A group of researchers from the Georgia Institute of Technology claims that Tile Bluetooth trackers transmit identifying data in plaintext. This makes it easy to identify and track their owners.
According to experts, the numerous issues with Tile devices contradict the security and privacy assurances made by the manufacturer, Life360. Researchers say the most surprising finding is that Tile’s servers continuously collect data on tracker locations, MAC addresses, and unique IDs without end-to-end encryption.
At the same time, the tags themselves broadcast unencrypted Bluetooth signals, which can be intercepted to eavesdrop on and track someone else’s device. Worse, Tile device MAC addresses are static, and the periodically repeating unique IDs are only partially randomized and are reused over time.
It is worth noting that in 2023, several stalking victims filed a lawsuit against Life360, the tracker manufacturer. They claimed that the company’s partnership with Amazon, which gave the trackers access to the Sidewalk network, only increased the danger faced by stalking targets. Since then, various anti-stalking protections have been added to Android and Apple devices, yet Tile devices still have a number of serious problems.
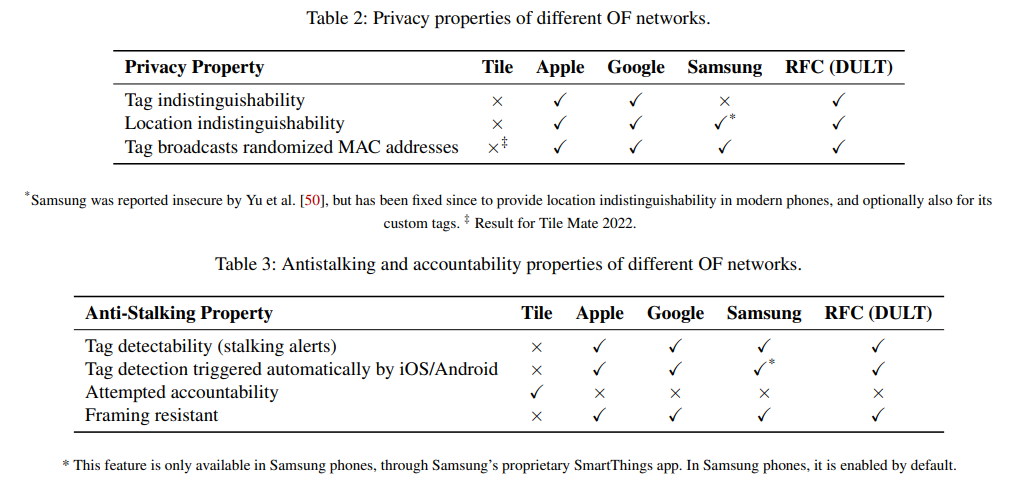
As decompilation of the Tile app for Android, examination of its code, and analysis of the Bluetooth and network traffic between the Tile Mate and a Google Pixel 3 XL have shown, Tile’s anti-stalking features are practically useless, since the tracker constantly broadcasts a static MAC address over Bluetooth in plaintext.
Since Tile trackers transmit unencrypted data, attackers can target the device’s Bluetooth broadcasts, identify specific trackers, and build detailed profiles of people’s movements without their knowledge or consent.
At the same time, one of the features created to protect against stalking (the Scan and Secure mode) makes Tile tags visible to anyone who scans them. This feature is intended to detect unauthorized trackers that could be used for surveillance. However, the anti-theft feature, which the company promotes in the context of placing hidden trackers, can be enabled and makes devices invisible to Scan and Secure.
The report notes that when using the anti-theft protection feature, Tile’s servers do not show results for specific trackers; however, “a user with a modified app can display all privateIDs logged” during a Scan and Secure search.
“All manufacturers except Tile have long since implemented anti-stalking algorithms that ensure tracker detection at the operating system level, providing continuous background scanning and automatic user notifications,” the researchers say. “By relying on manual, user-initiated scanning, Tile creates dangerous gaps in detection.”
This drawback is due to the fact that Tile is a third-party product that does not have OS-level access, only application-level access. This means Tile cannot perform background scanning unless it uses Google’s or Apple’s proprietary protocols.
Researchers note that they only examined the Tile Mate tracker, but they have no reason to believe that the company’s other products and third-party devices using its protocols are any more secure.
“In the version of the protocol we examined, Tile continuously receives users’ location data and can share it with law enforcement or other parties. Users concerned about privacy should avoid using such devices altogether,” the experts state.
For the first time, researchers at the Georgia Institute of Technology shared their findings with Life360 in November 2024, reaching out to the company’s CEO and support team, since the company has no official channel for vulnerability disclosure. Initially, Life360 representatives responded to the researchers and acknowledged the vulnerabilities, but after some time the communication ceased.
The researchers write that they proposed a number of measures to address the identified issues (for example, MAC address randomization, end-to-end data encryption, and randomization of unique device identifiers), but it is unclear whether Life360 has received these proposals.
Life360 told The Register that the company did receive warnings from experts and has made improvements to how the devices operate, but shared virtually no details. The company assured that it already encrypts data in transit from the devices to its servers and is also transitioning to the use of rotating MAC addresses.
