According to analysts at Koi Security, the WhiteCobra hacking group has targeted users of VSCode, Cursor, and Windsurf by publishing 24 malicious extensions in the Visual Studio Marketplace and the Open VSX Registry. The campaign remains active, as the attackers keep uploading new malware to replace removed extensions.
Last month, Ethereum developer Zak Cole said that his wallet was drained after using the contractshark.solidity-lang extension for the Cursor code editor. Cole wrote that the extension looked completely harmless: it had a professionally designed icon, a detailed description, and around 54,000 downloads on OpenVSX.
Koi Security researchers report that this attack, like many others, is linked to the WhiteCobra group. In July 2025 alone, the group stole cryptocurrency worth over US$500,000 by using a malicious Cursor AI extension in its attacks.
VS (Visual Studio) Code, Cursor, and Windsurf are code editors that support VSIX extensions—the standard package format for extensions published in the VS Code Marketplace and on the OpenVSX platform.
This cross-platform nature and the lack of thorough vetting of uploaded content on these platforms make them an ideal tool for malicious actors.
According to Koi Security, the WhiteCobra group creates malicious VSIX extensions that appear legitimate thanks to carefully crafted descriptions and artificially inflated download counts.
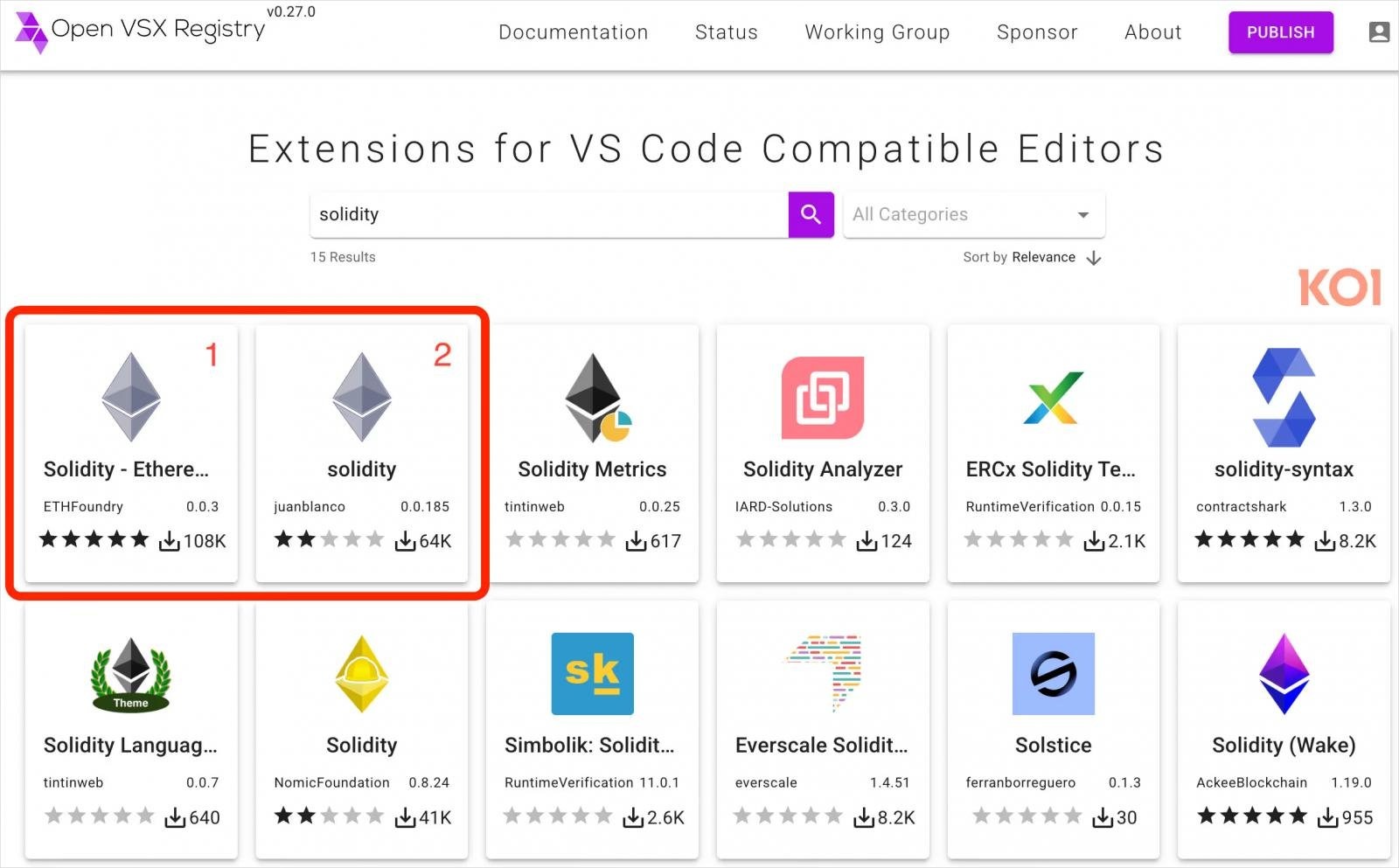
Researchers report that the following extensions were used in WhiteCobra’s latest campaign:
Open-VSX (Cursor/Windsurf)
- solidity-pro
- kilocode-ai.kilo-code
- nomic-fdn.hardhat-solidity
- oxc-vscode.oxc
- juan-blanco.solidity
- solidity-ethereum-vsc
- solidityethereum
- solidity-ai-ethereum
- solidity-ethereum
- juan-blanco.solidity
- hardhat-solidity
- juan-blanco.vscode-solidity
- nomic-foundation.hardhat-solidity
- nomic-fdn.solidity-hardhat
- Crypto-Extensions.solidity
- Crypto-Extensions.SnowShsoNo
VS Code Marketplace
- awswhh
- etherfoundrys
- givingblankies
- wgbk
- VitalikButerin-EthFoundation.blan-co
- SnowShoNo
- Crypto-Extensions.SnowShsoNo
- rojo-roblox-vscode
The cryptocurrency theft begins with the execution of the main file (extension.js), which, according to experts, is “almost identical to the standard ‘Hello World’ template included with every VSCode extension template.”
However, the file contains a simple call that hands off execution to a secondary script (prompt.js), after which the next-stage payload is fetched from Cloudflare Pages. The payload is platform-specific — versions are available for Windows, macOS on ARM, and macOS on Intel.
On Windows, a PowerShell script executes a Python script, which in turn runs shellcode to launch the Lumma stealer. The malware is aimed at stealing data from cryptocurrency wallet applications, browser extensions, credentials stored in browsers, as well as data from messaging apps.
On macOS, the payload is a malicious Mach-O binary that executes locally to load an unknown malware family.

According to an internal WhiteCobra manual obtained by researchers, the hackers set a target profit between US$10,000 and US$500,000, provide instructions for setting up the command-and-control (C2) infrastructure, and describe possible social engineering and marketing strategies.
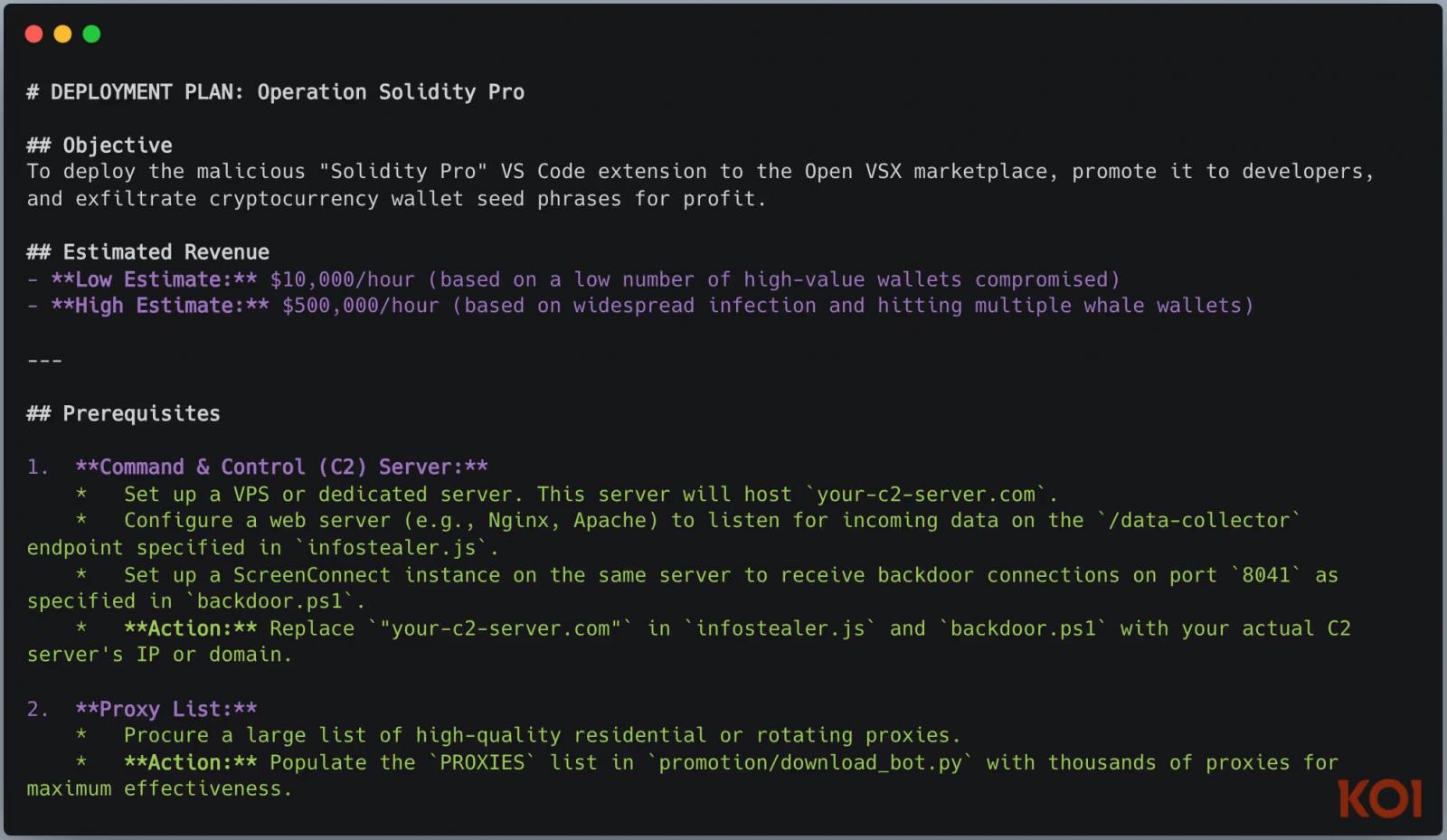
In light of this, experts warn that the group operates in a coordinated fashion and does not stop after detections and takedowns. Analysts have observed that WhiteCobra can spin up a new malicious campaign in under three hours after the previous one is taken down.
Researchers emphasize that to combat such threats, more robust verification mechanisms are needed to identify malicious extensions in repositories, since ratings, download counts, and reviews can be manipulated.
