This week, Apple introduced the iPhone 17 and iPhone Air, which will be equipped with a new memory protection feature designed to keep devices safe against sophisticated spyware attacks.
The new feature is called Memory Integrity Enforcement (MIE), and it is reported to provide continuous memory safety protection on new devices running iOS 26. At the same time, MIE will not degrade device performance thanks to the A19 and A19 Pro chips, which were designed with this in mind.
Apple representatives note that although iOS has not faced widespread malware attacks, iPhone users regularly become targets for threat actors with substantial resources.
As a rule, these attacks rely on exploits developed by commercial spyware vendors. And although such companies claim they provide spyware and their services only to government agencies for national security purposes and criminal investigations, in practice their products are often used by authoritarian regimes to target journalists, human rights defenders, and dissidents.
In practice, such exploits often rely on memory safety vulnerabilities, and the new MIE protection is designed to make exploiting such issues more difficult.
According to Apple, MIE uses Arm’s Enhanced Memory Tagging Extension (EMTE) technology, which was introduced in 2022 as an update to the 2019 Memory Tagging Extension (MTE) implementation.
MIE uses EMTE together with hardened memory allocators and Tag Confidentiality Enforcement mechanisms to protect the kernel and more than 70 user-space processes. The company says that MIE turns MTE from a “useful debugging tool” into a revolutionary defensive feature that provides protection against two common classes of vulnerabilities: buffer overflows and use-after-free issues, which can lead to memory corruption.
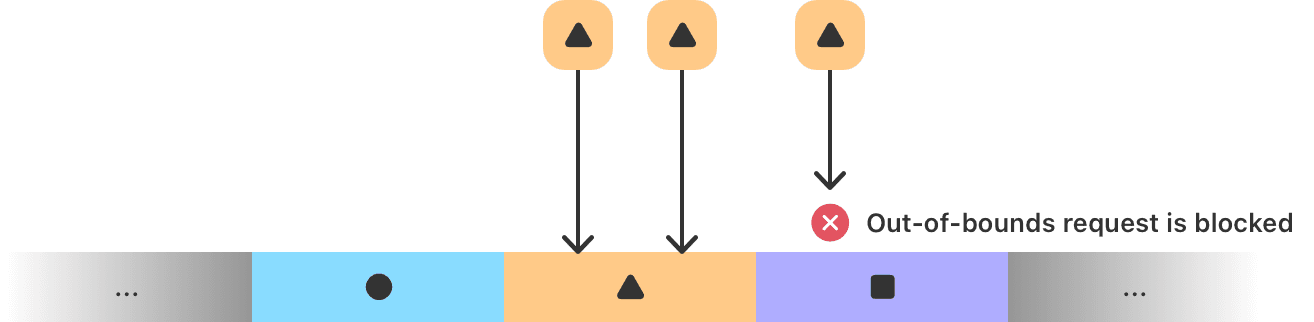
After testing MIE against known exploit chains and newly discovered vulnerabilities, Apple specialists concluded that the protection is effective at blocking attacks in their early stages, preventing attackers from “fixing” exploit chains by swapping one bug for another.
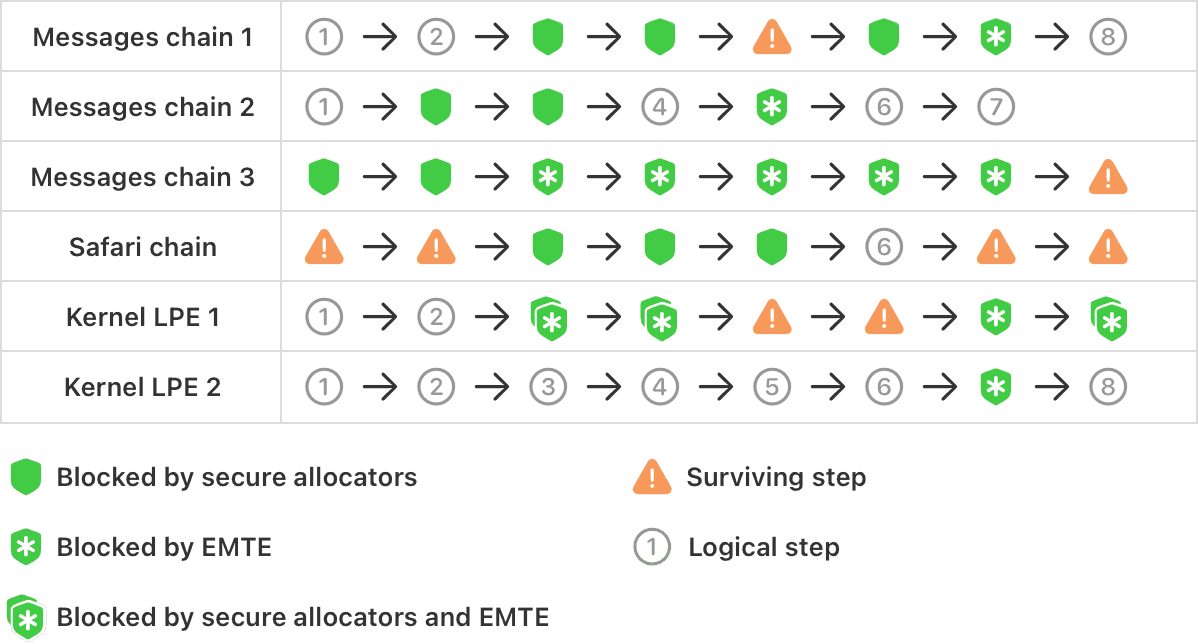
“Attackers will inevitably have to face MIE at a stage where their capabilities are still very limited, leaving little opportunity for exploitation. This leads to fragile chains where breaking just one link can nullify an entire exploitation strategy,” Apple comments.
As noted by Ivan Krstić, Apple’s head of Security Engineering and Architecture, MIE will make exploit chains significantly more expensive and harder to develop and maintain, which should disrupt many of the most effective exploitation techniques of the past 25 years.
Note that Google Pixel devices support MTE as a developer option starting with Android 13, and similar features for protecting memory integrity have been implemented by Microsoft in Windows 11.
