British customers of automakers Renault and Dacia have been notified that their personal data has been compromised. It is reported that the leak occurred at a third-party contractor.
CONTINUE READING 🡒 Hunting Raccoon Stealer: How a Malware Developer’s OPSEC Failure Exposed…
In most cases, actors get unmasked because the malware author makes a basic OPSEC mistake. That’s what happened this time: the Trojan’s developer not only exposed himself but also gave away all his customers—much to the delight…
CONTINUE READING 🡒 Self-propagating SORVEPOTEL worm targets WhatsApp users
Trend Micro analysts have warned that Brazilian WhatsApp users are being targeted by a new self-propagating malware, SORVEPOTEL, which is aimed at infecting Windows systems.
CONTINUE READING 🡒 CometJacking attack turns Perplexity’s AI browser into a data‑stealing tool
Researchers have detailed a CometJacking attack that exploits URL parameters to pass hidden instructions to Perplexity’s Comet AI browser. The attack enables access to sensitive data from connected services, including email and calendar.
CONTINUE READING 🡒 Bugs in OpenSSL allowed private key recovery, code execution, and…
The OpenSSL developers have announced the release of several new versions of the open-source SSL/TLS toolkit that fix three vulnerabilities at once.
CONTINUE READING 🡒 Battering RAM attack bypasses the latest protections on Intel and…
Experts have demonstrated the Battering RAM hardware attack, which bypasses protections on the latest Intel and AMD processors used in cloud infrastructure. However, vendors are not overly concerned, since the attack requires physical access to the target…
CONTINUE READING 🡒 Outlook bug can only be fixed via Microsoft Support
Microsoft is investigating an issue that causes the classic Outlook mail client to crash on startup. For now, the bug can only be fixed via Microsoft Support.
CONTINUE READING 🡒 Listen to your heart. Writing an account hijacking utility
Today, you will write a program that intercepts user credentials, transmits them to a remote host in real time, makes it possible to start multiple RDP sessions, and breaks competing connections. In fact, all you have to do is modify the Mimikatz code.
CONTINUE READING 🡒 Critical Vulnerability in WD My Cloud Allows Remote Command Injection
Western Digital has released firmware updates for several My Cloud NAS models. The update fixes a critical vulnerability that could be used for remote execution of arbitrary commands.
CONTINUE READING 🡒 Crypto Mining FAQ: What to Mine Today, How to Mine…
You hear the word “mining” everywhere these days—even from people far outside the IT world. Crypto exchanges are seeing unprecedented price swings, and in July the combined market cap of cryptocurrencies topped $100 billion. The hype is…
CONTINUE READING 🡒 Gemini Trifecta vulnerabilities made the Gemini AI assistant steal data
Researchers have disclosed details of three already-fixed vulnerabilities in Google’s Gemini AI assistant, collectively dubbed Gemini Trifecta. If successfully exploited, these issues allowed attackers to trick the AI into participating in data theft and other malicious activity.
CONTINUE READING 🡒 DrayTek patches an RCE vulnerability in its routers
DrayTek, a networking equipment manufacturer, has issued an advisory about a vulnerability that affects several Vigor router models. The flaw allows remote, unauthenticated attackers to execute arbitrary code.
CONTINUE READING 🡒 Hackers stole Discord users’ data and identity documents
Hackers stole payment information and personal data (including real names and identity documents) of some Discord users. The attack occurred on September 20, 2025 and is linked to the compromise of a third-party provider that supplies the…
CONTINUE READING 🡒 Eight-Year-Old Vulnerability Found in the Unity Engine
A vulnerability has been discovered in the Unity game engine that has existed since 2017. The issue can be exploited for code execution on Android and for privilege escalation on Windows. Valve’s developers have already updated Steam,…
CONTINUE READING 🡒 Android: 8 Universal ROMs, Modern Click Bots, App Hacking, and…
In this issue: universal Android 8 ROMs, multi-headed trojans and chatbots, clickbots, abusing Android notifications, breaking into apps via trusted components, and of course a quick network pentest—how to make apps trust us. We didn’t forget coding…
CONTINUE READING 🡒 Android for Linux Users: Integrating Your Smartphone with Linux
Android and Linux distributions aren’t just related OSes—they share the same kernel and are very similar under the hood. Most Linux commands work on Android; you can install bash, write scripts, and even run servers. Set up…
CONTINUE READING 🡒 ReactOS: Why Trojans Run on the Windows Alternative but Microsoft…
On display in our cabinet of curiosities today is an unusual specimen—a twenty‑year‑gestating OS embryo learning to take its first steps. For now it can only stand and move gingerly, but it’s already trying to communicate with…
CONTINUE READING 🡒 Hands-on with the Omega2: What a Tiny, Low-Cost Linux Microcomputer…
Every maker eventually hits a point where basic microcontrollers just don’t cut it anymore, but dropping cash on a Raspberry Pi feels hard to justify. That’s where the modestly named Onion Omega2 comes in. It’s comparable to…
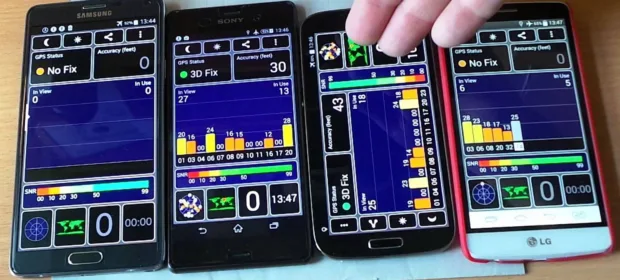
CONTINUE READING 🡒 How to Test and Improve GPS Signal Quality on Android
If you often find your phone struggles to get an accurate GPS fix, don’t rush to blame the navigation app. The problem is usually with GPS signal reception and satellite acquisition. You can test the receiver’s performance…
CONTINUE READING 🡒 Android SQLite Database: Quick Integration Guide
Android apps can store large amounts of data in a private, app-specific database—hidden from prying eyes. You’ll be surprised how useful this is and, more importantly, how easy it can be.
CONTINUE READING 🡒