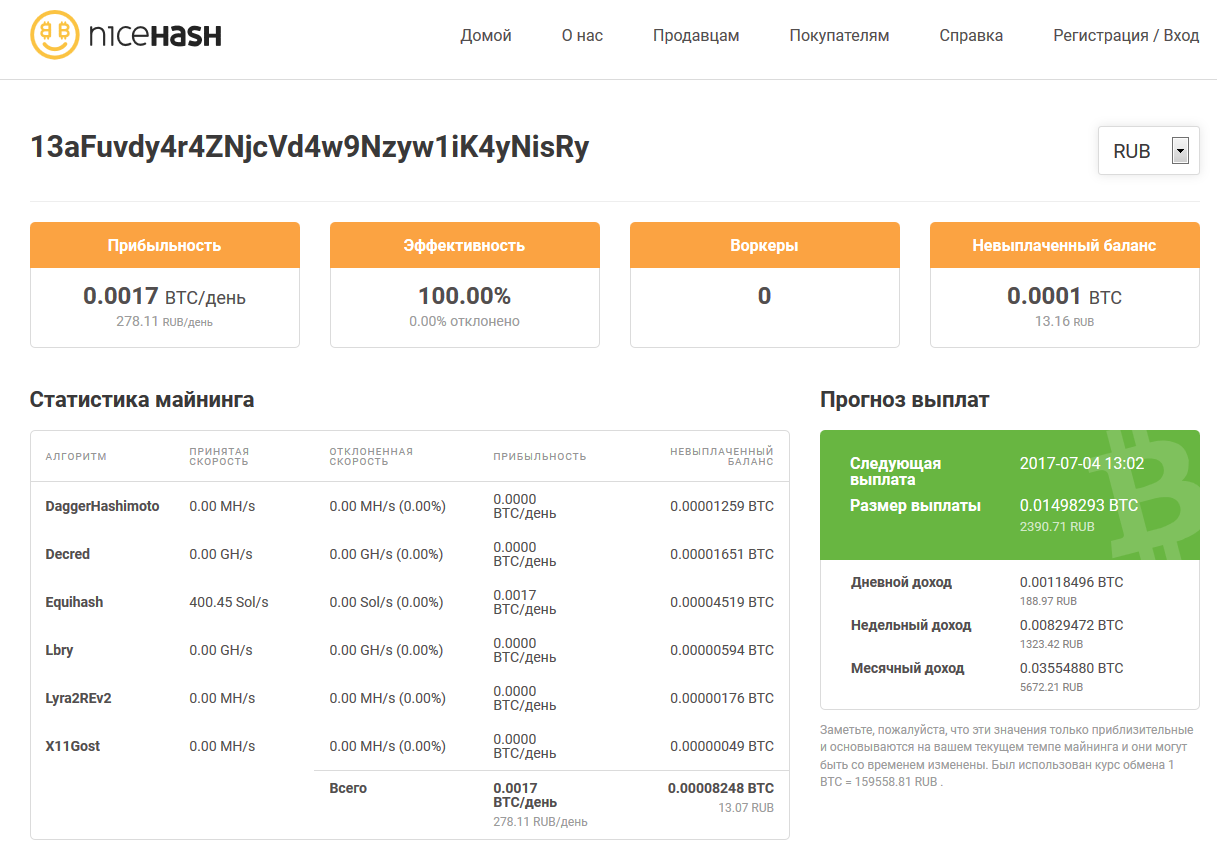
It’s better to assess profitability over a longer period—at least a week. The stats available in the NHM pool’s web interface will help with that. In the example below, you can see how the first 100 uBTC were earned. Most of it was paid for work done by “Excavator.” A small amount came from Decred and Ether, while mining the other altcoins was unprofitable most of the time.
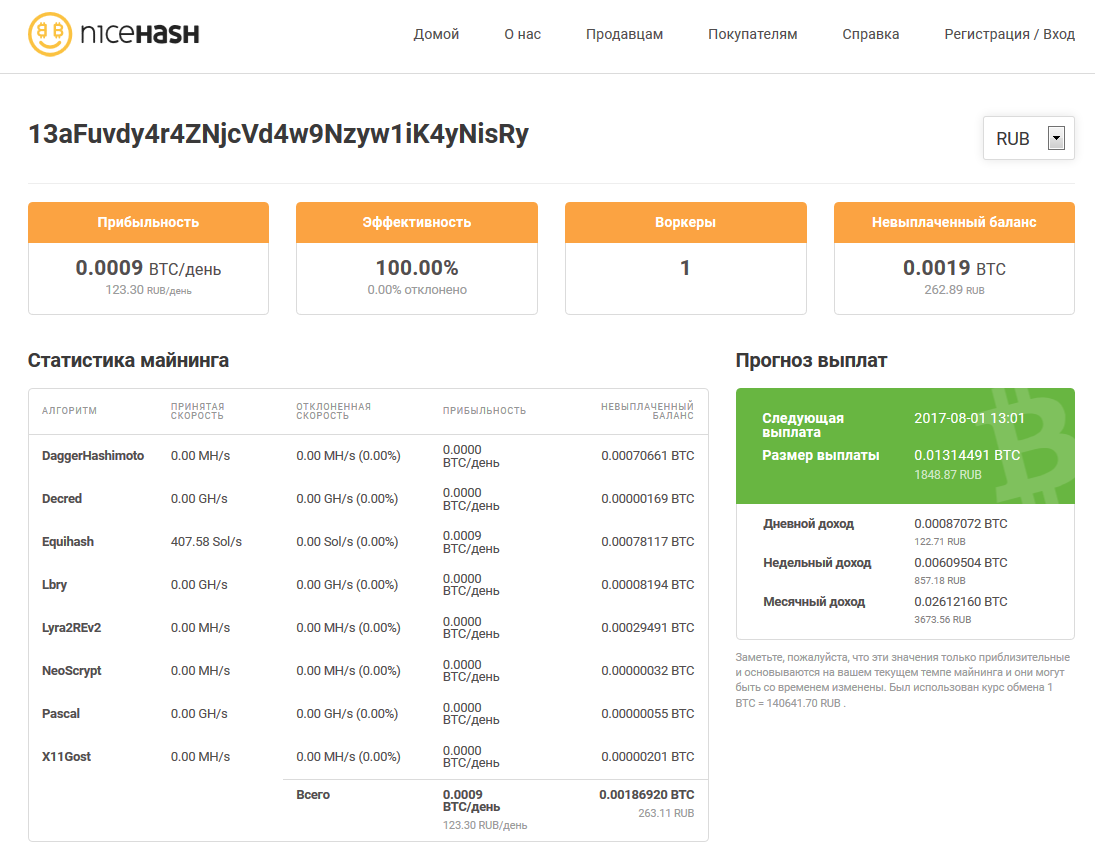
However, the balance shifts over time. Most payouts now come from Ether and ZCash in roughly equal shares, and when both see weak profitability, Lyra2REv2 picks up the slack.
Optimizing Mining Profitability
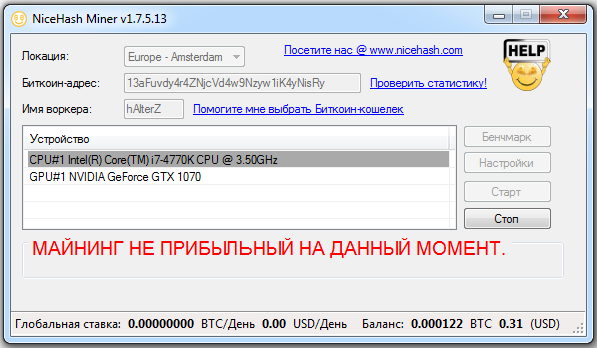
Estimated mining profitability depends on current market prices, network difficulty, and a range of other factors. There are many of them, they change constantly, and tracking them manually is highly inefficient. That’s why NHM and similar automation tools make sense. However, with default settings they often ignore important adjustments and can do more harm than good by switching you to less profitable algorithms.
The idea behind the profitability settings is straightforward: if the electricity your system consumes costs you more than you’re currently earning from mining the selected cryptocurrency, the software will try switching to other altcoins. If all of them are still unprofitable, mining becomes pointless and is automatically paused until conditions improve.
The sweet spot might arrive in fifteen minutes or in a couple of days—there’s no way to know ahead of time. That’s why NHM periodically reevaluates conditions and automatically starts mining when it’s advantageous. You can see the current hashrate and an estimate of profitability in NHM’s main window. These figures update nearly in real time and are shown in both dollars and bitcoin.
The technology for automatically switching mining to the most profitable algorithm is called BPASMAM (Best Profit Auto-Switching Multi-Algorithm Mining). Every ten minutes it checks order data on NiceHash.com to determine which cryptocurrency is currently in highest demand and launches your miner with the corresponding algorithm.
Example: you start mining ZCash in NHM and see an estimated average profitability of about 2.40 USD per day per GPU. Within ten minutes, NHM figures out that mining Ethereum is currently more profitable and switches automatically, bringing you around 2.62 USD per day. A few hours later, new ZCash orders appear on the NHM marketplace and its profitability temporarily jumps to, say, 2.76 USD per day—NHM switches back. If someone places large orders for Vertcoin, the Lyra2REv2 algorithm will temporarily take the lead, and the corresponding miner will auto-start on your rig as well. Constantly tracking crypto exchange rates and switching miners by hand is practically impossible. That’s why sticking to a single coin will usually earn you less than letting the miner hop across multiple algorithms.
The exception is when you’ve got insider information that a particular altcoin is about to attract major investment. In that case you mine it ahead of time despite its current low profitability, betting that the price will surge and you’ll sell the coins you mined early at a profit. But that’s just playing the market and guessing—you could hit the jackpot or lose everything, depending on how the chips fall. NHM helps you earn a steady income as efficiently as possible. Whatever altcoins you mine, you get paid in the “gold standard”—Bitcoin. For now, everything else still tends to follow Bitcoin’s price.
As another fallback algorithm during testing, I used Lyra2REv2. It’s exceptionally fast in CCminer and puts less load on the GPU than ethminer with its DAG files or the Excavator miner for ZCash. Lyra2REv2 would sometimes turn out to be the most profitable option, especially during periods of high market volatility.
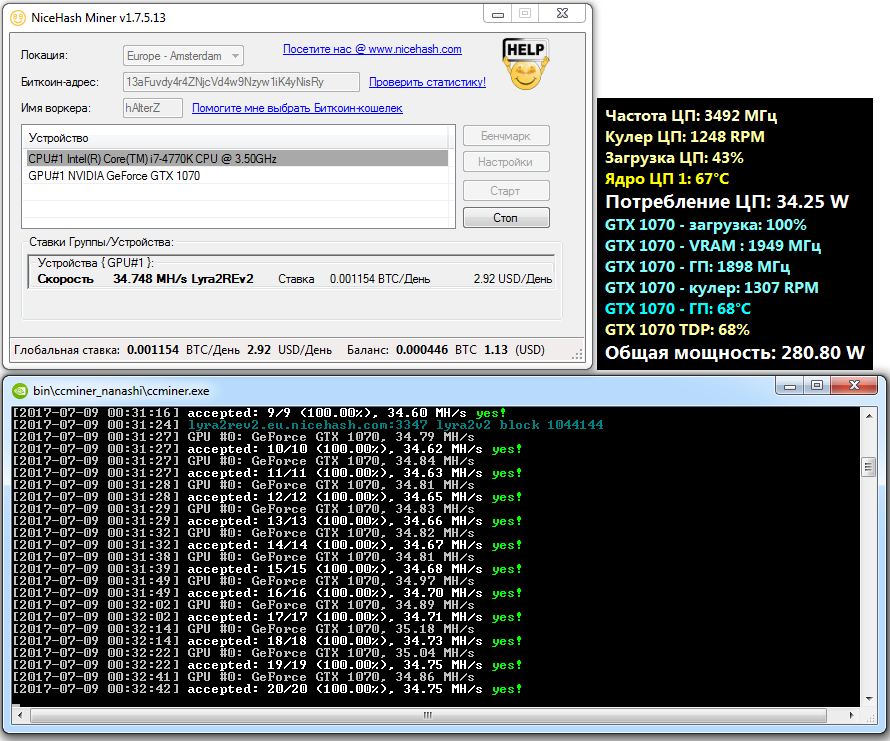
To determine the most profitable algorithm, a range of parameters are taken into account:
- Equivalent algorithm hashrate, expressed in gigahashes per second (GH/s)
- Weighted average price of current orders for each algorithm on the NiceHash pool (to compute equivalent altcoin profitability)
- Total open order volume per algorithm (to avoid switching to algorithms whose orders will be filled too quickly)
You can also optionally set user-defined adjustments (fX parameters), such as the farm’s performance and its daily electricity costs.
The final profitability table is calculated after the benchmark. I recommend using the precise evaluation mode instead of the standard one, because some algorithms are mismeasured in short benchmarks. For example, with Dagger-Hashimoto, starting the miner involves lengthy DAG file uploads to GPU memory and a sequential thread startup. As a result, its performance in the first minute is noticeably lower than it is afterward.
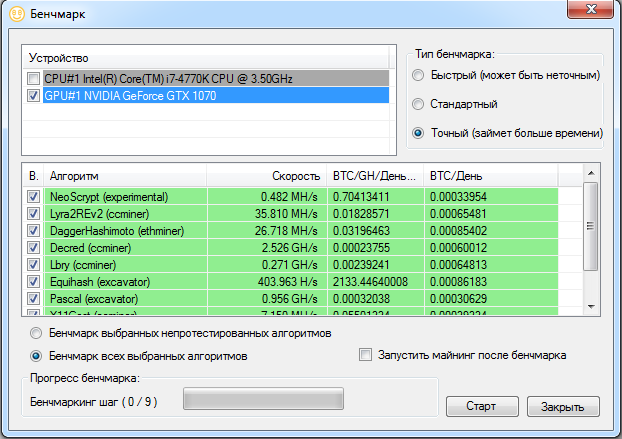
Profitability in the benchmark table is shown in normalized units: BTC/GH/day. Because different algorithms and miners compute hashes at different rates, NHM applies conversion multipliers relative to Scrypt. These are rough estimates. For example, the default multiplier for ScryptJaneNf16 is 0.0007, and for Keccak it’s 500. On your particular rig, they may be different. By default, the following algorithms have zero multipliers: Lyra2RE, Lyra2REv2, Quark, Qubit, WhirlpoolX. So once you’ve gathered enough performance data from your own farm, you should adjust these values. For details on how to do that, see the FAQ on the official site: FAQ.
Pro tip: from the many available cryptocurrencies, keep only two or three of the most profitable so you can switch between them. At a minimum, disable the least profitable ones and don’t waste time on them. For example, at the time of writing, mining Decred wasn’t worthwhile. Even after quadrupling the hashrate, it paid only twice as much because the difficulty spiked and prices tanked.
You can mine on CPUs with NHM, but it only makes economic sense if you have a lot of them, they’re otherwise idle, and you’re not paying for the electricity they consume.
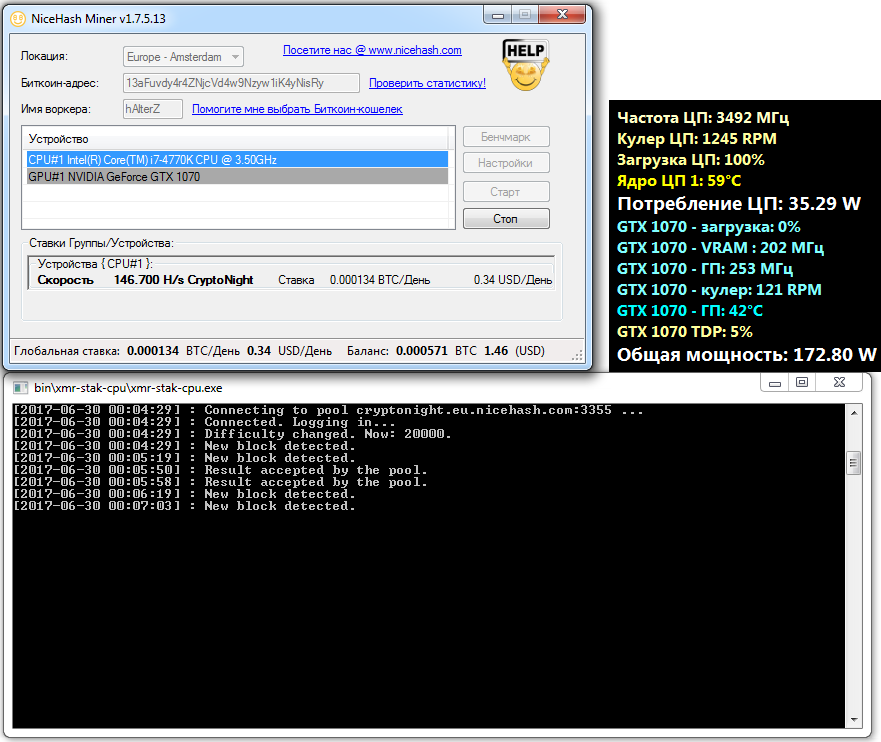
Factoring In the Real Costs
Beginner miners often make the same mistake: they rely on rough cost estimates based on a GPU’s TDP, because that’s the figure reported by command-line mining software. In reality, TDP doesn’t reflect actual power consumption. There are better ways to estimate mining costs more accurately.
To measure the farm’s total power draw, use a wattmeter. For my tests, I chose the Robiton PM-2 as the most accurate consumer model.

It can monitor power usage for connected loads up to 3.6 kW in total, which is enough for most entry- to mid-range mining farms. The same screen also shows other electrical parameters: voltage, current, power factor… It can even log total energy consumption and automatically calculate the cost once you enter the current rate.

I also displayed the readings from the built-in wattmeter in the CyberPower CP900EPFCLCD UPS. It measures the real-time power draw of the entire setup. In my case, that includes the monitor, router, external hard drive, and an auxiliary cooling system. You can see the total system power consumption in the screenshots with the miners running.
Why Open-Source Mining Matters to Developers
There are plenty of ways to make money in crypto. One of the most straightforward, in my view, is building a dedicated platform that helps investors, traders, and different kinds of miners find each other. For example, some people want to buy cloud mining services so they don’t have to pay for hardware or deal with setup and maintenance. Others want to mine in a pool using their own rigs, effectively renting out their hash power remotely. NiceHash, launched in 2014, connects both sides and makes money by charging fees.
A single intermediary service is inexpensive, but multiplied across thousands of contracts it generates substantial profit. Withdrawal fees are 2–4%. Payouts for any mining are made in bitcoin on a set schedule:
- Daily for all internal accounts with balances over 0.001 BTC
- Daily for all external wallets with balances over 0.1 BTC
- Weekly for all external wallets with balances over 0.01 BTC
Unpaid balances count as assets for NiceHash, and they can profit by accumulating and investing that cryptocurrency.
PiMP
If you want the easy route, you can buy a portable mining OS image—PiMP (Portable Instant Mining Platform). It’s a specialized, very easy-to-use Debian-based distro with a GUI, and it’s recommended to install it on a portable SSD of at least 16 GB. USB flash drives aren’t suitable due to heavy write workloads, and while USB hard drives are supported, they’re not recommended because of their low speed.
PiMP supports the Groestl, HEFTY1, JHA, Keccak, NIST5, Quark, Qubit, Scrypt, Scrypt-N, Scrypt-Jane, Skein, X11, X13, and X15 algorithms. New algorithms are added on an ongoing basis, but only those that can be mined efficiently on GPUs. For a long time, PiMP supported only AMD GPUs (Radeon HD 7700 and newer). In the latest 2.1 release, support for Nvidia GPUs was added (starting with the 400 series).

PiMP comes fully preconfigured out of the box. The desktop includes shortcuts to help and IRC support, and automatic updates are set to run on startup. PiMP costs 30 USD. After payment, along with the sector-by-sector image you’ll receive license keys and instructions for deploying the image using free tools in just a couple of clicks. To start mining, simply connect the PiMP SSD to any rig and boot from it.
You can also make money with PiMP and NHM through referral links, but I’m allergic to pyramid marketing, so this article uses plain links with no referral IDs.
Choosing a Wallet
To store cryptocurrency, you’ll need a wallet. You can install a bunch of coin-specific wallets for each altcoin, or use a single address by converting everything to Bitcoin. Wallets generally fall into three categories:
- Fully offline wallets (e.g., Armory);
- Lightweight mobile wallets (e.g., Copay);
- Fully online wallets (e.g., GreenAddress).
Full-node wallets give you the most control, but they’re extremely resource-hungry. The Bitcoin blockchain alone is over 120 GB. The initial sync can take nearly a day and hammers your storage with heavy multi-threaded I/O.
If you lose the password to your offline (cold) wallet, you’ll lose access to your coins—there’s no reset or recovery. Back up regularly!
Wallets of the second type are less resource-intensive because most of the blockchain is stored on remote servers. The trade-off is that you have to trust third‑party services. Some providers offer password recovery features, which can be a nice perk—or come back to bite you. These wallets are recommended for mobile devices because they save storage space and bandwidth.
Type-3 wallets are the most versatile. Essentially, all operations are performed remotely via a web interface in your browser or a mobile app. It’s the most lightweight—and the least trustworthy—option. You’re entirely dependent on third-party servers and you don’t actually control your coins.
Conclusions
Claymore’s Dual Miner, NiceHash Miner, and PiMP helped ignite the current mining craze. They lowered the barrier to entry so much that anyone, regardless of education or computer skills, can feel like a crypto mogul. As a result, people far removed from IT started seriously getting into altcoins and sparked a massive wave of interest in them—really a series of waves that was especially noticeable from April to July 2017. The current wave has subsided, but the next one is already on the horizon.
Many of those who jumped into crypto mining over the past six months never dug into the details. They’ve already gotten disillusioned and are now offloading their rigs, flooding the secondhand market with GPUs that have been run hard. Some are trying to make money another way—selling paid advice on mining and rig setup, or posing as small-scale cloud providers. So don’t be quick to trust these “experts” or swap out your hardware; run the numbers yourself first.
