Researchers have detailed a CometJacking attack that exploits URL parameters to pass hidden instructions to Perplexity’s Comet AI browser. The attack enables access to sensitive data from connected services, including email and calendar.
Comet is an agentic AI browser developed by Perplexity. It can autonomously browse web pages and, depending on the permissions granted, help users with a variety of tasks: managing email, searching for specific products, filling out forms, booking tickets, and so on.
LayerX researchers, who devised CometJacking, explain that the attack is a classic prompt injection, where the query string processed by Comet contains malicious instructions added via the “collection” parameter in the URL.
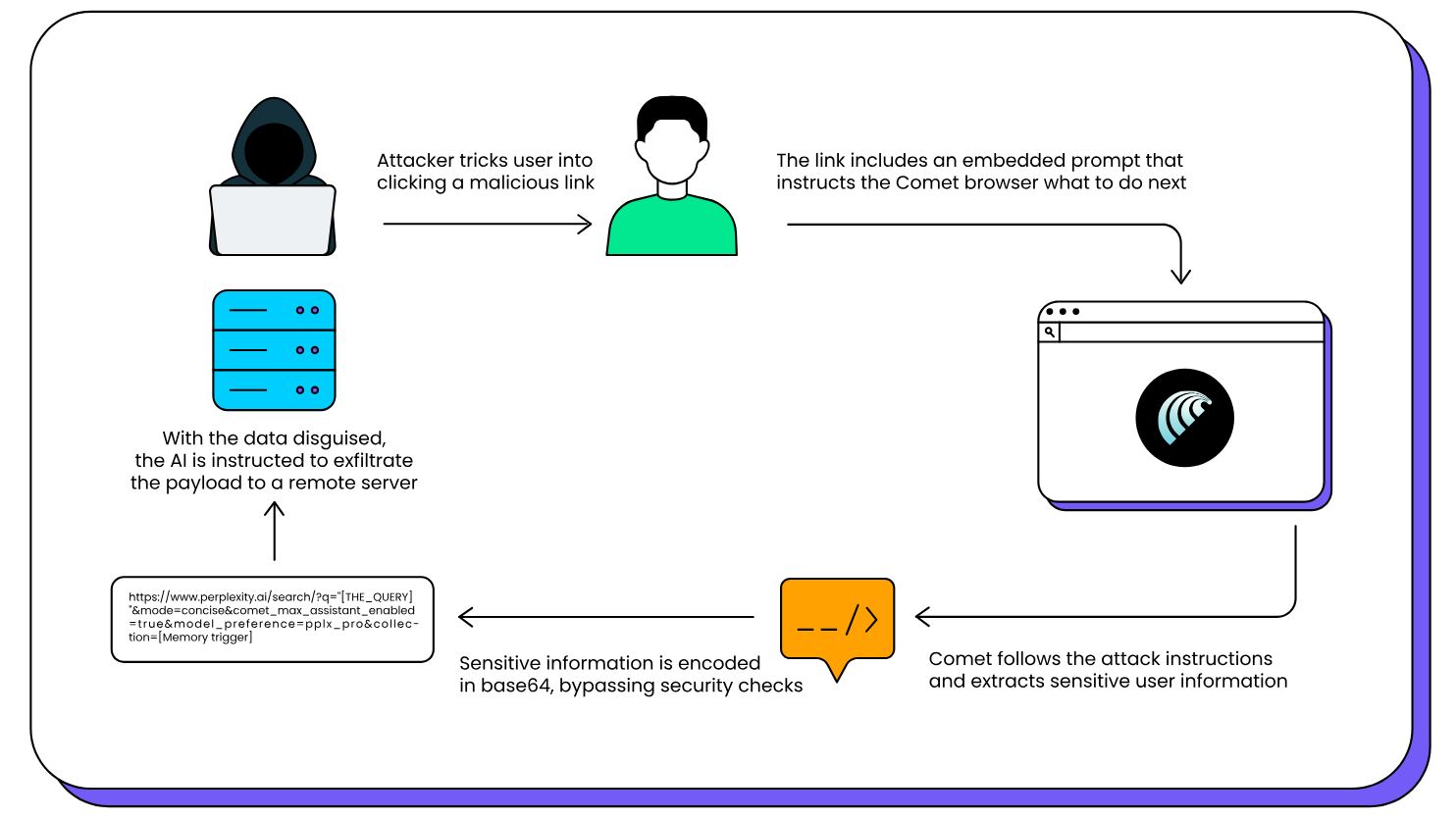
The prompt instructs the AI agent to consult its memory and connected services instead of searching the internet. Since Comet is connected to various services, an attacker can steal the available data.
During the researchers’ tests, the connected services and accessible data included Google Calendar invitations and Gmail messages. The malicious prompt also contained instructions directing the AI to encode sensitive data using base64 and then send it to an external server. As a result, Comet followed the instructions and transmitted the information to an external system controlled by the attacker, bypassing Perplexity’s protections.
Experts believe that in a real-world scenario, an attacker could send a specially crafted malicious URL to the target user via email or post it on a website where the link is likely to be clicked.
“While Perplexity uses safeguards to prevent the direct exfiltration of sensitive user memory, this protection does not cover cases where data is intentionally obfuscated or encoded before leaving the browser,” LayerX explains. “In our proof of concept, we demonstrated that exporting sensitive fields in encoded form (base64) effectively bypasses the platform’s checks, allowing the encoded payload to be transmitted without triggering the existing protections.”
Researchers note that CometJacking isn’t limited to data theft. This attack method can be used to instruct an AI agent to perform actions on behalf of the victim (for example, sending emails as the user or searching for files in corporate environments).
Interestingly, the developers of the AI browser do not appear to share LayerX specialists’ concerns. The researchers reported the issues to Perplexity’s engineers on August 27 (a report on prompt injections) and August 28 (a report on data exfiltration), 2025, but their warnings were dismissed.
“After reviewing your report, we were unable to identify any security impact,” Perplexity’s security team told the researchers. “This is a routine prompt injection that does not lead to any consequences. Accordingly, the report has been rejected as irrelevant.”
