A new Rowhammer attack variant has been developed that can bypass the latest protection mechanisms in SK Hynix DDR5 chips. The attack, dubbed Phoenix, can obtain root privileges on DDR5-based systems in under two minutes.
Recall that the original Rowhammer attack was introduced in 2014 by researchers at Carnegie Mellon University. Its essence is that rapidly and repeatedly accessing certain memory cells can cause bit flips in adjacent cells.
Memory cells store information as electrical charges that determine whether bits are 1 or 0. Due to the increased density of cells, repeated “hammering” (when an application accesses the same regions thousands of times within fractions of a second) can alter the charge state in adjacent rows, causing bit flips. That’s where the name Rowhammer comes from.
One of the defensive mechanisms against Rowhammer attacks is called Target Row Refresh (TRR). It prevents bit flips by triggering additional row refreshes when frequent accesses to a particular row are detected.
The Phoenix Rowhammer attack was developed by specialists at Google and the COMSEC team from the Swiss Federal Institute of Technology in Zurich (ETH Zurich). The report emphasizes that they tested the attack on Hynix DDR5 products (one of the largest memory chip manufacturers, which holds about 36% of the market), but Phoenix may also threaten products from other vendors.
After reverse-engineering the complex defense mechanisms that Hynix implemented to protect against Rowhammer attacks and studying how they work, the researchers discovered that certain refresh intervals are not tracked by the protection, which a hypothetical attacker could exploit.
The researchers also developed a method that allows Phoenix to track and synchronize thousands of refresh operations, performing self-correction upon detecting any that were missed.
To bypass TRR protection, Phoenix spans 128 and 2608 refresh intervals and targets specific activation slots only at specific times.
As a result, the researchers managed to flip bits on all 15 DDR5 memory chips in the test pool and develop a privilege escalation exploit using Rowhammer. Tests showed that obtaining a root shell on a “standard DDR5 system with default settings” takes just 109 seconds.
The Phoenix authors also examined the practical exploitation of the attack to take control of the target system. They found that, when targeting PTEs to create an arbitrary read/write primitive, every product in the test was vulnerable.
In another test, the researchers targeted a virtual machine’s RSA-2048 keys to compromise SSH authentication and found that 73% of DIMM modules are vulnerable to such an attack.
In the third experiment, the researchers found that they could modify the sudo binary to escalate local privileges to root on 33% of the tested chips.
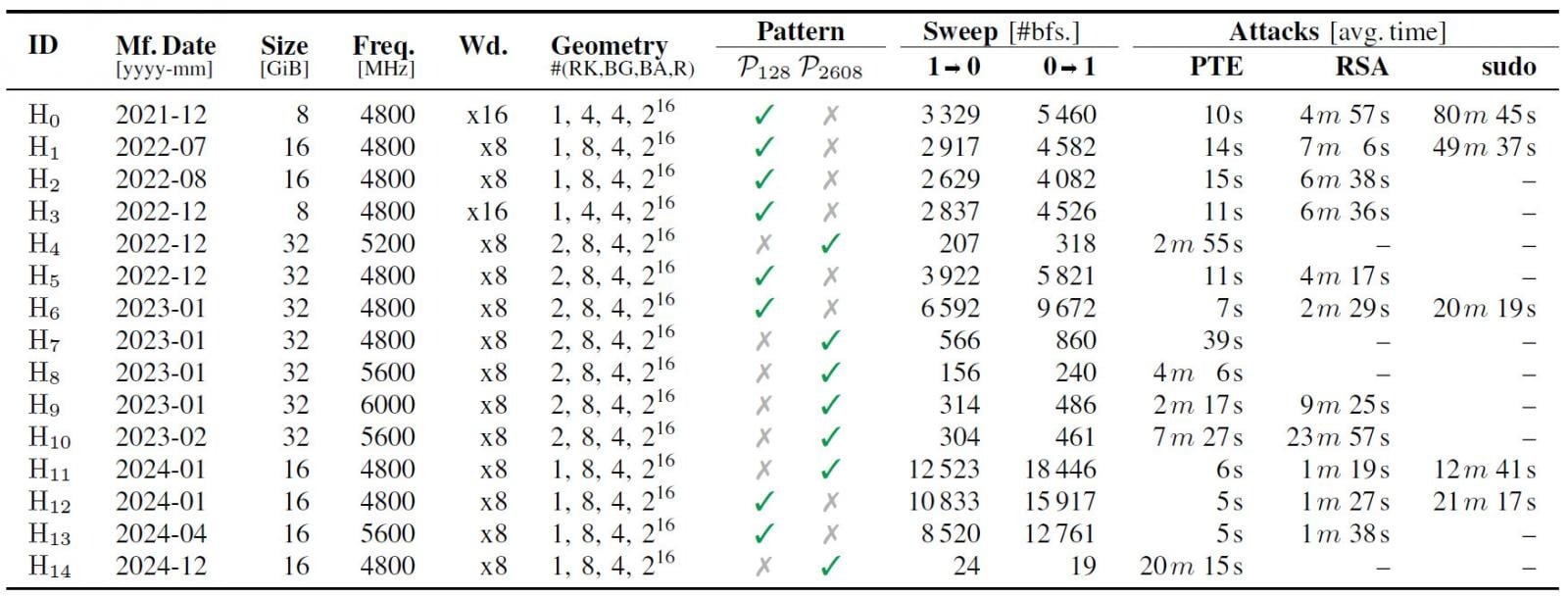
As can be seen from the table above, all the tested memory chips were vulnerable to at least one of the Phoenix Rowhammer attack patterns. The shorter pattern with 128 refresh intervals proved more effective and, on average, generates more “bit flips.”
The Phoenix issue has been assigned the identifier CVE-2025-6202, and the attack’s creators warn that it affects any DIMM RAM modules manufactured from January 2021 through December 2024.
Although Rowhammer is an industry-wide security issue that cannot be fixed in already shipped memory modules, users can protect themselves against Phoenix by tripling the DRAM refresh interval (tREFI). However, it is noted that this can provoke errors and data corruption, leading to overall system instability.
Alongside a detailed report on the new attack, the researchers have published on GitHub everything needed to reproduce Phoenix. The repository includes FPGA experiments for reverse-engineering TRR implementations and proof-of-concept exploit code.