Experts have demonstrated the Battering RAM hardware attack, which bypasses protections on the latest Intel and AMD processors used in cloud infrastructure. However, vendors are not overly concerned, since the attack requires physical access to the target device.
Battering RAM was created by researchers from KU Leuven (Catholic University of Leuven) and the University of Birmingham. Recall that late last year the same team demonstrated the BadRAM attack, which used about $10 worth of hardware to break AMD SEV-SNP (Secure Encrypted Virtualization–Secure Nested Paging), which protects the memory of virtual machines.
According to the researchers, Battering RAM disrupts the operation of the Intel SGX and AMD SEV-SNP mechanisms, which are widely used by cloud providers to protect data even from insiders and attackers who may have access to the host system.
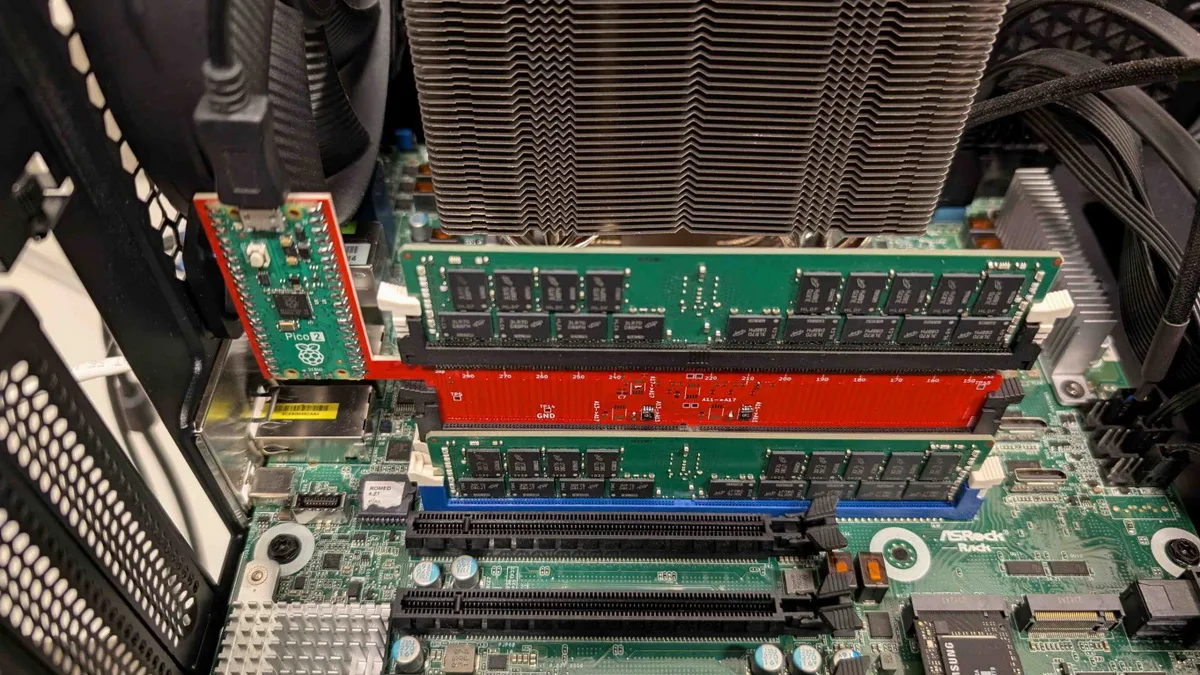
The attack works as follows: a special device-interposer is placed between the CPU and DRAM, which can be assembled for as little as $50. It attaches to a DIMM module and can operate unobtrusively, without raising suspicion. However, once activated, such a device begins covertly redirecting protected memory addresses to regions controlled by the attackers.
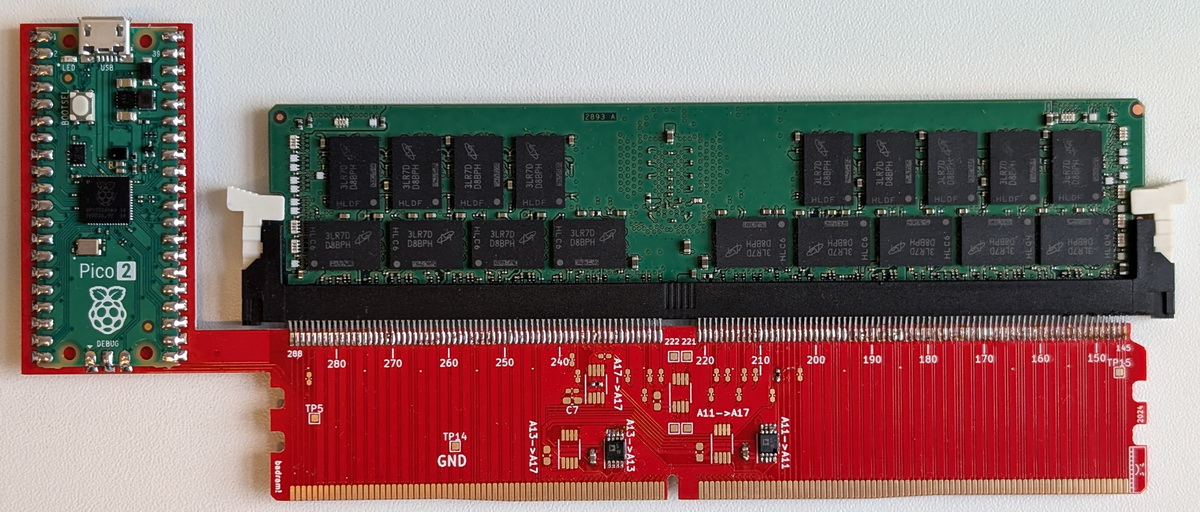
“Our stealthy interposer bypasses memory encryption and modern boot-time protections while remaining invisible to the OS,” the researchers explain. “It provides arbitrary access to plaintext data in SGX-protected memory and breaks SEV attestation on fully patched systems. As a result, Battering RAM highlights the limitations of modern scalable memory encryption.”
Carrying out such an attack requires physical access to the target system, but the researchers claim the attacker would need very little time. They believe that in real-world conditions such attacks could be carried out by rogue employees of cloud providers, data center technicians, law enforcement personnel, or participants in the memory module supply chain (at the manufacturing or delivery stage).
It is noted that the proof-of-concept interposer currently works only with DDR4 memory, but a more advanced version will be able to target DDR5 as well. In addition to the article describing the attack, the researchers have published all the technical information required to build an interposer for Battering RAM.
It is emphasized that software or firmware updates cannot address this vulnerability.
Representatives of Intel and AMD were notified about the issue back in February 2025. Although, alongside the publication of the research results, both manufacturers released their own bulletins on security, the companies emphasize that attacks requiring physical access fall outside the usual threat model for their products.
Intel noted that some Xeon processors support the Total Memory Encryption – Multi-Key (TME-MK) feature, which can provide additional protection against such attacks. The manufacturer also urged customers to ensure the physical security of their devices.